Unnamed: 0
int64 0
832k
| id
float64 2.49B
32.1B
| type
stringclasses 1
value | created_at
stringlengths 19
19
| repo
stringlengths 4
112
| repo_url
stringlengths 33
141
| action
stringclasses 3
values | title
stringlengths 1
994
| labels
stringlengths 4
719
| body
stringlengths 1
261k
| index
stringclasses 13
values | text_combine
stringlengths 95
261k
| label
stringclasses 2
values | text
stringlengths 96
252k
| binary_label
int64 0
1
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
161,211
| 6,111,107,841
|
IssuesEvent
|
2017-06-21 16:17:51
|
TerraFusion/basicFusion
|
https://api.github.com/repos/TerraFusion/basicFusion
|
closed
|
Check for MISR missing files in genInput.sh
|
Database Functionality Medium Priority
|
Need to write a check that if AA is missing, none of the other cameras are present.
|
1.0
|
Check for MISR missing files in genInput.sh - Need to write a check that if AA is missing, none of the other cameras are present.
|
non_secu
|
check for misr missing files in geninput sh need to write a check that if aa is missing none of the other cameras are present
| 0
|
393,041
| 26,969,855,035
|
IssuesEvent
|
2023-02-09 03:12:23
|
APSIMInitiative/ApsimX
|
https://api.github.com/repos/APSIMInitiative/ApsimX
|
closed
|
Add an example simulation that shows creating events in scripts
|
documentation
|
Need a simulation example that shows how to define events in a manager script that are published to the simulation.
|
1.0
|
Add an example simulation that shows creating events in scripts - Need a simulation example that shows how to define events in a manager script that are published to the simulation.
|
non_secu
|
add an example simulation that shows creating events in scripts need a simulation example that shows how to define events in a manager script that are published to the simulation
| 0
|
83,626
| 15,712,467,945
|
IssuesEvent
|
2021-03-27 12:15:25
|
emilykaldwin1827/goof
|
https://api.github.com/repos/emilykaldwin1827/goof
|
closed
|
CVE-2015-8855 (High) detected in semver-1.1.4.tgz
|
security vulnerability
|
## CVE-2015-8855 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>semver-1.1.4.tgz</b></p></summary>
<p>The semantic version parser used by npm.</p>
<p>Library home page: <a href="https://registry.npmjs.org/semver/-/semver-1.1.4.tgz">https://registry.npmjs.org/semver/-/semver-1.1.4.tgz</a></p>
<p>Path to dependency file: goof/package.json</p>
<p>Path to vulnerable library: goof/node_modules/npmconf/node_modules/semver/package.json</p>
<p>
Dependency Hierarchy:
- npmconf-0.0.24.tgz (Root Library)
- :x: **semver-1.1.4.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/emilykaldwin1827/goof/commit/27563f2447d85b487d3c44ea67f0f561f0c44b91">27563f2447d85b487d3c44ea67f0f561f0c44b91</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
The semver package before 4.3.2 for Node.js allows attackers to cause a denial of service (CPU consumption) via a long version string, aka a "regular expression denial of service (ReDoS)."
<p>Publish Date: 2017-01-23
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2015-8855>CVE-2015-8855</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2015-8855">https://nvd.nist.gov/vuln/detail/CVE-2015-8855</a></p>
<p>Release Date: 2017-01-23</p>
<p>Fix Resolution: semver (Npm package) - 4.3.2;Npm (NuGet package) - 2.14.14</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2015-8855 (High) detected in semver-1.1.4.tgz - ## CVE-2015-8855 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>semver-1.1.4.tgz</b></p></summary>
<p>The semantic version parser used by npm.</p>
<p>Library home page: <a href="https://registry.npmjs.org/semver/-/semver-1.1.4.tgz">https://registry.npmjs.org/semver/-/semver-1.1.4.tgz</a></p>
<p>Path to dependency file: goof/package.json</p>
<p>Path to vulnerable library: goof/node_modules/npmconf/node_modules/semver/package.json</p>
<p>
Dependency Hierarchy:
- npmconf-0.0.24.tgz (Root Library)
- :x: **semver-1.1.4.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/emilykaldwin1827/goof/commit/27563f2447d85b487d3c44ea67f0f561f0c44b91">27563f2447d85b487d3c44ea67f0f561f0c44b91</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
The semver package before 4.3.2 for Node.js allows attackers to cause a denial of service (CPU consumption) via a long version string, aka a "regular expression denial of service (ReDoS)."
<p>Publish Date: 2017-01-23
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2015-8855>CVE-2015-8855</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2015-8855">https://nvd.nist.gov/vuln/detail/CVE-2015-8855</a></p>
<p>Release Date: 2017-01-23</p>
<p>Fix Resolution: semver (Npm package) - 4.3.2;Npm (NuGet package) - 2.14.14</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve high detected in semver tgz cve high severity vulnerability vulnerable library semver tgz the semantic version parser used by npm library home page a href path to dependency file goof package json path to vulnerable library goof node modules npmconf node modules semver package json dependency hierarchy npmconf tgz root library x semver tgz vulnerable library found in head commit a href found in base branch master vulnerability details the semver package before for node js allows attackers to cause a denial of service cpu consumption via a long version string aka a regular expression denial of service redos publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution semver npm package npm nuget package step up your open source security game with whitesource
| 1
|
625,773
| 19,765,291,786
|
IssuesEvent
|
2022-01-17 00:52:39
|
secure-sw-dev/checkedc-llvm-project
|
https://api.github.com/repos/secure-sw-dev/checkedc-llvm-project
|
opened
|
Assertion fail for generic struct definition after non-generic pre-declaration
|
priority:3
|
This issue was copied from https://github.com/microsoft/checkedc-clang/issues/1092
----
```c
struct hash;
struct hash _For_any(K) {};
```
```
clang: /home/john/checkedc-clang/clang/lib/Sema/CheckedCSubst.cpp:302: bool clang::Sema::DiagnoseExpandingCycles(clang::RecordDecl*, clang::SourceLocation): Assertion `Base->isGenericOrItypeGeneric() && "Can only check expanding cycles for generic structs"' failed.
PLEASE submit a bug report to https://github.com/Microsoft/checkedc-clang/issues and include the crash backtrace, preprocessed source, and associated run script.
Stack dump:
0. Program arguments: clang -c hash.c
1. hash.c:2:27: current parser token ';'
2. hash.c:2:1: parsing struct/union body 'hash'
#0 0x000055c26848f381 llvm::sys::PrintStackTrace(llvm::raw_ostream&) /home/john/checkedc-clang/llvm/build/../lib/Support/Unix/Signals.inc:564:22
#1 0x000055c26848f418 PrintStackTraceSignalHandler(void*) /home/john/checkedc-clang/llvm/build/../lib/Support/Unix/Signals.inc:625:1
#2 0x000055c26848d16b llvm::sys::RunSignalHandlers() /home/john/checkedc-clang/llvm/build/../lib/Support/Signals.cpp:68:20
#3 0x000055c26848eb87 llvm::sys::CleanupOnSignal(unsigned long) /home/john/checkedc-clang/llvm/build/../lib/Support/Unix/Signals.inc:361:31
#4 0x000055c2683cf728 (anonymous namespace)::CrashRecoveryContextImpl::HandleCrash(int, unsigned long) /home/john/checkedc-clang/llvm/build/../lib/Support/CrashRecoveryContext.cpp:77:5
#5 0x000055c2683cfc1a CrashRecoverySignalHandler(int) /home/john/checkedc-clang/llvm/build/../lib/Support/CrashRecoveryContext.cpp:383:1
#6 0x00007fc9f787c3c0 __restore_rt (/lib/x86_64-linux-gnu/libpthread.so.0+0x153c0)
#7 0x00007fc9f731c18b raise /build/glibc-eX1tMB/glibc-2.31/signal/../sysdeps/unix/sysv/linux/raise.c:51:1
#8 0x00007fc9f72fb859 abort /build/glibc-eX1tMB/glibc-2.31/stdlib/abort.c:81:7
#9 0x00007fc9f72fb729 get_sysdep_segment_value /build/glibc-eX1tMB/glibc-2.31/intl/loadmsgcat.c:509:8
#10 0x00007fc9f72fb729 _nl_load_domain /build/glibc-eX1tMB/glibc-2.31/intl/loadmsgcat.c:970:34
#11 0x00007fc9f730cf36 (/lib/x86_64-linux-gnu/libc.so.6+0x36f36)
#12 0x000055c26b617e71 clang::Sema::DiagnoseExpandingCycles(clang::RecordDecl*, clang::SourceLocation) /home/john/checkedc-clang/clang/lib/Sema/CheckedCSubst.cpp:302:3
#13 0x000055c26b544be2 clang::Parser::ParseStructUnionBody(clang::SourceLocation, clang::TypeSpecifierType, clang::RecordDecl*) /home/john/checkedc-clang/clang/lib/Parse/ParseDecl.cpp:4572:9
#14 0x000055c26b566ad8 clang::Parser::ParseClassSpecifier(clang::tok::TokenKind, clang::SourceLocation, clang::DeclSpec&, clang::Parser::ParsedTemplateInfo const&, clang::AccessSpecifier, bool, clang::Parser::DeclSpecContext, clang::Parser::ParsedAttributesWithRange&) /home/john/checkedc-clang/clang/lib/Parse/ParseDeclCXX.cpp:2054:20
#15 0x000055c26b542cdf clang::Parser::ParseDeclarationSpecifiers(clang::DeclSpec&, clang::Parser::ParsedTemplateInfo const&, clang::AccessSpecifier, clang::Parser::DeclSpecContext, clang::Parser::LateParsedAttrList*) /home/john/checkedc-clang/clang/lib/Parse/ParseDecl.cpp:4067:26
#16 0x000055c26b51a843 clang::Parser::ParseDeclOrFunctionDefInternal(clang::Parser::ParsedAttributesWithRange&, clang::ParsingDeclSpec&, clang::AccessSpecifier) /home/john/checkedc-clang/clang/lib/Parse/Parser.cpp:1042:57
#17 0x000055c26b51af67 clang::Parser::ParseDeclarationOrFunctionDefinition(clang::Parser::ParsedAttributesWithRange&, clang::ParsingDeclSpec*, clang::AccessSpecifier) /home/john/checkedc-clang/clang/lib/Parse/Parser.cpp:1154:57
#18 0x000055c26b51a2d1 clang::Parser::ParseExternalDeclaration(clang::Parser::ParsedAttributesWithRange&, clang::ParsingDeclSpec*) (.localalias) /home/john/checkedc-clang/clang/lib/Parse/Parser.cpp:956:58
#19 0x000055c26b51942a clang::Parser::ParseTopLevelDecl(clang::OpaquePtr<clang::DeclGroupRef>&, bool) /home/john/checkedc-clang/clang/lib/Parse/Parser.cpp:704:42
#20 0x000055c26b514d88 clang::ParseAST(clang::Sema&, bool, bool) /home/john/checkedc-clang/clang/lib/Parse/ParseAST.cpp:158:37
#21 0x000055c2690e0b11 clang::ASTFrontendAction::ExecuteAction() /home/john/checkedc-clang/clang/lib/Frontend/FrontendAction.cpp:1057:11
#22 0x000055c269a5d7e3 clang::CodeGenAction::ExecuteAction() /home/john/checkedc-clang/clang/lib/CodeGen/CodeGenAction.cpp:1185:1
#23 0x000055c2690e0468 clang::FrontendAction::Execute() /home/john/checkedc-clang/clang/lib/Frontend/FrontendAction.cpp:954:38
#24 0x000055c269070d6f clang::CompilerInstance::ExecuteAction(clang::FrontendAction&) /home/john/checkedc-clang/clang/lib/Frontend/CompilerInstance.cpp:984:42
#25 0x000055c26927c4db clang::ExecuteCompilerInvocation(clang::CompilerInstance*) /home/john/checkedc-clang/clang/lib/FrontendTool/ExecuteCompilerInvocation.cpp:278:38
#26 0x000055c266b1a91b cc1_main(llvm::ArrayRef<char const*>, char const*, void*) /home/john/checkedc-clang/clang/tools/driver/cc1_main.cpp:240:40
#27 0x000055c266b0f7e3 ExecuteCC1Tool(llvm::SmallVectorImpl<char const*>&) /home/john/checkedc-clang/clang/tools/driver/driver.cpp:330:20
#28 0x000055c268f66659 clang::driver::CC1Command::Execute(llvm::ArrayRef<llvm::Optional<llvm::StringRef> >, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >*, bool*) const::'lambda'()::operator()() const /home/john/checkedc-clang/clang/lib/Driver/Job.cpp:400:32
#29 0x000055c268f66f22 void llvm::function_ref<void ()>::callback_fn<clang::driver::CC1Command::Execute(llvm::ArrayRef<llvm::Optional<llvm::StringRef> >, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >*, bool*) const::'lambda'()>(long) /home/john/checkedc-clang/llvm/include/llvm/ADT/STLExtras.h:186:40
#30 0x000055c2683c2636 llvm::function_ref<void ()>::operator()() const /home/john/checkedc-clang/llvm/build/../include/llvm/ADT/STLExtras.h:203:62
#31 0x000055c2683cfe2c llvm::CrashRecoveryContext::RunSafely(llvm::function_ref<void ()>) /home/john/checkedc-clang/llvm/build/../lib/Support/CrashRecoveryContext.cpp:419:10
#32 0x000055c268f66881 clang::driver::CC1Command::Execute(llvm::ArrayRef<llvm::Optional<llvm::StringRef> >, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >*, bool*) const /home/john/checkedc-clang/clang/lib/Driver/Job.cpp:400:7
#33 0x000055c268f196af clang::driver::Compilation::ExecuteCommand(clang::driver::Command const&, clang::driver::Command const*&) const /home/john/checkedc-clang/clang/lib/Driver/Compilation.cpp:195:22
#34 0x000055c268f19a12 clang::driver::Compilation::ExecuteJobs(clang::driver::JobList const&, llvm::SmallVectorImpl<std::pair<int, clang::driver::Command const*> >&) const /home/john/checkedc-clang/clang/lib/Driver/Compilation.cpp:246:53
#35 0x000055c268f298c2 clang::driver::Driver::ExecuteCompilation(clang::driver::Compilation&, llvm::SmallVectorImpl<std::pair<int, clang::driver::Command const*> >&) /home/john/checkedc-clang/clang/lib/Driver/Driver.cpp:1509:28
#36 0x000055c266b107b7 main /home/john/checkedc-clang/clang/tools/driver/driver.cpp:502:39
#37 0x00007fc9f72fd0b3 __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:342:3
#38 0x000055c266b0de7e _start (/home/john/checkedc-clang/llvm/build/bin/clang-11+0x2601e7e)
```
The assertion fail goes away if I switch the order, defining the generic struct first before declaring it without the `_For_any`. It is also fixed if the pre-declaration declares the struct with the generic (`struct hash _For_any(K)`).
Presumably this related to the unfinished work on generic structs for issue #644
|
1.0
|
Assertion fail for generic struct definition after non-generic pre-declaration - This issue was copied from https://github.com/microsoft/checkedc-clang/issues/1092
----
```c
struct hash;
struct hash _For_any(K) {};
```
```
clang: /home/john/checkedc-clang/clang/lib/Sema/CheckedCSubst.cpp:302: bool clang::Sema::DiagnoseExpandingCycles(clang::RecordDecl*, clang::SourceLocation): Assertion `Base->isGenericOrItypeGeneric() && "Can only check expanding cycles for generic structs"' failed.
PLEASE submit a bug report to https://github.com/Microsoft/checkedc-clang/issues and include the crash backtrace, preprocessed source, and associated run script.
Stack dump:
0. Program arguments: clang -c hash.c
1. hash.c:2:27: current parser token ';'
2. hash.c:2:1: parsing struct/union body 'hash'
#0 0x000055c26848f381 llvm::sys::PrintStackTrace(llvm::raw_ostream&) /home/john/checkedc-clang/llvm/build/../lib/Support/Unix/Signals.inc:564:22
#1 0x000055c26848f418 PrintStackTraceSignalHandler(void*) /home/john/checkedc-clang/llvm/build/../lib/Support/Unix/Signals.inc:625:1
#2 0x000055c26848d16b llvm::sys::RunSignalHandlers() /home/john/checkedc-clang/llvm/build/../lib/Support/Signals.cpp:68:20
#3 0x000055c26848eb87 llvm::sys::CleanupOnSignal(unsigned long) /home/john/checkedc-clang/llvm/build/../lib/Support/Unix/Signals.inc:361:31
#4 0x000055c2683cf728 (anonymous namespace)::CrashRecoveryContextImpl::HandleCrash(int, unsigned long) /home/john/checkedc-clang/llvm/build/../lib/Support/CrashRecoveryContext.cpp:77:5
#5 0x000055c2683cfc1a CrashRecoverySignalHandler(int) /home/john/checkedc-clang/llvm/build/../lib/Support/CrashRecoveryContext.cpp:383:1
#6 0x00007fc9f787c3c0 __restore_rt (/lib/x86_64-linux-gnu/libpthread.so.0+0x153c0)
#7 0x00007fc9f731c18b raise /build/glibc-eX1tMB/glibc-2.31/signal/../sysdeps/unix/sysv/linux/raise.c:51:1
#8 0x00007fc9f72fb859 abort /build/glibc-eX1tMB/glibc-2.31/stdlib/abort.c:81:7
#9 0x00007fc9f72fb729 get_sysdep_segment_value /build/glibc-eX1tMB/glibc-2.31/intl/loadmsgcat.c:509:8
#10 0x00007fc9f72fb729 _nl_load_domain /build/glibc-eX1tMB/glibc-2.31/intl/loadmsgcat.c:970:34
#11 0x00007fc9f730cf36 (/lib/x86_64-linux-gnu/libc.so.6+0x36f36)
#12 0x000055c26b617e71 clang::Sema::DiagnoseExpandingCycles(clang::RecordDecl*, clang::SourceLocation) /home/john/checkedc-clang/clang/lib/Sema/CheckedCSubst.cpp:302:3
#13 0x000055c26b544be2 clang::Parser::ParseStructUnionBody(clang::SourceLocation, clang::TypeSpecifierType, clang::RecordDecl*) /home/john/checkedc-clang/clang/lib/Parse/ParseDecl.cpp:4572:9
#14 0x000055c26b566ad8 clang::Parser::ParseClassSpecifier(clang::tok::TokenKind, clang::SourceLocation, clang::DeclSpec&, clang::Parser::ParsedTemplateInfo const&, clang::AccessSpecifier, bool, clang::Parser::DeclSpecContext, clang::Parser::ParsedAttributesWithRange&) /home/john/checkedc-clang/clang/lib/Parse/ParseDeclCXX.cpp:2054:20
#15 0x000055c26b542cdf clang::Parser::ParseDeclarationSpecifiers(clang::DeclSpec&, clang::Parser::ParsedTemplateInfo const&, clang::AccessSpecifier, clang::Parser::DeclSpecContext, clang::Parser::LateParsedAttrList*) /home/john/checkedc-clang/clang/lib/Parse/ParseDecl.cpp:4067:26
#16 0x000055c26b51a843 clang::Parser::ParseDeclOrFunctionDefInternal(clang::Parser::ParsedAttributesWithRange&, clang::ParsingDeclSpec&, clang::AccessSpecifier) /home/john/checkedc-clang/clang/lib/Parse/Parser.cpp:1042:57
#17 0x000055c26b51af67 clang::Parser::ParseDeclarationOrFunctionDefinition(clang::Parser::ParsedAttributesWithRange&, clang::ParsingDeclSpec*, clang::AccessSpecifier) /home/john/checkedc-clang/clang/lib/Parse/Parser.cpp:1154:57
#18 0x000055c26b51a2d1 clang::Parser::ParseExternalDeclaration(clang::Parser::ParsedAttributesWithRange&, clang::ParsingDeclSpec*) (.localalias) /home/john/checkedc-clang/clang/lib/Parse/Parser.cpp:956:58
#19 0x000055c26b51942a clang::Parser::ParseTopLevelDecl(clang::OpaquePtr<clang::DeclGroupRef>&, bool) /home/john/checkedc-clang/clang/lib/Parse/Parser.cpp:704:42
#20 0x000055c26b514d88 clang::ParseAST(clang::Sema&, bool, bool) /home/john/checkedc-clang/clang/lib/Parse/ParseAST.cpp:158:37
#21 0x000055c2690e0b11 clang::ASTFrontendAction::ExecuteAction() /home/john/checkedc-clang/clang/lib/Frontend/FrontendAction.cpp:1057:11
#22 0x000055c269a5d7e3 clang::CodeGenAction::ExecuteAction() /home/john/checkedc-clang/clang/lib/CodeGen/CodeGenAction.cpp:1185:1
#23 0x000055c2690e0468 clang::FrontendAction::Execute() /home/john/checkedc-clang/clang/lib/Frontend/FrontendAction.cpp:954:38
#24 0x000055c269070d6f clang::CompilerInstance::ExecuteAction(clang::FrontendAction&) /home/john/checkedc-clang/clang/lib/Frontend/CompilerInstance.cpp:984:42
#25 0x000055c26927c4db clang::ExecuteCompilerInvocation(clang::CompilerInstance*) /home/john/checkedc-clang/clang/lib/FrontendTool/ExecuteCompilerInvocation.cpp:278:38
#26 0x000055c266b1a91b cc1_main(llvm::ArrayRef<char const*>, char const*, void*) /home/john/checkedc-clang/clang/tools/driver/cc1_main.cpp:240:40
#27 0x000055c266b0f7e3 ExecuteCC1Tool(llvm::SmallVectorImpl<char const*>&) /home/john/checkedc-clang/clang/tools/driver/driver.cpp:330:20
#28 0x000055c268f66659 clang::driver::CC1Command::Execute(llvm::ArrayRef<llvm::Optional<llvm::StringRef> >, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >*, bool*) const::'lambda'()::operator()() const /home/john/checkedc-clang/clang/lib/Driver/Job.cpp:400:32
#29 0x000055c268f66f22 void llvm::function_ref<void ()>::callback_fn<clang::driver::CC1Command::Execute(llvm::ArrayRef<llvm::Optional<llvm::StringRef> >, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >*, bool*) const::'lambda'()>(long) /home/john/checkedc-clang/llvm/include/llvm/ADT/STLExtras.h:186:40
#30 0x000055c2683c2636 llvm::function_ref<void ()>::operator()() const /home/john/checkedc-clang/llvm/build/../include/llvm/ADT/STLExtras.h:203:62
#31 0x000055c2683cfe2c llvm::CrashRecoveryContext::RunSafely(llvm::function_ref<void ()>) /home/john/checkedc-clang/llvm/build/../lib/Support/CrashRecoveryContext.cpp:419:10
#32 0x000055c268f66881 clang::driver::CC1Command::Execute(llvm::ArrayRef<llvm::Optional<llvm::StringRef> >, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >*, bool*) const /home/john/checkedc-clang/clang/lib/Driver/Job.cpp:400:7
#33 0x000055c268f196af clang::driver::Compilation::ExecuteCommand(clang::driver::Command const&, clang::driver::Command const*&) const /home/john/checkedc-clang/clang/lib/Driver/Compilation.cpp:195:22
#34 0x000055c268f19a12 clang::driver::Compilation::ExecuteJobs(clang::driver::JobList const&, llvm::SmallVectorImpl<std::pair<int, clang::driver::Command const*> >&) const /home/john/checkedc-clang/clang/lib/Driver/Compilation.cpp:246:53
#35 0x000055c268f298c2 clang::driver::Driver::ExecuteCompilation(clang::driver::Compilation&, llvm::SmallVectorImpl<std::pair<int, clang::driver::Command const*> >&) /home/john/checkedc-clang/clang/lib/Driver/Driver.cpp:1509:28
#36 0x000055c266b107b7 main /home/john/checkedc-clang/clang/tools/driver/driver.cpp:502:39
#37 0x00007fc9f72fd0b3 __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:342:3
#38 0x000055c266b0de7e _start (/home/john/checkedc-clang/llvm/build/bin/clang-11+0x2601e7e)
```
The assertion fail goes away if I switch the order, defining the generic struct first before declaring it without the `_For_any`. It is also fixed if the pre-declaration declares the struct with the generic (`struct hash _For_any(K)`).
Presumably this related to the unfinished work on generic structs for issue #644
|
non_secu
|
assertion fail for generic struct definition after non generic pre declaration this issue was copied from c struct hash struct hash for any k clang home john checkedc clang clang lib sema checkedcsubst cpp bool clang sema diagnoseexpandingcycles clang recorddecl clang sourcelocation assertion base isgenericoritypegeneric can only check expanding cycles for generic structs failed please submit a bug report to and include the crash backtrace preprocessed source and associated run script stack dump program arguments clang c hash c hash c current parser token hash c parsing struct union body hash llvm sys printstacktrace llvm raw ostream home john checkedc clang llvm build lib support unix signals inc printstacktracesignalhandler void home john checkedc clang llvm build lib support unix signals inc llvm sys runsignalhandlers home john checkedc clang llvm build lib support signals cpp llvm sys cleanuponsignal unsigned long home john checkedc clang llvm build lib support unix signals inc anonymous namespace crashrecoverycontextimpl handlecrash int unsigned long home john checkedc clang llvm build lib support crashrecoverycontext cpp crashrecoverysignalhandler int home john checkedc clang llvm build lib support crashrecoverycontext cpp restore rt lib linux gnu libpthread so raise build glibc glibc signal sysdeps unix sysv linux raise c abort build glibc glibc stdlib abort c get sysdep segment value build glibc glibc intl loadmsgcat c nl load domain build glibc glibc intl loadmsgcat c lib linux gnu libc so clang sema diagnoseexpandingcycles clang recorddecl clang sourcelocation home john checkedc clang clang lib sema checkedcsubst cpp clang parser parsestructunionbody clang sourcelocation clang typespecifiertype clang recorddecl home john checkedc clang clang lib parse parsedecl cpp clang parser parseclassspecifier clang tok tokenkind clang sourcelocation clang declspec clang parser parsedtemplateinfo const clang accessspecifier bool clang parser declspeccontext clang parser parsedattributeswithrange home john checkedc clang clang lib parse parsedeclcxx cpp clang parser parsedeclarationspecifiers clang declspec clang parser parsedtemplateinfo const clang accessspecifier clang parser declspeccontext clang parser lateparsedattrlist home john checkedc clang clang lib parse parsedecl cpp clang parser parsedeclorfunctiondefinternal clang parser parsedattributeswithrange clang parsingdeclspec clang accessspecifier home john checkedc clang clang lib parse parser cpp clang parser parsedeclarationorfunctiondefinition clang parser parsedattributeswithrange clang parsingdeclspec clang accessspecifier home john checkedc clang clang lib parse parser cpp clang parser parseexternaldeclaration clang parser parsedattributeswithrange clang parsingdeclspec localalias home john checkedc clang clang lib parse parser cpp clang parser parsetopleveldecl clang opaqueptr bool home john checkedc clang clang lib parse parser cpp clang parseast clang sema bool bool home john checkedc clang clang lib parse parseast cpp clang astfrontendaction executeaction home john checkedc clang clang lib frontend frontendaction cpp clang codegenaction executeaction home john checkedc clang clang lib codegen codegenaction cpp clang frontendaction execute home john checkedc clang clang lib frontend frontendaction cpp clang compilerinstance executeaction clang frontendaction home john checkedc clang clang lib frontend compilerinstance cpp clang executecompilerinvocation clang compilerinstance home john checkedc clang clang lib frontendtool executecompilerinvocation cpp main llvm arrayref char const void home john checkedc clang clang tools driver main cpp llvm smallvectorimpl home john checkedc clang clang tools driver driver cpp clang driver execute llvm arrayref std basic string std allocator bool const lambda operator const home john checkedc clang clang lib driver job cpp void llvm function ref callback fn std basic string std allocator bool const lambda long home john checkedc clang llvm include llvm adt stlextras h llvm function ref operator const home john checkedc clang llvm build include llvm adt stlextras h llvm crashrecoverycontext runsafely llvm function ref home john checkedc clang llvm build lib support crashrecoverycontext cpp clang driver execute llvm arrayref std basic string std allocator bool const home john checkedc clang clang lib driver job cpp clang driver compilation executecommand clang driver command const clang driver command const const home john checkedc clang clang lib driver compilation cpp clang driver compilation executejobs clang driver joblist const llvm smallvectorimpl const home john checkedc clang clang lib driver compilation cpp clang driver driver executecompilation clang driver compilation llvm smallvectorimpl home john checkedc clang clang lib driver driver cpp main home john checkedc clang clang tools driver driver cpp libc start main build glibc glibc csu csu libc start c start home john checkedc clang llvm build bin clang the assertion fail goes away if i switch the order defining the generic struct first before declaring it without the for any it is also fixed if the pre declaration declares the struct with the generic struct hash for any k presumably this related to the unfinished work on generic structs for issue
| 0
|
58,129
| 14,239,579,168
|
IssuesEvent
|
2020-11-18 20:21:23
|
CDH-Studio/I-Talent
|
https://api.github.com/repos/CDH-Studio/I-Talent
|
closed
|
ASC-10 DATA IN TRANSIT
|
security control
|
**ID:** ASC-10 DATA IN TRANSIT
**Description**
Data in transit, or data in motion, is data actively moving from one location to another such as across the internet or through a private network. Data protection in transit is the protection of this data while it’s traveling from network to network or being transferred from a local storage device to a cloud storage device – wherever data is moving, effective data protection measures for in transit data are critical as data is often considered less secure while in motion.
Data Protection in Transit Best Practices
1. Use HTTPS Everywhere
a. Ideally, HTTPS should be used for your entire application. If you have to limit where it's used, then HTTPS must be applied to any authentication pages as well as to all pages after the user is authenticated. If sensitive information (e.g. personal information) can be submitted before authentication, those features must also be sent over HTTPS.
2. Disable HTTP Access for All Protected Resources
a. For all pages requiring protection by HTTPS, the same URL should not be accessible via the insecure HTTP channel.
3. Use the Strict-Transport-Security Header (HSTS)
a. The Strict-Transport-Security header ensures that the browser does not talk to the server over HTTP. This helps reduce the risk of HTTP downgrade attacks as implemented by the sslsniff tool.
4. Securely Exchange Encryption Keys
a. If encryption keys are exchanged or pre-set in your application then any key establishment or exchange must be performed over a secure channel
5. Disable Weak TLS Configuration on Servers
a. Weak ciphers must be disabled on all servers. For example, SSL v2, SSL v3, and TLS protocols prior to 1.2 have known weaknesses and are not considered secure.
b. Disable the NULL, RC4, DES, and MD5 cipher suites.
c. Ensure all key lengths are greater than 128 bits, use secure renegotiation, and disable compression.
6. Using an encrypted channel (SSL/TLS) to send and receive data protects against eavesdropping attacks.
a. It prevents an attacker from intercepting sensitive information such as usernames, passwords, session IDs, and login forms. It also guards against cross-site request forgery.
b. Secure the transmission from browser to web app / web app to other resources internal or external.
c. Secure “inter-zone traffic” when data comes from a less restricted zone to a higher restricted zone
d. Secure transmission of credentials.
** Protecting only the login process or highly sensitive transactions is a good start. However, what many applications fail to protect are session IDs, which are just as sensitive as username and password. Only protecting the login but then transmitting the protected data over insecure channel doesn’t do much good when an attacker read it off the wire.
Sources / References:
1. Cryptographic Algorithms for Unclassified, Protected A, and Protected B information (https://www.cse-cst.gc.ca/en/node/1831/html/26515)
2. Securing Web Application Technologies [SWAT] Checklist https://software-security.sans.org/resources/swat
3. HTTP Strict Transport Security Cheat Sheet (https://www.owasp.org/index.php/HTTP_Strict_Transport_Security_Cheat_Sheet)
4. Guidance on security configuring network protocols (https://www.cse-cst.gc.ca/en/node/1830/html/26507)
**Evidence Required**
Please provide:
1. Documentation explaining the data in transit protection strategy
The documentation must identify:
- When does the application force the use of HTTPS?
- Does the application use HSTS to enforce HTTPS when necessary?
- Describe how encryption keys are managed and protected?
- Are the secure and HttpOnly flags set in the cookies?
2. Quality Assurance (QA) tests report
a. Qualys tool
b. ssl scanner
3. Pen testing report
|
True
|
ASC-10 DATA IN TRANSIT - **ID:** ASC-10 DATA IN TRANSIT
**Description**
Data in transit, or data in motion, is data actively moving from one location to another such as across the internet or through a private network. Data protection in transit is the protection of this data while it’s traveling from network to network or being transferred from a local storage device to a cloud storage device – wherever data is moving, effective data protection measures for in transit data are critical as data is often considered less secure while in motion.
Data Protection in Transit Best Practices
1. Use HTTPS Everywhere
a. Ideally, HTTPS should be used for your entire application. If you have to limit where it's used, then HTTPS must be applied to any authentication pages as well as to all pages after the user is authenticated. If sensitive information (e.g. personal information) can be submitted before authentication, those features must also be sent over HTTPS.
2. Disable HTTP Access for All Protected Resources
a. For all pages requiring protection by HTTPS, the same URL should not be accessible via the insecure HTTP channel.
3. Use the Strict-Transport-Security Header (HSTS)
a. The Strict-Transport-Security header ensures that the browser does not talk to the server over HTTP. This helps reduce the risk of HTTP downgrade attacks as implemented by the sslsniff tool.
4. Securely Exchange Encryption Keys
a. If encryption keys are exchanged or pre-set in your application then any key establishment or exchange must be performed over a secure channel
5. Disable Weak TLS Configuration on Servers
a. Weak ciphers must be disabled on all servers. For example, SSL v2, SSL v3, and TLS protocols prior to 1.2 have known weaknesses and are not considered secure.
b. Disable the NULL, RC4, DES, and MD5 cipher suites.
c. Ensure all key lengths are greater than 128 bits, use secure renegotiation, and disable compression.
6. Using an encrypted channel (SSL/TLS) to send and receive data protects against eavesdropping attacks.
a. It prevents an attacker from intercepting sensitive information such as usernames, passwords, session IDs, and login forms. It also guards against cross-site request forgery.
b. Secure the transmission from browser to web app / web app to other resources internal or external.
c. Secure “inter-zone traffic” when data comes from a less restricted zone to a higher restricted zone
d. Secure transmission of credentials.
** Protecting only the login process or highly sensitive transactions is a good start. However, what many applications fail to protect are session IDs, which are just as sensitive as username and password. Only protecting the login but then transmitting the protected data over insecure channel doesn’t do much good when an attacker read it off the wire.
Sources / References:
1. Cryptographic Algorithms for Unclassified, Protected A, and Protected B information (https://www.cse-cst.gc.ca/en/node/1831/html/26515)
2. Securing Web Application Technologies [SWAT] Checklist https://software-security.sans.org/resources/swat
3. HTTP Strict Transport Security Cheat Sheet (https://www.owasp.org/index.php/HTTP_Strict_Transport_Security_Cheat_Sheet)
4. Guidance on security configuring network protocols (https://www.cse-cst.gc.ca/en/node/1830/html/26507)
**Evidence Required**
Please provide:
1. Documentation explaining the data in transit protection strategy
The documentation must identify:
- When does the application force the use of HTTPS?
- Does the application use HSTS to enforce HTTPS when necessary?
- Describe how encryption keys are managed and protected?
- Are the secure and HttpOnly flags set in the cookies?
2. Quality Assurance (QA) tests report
a. Qualys tool
b. ssl scanner
3. Pen testing report
|
secu
|
asc data in transit id asc data in transit description data in transit or data in motion is data actively moving from one location to another such as across the internet or through a private network data protection in transit is the protection of this data while it’s traveling from network to network or being transferred from a local storage device to a cloud storage device – wherever data is moving effective data protection measures for in transit data are critical as data is often considered less secure while in motion data protection in transit best practices use https everywhere a ideally https should be used for your entire application if you have to limit where it s used then https must be applied to any authentication pages as well as to all pages after the user is authenticated if sensitive information e g personal information can be submitted before authentication those features must also be sent over https disable http access for all protected resources a for all pages requiring protection by https the same url should not be accessible via the insecure http channel use the strict transport security header hsts a the strict transport security header ensures that the browser does not talk to the server over http this helps reduce the risk of http downgrade attacks as implemented by the sslsniff tool securely exchange encryption keys a if encryption keys are exchanged or pre set in your application then any key establishment or exchange must be performed over a secure channel disable weak tls configuration on servers a weak ciphers must be disabled on all servers for example ssl ssl and tls protocols prior to have known weaknesses and are not considered secure b disable the null des and cipher suites c ensure all key lengths are greater than bits use secure renegotiation and disable compression using an encrypted channel ssl tls to send and receive data protects against eavesdropping attacks a it prevents an attacker from intercepting sensitive information such as usernames passwords session ids and login forms it also guards against cross site request forgery b secure the transmission from browser to web app web app to other resources internal or external c secure “inter zone traffic” when data comes from a less restricted zone to a higher restricted zone d secure transmission of credentials protecting only the login process or highly sensitive transactions is a good start however what many applications fail to protect are session ids which are just as sensitive as username and password only protecting the login but then transmitting the protected data over insecure channel doesn’t do much good when an attacker read it off the wire sources references cryptographic algorithms for unclassified protected a and protected b information securing web application technologies checklist http strict transport security cheat sheet guidance on security configuring network protocols evidence required please provide documentation explaining the data in transit protection strategy the documentation must identify when does the application force the use of https does the application use hsts to enforce https when necessary describe how encryption keys are managed and protected are the secure and httponly flags set in the cookies quality assurance qa tests report a qualys tool b ssl scanner pen testing report
| 1
|
238,204
| 18,235,640,224
|
IssuesEvent
|
2021-10-01 06:26:02
|
microsoftgraph/microsoft-graph-docs
|
https://api.github.com/repos/microsoftgraph/microsoft-graph-docs
|
closed
|
Misleading description of return value
|
area: teams bug: documentation teams: TACO MSTeams-Developer-Support
|
Using this API endpoint does not return team resource as hinted in the team resource link at the top of the article ("Get the teams in Microsoft Teams ..."), but rather an object (a group object with extra properties?) containing only displayName, description, id and isArchived.
Attempts to expand other team specific properties such as "webUrl" results in the following 400 error: "Could not find a property named 'webUrl' on type 'microsoft.graph.group'."
---
#### Document Details
⚠ *Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.*
* ID: b4878b58-31d9-f8e1-ed30-2316c5f9ca15
* Version Independent ID: 1dcb5dda-2a45-77e1-bbe1-46ec24b33eec
* Content: [List joinedTeams - Microsoft Graph beta](https://docs.microsoft.com/en-us/graph/api/user-list-joinedteams?view=graph-rest-beta#feedback)
* Content Source: [api-reference/beta/api/user-list-joinedteams.md](https://github.com/microsoftgraph/microsoft-graph-docs/blob/master/api-reference/beta/api/user-list-joinedteams.md)
* Product: **microsoft-identity-platform**
* Technology: **microsoft-graph**
* GitHub Login: @dkershaw10
* Microsoft Alias: **MSGraphDocsVteam**
|
1.0
|
Misleading description of return value - Using this API endpoint does not return team resource as hinted in the team resource link at the top of the article ("Get the teams in Microsoft Teams ..."), but rather an object (a group object with extra properties?) containing only displayName, description, id and isArchived.
Attempts to expand other team specific properties such as "webUrl" results in the following 400 error: "Could not find a property named 'webUrl' on type 'microsoft.graph.group'."
---
#### Document Details
⚠ *Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.*
* ID: b4878b58-31d9-f8e1-ed30-2316c5f9ca15
* Version Independent ID: 1dcb5dda-2a45-77e1-bbe1-46ec24b33eec
* Content: [List joinedTeams - Microsoft Graph beta](https://docs.microsoft.com/en-us/graph/api/user-list-joinedteams?view=graph-rest-beta#feedback)
* Content Source: [api-reference/beta/api/user-list-joinedteams.md](https://github.com/microsoftgraph/microsoft-graph-docs/blob/master/api-reference/beta/api/user-list-joinedteams.md)
* Product: **microsoft-identity-platform**
* Technology: **microsoft-graph**
* GitHub Login: @dkershaw10
* Microsoft Alias: **MSGraphDocsVteam**
|
non_secu
|
misleading description of return value using this api endpoint does not return team resource as hinted in the team resource link at the top of the article get the teams in microsoft teams but rather an object a group object with extra properties containing only displayname description id and isarchived attempts to expand other team specific properties such as weburl results in the following error could not find a property named weburl on type microsoft graph group document details ⚠ do not edit this section it is required for docs microsoft com ➟ github issue linking id version independent id content content source product microsoft identity platform technology microsoft graph github login microsoft alias msgraphdocsvteam
| 0
|
142,605
| 19,099,369,080
|
IssuesEvent
|
2021-11-29 20:27:36
|
harrinry/stream-chat-react
|
https://api.github.com/repos/harrinry/stream-chat-react
|
opened
|
CVE-2021-23362 (Medium) detected in hosted-git-info-2.8.8.tgz, hosted-git-info-3.0.7.tgz
|
security vulnerability
|
## CVE-2021-23362 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>hosted-git-info-2.8.8.tgz</b>, <b>hosted-git-info-3.0.7.tgz</b></p></summary>
<p>
<details><summary><b>hosted-git-info-2.8.8.tgz</b></p></summary>
<p>Provides metadata and conversions from repository urls for Github, Bitbucket and Gitlab</p>
<p>Library home page: <a href="https://registry.npmjs.org/hosted-git-info/-/hosted-git-info-2.8.8.tgz">https://registry.npmjs.org/hosted-git-info/-/hosted-git-info-2.8.8.tgz</a></p>
<p>Path to dependency file: stream-chat-react/package.json</p>
<p>Path to vulnerable library: stream-chat-react/node_modules/hosted-git-info/package.json</p>
<p>
Dependency Hierarchy:
- stylelint-13.8.0.tgz (Root Library)
- meow-8.0.0.tgz
- read-pkg-up-7.0.1.tgz
- read-pkg-5.2.0.tgz
- normalize-package-data-2.5.0.tgz
- :x: **hosted-git-info-2.8.8.tgz** (Vulnerable Library)
</details>
<details><summary><b>hosted-git-info-3.0.7.tgz</b></p></summary>
<p>Provides metadata and conversions from repository urls for Github, Bitbucket and Gitlab</p>
<p>Library home page: <a href="https://registry.npmjs.org/hosted-git-info/-/hosted-git-info-3.0.7.tgz">https://registry.npmjs.org/hosted-git-info/-/hosted-git-info-3.0.7.tgz</a></p>
<p>Path to dependency file: stream-chat-react/package.json</p>
<p>Path to vulnerable library: stream-chat-react/node_modules/hosted-git-info/package.json</p>
<p>
Dependency Hierarchy:
- stylelint-13.8.0.tgz (Root Library)
- meow-8.0.0.tgz
- normalize-package-data-3.0.0.tgz
- :x: **hosted-git-info-3.0.7.tgz** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/harrinry/stream-chat-react/commit/a80df0ece7581dc566b7c05d5f5ae6ecc66b730f">a80df0ece7581dc566b7c05d5f5ae6ecc66b730f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
The package hosted-git-info before 3.0.8 are vulnerable to Regular Expression Denial of Service (ReDoS) via regular expression shortcutMatch in the fromUrl function in index.js. The affected regular expression exhibits polynomial worst-case time complexity.
<p>Publish Date: 2021-03-23
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-23362>CVE-2021-23362</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/advisories/GHSA-43f8-2h32-f4cj">https://github.com/advisories/GHSA-43f8-2h32-f4cj</a></p>
<p>Release Date: 2021-03-23</p>
<p>Fix Resolution: hosted-git-info - 2.8.9,3.0.8</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":false,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"hosted-git-info","packageVersion":"2.8.8","packageFilePaths":["/package.json"],"isTransitiveDependency":true,"dependencyTree":"stylelint:13.8.0;meow:8.0.0;read-pkg-up:7.0.1;read-pkg:5.2.0;normalize-package-data:2.5.0;hosted-git-info:2.8.8","isMinimumFixVersionAvailable":true,"minimumFixVersion":"hosted-git-info - 2.8.9,3.0.8","isBinary":false},{"packageType":"javascript/Node.js","packageName":"hosted-git-info","packageVersion":"3.0.7","packageFilePaths":["/package.json"],"isTransitiveDependency":true,"dependencyTree":"stylelint:13.8.0;meow:8.0.0;normalize-package-data:3.0.0;hosted-git-info:3.0.7","isMinimumFixVersionAvailable":true,"minimumFixVersion":"hosted-git-info - 2.8.9,3.0.8","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2021-23362","vulnerabilityDetails":"The package hosted-git-info before 3.0.8 are vulnerable to Regular Expression Denial of Service (ReDoS) via regular expression shortcutMatch in the fromUrl function in index.js. The affected regular expression exhibits polynomial worst-case time complexity.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-23362","cvss3Severity":"medium","cvss3Score":"5.3","cvss3Metrics":{"A":"Low","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}}</REMEDIATE> -->
|
True
|
CVE-2021-23362 (Medium) detected in hosted-git-info-2.8.8.tgz, hosted-git-info-3.0.7.tgz - ## CVE-2021-23362 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>hosted-git-info-2.8.8.tgz</b>, <b>hosted-git-info-3.0.7.tgz</b></p></summary>
<p>
<details><summary><b>hosted-git-info-2.8.8.tgz</b></p></summary>
<p>Provides metadata and conversions from repository urls for Github, Bitbucket and Gitlab</p>
<p>Library home page: <a href="https://registry.npmjs.org/hosted-git-info/-/hosted-git-info-2.8.8.tgz">https://registry.npmjs.org/hosted-git-info/-/hosted-git-info-2.8.8.tgz</a></p>
<p>Path to dependency file: stream-chat-react/package.json</p>
<p>Path to vulnerable library: stream-chat-react/node_modules/hosted-git-info/package.json</p>
<p>
Dependency Hierarchy:
- stylelint-13.8.0.tgz (Root Library)
- meow-8.0.0.tgz
- read-pkg-up-7.0.1.tgz
- read-pkg-5.2.0.tgz
- normalize-package-data-2.5.0.tgz
- :x: **hosted-git-info-2.8.8.tgz** (Vulnerable Library)
</details>
<details><summary><b>hosted-git-info-3.0.7.tgz</b></p></summary>
<p>Provides metadata and conversions from repository urls for Github, Bitbucket and Gitlab</p>
<p>Library home page: <a href="https://registry.npmjs.org/hosted-git-info/-/hosted-git-info-3.0.7.tgz">https://registry.npmjs.org/hosted-git-info/-/hosted-git-info-3.0.7.tgz</a></p>
<p>Path to dependency file: stream-chat-react/package.json</p>
<p>Path to vulnerable library: stream-chat-react/node_modules/hosted-git-info/package.json</p>
<p>
Dependency Hierarchy:
- stylelint-13.8.0.tgz (Root Library)
- meow-8.0.0.tgz
- normalize-package-data-3.0.0.tgz
- :x: **hosted-git-info-3.0.7.tgz** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/harrinry/stream-chat-react/commit/a80df0ece7581dc566b7c05d5f5ae6ecc66b730f">a80df0ece7581dc566b7c05d5f5ae6ecc66b730f</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
The package hosted-git-info before 3.0.8 are vulnerable to Regular Expression Denial of Service (ReDoS) via regular expression shortcutMatch in the fromUrl function in index.js. The affected regular expression exhibits polynomial worst-case time complexity.
<p>Publish Date: 2021-03-23
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-23362>CVE-2021-23362</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/advisories/GHSA-43f8-2h32-f4cj">https://github.com/advisories/GHSA-43f8-2h32-f4cj</a></p>
<p>Release Date: 2021-03-23</p>
<p>Fix Resolution: hosted-git-info - 2.8.9,3.0.8</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":false,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"hosted-git-info","packageVersion":"2.8.8","packageFilePaths":["/package.json"],"isTransitiveDependency":true,"dependencyTree":"stylelint:13.8.0;meow:8.0.0;read-pkg-up:7.0.1;read-pkg:5.2.0;normalize-package-data:2.5.0;hosted-git-info:2.8.8","isMinimumFixVersionAvailable":true,"minimumFixVersion":"hosted-git-info - 2.8.9,3.0.8","isBinary":false},{"packageType":"javascript/Node.js","packageName":"hosted-git-info","packageVersion":"3.0.7","packageFilePaths":["/package.json"],"isTransitiveDependency":true,"dependencyTree":"stylelint:13.8.0;meow:8.0.0;normalize-package-data:3.0.0;hosted-git-info:3.0.7","isMinimumFixVersionAvailable":true,"minimumFixVersion":"hosted-git-info - 2.8.9,3.0.8","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2021-23362","vulnerabilityDetails":"The package hosted-git-info before 3.0.8 are vulnerable to Regular Expression Denial of Service (ReDoS) via regular expression shortcutMatch in the fromUrl function in index.js. The affected regular expression exhibits polynomial worst-case time complexity.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-23362","cvss3Severity":"medium","cvss3Score":"5.3","cvss3Metrics":{"A":"Low","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}}</REMEDIATE> -->
|
secu
|
cve medium detected in hosted git info tgz hosted git info tgz cve medium severity vulnerability vulnerable libraries hosted git info tgz hosted git info tgz hosted git info tgz provides metadata and conversions from repository urls for github bitbucket and gitlab library home page a href path to dependency file stream chat react package json path to vulnerable library stream chat react node modules hosted git info package json dependency hierarchy stylelint tgz root library meow tgz read pkg up tgz read pkg tgz normalize package data tgz x hosted git info tgz vulnerable library hosted git info tgz provides metadata and conversions from repository urls for github bitbucket and gitlab library home page a href path to dependency file stream chat react package json path to vulnerable library stream chat react node modules hosted git info package json dependency hierarchy stylelint tgz root library meow tgz normalize package data tgz x hosted git info tgz vulnerable library found in head commit a href found in base branch master vulnerability details the package hosted git info before are vulnerable to regular expression denial of service redos via regular expression shortcutmatch in the fromurl function in index js the affected regular expression exhibits polynomial worst case time complexity publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact low for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution hosted git info isopenpronvulnerability false ispackagebased true isdefaultbranch true packages istransitivedependency true dependencytree stylelint meow read pkg up read pkg normalize package data hosted git info isminimumfixversionavailable true minimumfixversion hosted git info isbinary false packagetype javascript node js packagename hosted git info packageversion packagefilepaths istransitivedependency true dependencytree stylelint meow normalize package data hosted git info isminimumfixversionavailable true minimumfixversion hosted git info isbinary false basebranches vulnerabilityidentifier cve vulnerabilitydetails the package hosted git info before are vulnerable to regular expression denial of service redos via regular expression shortcutmatch in the fromurl function in index js the affected regular expression exhibits polynomial worst case time complexity vulnerabilityurl
| 1
|
74,528
| 15,350,274,958
|
IssuesEvent
|
2021-03-01 01:56:10
|
bitbar/test-samples
|
https://api.github.com/repos/bitbar/test-samples
|
closed
|
WS-2019-0425 (Medium) detected in mocha-5.2.0.tgz, mocha-3.5.3.tgz
|
closing security vulnerability
|
## WS-2019-0425 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>mocha-5.2.0.tgz</b>, <b>mocha-3.5.3.tgz</b></p></summary>
<p>
<details><summary><b>mocha-5.2.0.tgz</b></p></summary>
<p>simple, flexible, fun test framework</p>
<p>Library home page: <a href="https://registry.npmjs.org/mocha/-/mocha-5.2.0.tgz">https://registry.npmjs.org/mocha/-/mocha-5.2.0.tgz</a></p>
<p>Path to dependency file: test-samples/samples/testing-frameworks/detox/react-native/package.json</p>
<p>Path to vulnerable library: test-samples/samples/testing-frameworks/detox/react-native/node_modules/mocha/package.json</p>
<p>
Dependency Hierarchy:
- :x: **mocha-5.2.0.tgz** (Vulnerable Library)
</details>
<details><summary><b>mocha-3.5.3.tgz</b></p></summary>
<p>simple, flexible, fun test framework</p>
<p>Library home page: <a href="https://registry.npmjs.org/mocha/-/mocha-3.5.3.tgz">https://registry.npmjs.org/mocha/-/mocha-3.5.3.tgz</a></p>
<p>Path to dependency file: test-samples/samples/testing-frameworks/detox/react-native/package.json</p>
<p>Path to vulnerable library: test-samples/samples/testing-frameworks/detox/react-native/node_modules/mocha-jenkins-reporter/node_modules/mocha/package.json</p>
<p>
Dependency Hierarchy:
- mocha-jenkins-reporter-0.3.12.tgz (Root Library)
- :x: **mocha-3.5.3.tgz** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/bitbar/test-samples/commit/12af4f854b64888df6e4492ecc94e141388e939a">12af4f854b64888df6e4492ecc94e141388e939a</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Mocha is vulnerable to ReDoS attack. If the stack trace in utils.js begins with a large error message, and full-trace is not enabled, utils.stackTraceFilter() will take exponential run time.
<p>Publish Date: 2019-01-24
<p>URL: <a href=https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559>WS-2019-0425</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="v6.0.0">v6.0.0</a></p>
<p>Release Date: 2020-05-07</p>
<p>Fix Resolution: https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":false,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"mocha","packageVersion":"5.2.0","isTransitiveDependency":false,"dependencyTree":"mocha:5.2.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559"},{"packageType":"javascript/Node.js","packageName":"mocha","packageVersion":"3.5.3","isTransitiveDependency":true,"dependencyTree":"mocha-jenkins-reporter:0.3.12;mocha:3.5.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559"}],"vulnerabilityIdentifier":"WS-2019-0425","vulnerabilityDetails":"Mocha is vulnerable to ReDoS attack. If the stack trace in utils.js begins with a large error message, and full-trace is not enabled, utils.stackTraceFilter() will take exponential run time.","vulnerabilityUrl":"https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559","cvss3Severity":"medium","cvss3Score":"5.3","cvss3Metrics":{"A":"Low","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}}</REMEDIATE> -->
|
True
|
WS-2019-0425 (Medium) detected in mocha-5.2.0.tgz, mocha-3.5.3.tgz - ## WS-2019-0425 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>mocha-5.2.0.tgz</b>, <b>mocha-3.5.3.tgz</b></p></summary>
<p>
<details><summary><b>mocha-5.2.0.tgz</b></p></summary>
<p>simple, flexible, fun test framework</p>
<p>Library home page: <a href="https://registry.npmjs.org/mocha/-/mocha-5.2.0.tgz">https://registry.npmjs.org/mocha/-/mocha-5.2.0.tgz</a></p>
<p>Path to dependency file: test-samples/samples/testing-frameworks/detox/react-native/package.json</p>
<p>Path to vulnerable library: test-samples/samples/testing-frameworks/detox/react-native/node_modules/mocha/package.json</p>
<p>
Dependency Hierarchy:
- :x: **mocha-5.2.0.tgz** (Vulnerable Library)
</details>
<details><summary><b>mocha-3.5.3.tgz</b></p></summary>
<p>simple, flexible, fun test framework</p>
<p>Library home page: <a href="https://registry.npmjs.org/mocha/-/mocha-3.5.3.tgz">https://registry.npmjs.org/mocha/-/mocha-3.5.3.tgz</a></p>
<p>Path to dependency file: test-samples/samples/testing-frameworks/detox/react-native/package.json</p>
<p>Path to vulnerable library: test-samples/samples/testing-frameworks/detox/react-native/node_modules/mocha-jenkins-reporter/node_modules/mocha/package.json</p>
<p>
Dependency Hierarchy:
- mocha-jenkins-reporter-0.3.12.tgz (Root Library)
- :x: **mocha-3.5.3.tgz** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/bitbar/test-samples/commit/12af4f854b64888df6e4492ecc94e141388e939a">12af4f854b64888df6e4492ecc94e141388e939a</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Mocha is vulnerable to ReDoS attack. If the stack trace in utils.js begins with a large error message, and full-trace is not enabled, utils.stackTraceFilter() will take exponential run time.
<p>Publish Date: 2019-01-24
<p>URL: <a href=https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559>WS-2019-0425</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="v6.0.0">v6.0.0</a></p>
<p>Release Date: 2020-05-07</p>
<p>Fix Resolution: https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":false,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"mocha","packageVersion":"5.2.0","isTransitiveDependency":false,"dependencyTree":"mocha:5.2.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559"},{"packageType":"javascript/Node.js","packageName":"mocha","packageVersion":"3.5.3","isTransitiveDependency":true,"dependencyTree":"mocha-jenkins-reporter:0.3.12;mocha:3.5.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559"}],"vulnerabilityIdentifier":"WS-2019-0425","vulnerabilityDetails":"Mocha is vulnerable to ReDoS attack. If the stack trace in utils.js begins with a large error message, and full-trace is not enabled, utils.stackTraceFilter() will take exponential run time.","vulnerabilityUrl":"https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559","cvss3Severity":"medium","cvss3Score":"5.3","cvss3Metrics":{"A":"Low","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}}</REMEDIATE> -->
|
secu
|
ws medium detected in mocha tgz mocha tgz ws medium severity vulnerability vulnerable libraries mocha tgz mocha tgz mocha tgz simple flexible fun test framework library home page a href path to dependency file test samples samples testing frameworks detox react native package json path to vulnerable library test samples samples testing frameworks detox react native node modules mocha package json dependency hierarchy x mocha tgz vulnerable library mocha tgz simple flexible fun test framework library home page a href path to dependency file test samples samples testing frameworks detox react native package json path to vulnerable library test samples samples testing frameworks detox react native node modules mocha jenkins reporter node modules mocha package json dependency hierarchy mocha jenkins reporter tgz root library x mocha tgz vulnerable library found in head commit a href found in base branch master vulnerability details mocha is vulnerable to redos attack if the stack trace in utils js begins with a large error message and full trace is not enabled utils stacktracefilter will take exponential run time publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact low for more information on scores click a href suggested fix type upgrade version origin release date fix resolution isopenpronvulnerability false ispackagebased true isdefaultbranch true packages vulnerabilityidentifier ws vulnerabilitydetails mocha is vulnerable to redos attack if the stack trace in utils js begins with a large error message and full trace is not enabled utils stacktracefilter will take exponential run time vulnerabilityurl
| 1
|
229,229
| 25,306,550,500
|
IssuesEvent
|
2022-11-17 14:33:54
|
Sultan-Dev-Readonly-Org/Baragon-WSD-2004
|
https://api.github.com/repos/Sultan-Dev-Readonly-Org/Baragon-WSD-2004
|
opened
|
jackson-databind-2.9.9.jar: 48 vulnerabilities (highest severity is: 9.8)
|
security vulnerability
|
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p></details>
## Vulnerabilities
| CVE | Severity | <img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS | Dependency | Type | Fixed in (jackson-databind version) | Remediation Available |
| ------------- | ------------- | ----- | ----- | ----- | ------------- | --- |
| [CVE-2019-14540](https://www.mend.io/vulnerability-database/CVE-2019-14540) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-8840](https://www.mend.io/vulnerability-database/CVE-2020-8840) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2019-16942](https://www.mend.io/vulnerability-database/CVE-2019-16942) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00002 | ✅ |
| [CVE-2019-16943](https://www.mend.io/vulnerability-database/CVE-2019-16943) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00002 | ✅ |
| [CVE-2019-17531](https://www.mend.io/vulnerability-database/CVE-2019-17531) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00002 | ✅ |
| [CVE-2019-16335](https://www.mend.io/vulnerability-database/CVE-2019-16335) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.9.3-redhat-00001 | ✅ |
| [CVE-2019-14893](https://www.mend.io/vulnerability-database/CVE-2019-14893) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10 | ✅ |
| [CVE-2019-14892](https://www.mend.io/vulnerability-database/CVE-2019-14892) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.9.3-redhat-00001 | ✅ |
| [CVE-2020-9546](https://www.mend.io/vulnerability-database/CVE-2020-9546) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2019-14379](https://www.mend.io/vulnerability-database/CVE-2019-14379) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.9.2 | ✅ |
| [CVE-2019-17267](https://www.mend.io/vulnerability-database/CVE-2019-17267) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.9.3-redhat-00001 | ✅ |
| [CVE-2020-9547](https://www.mend.io/vulnerability-database/CVE-2020-9547) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-9548](https://www.mend.io/vulnerability-database/CVE-2020-9548) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2019-20330](https://www.mend.io/vulnerability-database/CVE-2019-20330) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-11111](https://www.mend.io/vulnerability-database/CVE-2020-11111) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-11113](https://www.mend.io/vulnerability-database/CVE-2020-11113) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-11112](https://www.mend.io/vulnerability-database/CVE-2020-11112) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-10968](https://www.mend.io/vulnerability-database/CVE-2020-10968) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.9.jar | Direct | 2.9.9.redhat-00001 | ✅ |
| [CVE-2020-10969](https://www.mend.io/vulnerability-database/CVE-2020-10969) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-10672](https://www.mend.io/vulnerability-database/CVE-2020-10672) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-10673](https://www.mend.io/vulnerability-database/CVE-2020-10673) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2021-20190](https://www.mend.io/vulnerability-database/CVE-2021-20190) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36179](https://www.mend.io/vulnerability-database/CVE-2020-36179) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-24616](https://www.mend.io/vulnerability-database/CVE-2020-24616) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-14060](https://www.mend.io/vulnerability-database/CVE-2020-14060) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-14061](https://www.mend.io/vulnerability-database/CVE-2020-14061) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-14062](https://www.mend.io/vulnerability-database/CVE-2020-14062) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-24750](https://www.mend.io/vulnerability-database/CVE-2020-24750) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-11619](https://www.mend.io/vulnerability-database/CVE-2020-11619) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-35728](https://www.mend.io/vulnerability-database/CVE-2020-35728) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36189](https://www.mend.io/vulnerability-database/CVE-2020-36189) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36188](https://www.mend.io/vulnerability-database/CVE-2020-36188) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-11620](https://www.mend.io/vulnerability-database/CVE-2020-11620) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36181](https://www.mend.io/vulnerability-database/CVE-2020-36181) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-14195](https://www.mend.io/vulnerability-database/CVE-2020-14195) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36180](https://www.mend.io/vulnerability-database/CVE-2020-36180) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-35490](https://www.mend.io/vulnerability-database/CVE-2020-35490) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36183](https://www.mend.io/vulnerability-database/CVE-2020-36183) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36182](https://www.mend.io/vulnerability-database/CVE-2020-36182) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36185](https://www.mend.io/vulnerability-database/CVE-2020-36185) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36184](https://www.mend.io/vulnerability-database/CVE-2020-36184) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-35491](https://www.mend.io/vulnerability-database/CVE-2020-35491) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36187](https://www.mend.io/vulnerability-database/CVE-2020-36187) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36186](https://www.mend.io/vulnerability-database/CVE-2020-36186) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-25649](https://www.mend.io/vulnerability-database/CVE-2020-25649) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2019-14439](https://www.mend.io/vulnerability-database/CVE-2019-14439) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | jackson-databind-2.9.9.jar | Direct | 2.9.9.2 | ✅ |
| [CVE-2019-12384](https://www.mend.io/vulnerability-database/CVE-2019-12384) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 5.9 | jackson-databind-2.9.9.jar | Direct | 2.9.9.1 | ✅ |
| [CVE-2019-12814](https://www.mend.io/vulnerability-database/CVE-2019-12814) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 5.9 | jackson-databind-2.9.9.jar | Direct | 2.9.9.redhat-00001 | ✅ |
## Details
> Partial details (21 vulnerabilities) are displayed below due to a content size limitation in GitHub. To view information on the remaining vulnerabilities, navigate to the Mend Application.<br>
<details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-14540</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind before 2.9.10. It is related to com.zaxxer.hikari.HikariConfig.
<p>Publish Date: 2019-09-15
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14540>CVE-2019-14540</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14540">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14540</a></p>
<p>Release Date: 2019-09-15</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-8840</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.0.0 through 2.9.10.2 lacks certain xbean-reflect/JNDI blocking, as demonstrated by org.apache.xbean.propertyeditor.JndiConverter.
<p>Publish Date: 2020-02-10
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-8840>CVE-2020-8840</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-02-10</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-16942</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.0.0 through 2.9.10. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint and the service has the commons-dbcp (1.4) jar in the classpath, and an attacker can find an RMI service endpoint to access, it is possible to make the service execute a malicious payload. This issue exists because of org.apache.commons.dbcp.datasources.SharedPoolDataSource and org.apache.commons.dbcp.datasources.PerUserPoolDataSource mishandling.
<p>Publish Date: 2019-10-01
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-16942>CVE-2019-16942</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16942">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16942</a></p>
<p>Release Date: 2019-10-01</p>
<p>Fix Resolution: 2.9.10.redhat-00002</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-16943</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.0.0 through 2.9.10. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint and the service has the p6spy (3.8.6) jar in the classpath, and an attacker can find an RMI service endpoint to access, it is possible to make the service execute a malicious payload. This issue exists because of com.p6spy.engine.spy.P6DataSource mishandling.
<p>Publish Date: 2019-10-01
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-16943>CVE-2019-16943</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16943">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16943</a></p>
<p>Release Date: 2019-10-01</p>
<p>Fix Resolution: 2.9.10.redhat-00002</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-17531</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.0.0 through 2.9.10. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint and the service has the apache-log4j-extra (version 1.2.x) jar in the classpath, and an attacker can provide a JNDI service to access, it is possible to make the service execute a malicious payload.
<p>Publish Date: 2019-10-12
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-17531>CVE-2019-17531</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17531">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17531</a></p>
<p>Release Date: 2019-10-12</p>
<p>Fix Resolution: 2.9.10.redhat-00002</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-16335</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind before 2.9.10. It is related to com.zaxxer.hikari.HikariDataSource. This is a different vulnerability than CVE-2019-14540.
<p>Publish Date: 2019-09-15
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-16335>CVE-2019-16335</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2019-09-15</p>
<p>Fix Resolution: 2.9.9.3-redhat-00001</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-14893</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A flaw was discovered in FasterXML jackson-databind in all versions before 2.9.10 and 2.10.0, where it would permit polymorphic deserialization of malicious objects using the xalan JNDI gadget when used in conjunction with polymorphic type handling methods such as `enableDefaultTyping()` or when @JsonTypeInfo is using `Id.CLASS` or `Id.MINIMAL_CLASS` or in any other way which ObjectMapper.readValue might instantiate objects from unsafe sources. An attacker could use this flaw to execute arbitrary code.
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14893>CVE-2019-14893</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14893">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14893</a></p>
<p>Release Date: 2020-03-02</p>
<p>Fix Resolution: 2.9.10</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-14892</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A flaw was discovered in jackson-databind in versions before 2.9.10, 2.8.11.5 and 2.6.7.3, where it would permit polymorphic deserialization of a malicious object using commons-configuration 1 and 2 JNDI classes. An attacker could use this flaw to execute arbitrary code.
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14892>CVE-2019-14892</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-09-04</p>
<p>Fix Resolution: 2.9.9.3-redhat-00001</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-9546</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.hadoop.shaded.com.zaxxer.hikari.HikariConfig (aka shaded hikari-config).
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-9546>CVE-2020-9546</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9546">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9546</a></p>
<p>Release Date: 2020-03-02</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-14379</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
SubTypeValidator.java in FasterXML jackson-databind before 2.9.9.2 mishandles default typing when ehcache is used (because of net.sf.ehcache.transaction.manager.DefaultTransactionManagerLookup), leading to remote code execution.
<p>Publish Date: 2019-07-29
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14379>CVE-2019-14379</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14379">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14379</a></p>
<p>Release Date: 2019-07-29</p>
<p>Fix Resolution: 2.9.9.2</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-17267</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind before 2.9.10. It is related to net.sf.ehcache.hibernate.EhcacheJtaTransactionManagerLookup.
<p>Publish Date: 2019-10-07
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-17267>CVE-2019-17267</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2019-10-07</p>
<p>Fix Resolution: 2.9.9.3-redhat-00001</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-9547</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to com.ibatis.sqlmap.engine.transaction.jta.JtaTransactionConfig (aka ibatis-sqlmap).
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-9547>CVE-2020-9547</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9547">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9547</a></p>
<p>Release Date: 2020-03-02</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-9548</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to br.com.anteros.dbcp.AnterosDBCPConfig (aka anteros-core).
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-9548>CVE-2020-9548</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9548">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9548</a></p>
<p>Release Date: 2020-03-02</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-20330</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.2 lacks certain net.sf.ehcache blocking.
<p>Publish Date: 2020-01-03
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-20330>CVE-2019-20330</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-01-03</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-11111</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.activemq.* (aka activemq-jms, activemq-core, activemq-pool, and activemq-pool-jms).
<p>Publish Date: 2020-03-31
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-11111>CVE-2020-11111</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11113">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11113</a></p>
<p>Release Date: 2020-03-31</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-11113</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.openjpa.ee.WASRegistryManagedRuntime (aka openjpa).
<p>Publish Date: 2020-03-31
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-11113>CVE-2020-11113</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11113">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11113</a></p>
<p>Release Date: 2020-03-31</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-11112</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.commons.proxy.provider.remoting.RmiProvider (aka apache/commons-proxy).
<p>Publish Date: 2020-03-31
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-11112>CVE-2020-11112</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11112">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11112</a></p>
<p>Release Date: 2020-03-31</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-10968</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.aoju.bus.proxy.provider.remoting.RmiProvider (aka bus-proxy).
<p>Publish Date: 2020-03-26
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-10968>CVE-2020-10968</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2020-10968">https://nvd.nist.gov/vuln/detail/CVE-2020-10968</a></p>
<p>Release Date: 2020-03-26</p>
<p>Fix Resolution: 2.9.9.redhat-00001</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-10969</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to javax.swing.JEditorPane.
<p>Publish Date: 2020-03-26
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-10969>CVE-2020-10969</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-10969">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-10969</a></p>
<p>Release Date: 2020-03-26</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-10672</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.aries.transaction.jms.internal.XaPooledConnectionFactory (aka aries.transaction.jms).
<p>Publish Date: 2020-03-18
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-10672>CVE-2020-10672</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2020-10672">https://nvd.nist.gov/vuln/detail/CVE-2020-10672</a></p>
<p>Release Date: 2020-03-18</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-10673</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to com.caucho.config.types.ResourceRef (aka caucho-quercus).
<p>Publish Date: 2020-03-18
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-10673>CVE-2020-10673</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-03-18</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details>
***
<p>:rescue_worker_helmet: Automatic Remediation is available for this issue.</p>
|
True
|
jackson-databind-2.9.9.jar: 48 vulnerabilities (highest severity is: 9.8) - <details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p></details>
## Vulnerabilities
| CVE | Severity | <img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS | Dependency | Type | Fixed in (jackson-databind version) | Remediation Available |
| ------------- | ------------- | ----- | ----- | ----- | ------------- | --- |
| [CVE-2019-14540](https://www.mend.io/vulnerability-database/CVE-2019-14540) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-8840](https://www.mend.io/vulnerability-database/CVE-2020-8840) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2019-16942](https://www.mend.io/vulnerability-database/CVE-2019-16942) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00002 | ✅ |
| [CVE-2019-16943](https://www.mend.io/vulnerability-database/CVE-2019-16943) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00002 | ✅ |
| [CVE-2019-17531](https://www.mend.io/vulnerability-database/CVE-2019-17531) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00002 | ✅ |
| [CVE-2019-16335](https://www.mend.io/vulnerability-database/CVE-2019-16335) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.9.3-redhat-00001 | ✅ |
| [CVE-2019-14893](https://www.mend.io/vulnerability-database/CVE-2019-14893) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10 | ✅ |
| [CVE-2019-14892](https://www.mend.io/vulnerability-database/CVE-2019-14892) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.9.3-redhat-00001 | ✅ |
| [CVE-2020-9546](https://www.mend.io/vulnerability-database/CVE-2020-9546) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2019-14379](https://www.mend.io/vulnerability-database/CVE-2019-14379) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.9.2 | ✅ |
| [CVE-2019-17267](https://www.mend.io/vulnerability-database/CVE-2019-17267) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.9.3-redhat-00001 | ✅ |
| [CVE-2020-9547](https://www.mend.io/vulnerability-database/CVE-2020-9547) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-9548](https://www.mend.io/vulnerability-database/CVE-2020-9548) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2019-20330](https://www.mend.io/vulnerability-database/CVE-2019-20330) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 9.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-11111](https://www.mend.io/vulnerability-database/CVE-2020-11111) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-11113](https://www.mend.io/vulnerability-database/CVE-2020-11113) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-11112](https://www.mend.io/vulnerability-database/CVE-2020-11112) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-10968](https://www.mend.io/vulnerability-database/CVE-2020-10968) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.9.jar | Direct | 2.9.9.redhat-00001 | ✅ |
| [CVE-2020-10969](https://www.mend.io/vulnerability-database/CVE-2020-10969) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-10672](https://www.mend.io/vulnerability-database/CVE-2020-10672) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-10673](https://www.mend.io/vulnerability-database/CVE-2020-10673) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.8 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2021-20190](https://www.mend.io/vulnerability-database/CVE-2021-20190) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36179](https://www.mend.io/vulnerability-database/CVE-2020-36179) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-24616](https://www.mend.io/vulnerability-database/CVE-2020-24616) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-14060](https://www.mend.io/vulnerability-database/CVE-2020-14060) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-14061](https://www.mend.io/vulnerability-database/CVE-2020-14061) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-14062](https://www.mend.io/vulnerability-database/CVE-2020-14062) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-24750](https://www.mend.io/vulnerability-database/CVE-2020-24750) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-11619](https://www.mend.io/vulnerability-database/CVE-2020-11619) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-35728](https://www.mend.io/vulnerability-database/CVE-2020-35728) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36189](https://www.mend.io/vulnerability-database/CVE-2020-36189) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36188](https://www.mend.io/vulnerability-database/CVE-2020-36188) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-11620](https://www.mend.io/vulnerability-database/CVE-2020-11620) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36181](https://www.mend.io/vulnerability-database/CVE-2020-36181) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-14195](https://www.mend.io/vulnerability-database/CVE-2020-14195) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36180](https://www.mend.io/vulnerability-database/CVE-2020-36180) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-35490](https://www.mend.io/vulnerability-database/CVE-2020-35490) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36183](https://www.mend.io/vulnerability-database/CVE-2020-36183) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36182](https://www.mend.io/vulnerability-database/CVE-2020-36182) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36185](https://www.mend.io/vulnerability-database/CVE-2020-36185) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36184](https://www.mend.io/vulnerability-database/CVE-2020-36184) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-35491](https://www.mend.io/vulnerability-database/CVE-2020-35491) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36187](https://www.mend.io/vulnerability-database/CVE-2020-36187) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-36186](https://www.mend.io/vulnerability-database/CVE-2020-36186) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 8.1 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2020-25649](https://www.mend.io/vulnerability-database/CVE-2020-25649) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | jackson-databind-2.9.9.jar | Direct | 2.9.10.redhat-00005 | ✅ |
| [CVE-2019-14439](https://www.mend.io/vulnerability-database/CVE-2019-14439) | <img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> High | 7.5 | jackson-databind-2.9.9.jar | Direct | 2.9.9.2 | ✅ |
| [CVE-2019-12384](https://www.mend.io/vulnerability-database/CVE-2019-12384) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 5.9 | jackson-databind-2.9.9.jar | Direct | 2.9.9.1 | ✅ |
| [CVE-2019-12814](https://www.mend.io/vulnerability-database/CVE-2019-12814) | <img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Medium | 5.9 | jackson-databind-2.9.9.jar | Direct | 2.9.9.redhat-00001 | ✅ |
## Details
> Partial details (21 vulnerabilities) are displayed below due to a content size limitation in GitHub. To view information on the remaining vulnerabilities, navigate to the Mend Application.<br>
<details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-14540</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind before 2.9.10. It is related to com.zaxxer.hikari.HikariConfig.
<p>Publish Date: 2019-09-15
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14540>CVE-2019-14540</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14540">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14540</a></p>
<p>Release Date: 2019-09-15</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-8840</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.0.0 through 2.9.10.2 lacks certain xbean-reflect/JNDI blocking, as demonstrated by org.apache.xbean.propertyeditor.JndiConverter.
<p>Publish Date: 2020-02-10
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-8840>CVE-2020-8840</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-02-10</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-16942</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.0.0 through 2.9.10. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint and the service has the commons-dbcp (1.4) jar in the classpath, and an attacker can find an RMI service endpoint to access, it is possible to make the service execute a malicious payload. This issue exists because of org.apache.commons.dbcp.datasources.SharedPoolDataSource and org.apache.commons.dbcp.datasources.PerUserPoolDataSource mishandling.
<p>Publish Date: 2019-10-01
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-16942>CVE-2019-16942</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16942">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16942</a></p>
<p>Release Date: 2019-10-01</p>
<p>Fix Resolution: 2.9.10.redhat-00002</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-16943</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.0.0 through 2.9.10. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint and the service has the p6spy (3.8.6) jar in the classpath, and an attacker can find an RMI service endpoint to access, it is possible to make the service execute a malicious payload. This issue exists because of com.p6spy.engine.spy.P6DataSource mishandling.
<p>Publish Date: 2019-10-01
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-16943>CVE-2019-16943</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16943">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16943</a></p>
<p>Release Date: 2019-10-01</p>
<p>Fix Resolution: 2.9.10.redhat-00002</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-17531</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind 2.0.0 through 2.9.10. When Default Typing is enabled (either globally or for a specific property) for an externally exposed JSON endpoint and the service has the apache-log4j-extra (version 1.2.x) jar in the classpath, and an attacker can provide a JNDI service to access, it is possible to make the service execute a malicious payload.
<p>Publish Date: 2019-10-12
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-17531>CVE-2019-17531</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17531">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17531</a></p>
<p>Release Date: 2019-10-12</p>
<p>Fix Resolution: 2.9.10.redhat-00002</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-16335</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind before 2.9.10. It is related to com.zaxxer.hikari.HikariDataSource. This is a different vulnerability than CVE-2019-14540.
<p>Publish Date: 2019-09-15
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-16335>CVE-2019-16335</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2019-09-15</p>
<p>Fix Resolution: 2.9.9.3-redhat-00001</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-14893</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A flaw was discovered in FasterXML jackson-databind in all versions before 2.9.10 and 2.10.0, where it would permit polymorphic deserialization of malicious objects using the xalan JNDI gadget when used in conjunction with polymorphic type handling methods such as `enableDefaultTyping()` or when @JsonTypeInfo is using `Id.CLASS` or `Id.MINIMAL_CLASS` or in any other way which ObjectMapper.readValue might instantiate objects from unsafe sources. An attacker could use this flaw to execute arbitrary code.
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14893>CVE-2019-14893</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14893">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14893</a></p>
<p>Release Date: 2020-03-02</p>
<p>Fix Resolution: 2.9.10</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-14892</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A flaw was discovered in jackson-databind in versions before 2.9.10, 2.8.11.5 and 2.6.7.3, where it would permit polymorphic deserialization of a malicious object using commons-configuration 1 and 2 JNDI classes. An attacker could use this flaw to execute arbitrary code.
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14892>CVE-2019-14892</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-09-04</p>
<p>Fix Resolution: 2.9.9.3-redhat-00001</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-9546</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.hadoop.shaded.com.zaxxer.hikari.HikariConfig (aka shaded hikari-config).
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-9546>CVE-2020-9546</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9546">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9546</a></p>
<p>Release Date: 2020-03-02</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-14379</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
SubTypeValidator.java in FasterXML jackson-databind before 2.9.9.2 mishandles default typing when ehcache is used (because of net.sf.ehcache.transaction.manager.DefaultTransactionManagerLookup), leading to remote code execution.
<p>Publish Date: 2019-07-29
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14379>CVE-2019-14379</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14379">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14379</a></p>
<p>Release Date: 2019-07-29</p>
<p>Fix Resolution: 2.9.9.2</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-17267</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind before 2.9.10. It is related to net.sf.ehcache.hibernate.EhcacheJtaTransactionManagerLookup.
<p>Publish Date: 2019-10-07
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-17267>CVE-2019-17267</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2019-10-07</p>
<p>Fix Resolution: 2.9.9.3-redhat-00001</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-9547</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to com.ibatis.sqlmap.engine.transaction.jta.JtaTransactionConfig (aka ibatis-sqlmap).
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-9547>CVE-2020-9547</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9547">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9547</a></p>
<p>Release Date: 2020-03-02</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-9548</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to br.com.anteros.dbcp.AnterosDBCPConfig (aka anteros-core).
<p>Publish Date: 2020-03-02
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-9548>CVE-2020-9548</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9548">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-9548</a></p>
<p>Release Date: 2020-03-02</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2019-20330</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.2 lacks certain net.sf.ehcache blocking.
<p>Publish Date: 2020-01-03
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-20330>CVE-2019-20330</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>9.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-01-03</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-11111</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.activemq.* (aka activemq-jms, activemq-core, activemq-pool, and activemq-pool-jms).
<p>Publish Date: 2020-03-31
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-11111>CVE-2020-11111</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11113">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11113</a></p>
<p>Release Date: 2020-03-31</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-11113</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.openjpa.ee.WASRegistryManagedRuntime (aka openjpa).
<p>Publish Date: 2020-03-31
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-11113>CVE-2020-11113</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11113">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11113</a></p>
<p>Release Date: 2020-03-31</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-11112</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.commons.proxy.provider.remoting.RmiProvider (aka apache/commons-proxy).
<p>Publish Date: 2020-03-31
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-11112>CVE-2020-11112</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11112">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11112</a></p>
<p>Release Date: 2020-03-31</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-10968</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.aoju.bus.proxy.provider.remoting.RmiProvider (aka bus-proxy).
<p>Publish Date: 2020-03-26
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-10968>CVE-2020-10968</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2020-10968">https://nvd.nist.gov/vuln/detail/CVE-2020-10968</a></p>
<p>Release Date: 2020-03-26</p>
<p>Fix Resolution: 2.9.9.redhat-00001</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-10969</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to javax.swing.JEditorPane.
<p>Publish Date: 2020-03-26
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-10969>CVE-2020-10969</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-10969">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-10969</a></p>
<p>Release Date: 2020-03-26</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-10672</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to org.apache.aries.transaction.jms.internal.XaPooledConnectionFactory (aka aries.transaction.jms).
<p>Publish Date: 2020-03-18
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-10672>CVE-2020-10672</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2020-10672">https://nvd.nist.gov/vuln/detail/CVE-2020-10672</a></p>
<p>Release Date: 2020-03-18</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details><details>
<summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> CVE-2020-10673</summary>
### Vulnerable Library - <b>jackson-databind-2.9.9.jar</b></p>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /BaragonWatcher/pom.xml, /BaragonAgentService/pom.xml, /BaragonData/pom.xml, /BaragonClient/pom.xml, /BaragonCore/pom.xml, /BaragonService/pom.xml</p>
<p>Path to vulnerable library: /tory/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar, /home/wss-scanner/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.9/jackson-databind-2.9.9.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.9.9.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/Sultan-Dev-Readonly-Org/Baragon-WSD-2004/commit/cdd1bbe306a75a36e6e063dd440ce142a65ac159">cdd1bbe306a75a36e6e063dd440ce142a65ac159</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
<p></p>
### Vulnerability Details
<p>
FasterXML jackson-databind 2.x before 2.9.10.4 mishandles the interaction between serialization gadgets and typing, related to com.caucho.config.types.ResourceRef (aka caucho-quercus).
<p>Publish Date: 2020-03-18
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-10673>CVE-2020-10673</a></p>
</p>
<p></p>
### CVSS 3 Score Details (<b>8.8</b>)
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
<p></p>
### Suggested Fix
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-03-18</p>
<p>Fix Resolution: 2.9.10.redhat-00005</p>
</p>
<p></p>
:rescue_worker_helmet: Automatic Remediation is available for this issue
</details>
***
<p>:rescue_worker_helmet: Automatic Remediation is available for this issue.</p>
|
secu
|
jackson databind jar vulnerabilities highest severity is vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar found in head commit a href vulnerabilities cve severity cvss dependency type fixed in jackson databind version remediation available high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct redhat high jackson databind jar direct medium jackson databind jar direct medium jackson databind jar direct redhat details partial details vulnerabilities are displayed below due to a content size limitation in github to view information on the remaining vulnerabilities navigate to the mend application cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a polymorphic typing issue was discovered in fasterxml jackson databind before it is related to com zaxxer hikari hikariconfig publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind through lacks certain xbean reflect jndi blocking as demonstrated by org apache xbean propertyeditor jndiconverter publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a polymorphic typing issue was discovered in fasterxml jackson databind through when default typing is enabled either globally or for a specific property for an externally exposed json endpoint and the service has the commons dbcp jar in the classpath and an attacker can find an rmi service endpoint to access it is possible to make the service execute a malicious payload this issue exists because of org apache commons dbcp datasources sharedpooldatasource and org apache commons dbcp datasources peruserpooldatasource mishandling publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a polymorphic typing issue was discovered in fasterxml jackson databind through when default typing is enabled either globally or for a specific property for an externally exposed json endpoint and the service has the jar in the classpath and an attacker can find an rmi service endpoint to access it is possible to make the service execute a malicious payload this issue exists because of com engine spy mishandling publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a polymorphic typing issue was discovered in fasterxml jackson databind through when default typing is enabled either globally or for a specific property for an externally exposed json endpoint and the service has the apache extra version x jar in the classpath and an attacker can provide a jndi service to access it is possible to make the service execute a malicious payload publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a polymorphic typing issue was discovered in fasterxml jackson databind before it is related to com zaxxer hikari hikaridatasource this is a different vulnerability than cve publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a flaw was discovered in fasterxml jackson databind in all versions before and where it would permit polymorphic deserialization of malicious objects using the xalan jndi gadget when used in conjunction with polymorphic type handling methods such as enabledefaulttyping or when jsontypeinfo is using id class or id minimal class or in any other way which objectmapper readvalue might instantiate objects from unsafe sources an attacker could use this flaw to execute arbitrary code publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a flaw was discovered in jackson databind in versions before and where it would permit polymorphic deserialization of a malicious object using commons configuration and jndi classes an attacker could use this flaw to execute arbitrary code publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to org apache hadoop shaded com zaxxer hikari hikariconfig aka shaded hikari config publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details subtypevalidator java in fasterxml jackson databind before mishandles default typing when ehcache is used because of net sf ehcache transaction manager defaulttransactionmanagerlookup leading to remote code execution publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details a polymorphic typing issue was discovered in fasterxml jackson databind before it is related to net sf ehcache hibernate ehcachejtatransactionmanagerlookup publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to com ibatis sqlmap engine transaction jta jtatransactionconfig aka ibatis sqlmap publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to br com anteros dbcp anterosdbcpconfig aka anteros core publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before lacks certain net sf ehcache blocking publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to org apache activemq aka activemq jms activemq core activemq pool and activemq pool jms publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to org apache openjpa ee wasregistrymanagedruntime aka openjpa publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to org apache commons proxy provider remoting rmiprovider aka apache commons proxy publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to org aoju bus proxy provider remoting rmiprovider aka bus proxy publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to javax swing jeditorpane publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to org apache aries transaction jms internal xapooledconnectionfactory aka aries transaction jms publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue cve vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file baragonwatcher pom xml baragonagentservice pom xml baragondata pom xml baragonclient pom xml baragoncore pom xml baragonservice pom xml path to vulnerable library tory com fasterxml jackson core jackson databind jackson databind jar home wss scanner repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to com caucho config types resourceref aka caucho quercus publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution redhat rescue worker helmet automatic remediation is available for this issue rescue worker helmet automatic remediation is available for this issue
| 1
|
270,371
| 8,455,108,785
|
IssuesEvent
|
2018-10-21 11:45:02
|
vasyoid/cremebrulee
|
https://api.github.com/repos/vasyoid/cremebrulee
|
closed
|
Не обновляется аватарка пользователя
|
bug high priority medium importance
|
#### Описание
При смене пользовательского аватара, на странице пользователя показывается старый аватар.
#### Версия приложения
228.1337 (Android)
#### Шаги для воспроизведения
- Авторизируемся любым пользователем в Android-приложении
- Попадаем на страницу пользователя
- Заходим в настройки
- На странице настроек нажимаем на кнопку "загрузить" под аватаром
- Выбираем изображение
- На странице настроек нажимаем "выйти"
- Попадаем на страницу пользователя
#### Результат
На странице пользователя видим старое изображение
|
1.0
|
Не обновляется аватарка пользователя - #### Описание
При смене пользовательского аватара, на странице пользователя показывается старый аватар.
#### Версия приложения
228.1337 (Android)
#### Шаги для воспроизведения
- Авторизируемся любым пользователем в Android-приложении
- Попадаем на страницу пользователя
- Заходим в настройки
- На странице настроек нажимаем на кнопку "загрузить" под аватаром
- Выбираем изображение
- На странице настроек нажимаем "выйти"
- Попадаем на страницу пользователя
#### Результат
На странице пользователя видим старое изображение
|
non_secu
|
не обновляется аватарка пользователя описание при смене пользовательского аватара на странице пользователя показывается старый аватар версия приложения android шаги для воспроизведения авторизируемся любым пользователем в android приложении попадаем на страницу пользователя заходим в настройки на странице настроек нажимаем на кнопку загрузить под аватаром выбираем изображение на странице настроек нажимаем выйти попадаем на страницу пользователя результат на странице пользователя видим старое изображение
| 0
|
531,961
| 15,527,864,211
|
IssuesEvent
|
2021-03-13 08:13:20
|
containrrr/watchtower
|
https://api.github.com/repos/containrrr/watchtower
|
closed
|
Add MQTT and WebHook as notification options
|
Priority: Low Status: Available Type: Enhancement
|
I'd like to be able to monitor the status of container updates using Home Assistant. At present, this is very tricky to do.
Watchtower could easily achieve this if MQTT or Webhook's were added as notification options.
Like other notification options, these could easily be configured using the Env variables to specify the MQTT host, user, password, topic, etc. Or the Webhook address etc.
|
1.0
|
Add MQTT and WebHook as notification options - I'd like to be able to monitor the status of container updates using Home Assistant. At present, this is very tricky to do.
Watchtower could easily achieve this if MQTT or Webhook's were added as notification options.
Like other notification options, these could easily be configured using the Env variables to specify the MQTT host, user, password, topic, etc. Or the Webhook address etc.
|
non_secu
|
add mqtt and webhook as notification options i d like to be able to monitor the status of container updates using home assistant at present this is very tricky to do watchtower could easily achieve this if mqtt or webhook s were added as notification options like other notification options these could easily be configured using the env variables to specify the mqtt host user password topic etc or the webhook address etc
| 0
|
245,158
| 26,519,977,167
|
IssuesEvent
|
2023-01-19 01:08:00
|
n-devs/testTungTonScript
|
https://api.github.com/repos/n-devs/testTungTonScript
|
opened
|
CVE-2021-32803 (High) detected in tar-4.4.10.tgz
|
security vulnerability
|
## CVE-2021-32803 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>tar-4.4.10.tgz</b></p></summary>
<p>tar for node</p>
<p>Library home page: <a href="https://registry.npmjs.org/tar/-/tar-4.4.10.tgz">https://registry.npmjs.org/tar/-/tar-4.4.10.tgz</a></p>
<p>Path to dependency file: /testTungTonScript/package.json</p>
<p>Path to vulnerable library: /node_modules/tar/package.json</p>
<p>
Dependency Hierarchy:
- react-native-scripts-1.13.1.tgz (Root Library)
- xdl-48.1.4.tgz
- :x: **tar-4.4.10.tgz** (Vulnerable Library)
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
The npm package "tar" (aka node-tar) before versions 6.1.2, 5.0.7, 4.4.15, and 3.2.3 has an arbitrary File Creation/Overwrite vulnerability via insufficient symlink protection. `node-tar` aims to guarantee that any file whose location would be modified by a symbolic link is not extracted. This is, in part, achieved by ensuring that extracted directories are not symlinks. Additionally, in order to prevent unnecessary `stat` calls to determine whether a given path is a directory, paths are cached when directories are created. This logic was insufficient when extracting tar files that contained both a directory and a symlink with the same name as the directory. This order of operations resulted in the directory being created and added to the `node-tar` directory cache. When a directory is present in the directory cache, subsequent calls to mkdir for that directory are skipped. However, this is also where `node-tar` checks for symlinks occur. By first creating a directory, and then replacing that directory with a symlink, it was thus possible to bypass `node-tar` symlink checks on directories, essentially allowing an untrusted tar file to symlink into an arbitrary location and subsequently extracting arbitrary files into that location, thus allowing arbitrary file creation and overwrite. This issue was addressed in releases 3.2.3, 4.4.15, 5.0.7 and 6.1.2.
<p>Publish Date: 2021-08-03
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2021-32803>CVE-2021-32803</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>8.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/npm/node-tar/security/advisories/GHSA-r628-mhmh-qjhw">https://github.com/npm/node-tar/security/advisories/GHSA-r628-mhmh-qjhw</a></p>
<p>Release Date: 2021-08-03</p>
<p>Fix Resolution (tar): 4.4.15</p>
<p>Direct dependency fix Resolution (react-native-scripts): 1.13.2</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2021-32803 (High) detected in tar-4.4.10.tgz - ## CVE-2021-32803 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>tar-4.4.10.tgz</b></p></summary>
<p>tar for node</p>
<p>Library home page: <a href="https://registry.npmjs.org/tar/-/tar-4.4.10.tgz">https://registry.npmjs.org/tar/-/tar-4.4.10.tgz</a></p>
<p>Path to dependency file: /testTungTonScript/package.json</p>
<p>Path to vulnerable library: /node_modules/tar/package.json</p>
<p>
Dependency Hierarchy:
- react-native-scripts-1.13.1.tgz (Root Library)
- xdl-48.1.4.tgz
- :x: **tar-4.4.10.tgz** (Vulnerable Library)
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
The npm package "tar" (aka node-tar) before versions 6.1.2, 5.0.7, 4.4.15, and 3.2.3 has an arbitrary File Creation/Overwrite vulnerability via insufficient symlink protection. `node-tar` aims to guarantee that any file whose location would be modified by a symbolic link is not extracted. This is, in part, achieved by ensuring that extracted directories are not symlinks. Additionally, in order to prevent unnecessary `stat` calls to determine whether a given path is a directory, paths are cached when directories are created. This logic was insufficient when extracting tar files that contained both a directory and a symlink with the same name as the directory. This order of operations resulted in the directory being created and added to the `node-tar` directory cache. When a directory is present in the directory cache, subsequent calls to mkdir for that directory are skipped. However, this is also where `node-tar` checks for symlinks occur. By first creating a directory, and then replacing that directory with a symlink, it was thus possible to bypass `node-tar` symlink checks on directories, essentially allowing an untrusted tar file to symlink into an arbitrary location and subsequently extracting arbitrary files into that location, thus allowing arbitrary file creation and overwrite. This issue was addressed in releases 3.2.3, 4.4.15, 5.0.7 and 6.1.2.
<p>Publish Date: 2021-08-03
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2021-32803>CVE-2021-32803</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>8.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/npm/node-tar/security/advisories/GHSA-r628-mhmh-qjhw">https://github.com/npm/node-tar/security/advisories/GHSA-r628-mhmh-qjhw</a></p>
<p>Release Date: 2021-08-03</p>
<p>Fix Resolution (tar): 4.4.15</p>
<p>Direct dependency fix Resolution (react-native-scripts): 1.13.2</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve high detected in tar tgz cve high severity vulnerability vulnerable library tar tgz tar for node library home page a href path to dependency file testtungtonscript package json path to vulnerable library node modules tar package json dependency hierarchy react native scripts tgz root library xdl tgz x tar tgz vulnerable library vulnerability details the npm package tar aka node tar before versions and has an arbitrary file creation overwrite vulnerability via insufficient symlink protection node tar aims to guarantee that any file whose location would be modified by a symbolic link is not extracted this is in part achieved by ensuring that extracted directories are not symlinks additionally in order to prevent unnecessary stat calls to determine whether a given path is a directory paths are cached when directories are created this logic was insufficient when extracting tar files that contained both a directory and a symlink with the same name as the directory this order of operations resulted in the directory being created and added to the node tar directory cache when a directory is present in the directory cache subsequent calls to mkdir for that directory are skipped however this is also where node tar checks for symlinks occur by first creating a directory and then replacing that directory with a symlink it was thus possible to bypass node tar symlink checks on directories essentially allowing an untrusted tar file to symlink into an arbitrary location and subsequently extracting arbitrary files into that location thus allowing arbitrary file creation and overwrite this issue was addressed in releases and publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact none integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution tar direct dependency fix resolution react native scripts step up your open source security game with mend
| 1
|
75,704
| 14,515,689,573
|
IssuesEvent
|
2020-12-13 13:19:43
|
languagetool-org/languagetool
|
https://api.github.com/repos/languagetool-org/languagetool
|
opened
|
[de] bad spelling suggestions "freit"
|
German code/java
|
Maybe because "freit" is in `prohibit.txt`?
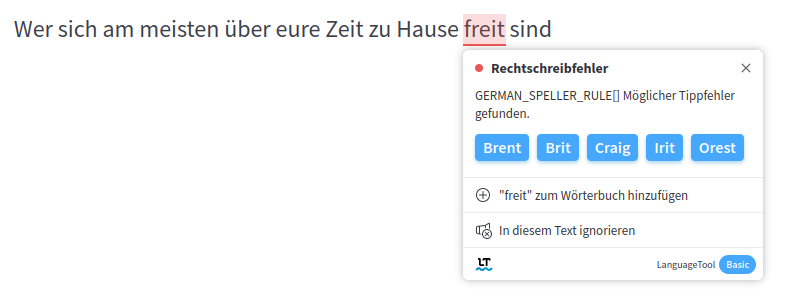
-> top suggestion should be "freut"
|
1.0
|
[de] bad spelling suggestions "freit" - Maybe because "freit" is in `prohibit.txt`?

-> top suggestion should be "freut"
|
non_secu
|
bad spelling suggestions freit maybe because freit is in prohibit txt top suggestion should be freut
| 0
|
84,185
| 10,483,191,018
|
IssuesEvent
|
2019-09-24 13:33:53
|
ethereum/ethereum-org-website
|
https://api.github.com/repos/ethereum/ethereum-org-website
|
closed
|
Establish consistent font hierarchy
|
design wip
|
- Homepage section titles should be headers (`<h2>`?), not `<li>`
- Every page should have an `<h1>` - all header titles should be `<h1>` not `<h2>`
- Headers & HTML elements should have consistent size
- e.g. `<h1>` on /developers has custom styling to display like an `<h2>`!?
|
1.0
|
Establish consistent font hierarchy - - Homepage section titles should be headers (`<h2>`?), not `<li>`
- Every page should have an `<h1>` - all header titles should be `<h1>` not `<h2>`
- Headers & HTML elements should have consistent size
- e.g. `<h1>` on /developers has custom styling to display like an `<h2>`!?
|
non_secu
|
establish consistent font hierarchy homepage section titles should be headers not every page should have an all header titles should be not headers html elements should have consistent size e g on developers has custom styling to display like an
| 0
|
140,910
| 18,927,436,605
|
IssuesEvent
|
2021-11-17 11:01:48
|
sultanabubaker/Rem_Ren_Test
|
https://api.github.com/repos/sultanabubaker/Rem_Ren_Test
|
opened
|
WS-2019-0331 (Medium) detected in handlebars-4.0.10.tgz
|
security vulnerability
|
## WS-2019-0331 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>handlebars-4.0.10.tgz</b></p></summary>
<p>Handlebars provides the power necessary to let you build semantic templates effectively with no frustration</p>
<p>Library home page: <a href="https://registry.npmjs.org/handlebars/-/handlebars-4.0.10.tgz">https://registry.npmjs.org/handlebars/-/handlebars-4.0.10.tgz</a></p>
<p>Path to dependency file: Rem_Ren_Test/package.json</p>
<p>Path to vulnerable library: /node_modules/handlebars/package.json</p>
<p>
Dependency Hierarchy:
- :x: **handlebars-4.0.10.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sultanabubaker/Rem_Ren_Test/commit/60f3742ac7e0785171a0979516de0ea7cd6d1cbb">60f3742ac7e0785171a0979516de0ea7cd6d1cbb</a></p>
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Arbitrary Code Execution vulnerability found in handlebars before 4.5.2. Lookup helper fails to validate templates. Attack may submit templates that execute arbitrary JavaScript in the system.
<p>Publish Date: 2019-11-13
<p>URL: <a href=https://github.com/wycats/handlebars.js/commit/d54137810a49939fd2ad01a91a34e182ece4528e>WS-2019-0331</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 2 Score Details (<b>5.0</b>)</summary>
<p>
Base Score Metrics not available</p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/advisories/1316">https://www.npmjs.com/advisories/1316</a></p>
<p>Release Date: 2019-11-13</p>
<p>Fix Resolution: handlebars - 4.5.2</p>
</p>
</details>
<p></p>
***
<!-- REMEDIATE-OPEN-PR-START -->
- [ ] Check this box to open an automated fix PR
<!-- REMEDIATE-OPEN-PR-END -->
<!-- <REMEDIATE>{"isOpenPROnVulnerability":false,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"handlebars","packageVersion":"4.0.10","packageFilePaths":["/package.json"],"isTransitiveDependency":false,"dependencyTree":"handlebars:4.0.10","isMinimumFixVersionAvailable":true,"minimumFixVersion":"handlebars - 4.5.2"}],"baseBranches":["main"],"vulnerabilityIdentifier":"WS-2019-0331","vulnerabilityDetails":"Arbitrary Code Execution vulnerability found in handlebars before 4.5.2. Lookup helper fails to validate templates. Attack may submit templates that execute arbitrary JavaScript in the system.","vulnerabilityUrl":"https://github.com/wycats/handlebars.js/commit/d54137810a49939fd2ad01a91a34e182ece4528e","cvss2Severity":"medium","cvss2Score":"5.0","extraData":{}}</REMEDIATE> -->
|
True
|
WS-2019-0331 (Medium) detected in handlebars-4.0.10.tgz - ## WS-2019-0331 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>handlebars-4.0.10.tgz</b></p></summary>
<p>Handlebars provides the power necessary to let you build semantic templates effectively with no frustration</p>
<p>Library home page: <a href="https://registry.npmjs.org/handlebars/-/handlebars-4.0.10.tgz">https://registry.npmjs.org/handlebars/-/handlebars-4.0.10.tgz</a></p>
<p>Path to dependency file: Rem_Ren_Test/package.json</p>
<p>Path to vulnerable library: /node_modules/handlebars/package.json</p>
<p>
Dependency Hierarchy:
- :x: **handlebars-4.0.10.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/sultanabubaker/Rem_Ren_Test/commit/60f3742ac7e0785171a0979516de0ea7cd6d1cbb">60f3742ac7e0785171a0979516de0ea7cd6d1cbb</a></p>
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Arbitrary Code Execution vulnerability found in handlebars before 4.5.2. Lookup helper fails to validate templates. Attack may submit templates that execute arbitrary JavaScript in the system.
<p>Publish Date: 2019-11-13
<p>URL: <a href=https://github.com/wycats/handlebars.js/commit/d54137810a49939fd2ad01a91a34e182ece4528e>WS-2019-0331</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 2 Score Details (<b>5.0</b>)</summary>
<p>
Base Score Metrics not available</p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/advisories/1316">https://www.npmjs.com/advisories/1316</a></p>
<p>Release Date: 2019-11-13</p>
<p>Fix Resolution: handlebars - 4.5.2</p>
</p>
</details>
<p></p>
***
<!-- REMEDIATE-OPEN-PR-START -->
- [ ] Check this box to open an automated fix PR
<!-- REMEDIATE-OPEN-PR-END -->
<!-- <REMEDIATE>{"isOpenPROnVulnerability":false,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"handlebars","packageVersion":"4.0.10","packageFilePaths":["/package.json"],"isTransitiveDependency":false,"dependencyTree":"handlebars:4.0.10","isMinimumFixVersionAvailable":true,"minimumFixVersion":"handlebars - 4.5.2"}],"baseBranches":["main"],"vulnerabilityIdentifier":"WS-2019-0331","vulnerabilityDetails":"Arbitrary Code Execution vulnerability found in handlebars before 4.5.2. Lookup helper fails to validate templates. Attack may submit templates that execute arbitrary JavaScript in the system.","vulnerabilityUrl":"https://github.com/wycats/handlebars.js/commit/d54137810a49939fd2ad01a91a34e182ece4528e","cvss2Severity":"medium","cvss2Score":"5.0","extraData":{}}</REMEDIATE> -->
|
secu
|
ws medium detected in handlebars tgz ws medium severity vulnerability vulnerable library handlebars tgz handlebars provides the power necessary to let you build semantic templates effectively with no frustration library home page a href path to dependency file rem ren test package json path to vulnerable library node modules handlebars package json dependency hierarchy x handlebars tgz vulnerable library found in head commit a href found in base branch main vulnerability details arbitrary code execution vulnerability found in handlebars before lookup helper fails to validate templates attack may submit templates that execute arbitrary javascript in the system publish date url a href cvss score details base score metrics not available suggested fix type upgrade version origin a href release date fix resolution handlebars check this box to open an automated fix pr isopenpronvulnerability false ispackagebased true isdefaultbranch true packages istransitivedependency false dependencytree handlebars isminimumfixversionavailable true minimumfixversion handlebars basebranches vulnerabilityidentifier ws vulnerabilitydetails arbitrary code execution vulnerability found in handlebars before lookup helper fails to validate templates attack may submit templates that execute arbitrary javascript in the system vulnerabilityurl
| 1
|
478,040
| 13,771,787,016
|
IssuesEvent
|
2020-10-07 22:47:33
|
metabase/metabase
|
https://api.github.com/repos/metabase/metabase
|
closed
|
0.37-rc1: empty click behavior sidebar when dealing with a dashboard card displaying an error
|
Priority:P2 Type:Bug
|
When dealing with a dashboard card displaying the error message, "There was a problem displaying this chart," the click behavior sidebar is empty, only showing the title "On-click behavior for each column."
|
1.0
|
0.37-rc1: empty click behavior sidebar when dealing with a dashboard card displaying an error - When dealing with a dashboard card displaying the error message, "There was a problem displaying this chart," the click behavior sidebar is empty, only showing the title "On-click behavior for each column."
|
non_secu
|
empty click behavior sidebar when dealing with a dashboard card displaying an error when dealing with a dashboard card displaying the error message there was a problem displaying this chart the click behavior sidebar is empty only showing the title on click behavior for each column
| 0
|
159,684
| 20,085,892,320
|
IssuesEvent
|
2022-02-05 01:07:55
|
AkshayMukkavilli/Analyzing-the-Significance-of-Structure-in-Amazon-Review-Data-Using-Machine-Learning-Approaches
|
https://api.github.com/repos/AkshayMukkavilli/Analyzing-the-Significance-of-Structure-in-Amazon-Review-Data-Using-Machine-Learning-Approaches
|
opened
|
CVE-2021-41204 (Medium) detected in tensorflow-1.13.1-cp27-cp27mu-manylinux1_x86_64.whl
|
security vulnerability
|
## CVE-2021-41204 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>tensorflow-1.13.1-cp27-cp27mu-manylinux1_x86_64.whl</b></p></summary>
<p>TensorFlow is an open source machine learning framework for everyone.</p>
<p>Library home page: <a href="https://files.pythonhosted.org/packages/d2/ea/ab2c8c0e81bd051cc1180b104c75a865ab0fc66c89be992c4b20bbf6d624/tensorflow-1.13.1-cp27-cp27mu-manylinux1_x86_64.whl">https://files.pythonhosted.org/packages/d2/ea/ab2c8c0e81bd051cc1180b104c75a865ab0fc66c89be992c4b20bbf6d624/tensorflow-1.13.1-cp27-cp27mu-manylinux1_x86_64.whl</a></p>
<p>Path to dependency file: /FinalProject/requirements.txt</p>
<p>Path to vulnerable library: /teSource-ArchiveExtractor_8b9e071c-3b11-4aa9-ba60-cdeb60d053b7/20190525011350_65403/20190525011256_depth_0/9/tensorflow-1.13.1-cp27-cp27mu-manylinux1_x86_64/tensorflow-1.13.1.data/purelib/tensorflow</p>
<p>
Dependency Hierarchy:
- :x: **tensorflow-1.13.1-cp27-cp27mu-manylinux1_x86_64.whl** (Vulnerable Library)
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
TensorFlow is an open source platform for machine learning. In affected versions during TensorFlow's Grappler optimizer phase, constant folding might attempt to deep copy a resource tensor. This results in a segfault, as these tensors are supposed to not change. The fix will be included in TensorFlow 2.7.0. We will also cherrypick this commit on TensorFlow 2.6.1, TensorFlow 2.5.2, and TensorFlow 2.4.4, as these are also affected and still in supported range.
<p>Publish Date: 2021-11-05
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-41204>CVE-2021-41204</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/tensorflow/tensorflow/security/advisories/GHSA-786j-5qwq-r36x">https://github.com/tensorflow/tensorflow/security/advisories/GHSA-786j-5qwq-r36x</a></p>
<p>Release Date: 2021-11-05</p>
<p>Fix Resolution: tensorflow - 2.4.4, 2.5.2, 2.6.1, 2.7.0;tensorflow-cpu - 2.4.4, 2.5.2, 2.6.1, 2.7.0;tensorflow-gpu - 2.4.4, 2.5.2, 2.6.1, 2.7.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2021-41204 (Medium) detected in tensorflow-1.13.1-cp27-cp27mu-manylinux1_x86_64.whl - ## CVE-2021-41204 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>tensorflow-1.13.1-cp27-cp27mu-manylinux1_x86_64.whl</b></p></summary>
<p>TensorFlow is an open source machine learning framework for everyone.</p>
<p>Library home page: <a href="https://files.pythonhosted.org/packages/d2/ea/ab2c8c0e81bd051cc1180b104c75a865ab0fc66c89be992c4b20bbf6d624/tensorflow-1.13.1-cp27-cp27mu-manylinux1_x86_64.whl">https://files.pythonhosted.org/packages/d2/ea/ab2c8c0e81bd051cc1180b104c75a865ab0fc66c89be992c4b20bbf6d624/tensorflow-1.13.1-cp27-cp27mu-manylinux1_x86_64.whl</a></p>
<p>Path to dependency file: /FinalProject/requirements.txt</p>
<p>Path to vulnerable library: /teSource-ArchiveExtractor_8b9e071c-3b11-4aa9-ba60-cdeb60d053b7/20190525011350_65403/20190525011256_depth_0/9/tensorflow-1.13.1-cp27-cp27mu-manylinux1_x86_64/tensorflow-1.13.1.data/purelib/tensorflow</p>
<p>
Dependency Hierarchy:
- :x: **tensorflow-1.13.1-cp27-cp27mu-manylinux1_x86_64.whl** (Vulnerable Library)
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
TensorFlow is an open source platform for machine learning. In affected versions during TensorFlow's Grappler optimizer phase, constant folding might attempt to deep copy a resource tensor. This results in a segfault, as these tensors are supposed to not change. The fix will be included in TensorFlow 2.7.0. We will also cherrypick this commit on TensorFlow 2.6.1, TensorFlow 2.5.2, and TensorFlow 2.4.4, as these are also affected and still in supported range.
<p>Publish Date: 2021-11-05
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-41204>CVE-2021-41204</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/tensorflow/tensorflow/security/advisories/GHSA-786j-5qwq-r36x">https://github.com/tensorflow/tensorflow/security/advisories/GHSA-786j-5qwq-r36x</a></p>
<p>Release Date: 2021-11-05</p>
<p>Fix Resolution: tensorflow - 2.4.4, 2.5.2, 2.6.1, 2.7.0;tensorflow-cpu - 2.4.4, 2.5.2, 2.6.1, 2.7.0;tensorflow-gpu - 2.4.4, 2.5.2, 2.6.1, 2.7.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve medium detected in tensorflow whl cve medium severity vulnerability vulnerable library tensorflow whl tensorflow is an open source machine learning framework for everyone library home page a href path to dependency file finalproject requirements txt path to vulnerable library tesource archiveextractor depth tensorflow tensorflow data purelib tensorflow dependency hierarchy x tensorflow whl vulnerable library vulnerability details tensorflow is an open source platform for machine learning in affected versions during tensorflow s grappler optimizer phase constant folding might attempt to deep copy a resource tensor this results in a segfault as these tensors are supposed to not change the fix will be included in tensorflow we will also cherrypick this commit on tensorflow tensorflow and tensorflow as these are also affected and still in supported range publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required low user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution tensorflow tensorflow cpu tensorflow gpu step up your open source security game with whitesource
| 1
|
8,823
| 7,457,017,821
|
IssuesEvent
|
2018-03-30 01:14:51
|
s-newman/skitter
|
https://api.github.com/repos/s-newman/skitter
|
closed
|
Picture Processing
|
required security
|
When users upload profile pictures, we will have to process them to ensure that they aren't trying to sneak in anything malicious. This should be done before reaching the microservices.
|
True
|
Picture Processing - When users upload profile pictures, we will have to process them to ensure that they aren't trying to sneak in anything malicious. This should be done before reaching the microservices.
|
secu
|
picture processing when users upload profile pictures we will have to process them to ensure that they aren t trying to sneak in anything malicious this should be done before reaching the microservices
| 1
|
799,381
| 28,305,698,868
|
IssuesEvent
|
2023-04-10 10:46:17
|
bounswe/bounswe2023group8
|
https://api.github.com/repos/bounswe/bounswe2023group8
|
opened
|
Implementing Milestone 1 Report to Wiki
|
type: wiki type: improvement status: to-do priority: high effort: low
|
As the Milestone 1 Report is set with the #65, we need to implement the missing chapters of the report to related wiki page.
|
1.0
|
Implementing Milestone 1 Report to Wiki - As the Milestone 1 Report is set with the #65, we need to implement the missing chapters of the report to related wiki page.
|
non_secu
|
implementing milestone report to wiki as the milestone report is set with the we need to implement the missing chapters of the report to related wiki page
| 0
|
178,917
| 6,620,046,048
|
IssuesEvent
|
2017-09-21 14:22:02
|
robotology/yarp
|
https://api.github.com/repos/robotology/yarp
|
closed
|
yarp devel is not configuring if YCM 0.4.0 is installed in the system
|
Component: CMake Fixed in: YARP 2.3.72 Priority: High Resolution: Fixed
|
I have `ycm` installed from homebrew, and the latest YARP devel is not configuring with this error:
~~~
CMake Error at /usr/local/share/YCM/modules/AddInstallRPATHSupport.cmake:137 (file):
file RELATIVE_PATH must be passed a full path to the directory:
INSTALL_NAME_DIR
Call Stack (most recent call first):
cmake/YarpOptions.cmake:359 (add_install_rpath_support)
CMakeLists.txt:63 (include)
~~~
|
1.0
|
yarp devel is not configuring if YCM 0.4.0 is installed in the system - I have `ycm` installed from homebrew, and the latest YARP devel is not configuring with this error:
~~~
CMake Error at /usr/local/share/YCM/modules/AddInstallRPATHSupport.cmake:137 (file):
file RELATIVE_PATH must be passed a full path to the directory:
INSTALL_NAME_DIR
Call Stack (most recent call first):
cmake/YarpOptions.cmake:359 (add_install_rpath_support)
CMakeLists.txt:63 (include)
~~~
|
non_secu
|
yarp devel is not configuring if ycm is installed in the system i have ycm installed from homebrew and the latest yarp devel is not configuring with this error cmake error at usr local share ycm modules addinstallrpathsupport cmake file file relative path must be passed a full path to the directory install name dir call stack most recent call first cmake yarpoptions cmake add install rpath support cmakelists txt include
| 0
|
42,439
| 12,891,413,604
|
IssuesEvent
|
2020-07-13 17:41:21
|
jtimberlake/jazz
|
https://api.github.com/repos/jtimberlake/jazz
|
opened
|
WS-2019-0425 (Medium) detected in multiple libraries
|
security vulnerability
|
## WS-2019-0425 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>mocha-3.5.3.tgz</b>, <b>mocha-4.1.0.tgz</b>, <b>mocha-5.2.0.tgz</b></p></summary>
<p>
<details><summary><b>mocha-3.5.3.tgz</b></p></summary>
<p>simple, flexible, fun test framework</p>
<p>Library home page: <a href="https://registry.npmjs.org/mocha/-/mocha-3.5.3.tgz">https://registry.npmjs.org/mocha/-/mocha-3.5.3.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/jazz/templates/sls-app-template-nodejs/package.json</p>
<p>Path to vulnerable library: /jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json</p>
<p>
Dependency Hierarchy:
- :x: **mocha-3.5.3.tgz** (Vulnerable Library)
</details>
<details><summary><b>mocha-4.1.0.tgz</b></p></summary>
<p>simple, flexible, fun test framework</p>
<p>Library home page: <a href="https://registry.npmjs.org/mocha/-/mocha-4.1.0.tgz">https://registry.npmjs.org/mocha/-/mocha-4.1.0.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/jazz/core/jazz_is-service-available/package.json</p>
<p>Path to vulnerable library: /jazz/core/jazz_is-service-available/node_modules/mocha/package.json</p>
<p>
Dependency Hierarchy:
- :x: **mocha-4.1.0.tgz** (Vulnerable Library)
</details>
<details><summary><b>mocha-5.2.0.tgz</b></p></summary>
<p>simple, flexible, fun test framework</p>
<p>Library home page: <a href="https://registry.npmjs.org/mocha/-/mocha-5.2.0.tgz">https://registry.npmjs.org/mocha/-/mocha-5.2.0.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/jazz/core/jazz_metrics/package.json</p>
<p>Path to vulnerable library: /jazz/core/jazz_metrics/node_modules/mocha/package.json</p>
<p>
Dependency Hierarchy:
- :x: **mocha-5.2.0.tgz** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/jtimberlake/jazz/commit/f31a850168fa59ceb2dfbdfb70a04c1bbe9b9fec">f31a850168fa59ceb2dfbdfb70a04c1bbe9b9fec</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Mocha is vulnerable to ReDoS attack. If the stack trace in utils.js begins with a large error message, and full-trace is not enabled, utils.stackTraceFilter() will take exponential run time.
<p>Publish Date: 2019-01-24
<p>URL: <a href=https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559>WS-2019-0425</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="v6.0.0">v6.0.0</a></p>
<p>Release Date: 2020-05-07</p>
<p>Fix Resolution: https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":false,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"mocha","packageVersion":"3.5.3","isTransitiveDependency":false,"dependencyTree":"mocha:3.5.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559"},{"packageType":"javascript/Node.js","packageName":"mocha","packageVersion":"4.1.0","isTransitiveDependency":false,"dependencyTree":"mocha:4.1.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559"},{"packageType":"javascript/Node.js","packageName":"mocha","packageVersion":"5.2.0","isTransitiveDependency":false,"dependencyTree":"mocha:5.2.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559"}],"vulnerabilityIdentifier":"WS-2019-0425","vulnerabilityDetails":"Mocha is vulnerable to ReDoS attack. If the stack trace in utils.js begins with a large error message, and full-trace is not enabled, utils.stackTraceFilter() will take exponential run time.","vulnerabilityUrl":"https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559","cvss3Severity":"medium","cvss3Score":"5.3","cvss3Metrics":{"A":"Low","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}}</REMEDIATE> -->
|
True
|
WS-2019-0425 (Medium) detected in multiple libraries - ## WS-2019-0425 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>mocha-3.5.3.tgz</b>, <b>mocha-4.1.0.tgz</b>, <b>mocha-5.2.0.tgz</b></p></summary>
<p>
<details><summary><b>mocha-3.5.3.tgz</b></p></summary>
<p>simple, flexible, fun test framework</p>
<p>Library home page: <a href="https://registry.npmjs.org/mocha/-/mocha-3.5.3.tgz">https://registry.npmjs.org/mocha/-/mocha-3.5.3.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/jazz/templates/sls-app-template-nodejs/package.json</p>
<p>Path to vulnerable library: /jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json,/jazz/templates/function-template-nodejs/node_modules/mocha/package.json</p>
<p>
Dependency Hierarchy:
- :x: **mocha-3.5.3.tgz** (Vulnerable Library)
</details>
<details><summary><b>mocha-4.1.0.tgz</b></p></summary>
<p>simple, flexible, fun test framework</p>
<p>Library home page: <a href="https://registry.npmjs.org/mocha/-/mocha-4.1.0.tgz">https://registry.npmjs.org/mocha/-/mocha-4.1.0.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/jazz/core/jazz_is-service-available/package.json</p>
<p>Path to vulnerable library: /jazz/core/jazz_is-service-available/node_modules/mocha/package.json</p>
<p>
Dependency Hierarchy:
- :x: **mocha-4.1.0.tgz** (Vulnerable Library)
</details>
<details><summary><b>mocha-5.2.0.tgz</b></p></summary>
<p>simple, flexible, fun test framework</p>
<p>Library home page: <a href="https://registry.npmjs.org/mocha/-/mocha-5.2.0.tgz">https://registry.npmjs.org/mocha/-/mocha-5.2.0.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/jazz/core/jazz_metrics/package.json</p>
<p>Path to vulnerable library: /jazz/core/jazz_metrics/node_modules/mocha/package.json</p>
<p>
Dependency Hierarchy:
- :x: **mocha-5.2.0.tgz** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/jtimberlake/jazz/commit/f31a850168fa59ceb2dfbdfb70a04c1bbe9b9fec">f31a850168fa59ceb2dfbdfb70a04c1bbe9b9fec</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Mocha is vulnerable to ReDoS attack. If the stack trace in utils.js begins with a large error message, and full-trace is not enabled, utils.stackTraceFilter() will take exponential run time.
<p>Publish Date: 2019-01-24
<p>URL: <a href=https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559>WS-2019-0425</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="v6.0.0">v6.0.0</a></p>
<p>Release Date: 2020-05-07</p>
<p>Fix Resolution: https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":false,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"mocha","packageVersion":"3.5.3","isTransitiveDependency":false,"dependencyTree":"mocha:3.5.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559"},{"packageType":"javascript/Node.js","packageName":"mocha","packageVersion":"4.1.0","isTransitiveDependency":false,"dependencyTree":"mocha:4.1.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559"},{"packageType":"javascript/Node.js","packageName":"mocha","packageVersion":"5.2.0","isTransitiveDependency":false,"dependencyTree":"mocha:5.2.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559"}],"vulnerabilityIdentifier":"WS-2019-0425","vulnerabilityDetails":"Mocha is vulnerable to ReDoS attack. If the stack trace in utils.js begins with a large error message, and full-trace is not enabled, utils.stackTraceFilter() will take exponential run time.","vulnerabilityUrl":"https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559","cvss3Severity":"medium","cvss3Score":"5.3","cvss3Metrics":{"A":"Low","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}}</REMEDIATE> -->
|
secu
|
ws medium detected in multiple libraries ws medium severity vulnerability vulnerable libraries mocha tgz mocha tgz mocha tgz mocha tgz simple flexible fun test framework library home page a href path to dependency file tmp ws scm jazz templates sls app template nodejs package json path to vulnerable library jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json jazz templates function template nodejs node modules mocha package json dependency hierarchy x mocha tgz vulnerable library mocha tgz simple flexible fun test framework library home page a href path to dependency file tmp ws scm jazz core jazz is service available package json path to vulnerable library jazz core jazz is service available node modules mocha package json dependency hierarchy x mocha tgz vulnerable library mocha tgz simple flexible fun test framework library home page a href path to dependency file tmp ws scm jazz core jazz metrics package json path to vulnerable library jazz core jazz metrics node modules mocha package json dependency hierarchy x mocha tgz vulnerable library found in head commit a href vulnerability details mocha is vulnerable to redos attack if the stack trace in utils js begins with a large error message and full trace is not enabled utils stacktracefilter will take exponential run time publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact low for more information on scores click a href suggested fix type upgrade version origin release date fix resolution isopenpronvulnerability false ispackagebased true isdefaultbranch true packages vulnerabilityidentifier ws vulnerabilitydetails mocha is vulnerable to redos attack if the stack trace in utils js begins with a large error message and full trace is not enabled utils stacktracefilter will take exponential run time vulnerabilityurl
| 1
|
19,637
| 10,374,702,641
|
IssuesEvent
|
2019-09-09 10:12:04
|
vicvega/chaltron
|
https://api.github.com/repos/vicvega/chaltron
|
closed
|
CVE-2018-8048 (Medium) detected in loofah-2.1.1.gem
|
security vulnerability
|
## CVE-2018-8048 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>loofah-2.1.1.gem</b></p></summary>
<p>Loofah is a general library for manipulating and transforming HTML/XML
documents and fragments. It's built on top of Nokogiri and libxml2, so
it's fast and has a nice API.
Loofah excels at HTML sanitization (XSS prevention). It includes some
nice HTML sanitizers, which are based on HTML5lib's whitelist, so it
most likely won't make your codes less secure. (These statements have
not been evaluated by Netexperts.)
ActiveRecord extensions for sanitization are available in the
`loofah-activerecord` gem (see
https://github.com/flavorjones/loofah-activerecord).</p>
<p>Library home page: <a href="https://rubygems.org/gems/loofah-2.1.1.gem">https://rubygems.org/gems/loofah-2.1.1.gem</a></p>
<p>Path to dependency file: /chaltron/Gemfile.lock</p>
<p>Path to vulnerable library: /var/lib/gems/2.3.0/cache/loofah-2.1.1.gem</p>
<p>
Dependency Hierarchy:
- factory_bot_rails-4.8.2.gem (Root Library)
- railties-5.1.4.gem
- actionpack-5.1.4.gem
- actionview-5.1.4.gem
- rails-html-sanitizer-1.0.3.gem
- :x: **loofah-2.1.1.gem** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/vicvega/chaltron/commit/1a064cdc3927fccfa0d178d4932613686897f05c">1a064cdc3927fccfa0d178d4932613686897f05c</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
In the Loofah gem through 2.2.0 for Ruby, non-whitelisted HTML attributes may occur in sanitized output by republishing a crafted HTML fragment.
<p>Publish Date: 2018-03-27
<p>URL: <a href=https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-8048>CVE-2018-8048</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Change files</p>
<p>Origin: <a href="https://github.com/flavorjones/loofah/commit/f739cf8eac5851f328b8044281d6653f74eff116">https://github.com/flavorjones/loofah/commit/f739cf8eac5851f328b8044281d6653f74eff116</a></p>
<p>Release Date: 2018-03-15</p>
<p>Fix Resolution: Replace or update the following files: scrub.rb, test_ad_hoc.rb, loofah.rb, libxml2_workarounds.rb</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2018-8048 (Medium) detected in loofah-2.1.1.gem - ## CVE-2018-8048 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>loofah-2.1.1.gem</b></p></summary>
<p>Loofah is a general library for manipulating and transforming HTML/XML
documents and fragments. It's built on top of Nokogiri and libxml2, so
it's fast and has a nice API.
Loofah excels at HTML sanitization (XSS prevention). It includes some
nice HTML sanitizers, which are based on HTML5lib's whitelist, so it
most likely won't make your codes less secure. (These statements have
not been evaluated by Netexperts.)
ActiveRecord extensions for sanitization are available in the
`loofah-activerecord` gem (see
https://github.com/flavorjones/loofah-activerecord).</p>
<p>Library home page: <a href="https://rubygems.org/gems/loofah-2.1.1.gem">https://rubygems.org/gems/loofah-2.1.1.gem</a></p>
<p>Path to dependency file: /chaltron/Gemfile.lock</p>
<p>Path to vulnerable library: /var/lib/gems/2.3.0/cache/loofah-2.1.1.gem</p>
<p>
Dependency Hierarchy:
- factory_bot_rails-4.8.2.gem (Root Library)
- railties-5.1.4.gem
- actionpack-5.1.4.gem
- actionview-5.1.4.gem
- rails-html-sanitizer-1.0.3.gem
- :x: **loofah-2.1.1.gem** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/vicvega/chaltron/commit/1a064cdc3927fccfa0d178d4932613686897f05c">1a064cdc3927fccfa0d178d4932613686897f05c</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
In the Loofah gem through 2.2.0 for Ruby, non-whitelisted HTML attributes may occur in sanitized output by republishing a crafted HTML fragment.
<p>Publish Date: 2018-03-27
<p>URL: <a href=https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-8048>CVE-2018-8048</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Change files</p>
<p>Origin: <a href="https://github.com/flavorjones/loofah/commit/f739cf8eac5851f328b8044281d6653f74eff116">https://github.com/flavorjones/loofah/commit/f739cf8eac5851f328b8044281d6653f74eff116</a></p>
<p>Release Date: 2018-03-15</p>
<p>Fix Resolution: Replace or update the following files: scrub.rb, test_ad_hoc.rb, loofah.rb, libxml2_workarounds.rb</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve medium detected in loofah gem cve medium severity vulnerability vulnerable library loofah gem loofah is a general library for manipulating and transforming html xml documents and fragments it s built on top of nokogiri and so it s fast and has a nice api loofah excels at html sanitization xss prevention it includes some nice html sanitizers which are based on s whitelist so it most likely won t make your codes less secure these statements have not been evaluated by netexperts activerecord extensions for sanitization are available in the loofah activerecord gem see library home page a href path to dependency file chaltron gemfile lock path to vulnerable library var lib gems cache loofah gem dependency hierarchy factory bot rails gem root library railties gem actionpack gem actionview gem rails html sanitizer gem x loofah gem vulnerable library found in head commit a href vulnerability details in the loofah gem through for ruby non whitelisted html attributes may occur in sanitized output by republishing a crafted html fragment publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope changed impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type change files origin a href release date fix resolution replace or update the following files scrub rb test ad hoc rb loofah rb workarounds rb step up your open source security game with whitesource
| 1
|
793,390
| 27,994,021,021
|
IssuesEvent
|
2023-03-27 07:07:44
|
apache/kyuubi
|
https://api.github.com/repos/apache/kyuubi
|
opened
|
[Bug] flink engine failed to generate operation log
|
kind:bug priority:major
|
### Code of Conduct
- [X] I agree to follow this project's [Code of Conduct](https://www.apache.org/foundation/policies/conduct)
### Search before asking
- [X] I have searched in the [issues](https://github.com/apache/kyuubi/issues?q=is%3Aissue) and found no similar issues.
### Describe the bug
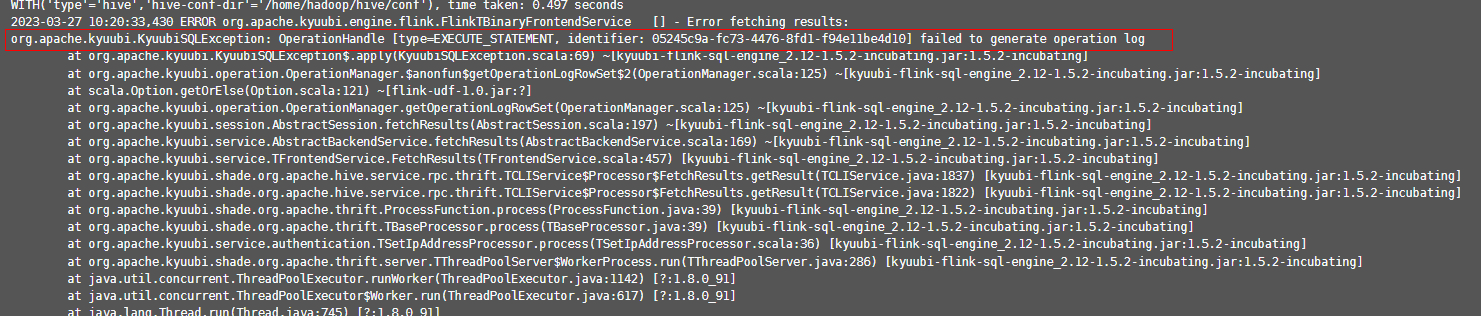
#4111
I read this issue, but found that the structure of the fix code is kyuubi-1.6.1 version, my current kyuubi version is 1.5.2, how should I deal with this problem, directly upgrade kyuubi to 1.7.0?
### Affects Version(s)
1.5.2
### Kyuubi Server Log Output
_No response_
### Kyuubi Engine Log Output
```logtalk
2023-03-27 10:20:33,430 ERROR org.apache.kyuubi.engine.flink.FlinkTBinaryFrontendService [] - Error fetching results:
org.apache.kyuubi.KyuubiSQLException: OperationHandle [type=EXECUTE_STATEMENT, identifier: 05245c9a-fc73-4476-8fd1-f94e11be4d10] failed to generate operation log
```
### Kyuubi Server Configurations
_No response_
### Kyuubi Engine Configurations
_No response_
### Additional context
_No response_
### Are you willing to submit PR?
- [ ] Yes. I would be willing to submit a PR with guidance from the Kyuubi community to fix.
- [ ] No. I cannot submit a PR at this time.
|
1.0
|
[Bug] flink engine failed to generate operation log - ### Code of Conduct
- [X] I agree to follow this project's [Code of Conduct](https://www.apache.org/foundation/policies/conduct)
### Search before asking
- [X] I have searched in the [issues](https://github.com/apache/kyuubi/issues?q=is%3Aissue) and found no similar issues.
### Describe the bug

#4111
I read this issue, but found that the structure of the fix code is kyuubi-1.6.1 version, my current kyuubi version is 1.5.2, how should I deal with this problem, directly upgrade kyuubi to 1.7.0?
### Affects Version(s)
1.5.2
### Kyuubi Server Log Output
_No response_
### Kyuubi Engine Log Output
```logtalk
2023-03-27 10:20:33,430 ERROR org.apache.kyuubi.engine.flink.FlinkTBinaryFrontendService [] - Error fetching results:
org.apache.kyuubi.KyuubiSQLException: OperationHandle [type=EXECUTE_STATEMENT, identifier: 05245c9a-fc73-4476-8fd1-f94e11be4d10] failed to generate operation log
```
### Kyuubi Server Configurations
_No response_
### Kyuubi Engine Configurations
_No response_
### Additional context
_No response_
### Are you willing to submit PR?
- [ ] Yes. I would be willing to submit a PR with guidance from the Kyuubi community to fix.
- [ ] No. I cannot submit a PR at this time.
|
non_secu
|
flink engine failed to generate operation log code of conduct i agree to follow this project s search before asking i have searched in the and found no similar issues describe the bug i read this issue but found that the structure of the fix code is kyuubi version my current kyuubi version is how should i deal with this problem directly upgrade kyuubi to affects version s kyuubi server log output no response kyuubi engine log output logtalk error org apache kyuubi engine flink flinktbinaryfrontendservice error fetching results org apache kyuubi kyuubisqlexception operationhandle failed to generate operation log kyuubi server configurations no response kyuubi engine configurations no response additional context no response are you willing to submit pr yes i would be willing to submit a pr with guidance from the kyuubi community to fix no i cannot submit a pr at this time
| 0
|
3,313
| 4,323,658,942
|
IssuesEvent
|
2016-07-25 17:41:51
|
dkopecek/usbguard
|
https://api.github.com/repos/dkopecek/usbguard
|
closed
|
Descriptor data not included in the device hash value computation
|
bug security
|
During the rule parser refactoring I've noticed that the device hash computation routine doesn't take the descriptor data blob into account. Only the values of several attribute are included in the hash computation. Fixing this will lead to a backwards incompatibility which is very unfortunate :-(
|
True
|
Descriptor data not included in the device hash value computation - During the rule parser refactoring I've noticed that the device hash computation routine doesn't take the descriptor data blob into account. Only the values of several attribute are included in the hash computation. Fixing this will lead to a backwards incompatibility which is very unfortunate :-(
|
secu
|
descriptor data not included in the device hash value computation during the rule parser refactoring i ve noticed that the device hash computation routine doesn t take the descriptor data blob into account only the values of several attribute are included in the hash computation fixing this will lead to a backwards incompatibility which is very unfortunate
| 1
|
32,594
| 12,131,321,182
|
IssuesEvent
|
2020-04-23 04:21:15
|
kenferrara/spark
|
https://api.github.com/repos/kenferrara/spark
|
opened
|
CVE-2019-8331 (Medium) detected in bootstrap-2.1.0.min.js, bootstrap-2.1.0.js
|
security vulnerability
|
## CVE-2019-8331 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>bootstrap-2.1.0.min.js</b>, <b>bootstrap-2.1.0.js</b></p></summary>
<p>
<details><summary><b>bootstrap-2.1.0.min.js</b></p></summary>
<p>The most popular front-end framework for developing responsive, mobile first projects on the web.</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/twitter-bootstrap/2.1.0/bootstrap.min.js">https://cdnjs.cloudflare.com/ajax/libs/twitter-bootstrap/2.1.0/bootstrap.min.js</a></p>
<p>Path to vulnerable library: /spark/docs/js/vendor/bootstrap.min.js,/spark/docs/js/vendor/bootstrap.min.js</p>
<p>
Dependency Hierarchy:
- :x: **bootstrap-2.1.0.min.js** (Vulnerable Library)
</details>
<details><summary><b>bootstrap-2.1.0.js</b></p></summary>
<p>The most popular front-end framework for developing responsive, mobile first projects on the web.</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/twitter-bootstrap/2.1.0/bootstrap.js">https://cdnjs.cloudflare.com/ajax/libs/twitter-bootstrap/2.1.0/bootstrap.js</a></p>
<p>Path to vulnerable library: /spark/docs/js/vendor/bootstrap.js,/spark/docs/js/vendor/bootstrap.js</p>
<p>
Dependency Hierarchy:
- :x: **bootstrap-2.1.0.js** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/kenferrara/spark/commit/486b2d6a475cb2e6ab8e936905d6ceec71fc60ce">486b2d6a475cb2e6ab8e936905d6ceec71fc60ce</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
In Bootstrap before 3.4.1 and 4.3.x before 4.3.1, XSS is possible in the tooltip or popover data-template attribute.
<p>Publish Date: 2019-02-20
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2019-8331>CVE-2019-8331</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/twbs/bootstrap/pull/28236">https://github.com/twbs/bootstrap/pull/28236</a></p>
<p>Release Date: 2019-02-20</p>
<p>Fix Resolution: bootstrap - 3.4.1,4.3.1;bootstrap-sass - 3.4.1,4.3.1</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":false,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"JavaScript","packageName":"twitter-bootstrap","packageVersion":"2.1.0","isTransitiveDependency":false,"dependencyTree":"twitter-bootstrap:2.1.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"bootstrap - 3.4.1,4.3.1;bootstrap-sass - 3.4.1,4.3.1"},{"packageType":"JavaScript","packageName":"twitter-bootstrap","packageVersion":"2.1.0","isTransitiveDependency":false,"dependencyTree":"twitter-bootstrap:2.1.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"bootstrap - 3.4.1,4.3.1;bootstrap-sass - 3.4.1,4.3.1"}],"vulnerabilityIdentifier":"CVE-2019-8331","vulnerabilityDetails":"In Bootstrap before 3.4.1 and 4.3.x before 4.3.1, XSS is possible in the tooltip or popover data-template attribute.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2019-8331","cvss3Severity":"medium","cvss3Score":"6.1","cvss3Metrics":{"A":"None","AC":"Low","PR":"None","S":"Changed","C":"Low","UI":"Required","AV":"Network","I":"Low"},"extraData":{}}</REMEDIATE> -->
|
True
|
CVE-2019-8331 (Medium) detected in bootstrap-2.1.0.min.js, bootstrap-2.1.0.js - ## CVE-2019-8331 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>bootstrap-2.1.0.min.js</b>, <b>bootstrap-2.1.0.js</b></p></summary>
<p>
<details><summary><b>bootstrap-2.1.0.min.js</b></p></summary>
<p>The most popular front-end framework for developing responsive, mobile first projects on the web.</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/twitter-bootstrap/2.1.0/bootstrap.min.js">https://cdnjs.cloudflare.com/ajax/libs/twitter-bootstrap/2.1.0/bootstrap.min.js</a></p>
<p>Path to vulnerable library: /spark/docs/js/vendor/bootstrap.min.js,/spark/docs/js/vendor/bootstrap.min.js</p>
<p>
Dependency Hierarchy:
- :x: **bootstrap-2.1.0.min.js** (Vulnerable Library)
</details>
<details><summary><b>bootstrap-2.1.0.js</b></p></summary>
<p>The most popular front-end framework for developing responsive, mobile first projects on the web.</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/twitter-bootstrap/2.1.0/bootstrap.js">https://cdnjs.cloudflare.com/ajax/libs/twitter-bootstrap/2.1.0/bootstrap.js</a></p>
<p>Path to vulnerable library: /spark/docs/js/vendor/bootstrap.js,/spark/docs/js/vendor/bootstrap.js</p>
<p>
Dependency Hierarchy:
- :x: **bootstrap-2.1.0.js** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/kenferrara/spark/commit/486b2d6a475cb2e6ab8e936905d6ceec71fc60ce">486b2d6a475cb2e6ab8e936905d6ceec71fc60ce</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
In Bootstrap before 3.4.1 and 4.3.x before 4.3.1, XSS is possible in the tooltip or popover data-template attribute.
<p>Publish Date: 2019-02-20
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2019-8331>CVE-2019-8331</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/twbs/bootstrap/pull/28236">https://github.com/twbs/bootstrap/pull/28236</a></p>
<p>Release Date: 2019-02-20</p>
<p>Fix Resolution: bootstrap - 3.4.1,4.3.1;bootstrap-sass - 3.4.1,4.3.1</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":false,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"JavaScript","packageName":"twitter-bootstrap","packageVersion":"2.1.0","isTransitiveDependency":false,"dependencyTree":"twitter-bootstrap:2.1.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"bootstrap - 3.4.1,4.3.1;bootstrap-sass - 3.4.1,4.3.1"},{"packageType":"JavaScript","packageName":"twitter-bootstrap","packageVersion":"2.1.0","isTransitiveDependency":false,"dependencyTree":"twitter-bootstrap:2.1.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"bootstrap - 3.4.1,4.3.1;bootstrap-sass - 3.4.1,4.3.1"}],"vulnerabilityIdentifier":"CVE-2019-8331","vulnerabilityDetails":"In Bootstrap before 3.4.1 and 4.3.x before 4.3.1, XSS is possible in the tooltip or popover data-template attribute.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2019-8331","cvss3Severity":"medium","cvss3Score":"6.1","cvss3Metrics":{"A":"None","AC":"Low","PR":"None","S":"Changed","C":"Low","UI":"Required","AV":"Network","I":"Low"},"extraData":{}}</REMEDIATE> -->
|
secu
|
cve medium detected in bootstrap min js bootstrap js cve medium severity vulnerability vulnerable libraries bootstrap min js bootstrap js bootstrap min js the most popular front end framework for developing responsive mobile first projects on the web library home page a href path to vulnerable library spark docs js vendor bootstrap min js spark docs js vendor bootstrap min js dependency hierarchy x bootstrap min js vulnerable library bootstrap js the most popular front end framework for developing responsive mobile first projects on the web library home page a href path to vulnerable library spark docs js vendor bootstrap js spark docs js vendor bootstrap js dependency hierarchy x bootstrap js vulnerable library found in head commit a href vulnerability details in bootstrap before and x before xss is possible in the tooltip or popover data template attribute publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope changed impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution bootstrap bootstrap sass isopenpronvulnerability false ispackagebased true isdefaultbranch true packages vulnerabilityidentifier cve vulnerabilitydetails in bootstrap before and x before xss is possible in the tooltip or popover data template attribute vulnerabilityurl
| 1
|
134,873
| 5,239,008,124
|
IssuesEvent
|
2017-01-31 08:12:39
|
status-im/status-react
|
https://api.github.com/repos/status-im/status-react
|
closed
|
Discover view lost its over scroll bungie effect
|
bug in progress intermediate medium-priority
|
## Description
[iOS] The Chats and Contacts views will allow you to slide a view beyond its max height and it will snap back. The Discover view has lost this effect.
## Reproduction
1. Go to Discover view.
2. Slide down to go beyond top of page. **[nothing happens]**
3. Go to Chats view.
4. Slide down to go beyond top of page. **[bungie effect is visible]**
|
1.0
|
Discover view lost its over scroll bungie effect - ## Description
[iOS] The Chats and Contacts views will allow you to slide a view beyond its max height and it will snap back. The Discover view has lost this effect.
## Reproduction
1. Go to Discover view.
2. Slide down to go beyond top of page. **[nothing happens]**
3. Go to Chats view.
4. Slide down to go beyond top of page. **[bungie effect is visible]**
|
non_secu
|
discover view lost its over scroll bungie effect description the chats and contacts views will allow you to slide a view beyond its max height and it will snap back the discover view has lost this effect reproduction go to discover view slide down to go beyond top of page go to chats view slide down to go beyond top of page
| 0
|
257,802
| 19,532,166,657
|
IssuesEvent
|
2021-12-30 19:11:42
|
fleetdm/fleet
|
https://api.github.com/repos/fleetdm/fleet
|
opened
|
Add a "Signing installers" section to the "Adding hosts" documentation page
|
:improve documentation idea
|
### Goal
Add a "Signing installers" section to the "Adding hosts" documentation page
### How?
- [ ] Add a "Signing installers" section
- [ ] Add instructions that answer the following questions:
- What do I need to use to sign an osquery installer for macOS?
- What do I need to use to sign an osquery installer for Windows?
|
1.0
|
Add a "Signing installers" section to the "Adding hosts" documentation page - ### Goal
Add a "Signing installers" section to the "Adding hosts" documentation page
### How?
- [ ] Add a "Signing installers" section
- [ ] Add instructions that answer the following questions:
- What do I need to use to sign an osquery installer for macOS?
- What do I need to use to sign an osquery installer for Windows?
|
non_secu
|
add a signing installers section to the adding hosts documentation page goal add a signing installers section to the adding hosts documentation page how add a signing installers section add instructions that answer the following questions what do i need to use to sign an osquery installer for macos what do i need to use to sign an osquery installer for windows
| 0
|
127,305
| 10,465,345,542
|
IssuesEvent
|
2019-09-21 10:02:22
|
fastify/fastify
|
https://api.github.com/repos/fastify/fastify
|
closed
|
Remove Travis from master
|
discussion test
|
Travis has already been removed from the 1.x and next branches. Azure Pipelines has been working very well. It’s time to remove Travis from master, and disconnect it from the repository as a whole.
|
1.0
|
Remove Travis from master - Travis has already been removed from the 1.x and next branches. Azure Pipelines has been working very well. It’s time to remove Travis from master, and disconnect it from the repository as a whole.
|
non_secu
|
remove travis from master travis has already been removed from the x and next branches azure pipelines has been working very well it’s time to remove travis from master and disconnect it from the repository as a whole
| 0
|
170,589
| 6,459,567,243
|
IssuesEvent
|
2017-08-16 00:10:40
|
objectpartners/angular2-timesheet
|
https://api.github.com/repos/objectpartners/angular2-timesheet
|
opened
|
Add support links into navigation in the workshop
|
Priority: Low
|
In an effort to better aid workshoppees, we should add links to the github repo, workshop slides, angular docs, and angular material docs.
|
1.0
|
Add support links into navigation in the workshop - In an effort to better aid workshoppees, we should add links to the github repo, workshop slides, angular docs, and angular material docs.
|
non_secu
|
add support links into navigation in the workshop in an effort to better aid workshoppees we should add links to the github repo workshop slides angular docs and angular material docs
| 0
|
364,052
| 25,479,277,849
|
IssuesEvent
|
2022-11-25 18:02:58
|
entropyqueen/trans-cec
|
https://api.github.com/repos/entropyqueen/trans-cec
|
opened
|
Faire un README propre
|
documentation
|
C'est mooooche, c'est tout plein de trucs c'est compliqué, bref.
Simplifions, facilitons, tout ça tout ça...
|
1.0
|
Faire un README propre - C'est mooooche, c'est tout plein de trucs c'est compliqué, bref.
Simplifions, facilitons, tout ça tout ça...
|
non_secu
|
faire un readme propre c est mooooche c est tout plein de trucs c est compliqué bref simplifions facilitons tout ça tout ça
| 0
|
2,163
| 5,008,956,794
|
IssuesEvent
|
2016-12-12 20:59:58
|
bongo227/StatsNotes
|
https://api.github.com/repos/bongo227/StatsNotes
|
opened
|
Estimation of short-term standard deviation from small samples. Ability of a process to meet tolerances.
|
15.3 Statistical Process Control
|
From the spec:
Estimate of proportion not meeting tolerances.
|
1.0
|
Estimation of short-term standard deviation from small samples. Ability of a process to meet tolerances. - From the spec:
Estimate of proportion not meeting tolerances.
|
non_secu
|
estimation of short term standard deviation from small samples ability of a process to meet tolerances from the spec estimate of proportion not meeting tolerances
| 0
|
71,907
| 15,210,106,322
|
IssuesEvent
|
2021-02-17 06:49:18
|
andythinkpower/Proj_02
|
https://api.github.com/repos/andythinkpower/Proj_02
|
opened
|
CVE-2018-11771 (Medium) detected in commons-compress-1.12.jar
|
security vulnerability
|
## CVE-2018-11771 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>commons-compress-1.12.jar</b></p></summary>
<p>Apache Commons Compress software defines an API for working with
compression and archive formats. These include: bzip2, gzip, pack200,
lzma, xz, Snappy, traditional Unix Compress, DEFLATE and ar, cpio,
jar, tar, zip, dump, 7z, arj.</p>
<p>Path to dependency file: Proj_02/Proj_02/pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/org/apache/commons/commons-compress/1.12/commons-compress-1.12.jar</p>
<p>
Dependency Hierarchy:
- crawler-1.1.1.jar (Root Library)
- :x: **commons-compress-1.12.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/andythinkpower/Proj_02/commit/6a5524c5fbfdc64743279b212644fc3cfd9fe515">6a5524c5fbfdc64743279b212644fc3cfd9fe515</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
When reading a specially crafted ZIP archive, the read method of Apache Commons Compress 1.7 to 1.17's ZipArchiveInputStream can fail to return the correct EOF indication after the end of the stream has been reached. When combined with a java.io.InputStreamReader this can lead to an infinite stream, which can be used to mount a denial of service attack against services that use Compress' zip package.
<p>Publish Date: 2018-08-16
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-11771>CVE-2018-11771</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-11771">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-11771</a></p>
<p>Release Date: 2018-08-16</p>
<p>Fix Resolution: 1.18</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2018-11771 (Medium) detected in commons-compress-1.12.jar - ## CVE-2018-11771 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>commons-compress-1.12.jar</b></p></summary>
<p>Apache Commons Compress software defines an API for working with
compression and archive formats. These include: bzip2, gzip, pack200,
lzma, xz, Snappy, traditional Unix Compress, DEFLATE and ar, cpio,
jar, tar, zip, dump, 7z, arj.</p>
<p>Path to dependency file: Proj_02/Proj_02/pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/org/apache/commons/commons-compress/1.12/commons-compress-1.12.jar</p>
<p>
Dependency Hierarchy:
- crawler-1.1.1.jar (Root Library)
- :x: **commons-compress-1.12.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/andythinkpower/Proj_02/commit/6a5524c5fbfdc64743279b212644fc3cfd9fe515">6a5524c5fbfdc64743279b212644fc3cfd9fe515</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
When reading a specially crafted ZIP archive, the read method of Apache Commons Compress 1.7 to 1.17's ZipArchiveInputStream can fail to return the correct EOF indication after the end of the stream has been reached. When combined with a java.io.InputStreamReader this can lead to an infinite stream, which can be used to mount a denial of service attack against services that use Compress' zip package.
<p>Publish Date: 2018-08-16
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-11771>CVE-2018-11771</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-11771">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-11771</a></p>
<p>Release Date: 2018-08-16</p>
<p>Fix Resolution: 1.18</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve medium detected in commons compress jar cve medium severity vulnerability vulnerable library commons compress jar apache commons compress software defines an api for working with compression and archive formats these include gzip lzma xz snappy traditional unix compress deflate and ar cpio jar tar zip dump arj path to dependency file proj proj pom xml path to vulnerable library home wss scanner repository org apache commons commons compress commons compress jar dependency hierarchy crawler jar root library x commons compress jar vulnerable library found in head commit a href found in base branch master vulnerability details when reading a specially crafted zip archive the read method of apache commons compress to s ziparchiveinputstream can fail to return the correct eof indication after the end of the stream has been reached when combined with a java io inputstreamreader this can lead to an infinite stream which can be used to mount a denial of service attack against services that use compress zip package publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource
| 1
|
171,587
| 20,977,553,337
|
IssuesEvent
|
2022-03-28 16:32:21
|
hejny/czech.events
|
https://api.github.com/repos/hejny/czech.events
|
closed
|
CVE-2022-0691 (High) detected in url-parse-1.5.4.tgz - autoclosed
|
security vulnerability
|
## CVE-2022-0691 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>url-parse-1.5.4.tgz</b></p></summary>
<p>Small footprint URL parser that works seamlessly across Node.js and browser environments</p>
<p>Library home page: <a href="https://registry.npmjs.org/url-parse/-/url-parse-1.5.4.tgz">https://registry.npmjs.org/url-parse/-/url-parse-1.5.4.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/url-parse/package.json</p>
<p>
Dependency Hierarchy:
- react-scripts-4.0.1.tgz (Root Library)
- webpack-dev-server-3.11.0.tgz
- sockjs-client-1.4.0.tgz
- :x: **url-parse-1.5.4.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/hejny/czech.events/commit/36f62f87577c43d4fbf9ddf409e6cc8ae77c17bb">36f62f87577c43d4fbf9ddf409e6cc8ae77c17bb</a></p>
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Authorization Bypass Through User-Controlled Key in NPM url-parse prior to 1.5.9.
<p>Publish Date: 2022-02-21
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2022-0691>CVE-2022-0691</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>9.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0691">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0691</a></p>
<p>Release Date: 2022-02-21</p>
<p>Fix Resolution (url-parse): 1.5.9</p>
<p>Direct dependency fix Resolution (react-scripts): 4.0.2</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2022-0691 (High) detected in url-parse-1.5.4.tgz - autoclosed - ## CVE-2022-0691 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>url-parse-1.5.4.tgz</b></p></summary>
<p>Small footprint URL parser that works seamlessly across Node.js and browser environments</p>
<p>Library home page: <a href="https://registry.npmjs.org/url-parse/-/url-parse-1.5.4.tgz">https://registry.npmjs.org/url-parse/-/url-parse-1.5.4.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/url-parse/package.json</p>
<p>
Dependency Hierarchy:
- react-scripts-4.0.1.tgz (Root Library)
- webpack-dev-server-3.11.0.tgz
- sockjs-client-1.4.0.tgz
- :x: **url-parse-1.5.4.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/hejny/czech.events/commit/36f62f87577c43d4fbf9ddf409e6cc8ae77c17bb">36f62f87577c43d4fbf9ddf409e6cc8ae77c17bb</a></p>
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Authorization Bypass Through User-Controlled Key in NPM url-parse prior to 1.5.9.
<p>Publish Date: 2022-02-21
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2022-0691>CVE-2022-0691</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>9.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0691">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0691</a></p>
<p>Release Date: 2022-02-21</p>
<p>Fix Resolution (url-parse): 1.5.9</p>
<p>Direct dependency fix Resolution (react-scripts): 4.0.2</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve high detected in url parse tgz autoclosed cve high severity vulnerability vulnerable library url parse tgz small footprint url parser that works seamlessly across node js and browser environments library home page a href path to dependency file package json path to vulnerable library node modules url parse package json dependency hierarchy react scripts tgz root library webpack dev server tgz sockjs client tgz x url parse tgz vulnerable library found in head commit a href found in base branch main vulnerability details authorization bypass through user controlled key in npm url parse prior to publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution url parse direct dependency fix resolution react scripts step up your open source security game with whitesource
| 1
|
432,054
| 12,488,608,477
|
IssuesEvent
|
2020-05-31 15:01:55
|
arfc/2020-fairhurst-hydrogen-production
|
https://api.github.com/repos/arfc/2020-fairhurst-hydrogen-production
|
closed
|
Add document with more information about iodine-sulfur cycle
|
Comp:Core Difficulty:2-Challenging Priority:2-Normal Status:1-New Type:Docs
|
This issue can be closed when more information about the iodine-sulfur thermochemical cycle for producing hydrogen is added to the repository. This information should also contain more accurate data about the energy (both thermal and electric) demanded by the process.
|
1.0
|
Add document with more information about iodine-sulfur cycle - This issue can be closed when more information about the iodine-sulfur thermochemical cycle for producing hydrogen is added to the repository. This information should also contain more accurate data about the energy (both thermal and electric) demanded by the process.
|
non_secu
|
add document with more information about iodine sulfur cycle this issue can be closed when more information about the iodine sulfur thermochemical cycle for producing hydrogen is added to the repository this information should also contain more accurate data about the energy both thermal and electric demanded by the process
| 0
|
53,658
| 13,866,942,787
|
IssuesEvent
|
2020-10-16 07:41:39
|
stefanfreitag/terraforming_aws
|
https://api.github.com/repos/stefanfreitag/terraforming_aws
|
opened
|
CVE-2018-20190 (Medium) detected in opennmsopennms-source-25.1.0-1, node-sass-4.14.1.tgz
|
security vulnerability
|
## CVE-2018-20190 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>opennmsopennms-source-25.1.0-1</b>, <b>node-sass-4.14.1.tgz</b></p></summary>
<p>
<details><summary><b>node-sass-4.14.1.tgz</b></p></summary>
<p>Wrapper around libsass</p>
<p>Library home page: <a href="https://registry.npmjs.org/node-sass/-/node-sass-4.14.1.tgz">https://registry.npmjs.org/node-sass/-/node-sass-4.14.1.tgz</a></p>
<p>Path to dependency file: terraforming_aws/package.json</p>
<p>Path to vulnerable library: terraforming_aws/node_modules/node-sass/package.json</p>
<p>
Dependency Hierarchy:
- gulp-sass-4.1.0.tgz (Root Library)
- :x: **node-sass-4.14.1.tgz** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/stefanfreitag/terraforming_aws/commit/623bc34dec328e840fb0bb8649481fc0a71c8158">623bc34dec328e840fb0bb8649481fc0a71c8158</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
In LibSass 3.5.5, a NULL Pointer Dereference in the function Sass::Eval::operator()(Sass::Supports_Operator*) in eval.cpp may cause a Denial of Service (application crash) via a crafted sass input file.
<p>Publish Date: 2018-12-17
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-20190>CVE-2018-20190</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20190">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20190</a></p>
<p>Release Date: 2018-12-17</p>
<p>Fix Resolution: LibSass - 3.6.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2018-20190 (Medium) detected in opennmsopennms-source-25.1.0-1, node-sass-4.14.1.tgz - ## CVE-2018-20190 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>opennmsopennms-source-25.1.0-1</b>, <b>node-sass-4.14.1.tgz</b></p></summary>
<p>
<details><summary><b>node-sass-4.14.1.tgz</b></p></summary>
<p>Wrapper around libsass</p>
<p>Library home page: <a href="https://registry.npmjs.org/node-sass/-/node-sass-4.14.1.tgz">https://registry.npmjs.org/node-sass/-/node-sass-4.14.1.tgz</a></p>
<p>Path to dependency file: terraforming_aws/package.json</p>
<p>Path to vulnerable library: terraforming_aws/node_modules/node-sass/package.json</p>
<p>
Dependency Hierarchy:
- gulp-sass-4.1.0.tgz (Root Library)
- :x: **node-sass-4.14.1.tgz** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/stefanfreitag/terraforming_aws/commit/623bc34dec328e840fb0bb8649481fc0a71c8158">623bc34dec328e840fb0bb8649481fc0a71c8158</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
In LibSass 3.5.5, a NULL Pointer Dereference in the function Sass::Eval::operator()(Sass::Supports_Operator*) in eval.cpp may cause a Denial of Service (application crash) via a crafted sass input file.
<p>Publish Date: 2018-12-17
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-20190>CVE-2018-20190</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20190">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20190</a></p>
<p>Release Date: 2018-12-17</p>
<p>Fix Resolution: LibSass - 3.6.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve medium detected in opennmsopennms source node sass tgz cve medium severity vulnerability vulnerable libraries opennmsopennms source node sass tgz node sass tgz wrapper around libsass library home page a href path to dependency file terraforming aws package json path to vulnerable library terraforming aws node modules node sass package json dependency hierarchy gulp sass tgz root library x node sass tgz vulnerable library found in head commit a href found in base branch master vulnerability details in libsass a null pointer dereference in the function sass eval operator sass supports operator in eval cpp may cause a denial of service application crash via a crafted sass input file publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution libsass step up your open source security game with whitesource
| 1
|
21,062
| 10,568,905,744
|
IssuesEvent
|
2019-10-06 16:05:07
|
vvni/one-life-app
|
https://api.github.com/repos/vvni/one-life-app
|
opened
|
CVE-2019-10103 (High) detected in kotlin-stdlib-common-1.3.0.jar, kotlin-stdlib-1.3.0.jar
|
security vulnerability
|
## CVE-2019-10103 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>kotlin-stdlib-common-1.3.0.jar</b>, <b>kotlin-stdlib-1.3.0.jar</b></p></summary>
<p>
<details><summary><b>kotlin-stdlib-common-1.3.0.jar</b></p></summary>
<p>Kotlin Common Standard Library</p>
<p>Library home page: <a href="https://kotlinlang.org/">https://kotlinlang.org/</a></p>
<p>Path to vulnerable library: /one-life-app/node_modules/jetifier/lib/kotlin-stdlib-common-1.3.0.jar</p>
<p>
Dependency Hierarchy:
- :x: **kotlin-stdlib-common-1.3.0.jar** (Vulnerable Library)
</details>
<details><summary><b>kotlin-stdlib-1.3.0.jar</b></p></summary>
<p>Kotlin Standard Library for JVM</p>
<p>Library home page: <a href="https://kotlinlang.org/">https://kotlinlang.org/</a></p>
<p>Path to vulnerable library: /one-life-app/node_modules/jetifier/lib/kotlin-stdlib-1.3.0.jar</p>
<p>
Dependency Hierarchy:
- :x: **kotlin-stdlib-1.3.0.jar** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/vvni/one-life-app/commit/2550f1e3ade2b451077cec6fba9351bcdfffe79e">2550f1e3ade2b451077cec6fba9351bcdfffe79e</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
JetBrains IntelliJ IDEA projects created using the Kotlin (JS Client/JVM Server) IDE Template were resolving Gradle artifacts using an http connection, potentially allowing an MITM attack. This issue, which was fixed in Kotlin plugin version 1.3.30, is similar to CVE-2019-10101.
<p>Publish Date: 2019-07-03
<p>URL: <a href=https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-10103>CVE-2019-10103</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>8.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-10103">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-10103</a></p>
<p>Release Date: 2019-07-03</p>
<p>Fix Resolution: 1.3.30</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2019-10103 (High) detected in kotlin-stdlib-common-1.3.0.jar, kotlin-stdlib-1.3.0.jar - ## CVE-2019-10103 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>kotlin-stdlib-common-1.3.0.jar</b>, <b>kotlin-stdlib-1.3.0.jar</b></p></summary>
<p>
<details><summary><b>kotlin-stdlib-common-1.3.0.jar</b></p></summary>
<p>Kotlin Common Standard Library</p>
<p>Library home page: <a href="https://kotlinlang.org/">https://kotlinlang.org/</a></p>
<p>Path to vulnerable library: /one-life-app/node_modules/jetifier/lib/kotlin-stdlib-common-1.3.0.jar</p>
<p>
Dependency Hierarchy:
- :x: **kotlin-stdlib-common-1.3.0.jar** (Vulnerable Library)
</details>
<details><summary><b>kotlin-stdlib-1.3.0.jar</b></p></summary>
<p>Kotlin Standard Library for JVM</p>
<p>Library home page: <a href="https://kotlinlang.org/">https://kotlinlang.org/</a></p>
<p>Path to vulnerable library: /one-life-app/node_modules/jetifier/lib/kotlin-stdlib-1.3.0.jar</p>
<p>
Dependency Hierarchy:
- :x: **kotlin-stdlib-1.3.0.jar** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/vvni/one-life-app/commit/2550f1e3ade2b451077cec6fba9351bcdfffe79e">2550f1e3ade2b451077cec6fba9351bcdfffe79e</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
JetBrains IntelliJ IDEA projects created using the Kotlin (JS Client/JVM Server) IDE Template were resolving Gradle artifacts using an http connection, potentially allowing an MITM attack. This issue, which was fixed in Kotlin plugin version 1.3.30, is similar to CVE-2019-10101.
<p>Publish Date: 2019-07-03
<p>URL: <a href=https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-10103>CVE-2019-10103</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>8.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-10103">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-10103</a></p>
<p>Release Date: 2019-07-03</p>
<p>Fix Resolution: 1.3.30</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve high detected in kotlin stdlib common jar kotlin stdlib jar cve high severity vulnerability vulnerable libraries kotlin stdlib common jar kotlin stdlib jar kotlin stdlib common jar kotlin common standard library library home page a href path to vulnerable library one life app node modules jetifier lib kotlin stdlib common jar dependency hierarchy x kotlin stdlib common jar vulnerable library kotlin stdlib jar kotlin standard library for jvm library home page a href path to vulnerable library one life app node modules jetifier lib kotlin stdlib jar dependency hierarchy x kotlin stdlib jar vulnerable library found in head commit a href vulnerability details jetbrains intellij idea projects created using the kotlin js client jvm server ide template were resolving gradle artifacts using an http connection potentially allowing an mitm attack this issue which was fixed in kotlin plugin version is similar to cve publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource
| 1
|
282,208
| 30,889,223,341
|
IssuesEvent
|
2023-08-04 02:25:05
|
madhans23/linux-4.1.15
|
https://api.github.com/repos/madhans23/linux-4.1.15
|
reopened
|
CVE-2022-24958 (High) detected in linux-stable-rtv4.1.33
|
Mend: dependency security vulnerability
|
## CVE-2022-24958 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linux-stable-rtv4.1.33</b></p></summary>
<p>
<p>Julia Cartwright's fork of linux-stable-rt.git</p>
<p>Library home page: <a href=https://git.kernel.org/pub/scm/linux/kernel/git/julia/linux-stable-rt.git>https://git.kernel.org/pub/scm/linux/kernel/git/julia/linux-stable-rt.git</a></p>
<p>Found in base branch: <b>master</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (1)</summary>
<p></p>
<p>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png?' width=19 height=20> Vulnerability Details</summary>
<p>
drivers/usb/gadget/legacy/inode.c in the Linux kernel through 5.16.8 mishandles dev->buf release.
<p>Publish Date: 2022-02-11
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2022-24958>CVE-2022-24958</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-24958">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-24958</a></p>
<p>Release Date: 2022-02-11</p>
<p>Fix Resolution: v5.16</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2022-24958 (High) detected in linux-stable-rtv4.1.33 - ## CVE-2022-24958 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linux-stable-rtv4.1.33</b></p></summary>
<p>
<p>Julia Cartwright's fork of linux-stable-rt.git</p>
<p>Library home page: <a href=https://git.kernel.org/pub/scm/linux/kernel/git/julia/linux-stable-rt.git>https://git.kernel.org/pub/scm/linux/kernel/git/julia/linux-stable-rt.git</a></p>
<p>Found in base branch: <b>master</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (1)</summary>
<p></p>
<p>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png?' width=19 height=20> Vulnerability Details</summary>
<p>
drivers/usb/gadget/legacy/inode.c in the Linux kernel through 5.16.8 mishandles dev->buf release.
<p>Publish Date: 2022-02-11
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2022-24958>CVE-2022-24958</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-24958">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-24958</a></p>
<p>Release Date: 2022-02-11</p>
<p>Fix Resolution: v5.16</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve high detected in linux stable cve high severity vulnerability vulnerable library linux stable julia cartwright s fork of linux stable rt git library home page a href found in base branch master vulnerable source files vulnerability details drivers usb gadget legacy inode c in the linux kernel through mishandles dev buf release publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required low user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with mend
| 1
|
133,058
| 12,530,818,811
|
IssuesEvent
|
2020-06-04 13:39:44
|
GSG-K3/funny-hooks
|
https://api.github.com/repos/GSG-K3/funny-hooks
|
closed
|
create Read-me
|
Done documentation
|
In README:
- [x] Title
- [x] Description
- [x] user journey
- [x] how to run our project
- [x] Team members
|
1.0
|
create Read-me - In README:
- [x] Title
- [x] Description
- [x] user journey
- [x] how to run our project
- [x] Team members
|
non_secu
|
create read me in readme title description user journey how to run our project team members
| 0
|
21,004
| 10,565,534,925
|
IssuesEvent
|
2019-10-05 12:14:08
|
nidhisi/Postgres-11.3
|
https://api.github.com/repos/nidhisi/Postgres-11.3
|
opened
|
CVE-2019-10164 (High) detected in postgres-REL_11_3
|
security vulnerability
|
## CVE-2019-10164 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>postgresREL_11_3</b></p></summary>
<p>
<p>Mirror of the official PostgreSQL GIT repository. Note that this is just a *mirror* - we don't work with pull requests on github. To contribute, please see https://wiki.postgresql.org/wiki/Submitting_a_Patch</p>
<p>Library home page: <a href=https://github.com/postgres/postgres.git>https://github.com/postgres/postgres.git</a></p>
<p>Found in HEAD commit: <a href="https://github.com/nidhisi/Postgres-11.3/commit/5471e439dfb6d1349424c11bfae057c2c28f4e0e">5471e439dfb6d1349424c11bfae057c2c28f4e0e</a></p>
</p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Library Source Files (1118)</summary>
<p></p>
<p> * The source files were matched to this source library based on a best effort match. Source libraries are selected from a list of probable public libraries.</p>
<p>
- /Postgres-11.3/optimizer/path/equivclass.c
- /Postgres-11.3/port/inet_net_ntop.c
- /Postgres-11.3/pg_basebackup/t/030_pg_recvlogical.pl
- /Postgres-11.3/postmaster/startup.c
- /Postgres-11.3/pg_dump/dumputils.c
- /Postgres-11.3/adt/misc.c
- /Postgres-11.3/pg_upgrade/pg_upgrade.h
- /Postgres-11.3/xml2/xslt_proc.c
- /Postgres-11.3/adt/oracle_compat.c
- /Postgres-11.3/postmaster/pgstat.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_english.c
- /Postgres-11.3/adt/tsginidx.c
- /Postgres-11.3/cache/catcache.c
- /Postgres-11.3/tsearch/dict_thesaurus.c
- /Postgres-11.3/common/controldata_utils.c
- /Postgres-11.3/earthdistance/earthdistance.c
- /Postgres-11.3/pgbench/t/001_pgbench_with_server.pl
- /Postgres-11.3/adt/pg_upgrade_support.c
- /Postgres-11.3/port/win32/socket.c
- /Postgres-11.3/pg_upgrade/util.c
- /Postgres-11.3/scripts/dropuser.c
- /Postgres-11.3/psql/crosstabview.c
- /Postgres-11.3/lib/bipartite_match.c
- /Postgres-11.3/adt/char.c
- /Postgres-11.3/nodes/value.c
- /Postgres-11.3/optimizer/geqo/geqo_misc.c
- /Postgres-11.3/adt/expandedrecord.c
- /Postgres-11.3/cache/attoptcache.c
- /Postgres-11.3/sepgsql/selinux.c
- /Postgres-11.3/executor/nodeRecursiveunion.c
- /Postgres-11.3/rewrite/rewriteSupport.c
- /Postgres-11.3/hstore/hstore.h
- /Postgres-11.3/preproc/ecpg_keywords.c
- /Postgres-11.3/bloom/blvalidate.c
- /Postgres-11.3/bloom/blutils.c
- /Postgres-11.3/port/dirent.c
- /Postgres-11.3/bloom/blcost.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_portuguese.c
- /Postgres-11.3/storage/page/bufpage.c
- /Postgres-11.3/common/unicode/generate-unicode_norm_table.pl
- /Postgres-11.3/pg_dump/parallel.h
- /Postgres-11.3/test_decoding/test_decoding.c
- /Postgres-11.3/ltree/ltree_gist.c
- /Postgres-11.3/catalog/genbki.pl
- /Postgres-11.3/catalog/pg_inherits.c
- /Postgres-11.3/pg_upgrade/parallel.c
- /Postgres-11.3/mmgr/dsa.c
- /Postgres-11.3/misc/backend_random.c
- /Postgres-11.3/common/unicode_norm.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_romanian.c
- /Postgres-11.3/commands/constraint.c
- /Postgres-11.3/commands/extension.c
- /Postgres-11.3/psql/common.h
- /Postgres-11.3/time/combocid.c
- /Postgres-11.3/tools/copyright.pl
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_portuguese.c
- /Postgres-11.3/adt/quote.c
- /Postgres-11.3/plpy_exec.c
- /Postgres-11.3/commands/lockcmds.c
- /Postgres-11.3/common/string.c
- /Postgres-11.3/replication/logical/reorderbuffer.c
- /Postgres-11.3/parser/parse_agg.c
- /Postgres-11.3/pgcrypto/internal.c
- /Postgres-11.3/libpq/fe-protocol2.c
- /Postgres-11.3/ecpglib/extern.h
- /Postgres-11.3/commands/portalcmds.c
- /Postgres-11.3/adt/amutils.c
- /Postgres-11.3/pgcrypto/pgp-mpi.c
- /Postgres-11.3/jsonb_plpython/jsonb_plpython.c
- /Postgres-11.3/cache/syscache.c
- /Postgres-11.3/parser/parse_type.c
- /Postgres-11.3/libpq/fe-print.c
- /Postgres-11.3/plperl/plperl_helpers.h
- /Postgres-11.3/parser/parse_oper.c
- /Postgres-11.3/scripts/pg_isready.c
- /Postgres-11.3/nodes/readfuncs.c
- /Postgres-11.3/tools/msvc/builddoc.pl
- /Postgres-11.3/common/unicode/norm_test.c
- /Postgres-11.3/pgcrypto/crypt-gensalt.c
- /Postgres-11.3/commands/user.c
- /Postgres-11.3/parser/parse_cte.c
- /Postgres-11.3/optimizer/geqo/geqo_erx.c
- /Postgres-11.3/pgcrypto/pgp-mpi-openssl.c
- /Postgres-11.3/libpq/pqsignal.c
- /Postgres-11.3/plpy_planobject.c
- /Postgres-11.3/pg_dump/pg_backup_db.h
- /Postgres-11.3/catalog/pg_enum.c
- /Postgres-11.3/port/dynloader/netbsd.c
- /Postgres-11.3/replication/logical/launcher.c
- /Postgres-11.3/executor/nodeSubqueryscan.c
- /Postgres-11.3/snowball/dict_snowball.c
- /Postgres-11.3/storage/lmgr/lock.c
- /Postgres-11.3/preproc/ecpg.c
- /Postgres-11.3/regex/regprefix.c
- /Postgres-11.3/vacuumlo/vacuumlo.c
- /Postgres-11.3/plpy_spi.h
- /Postgres-11.3/init/postinit.c
- /Postgres-11.3/psql/startup.c
- /Postgres-11.3/include/sqlca.h
- /Postgres-11.3/storage/smgr/smgrtype.c
- /Postgres-11.3/initdb/t/001_initdb.pl
- /Postgres-11.3/preproc/extern.h
- /Postgres-11.3/port/qsort.c
- /Postgres-11.3/psql/describe.c
- /Postgres-11.3/adt/array_typanalyze.c
- /Postgres-11.3/expected/compat_informix-rfmtdate.c
- /Postgres-11.3/pg_ctl/t/001_start_stop.pl
- /Postgres-11.3/adt/cryptohashes.c
- /Postgres-11.3/cache/relmapper.c
- /Postgres-11.3/regex/regexec.c
- /Postgres-11.3/catalog/heap.c
- /Postgres-11.3/catalog/toasting.c
- /Postgres-11.3/parser/check_keywords.pl
- /Postgres-11.3/pgcrypto/pgp-mpi-internal.c
- /Postgres-11.3/regex/regc_nfa.c
- /Postgres-11.3/adt/dbsize.c
- /Postgres-11.3/adt/mac8.c
- /Postgres-11.3/executor/nodeLimit.c
- /Postgres-11.3/lib/binaryheap.c
- /Postgres-11.3/pgbench/t/002_pgbench_no_server.pl
- /Postgres-11.3/optimizer/geqo/geqo_selection.c
- /Postgres-11.3/executor/nodeSamplescan.c
- /Postgres-11.3/pgbench/pgbench.c
- /Postgres-11.3/pg_rewind/fetch.c
- /Postgres-11.3/psql/psqlscanslash.h
- /Postgres-11.3/libpq/pqexpbuffer.c
- /Postgres-11.3/plpgsql/src/generate-plerrcodes.pl
- /Postgres-11.3/pg_test_fsync/pg_test_fsync.c
- /Postgres-11.3/common/sha2_openssl.c
- /Postgres-11.3/commands/functioncmds.c
- /Postgres-11.3/adt/encode.c
- /Postgres-11.3/bootstrap/bootstrap.c
- /Postgres-11.3/catalog/pg_conversion.c
- /Postgres-11.3/jit/jit.c
- /Postgres-11.3/executor/execGrouping.c
- /Postgres-11.3/replication/walsender.c
- /Postgres-11.3/port/win32_sema.c
- /Postgres-11.3/adt/inet_net_pton.c
- /Postgres-11.3/adt/arrayutils.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_italian.c
- /Postgres-11.3/adt/array_selfuncs.c
- /Postgres-11.3/pg_upgrade/server.c
- /Postgres-11.3/tsearch/ts_utils.c
- /Postgres-11.3/nodes/equalfuncs.c
- /Postgres-11.3/pg_freespacemap/pg_freespacemap.c
- /Postgres-11.3/port/dynloader/darwin.c
- /Postgres-11.3/seg/seg.c
- /Postgres-11.3/sort/sortsupport.c
- /Postgres-11.3/common/ip.c
- /Postgres-11.3/scripts/t/102_vacuumdb_stages.pl
- /Postgres-11.3/tools/msvc/Mkvcbuild.pm
- /Postgres-11.3/pgcrypto/pgp-encrypt.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_spanish.c
- /Postgres-11.3/tsearch/dict_simple.c
- /Postgres-11.3/pgstattuple/pgstatindex.c
- /Postgres-11.3/adt/orderedsetaggs.c
- /Postgres-11.3/pg_dump/pg_backup_null.c
- /Postgres-11.3/executor/nodeNamedtuplestorescan.c
- /Postgres-11.3/ecpglib/misc.c
- /Postgres-11.3/btree_inet.c
- /Postgres-11.3/rewrite/rowsecurity.c
- /Postgres-11.3/tools/msvc/pgflex.pl
- /Postgres-11.3/unaccent/unaccent.c
- /Postgres-11.3/commands/comment.c
- /Postgres-11.3/port/dynloader/netbsd.h
- /Postgres-11.3/ltree/ltxtquery_op.c
- /Postgres-11.3/libpq/libpq-events.h
- /Postgres-11.3/executor/execProcnode.c
- /Postgres-11.3/pg_rewind/t/RewindTest.pm
- /Postgres-11.3/executor/nodeAgg.c
- /Postgres-11.3/port/win32error.c
- /Postgres-11.3/adt/uuid.c
- /Postgres-11.3/optimizer/geqo/geqo_main.c
- /Postgres-11.3/pgcrypto/px.c
- /Postgres-11.3/pg_dump/pg_dump_sort.c
- /Postgres-11.3/port/win32setlocale.c
- /Postgres-11.3/pg_dump/pg_backup_directory.c
- /Postgres-11.3/commands/typecmds.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_french.c
- /Postgres-11.3/replication/pgoutput/pgoutput.c
- /Postgres-11.3/citext/citext.c
- /Postgres-11.3/port/pg_crc32c_armv8.c
- /Postgres-11.3/pg_rewind/t/003_extrafiles.pl
- /Postgres-11.3/port/mkdtemp.c
- /Postgres-11.3/commands/indexcmds.c
- /Postgres-11.3/pgtypeslib/common.c
- /Postgres-11.3/ltree/crc32.c
- /Postgres-11.3/storage/page/checksum.c
- /Postgres-11.3/bloom/blinsert.c
- /Postgres-11.3/postmaster/fork_process.c
- /Postgres-11.3/spi/autoinc.c
- /Postgres-11.3/hash/hashfn.c
- /Postgres-11.3/plpgsql/src/pl_funcs.c
- /Postgres-11.3/sepgsql/label.c
- /Postgres-11.3/storage/ipc/procsignal.c
- /Postgres-11.3/spi/timetravel.c
- /Postgres-11.3/commands/vacuum.c
- /Postgres-11.3/misc/tzparser.c
- /Postgres-11.3/tsearch/ts_parse.c
- /Postgres-11.3/snowball/libstemmer/utilities.c
- /Postgres-11.3/adt/acl.c
- /Postgres-11.3/commands/amcmds.c
- /Postgres-11.3/initdb/initdb.c
- /Postgres-11.3/optimizer/geqo/geqo_cx.c
- /Postgres-11.3/executor/execUtils.c
- /Postgres-11.3/port/pgsleep.c
- /Postgres-11.3/tcop/utility.c
- /Postgres-11.3/pg_ctl/t/002_status.pl
- /Postgres-11.3/plpgsql/src/pl_exec.c
- /Postgres-11.3/plperl/ppport.h
- /Postgres-11.3/replication/logical/tablesync.c
- /Postgres-11.3/tsearch/regis.c
- /Postgres-11.3/pg_dump/pg_backup_tar.c
- /Postgres-11.3/btree_utils_var.c
- /Postgres-11.3/postmaster/walwriter.c
- /Postgres-11.3/libpq/libpq-fe.h
- /Postgres-11.3/commands/variable.c
- /Postgres-11.3/pg_waldump/compat.c
- /Postgres-11.3/sepgsql/dml.c
- /Postgres-11.3/scripts/t/010_clusterdb.pl
- /Postgres-11.3/plpy_subxactobject.c
- /Postgres-11.3/port/dynloader/openbsd.c
- /Postgres-11.3/port/dynloader/hpux.h
- /Postgres-11.3/tools/fix-old-flex-code.pl
- /Postgres-11.3/ecpglib/execute.c
- /Postgres-11.3/tablefunc/tablefunc.c
- /Postgres-11.3/dict_xsyn/dict_xsyn.c
- /Postgres-11.3/pg_basebackup/walmethods.h
- /Postgres-11.3/sepgsql/database.c
- /Postgres-11.3/storage/lmgr/predicate.c
- /Postgres-11.3/pgcrypto/pgcrypto.h
- /Postgres-11.3/libpq/fe-auth.h
- /Postgres-11.3/pageinspect/hashfuncs.c
- /Postgres-11.3/common/keywords.c
- /Postgres-11.3/port/getrusage.c
- /Postgres-11.3/common/username.c
- /Postgres-11.3/pg_rewind/libpq_fetch.c
- /Postgres-11.3/pgcrypto/pgp-info.c
- /Postgres-11.3/file_fdw/file_fdw.c
- /Postgres-11.3/uuid-ossp/uuid-ossp.c
- /Postgres-11.3/mmgr/portalmem.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_english.c
- /Postgres-11.3/adt/numutils.c
- /Postgres-11.3/port/pg_strong_random.c
- /Postgres-11.3/pg_controldata/t/001_pg_controldata.pl
- /Postgres-11.3/parser/analyze.c
- /Postgres-11.3/pg_waldump/pg_waldump.c
- /Postgres-11.3/commands/seclabel.c
- /Postgres-11.3/pg_trgm/trgm.h
- /Postgres-11.3/adt/levenshtein.c
- /Postgres-11.3/psql/crosstabview.h
- /Postgres-11.3/adt/float.c
- /Postgres-11.3/resowner/resowner.c
- /Postgres-11.3/intarray/_int_bool.c
- /Postgres-11.3/port/win32security.c
- /Postgres-11.3/pg_rewind/file_ops.h
- /Postgres-11.3/pg_rewind/pg_rewind.c
- /Postgres-11.3/port/tar.c
- /Postgres-11.3/executor/functions.c
- /Postgres-11.3/storage/freespace/freespace.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_spanish.c
- /Postgres-11.3/storage/file/buffile.c
- /Postgres-11.3/catalog/Catalog.pm
- /Postgres-11.3/btree_uuid.c
- /Postgres-11.3/storage/lmgr/proc.c
- /Postgres-11.3/regex/regc_lex.c
- /Postgres-11.3/regex/regc_color.c
- /Postgres-11.3/port/win32env.c
- /Postgres-11.3/libpq/fe-secure-openssl.c
- /Postgres-11.3/commands/statscmds.c
- /Postgres-11.3/parser/parse_node.c
- /Postgres-11.3/port/dynloader/cygwin.h
- /Postgres-11.3/common/file_utils.c
- /Postgres-11.3/storage/ipc/sinval.c
- /Postgres-11.3/libpq/ifaddr.c
- /Postgres-11.3/adt/like.c
- /Postgres-11.3/pg_dump/pg_backup.h
- /Postgres-11.3/adt/rangetypes_spgist.c
- /Postgres-11.3/scripts/reindexdb.c
- /Postgres-11.3/btree_ts.c
- /Postgres-11.3/bloom/blvacuum.c
- /Postgres-11.3/pgcrypto/px-crypt.h
- /Postgres-11.3/jit/llvm/llvmjit_wrap.cpp
- /Postgres-11.3/commands/aggregatecmds.c
- /Postgres-11.3/lib/dshash.c
- /Postgres-11.3/bloom/bloom.h
- /Postgres-11.3/pgcrypto/sha1.c
- /Postgres-11.3/executor/nodeForeignscan.c
- /Postgres-11.3/jit/llvm/llvmjit_error.cpp
- /Postgres-11.3/pgcrypto/pgp-armor.c
- /Postgres-11.3/parser/parser.c
- /Postgres-11.3/btree_utils_num.h
- /Postgres-11.3/pgcrypto/openssl.c
- /Postgres-11.3/tsearch/wparser.c
- /Postgres-11.3/scripts/vacuumdb.c
- /Postgres-11.3/optimizer/path/clausesel.c
- /Postgres-11.3/libpq/fe-secure.c
- /Postgres-11.3/executor/execJunk.c
- /Postgres-11.3/executor/nodeModifyTable.c
- /Postgres-11.3/btree_macaddr8.c
- /Postgres-11.3/common/exec.c
- /Postgres-11.3/plperl/plperl.c
- /Postgres-11.3/pg_dump/compress_io.h
- /Postgres-11.3/adt/jsonfuncs.c
- /Postgres-11.3/postgres_fdw/deparse.c
- /Postgres-11.3/adt/rangetypes_typanalyze.c
- /Postgres-11.3/plpy_util.c
- /Postgres-11.3/pg_controldata/pg_controldata.c
- /Postgres-11.3/commands/matview.c
- /Postgres-11.3/executor/execAmi.c
- /Postgres-11.3/libpq/pqformat.c
- /Postgres-11.3/storage/smgr/smgr.c
- /Postgres-11.3/storage/lmgr/condition_variable.c
- /Postgres-11.3/executor/execParallel.c
- /Postgres-11.3/port/win32/signal.c
- /Postgres-11.3/storage/ipc/procarray.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_finnish.c
- /Postgres-11.3/optimizer/path/joinrels.c
- /Postgres-11.3/libpq/fe-auth-scram.c
- /Postgres-11.3/statistics/mvdistinct.c
- /Postgres-11.3/adt/network_selfuncs.c
- /Postgres-11.3/pg_upgrade/pg_upgrade.c
- /Postgres-11.3/adt/tid.c
- /Postgres-11.3/mmgr/mcxt.c
- /Postgres-11.3/adt/int.c
- /Postgres-11.3/commands/proclang.c
- /Postgres-11.3/tsearch/ts_selfuncs.c
- /Postgres-11.3/adt/oid.c
- /Postgres-11.3/executor/execSRF.c
- /Postgres-11.3/fmgr/fmgr.c
- /Postgres-11.3/port/erand48.c
- /Postgres-11.3/executor/execCurrent.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_hungarian.c
- /Postgres-11.3/libpq/auth.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_turkish.c
- /Postgres-11.3/port/sysv_shmem.c
- /Postgres-11.3/commands/conversioncmds.c
- /Postgres-11.3/storage/lmgr/generate-lwlocknames.pl
- /Postgres-11.3/jsonb_plperl/jsonb_plperl.c
- /Postgres-11.3/tools/ifaddrs/test_ifaddrs.c
- /Postgres-11.3/preproc/check_rules.pl
- /Postgres-11.3/adt/int8.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_russian.c
- /Postgres-11.3/pg_upgrade/info.c
- /Postgres-11.3/parser/parse_clause.c
- /Postgres-11.3/executor/nodeCtescan.c
- /Postgres-11.3/adt/rangetypes_gist.c
- /Postgres-11.3/oid2name/oid2name.c
- /Postgres-11.3/preproc/parser.c
- /Postgres-11.3/pg_archivecleanup/pg_archivecleanup.c
- /Postgres-11.3/adt/regproc.c
- /Postgres-11.3/common/wait_error.c
- /Postgres-11.3/ltree/lquery_op.c
- /Postgres-11.3/misc/queryenvironment.c
- /Postgres-11.3/include/ecpglib.h
- /Postgres-11.3/storage/ipc/dsm.c
- /Postgres-11.3/storage/buffer/bufmgr.c
- /Postgres-11.3/common/md5.c
- /Postgres-11.3/port/getaddrinfo.c
- /Postgres-11.3/misc/guc.c
- /Postgres-11.3/auto_explain/auto_explain.c
- /Postgres-11.3/hstore_plpython/hstore_plpython.c
- /Postgres-11.3/storage/ipc/latch.c
- /Postgres-11.3/pageinspect/brinfuncs.c
- /Postgres-11.3/adt/varchar.c
- /Postgres-11.3/rewrite/rewriteDefine.c
- /Postgres-11.3/psql/create_help.pl
- /Postgres-11.3/plpython.h
- /Postgres-11.3/preproc/output.c
- /Postgres-11.3/executor/nodeSetOp.c
- /Postgres-11.3/adt/tsquery_gist.c
- /Postgres-11.3/pageinspect/btreefuncs.c
- /Postgres-11.3/snowball/libstemmer/api.c
- /Postgres-11.3/commands/trigger.c
- /Postgres-11.3/pgcrypto/imath.c
- /Postgres-11.3/regex/regerror.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_porter.c
- /Postgres-11.3/port/posix_sema.c
- /Postgres-11.3/plpy_plpymodule.c
- /Postgres-11.3/executor/nodeHashjoin.c
- /Postgres-11.3/replication/logical/worker.c
- /Postgres-11.3/tools/msvc/vcregress.pl
- /Postgres-11.3/adt/mac.c
- /Postgres-11.3/tsearch/dict_ispell.c
- /Postgres-11.3/include/pgtypes_interval.h
- /Postgres-11.3/include/ecpgerrno.h
- /Postgres-11.3/plpy_elog.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_french.c
- /Postgres-11.3/time/snapmgr.c
- /Postgres-11.3/pg_dump/pg_backup_archiver.h
- /Postgres-11.3/tcop/postgres.c
- /Postgres-11.3/catalog/objectaccess.c
- /Postgres-11.3/commands/dropcmds.c
- /Postgres-11.3/optimizer/plan/planmain.c
- /Postgres-11.3/pgcrypto/internal-sha2.c
- /Postgres-11.3/pg_rewind/file_ops.c
- /Postgres-11.3/commands/alter.c
- /Postgres-11.3/libpq/fe-lobj.c
- /Postgres-11.3/common/fe_memutils.c
- /Postgres-11.3/include/sqlda-native.h
- /Postgres-11.3/optimizer/plan/setrefs.c
- /Postgres-11.3/optimizer/plan/analyzejoins.c
- /Postgres-11.3/pg_rewind/logging.c
- /Postgres-11.3/pageinspect/ginfuncs.c
- /Postgres-11.3/regex/regc_pg_locale.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_italian.c
- /Postgres-11.3/intarray/bench/bench.pl
- /Postgres-11.3/preproc/variable.c
- /Postgres-11.3/misc/pg_controldata.c
- /Postgres-11.3/psql/large_obj.c
- /Postgres-11.3/catalog/pg_namespace.c
- /Postgres-11.3/partitioning/partbounds.c
- /Postgres-11.3/storage/ipc/shmqueue.c
- /Postgres-11.3/commands/event_trigger.c
- /Postgres-11.3/nodes/copyfuncs.c
- /Postgres-11.3/spi/insert_username.c
- /Postgres-11.3/replication/walreceiverfuncs.c
- /Postgres-11.3/fuzzystrmatch/dmetaphone.c
- /Postgres-11.3/hstore/hstore_op.c
- /Postgres-11.3/postgres_fdw/connection.c
- /Postgres-11.3/adt/network_gist.c
- /Postgres-11.3/cache/partcache.c
- /Postgres-11.3/ltree/_ltree_op.c
- /Postgres-11.3/error/elog.c
- /Postgres-11.3/pg_dump/pg_backup_archiver.c
- /Postgres-11.3/seg/seg-validate.pl
- /Postgres-11.3/libpq/fe-secure-common.h
- /Postgres-11.3/nodes/print.c
- /Postgres-11.3/port/qsort_arg.c
- /Postgres-11.3/nodes/tidbitmap.c
- /Postgres-11.3/hstore/hstore_gist.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_dutch.c
- /Postgres-11.3/pgrowlocks/pgrowlocks.c
- /Postgres-11.3/commands/vacuumlazy.c
- /Postgres-11.3/adt/nabstime.c
- /Postgres-11.3/psql/mainloop.c
- /Postgres-11.3/executor/nodeMergeAppend.c
- /Postgres-11.3/adt/domains.c
- /Postgres-11.3/tsm_system_time/tsm_system_time.c
- /Postgres-11.3/plpy_typeio.h
- /Postgres-11.3/pg_rewind/pg_rewind.h
- /Postgres-11.3/scripts/common.h
- /Postgres-11.3/timezone/pgtz.h
- /Postgres-11.3/catalog/pg_publication.c
- /Postgres-11.3/time/tqual.c
- /Postgres-11.3/expected/compat_informix-charfuncs.c
- /Postgres-11.3/pgcrypto/rijndael.c
- /Postgres-11.3/postmaster/bgwriter.c
- /Postgres-11.3/adt/varlena.c
- /Postgres-11.3/libpq/libpq-int.h
- /Postgres-11.3/adt/geo_ops.c
- /Postgres-11.3/expected/compat_informix-describe.c
- /Postgres-11.3/cache/plancache.c
- /Postgres-11.3/sort/sharedtuplestore.c
- /Postgres-11.3/fmgr/dfmgr.c
- /Postgres-11.3/Gen_dummy_probes.pl
- /Postgres-11.3/executor/nodeMergejoin.c
- /Postgres-11.3/pg_rewind/filemap.c
- /Postgres-11.3/psql/settings.h
- /Postgres-11.3/unaccent/generate_unaccent_rules.py
- /Postgres-11.3/scripts/createuser.c
- /Postgres-11.3/cache/lsyscache.c
- /Postgres-11.3/scripts/t/020_createdb.pl
- /Postgres-11.3/port/win32_shmem.c
- /Postgres-11.3/plpy_procedure.h
- /Postgres-11.3/port/sysv_sema.c
- /Postgres-11.3/pg_resetwal/pg_resetwal.c
- /Postgres-11.3/expected/compat_oracle-char_array.c
- /Postgres-11.3/optimizer/geqo/geqo_ox2.c
- /Postgres-11.3/ltree/ltxtquery_io.c
- /Postgres-11.3/adt/datum.c
- /Postgres-11.3/timezone/pgtz.c
- /Postgres-11.3/pg_rewind/copy_fetch.c
- /Postgres-11.3/mmgr/slab.c
- /Postgres-11.3/pageinspect/heapfuncs.c
- /Postgres-11.3/scripts/common.c
- /Postgres-11.3/pg_rewind/filemap.h
- /Postgres-11.3/tools/msvc/Solution.pm
- /Postgres-11.3/timezone/private.h
- /Postgres-11.3/adt/format_type.c
- /Postgres-11.3/sort/tuplestore.c
- /Postgres-11.3/catalog/pg_constraint.c
- /Postgres-11.3/port/dirmod.c
- /Postgres-11.3/jit/llvm/llvmjit_types.c
- /Postgres-11.3/regex/regfree.c
- /Postgres-11.3/replication/logical/origin.c
- /Postgres-11.3/storage/file/fd.c
- /Postgres-11.3/catalog/pg_shdepend.c
- /Postgres-11.3/tsearch/ts_typanalyze.c
- /Postgres-11.3/hstore_plperl/hstore_plperl.c
- /Postgres-11.3/spi/refint.c
- /Postgres-11.3/expected/compat_informix-rfmtlong.c
- /Postgres-11.3/adt/geo_selfuncs.c
- /Postgres-11.3/postmaster/autovacuum.c
- /Postgres-11.3/commands/analyze.c
- /Postgres-11.3/lib/ilist.c
- /Postgres-11.3/bloom/blscan.c
- /Postgres-11.3/lib/pairingheap.c
- /Postgres-11.3/commands/tsearchcmds.c
- /Postgres-11.3/port/pgcheckdir.c
- /Postgres-11.3/hstore/hstore_compat.c
- /Postgres-11.3/regex/regcomp.c
- /Postgres-11.3/intarray/_int.h
- /Postgres-11.3/adt/jsonb.c
- /Postgres-11.3/adt/tsquery.c
- /Postgres-11.3/pg_dump/pg_backup_utils.c
- /Postgres-11.3/preproc/c_keywords.c
- /Postgres-11.3/pg_visibility/pg_visibility.c
- /Postgres-11.3/port/getopt.c
- /Postgres-11.3/misc/pg_config.c
- /Postgres-11.3/include/pgtypes_timestamp.h
- /Postgres-11.3/hstore/hstore_io.c
- /Postgres-11.3/auth_delay/auth_delay.c
- /Postgres-11.3/catalog/pg_depend.c
- /Postgres-11.3/pgcrypto/mbuf.c
- /Postgres-11.3/plpgsql/src/pl_comp.c
- /Postgres-11.3/tools/msvc/pgbison.pl
- /Postgres-11.3/pageinspect/fsmfuncs.c
- /Postgres-11.3/psql/prompt.c
- /Postgres-11.3/optimizer/geqo/geqo_mutation.c
- /Postgres-11.3/adt/tsquery_op.c
- /Postgres-11.3/pgcrypto/pgp.c
- /Postgres-11.3/catalog/pg_type.c
- /Postgres-11.3/statistics/dependencies.c
- /Postgres-11.3/pgcrypto/crypt-md5.c
- /Postgres-11.3/pgcrypto/crypt-des.c
- /Postgres-11.3/optimizer/plan/initsplan.c
- /Postgres-11.3/expected/compat_informix-test_informix.c
- /Postgres-11.3/port/snprintf.c
- /Postgres-11.3/mmgr/freepage.c
- /Postgres-11.3/sepgsql/sepgsql.h
- /Postgres-11.3/adt/jsonb_util.c
- /Postgres-11.3/fe_utils/mbprint.c
- /Postgres-11.3/src/sgml/mk_feature_tables.pl
- /Postgres-11.3/pg_trgm/trgm_op.c
- /Postgres-11.3/pg_rewind/datapagemap.h
- /Postgres-11.3/common/relpath.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_porter.c
- /Postgres-11.3/preproc/type.c
- /Postgres-11.3/executor/nodeGroup.c
- /Postgres-11.3/init/globals.c
- /Postgres-11.3/parser/parse_coerce.c
- /Postgres-11.3/tools/msvc/Install.pm
- /Postgres-11.3/pgcrypto/blf.h
- /Postgres-11.3/adt/ri_triggers.c
- /Postgres-11.3/common/rmtree.c
- /Postgres-11.3/port/strlcpy.c
- /Postgres-11.3/storage/smgr/md.c
- /Postgres-11.3/parser/parse_target.c
- /Postgres-11.3/optimizer/path/joinpath.c
- /Postgres-11.3/fuzzystrmatch/fuzzystrmatch.c
- /Postgres-11.3/libpq/fe-exec.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_swedish.c
- /Postgres-11.3/pg_basebackup/streamutil.h
- /Postgres-11.3/btree_utils_num.c
- /Postgres-11.3/optimizer/plan/planner.c
- /Postgres-11.3/pg_upgrade/file.c
- /Postgres-11.3/common/config_info.c
- /Postgres-11.3/fmgr/funcapi.c
- /Postgres-11.3/include/ecpgtype.h
- /Postgres-11.3/catalog/namespace.c
- /Postgres-11.3/adt/pgstatfuncs.c
- /Postgres-11.3/optimizer/plan/createplan.c
- /Postgres-11.3/jit/llvm/llvmjit_expr.c
- /Postgres-11.3/parser/parse_expr.c
- /Postgres-11.3/libpq/test/uri-regress.c
- /Postgres-11.3/hash/dynahash.c
- /Postgres-11.3/expected/compat_informix-rnull.c
- /Postgres-11.3/port/fseeko.c
- /Postgres-11.3/libpq/fe-protocol3.c
- /Postgres-11.3/ecpglib/prepare.c
- /Postgres-11.3/tools/msvc/install.pl
- /Postgres-11.3/optimizer/geqo/geqo_ox1.c
- /Postgres-11.3/pg_dump/pg_backup_db.c
- /Postgres-11.3/commands/createas.c
- /Postgres-11.3/executor/execScan.c
- /Postgres-11.3/sepgsql/hooks.c
- /Postgres-11.3/libpq/fe-secure-common.c
- /Postgres-11.3/plpy_main.c
- /Postgres-11.3/port/pg_crc32c_armv8_choose.c
- /Postgres-11.3/ecpglib/memory.c
- /Postgres-11.3/psql/describe.h
- /Postgres-11.3/pgcrypto/px.h
- /Postgres-11.3/adt/pg_lsn.c
- /Postgres-11.3/replication/slot.c
- /Postgres-11.3/pg_dump/pg_dump.c
- /Postgres-11.3/libpq/auth-scram.c
- /Postgres-11.3/executor/nodeProjectSet.c
- /Postgres-11.3/executor/execExpr.c
- /Postgres-11.3/cache/spccache.c
- /Postgres-11.3/statistics/extended_stats.c
- /Postgres-11.3/executor/nodeAppend.c
- /Postgres-11.3/pgstattuple/pgstattuple.c
- /Postgres-11.3/plpy_main.h
- /Postgres-11.3/adt/ruleutils.c
- /Postgres-11.3/plperl/plc_perlboot.pl
- /Postgres-11.3/pg_buffercache/pg_buffercache_pages.c
- /Postgres-11.3/adt/tsquery_rewrite.c
- /Postgres-11.3/preproc/keywords.c
- /Postgres-11.3/libpq/fe-misc.c
- /Postgres-11.3/commands/define.c
- /Postgres-11.3/port/dynloader/freebsd.c
- /Postgres-11.3/ecpglib/error.c
- /Postgres-11.3/pgcrypto/pgcrypto.c
- /Postgres-11.3/optimizer/geqo/geqo_pmx.c
- /Postgres-11.3/scripts/t/200_connstr.pl
- /Postgres-11.3/regex/regc_locale.c
- /Postgres-11.3/executor/nodeHash.c
- /Postgres-11.3/catalog/pg_subscription.c
- /Postgres-11.3/misc/sampling.c
- /Postgres-11.3/compatlib/informix.c
- /Postgres-11.3/psql/stringutils.c
- /Postgres-11.3/port/open.c
- /Postgres-11.3/replication/basebackup.c
- /Postgres-11.3/psql/copy.c
- /Postgres-11.3/pgcrypto/pgp-pgsql.c
- /Postgres-11.3/ltree/ltree.h
- /Postgres-11.3/pageinspect/rawpage.c
- /Postgres-11.3/commands/opclasscmds.c
- /Postgres-11.3/psql/input.h
- /Postgres-11.3/pg_basebackup/receivelog.h
- /Postgres-11.3/optimizer/geqo/geqo_random.c
- /Postgres-11.3/adt/pseudotypes.c
- /Postgres-11.3/plpy_subxactobject.h
- /Postgres-11.3/libpq/pthread-win32.c
- /Postgres-11.3/replication/libpqwalreceiver/libpqwalreceiver.c
- /Postgres-11.3/commands/sequence.c
- /Postgres-11.3/adt/bool.c
- /Postgres-11.3/storage/file/reinit.c
- /Postgres-11.3/port/dynloader/linux.h
- /Postgres-11.3/adt/array_userfuncs.c
- /Postgres-11.3/port/dynloader/solaris.h
- /Postgres-11.3/pg_dump/pg_backup_custom.c
- /Postgres-11.3/parser/parse_relation.c
- /Postgres-11.3/tools/findoidjoins/findoidjoins.c
- /Postgres-11.3/parser/parse_enr.c
- /Postgres-11.3/pgcrypto/pgp-decrypt.c
- /Postgres-11.3/psql/stringutils.h
- /Postgres-11.3/libpq/be-secure.c
- /Postgres-11.3/btree_time.c
- /Postgres-11.3/plpy_elog.h
- /Postgres-11.3/pg_upgrade/tablespace.c
- /Postgres-11.3/executor/nodeGatherMerge.c
- /Postgres-11.3/pgtypeslib/extern.h
- /Postgres-11.3/libpq/be-fsstubs.c
- /Postgres-11.3/replication/logical/proto.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_hungarian.c
- /Postgres-11.3/port/sprompt.c
- /Postgres-11.3/libpq/be-secure-common.c
- /Postgres-11.3/pgevent/pgevent.c
- /Postgres-11.3/btree_gist.c
- /Postgres-11.3/executor/nodeBitmapAnd.c
- /Postgres-11.3/plperl/plperl.h
- /Postgres-11.3/adt/date.c
- /Postgres-11.3/nodes/list.c
- /Postgres-11.3/optimizer/path/indxpath.c
- /Postgres-11.3/adt/timestamp.c
- /Postgres-11.3/btree_float8.c
- /Postgres-11.3/tsearch/dict.c
- /Postgres-11.3/catalog/pg_largeobject.c
- /Postgres-11.3/intarray/_int_op.c
- /Postgres-11.3/executor/execIndexing.c
- /Postgres-11.3/timezone/zic.c
- /Postgres-11.3/pg_rewind/t/004_pg_xlog_symlink.pl
- /Postgres-11.3/generate-spiexceptions.pl
- /Postgres-11.3/adt/inet_cidr_ntop.c
- /Postgres-11.3/commands/policy.c
- /Postgres-11.3/commands/tablespace.c
- /Postgres-11.3/adt/numeric.c
- /Postgres-11.3/storage/ipc/shmem.c
- /Postgres-11.3/lo/lo.c
- /Postgres-11.3/btree_int2.c
- /Postgres-11.3/adt/pg_locale.c
- /Postgres-11.3/sort/logtape.c
- /Postgres-11.3/libpq/hba.c
- /Postgres-11.3/cache/ts_cache.c
- /Postgres-11.3/pgevent/pgmsgevent.h
- /Postgres-11.3/storage/ipc/sinvaladt.c
- /Postgres-11.3/btree_utils_var.h
- /Postgres-11.3/port/pgmkdirp.c
- /Postgres-11.3/fe_utils/simple_list.c
- /Postgres-11.3/psql/variables.h
- /Postgres-11.3/postgres_fdw/postgres_fdw.c
- /Postgres-11.3/plpy_cursorobject.c
- /Postgres-11.3/commands/publicationcmds.c
- /Postgres-11.3/optimizer/path/pathkeys.c
- /Postgres-11.3/postmaster/pgarch.c
- /Postgres-11.3/commands/view.c
- /Postgres-11.3/storage/ipc/shm_toc.c
- /Postgres-11.3/common/base64.c
- /Postgres-11.3/adt/rangetypes.c
- /Postgres-11.3/tools/msvc/VCBuildProject.pm
- /Postgres-11.3/commands/copy.c
- /Postgres-11.3/tools/msvc/MSBuildProject.pm
- /Postgres-11.3/storage/file/sharedfileset.c
- /Postgres-11.3/adt/selfuncs.c
- /Postgres-11.3/parser/parse_collate.c
- /Postgres-11.3/cache/typcache.c
- /Postgres-11.3/psql/tab-complete.c
- /Postgres-11.3/pg_test_timing/pg_test_timing.c
- /Postgres-11.3/executor/instrument.c
- /Postgres-11.3/tsm_system_rows/tsm_system_rows.c
- /Postgres-11.3/storage/lmgr/s_lock.c
- /Postgres-11.3/adt/genfile.c
- /Postgres-11.3/pgcrypto/md5.c
- /Postgres-11.3/catalog/aclchk.c
- /Postgres-11.3/port/path.c
- /Postgres-11.3/executor/execMain.c
- /Postgres-11.3/adt/tsgistidx.c
- /Postgres-11.3/pgcrypto/px-crypt.c
- /Postgres-11.3/pg_upgrade/exec.c
- /Postgres-11.3/executor/execTuples.c
- /Postgres-11.3/catalog/dependency.c
- /Postgres-11.3/pg_upgrade/dump.c
- /Postgres-11.3/storage/lmgr/lmgr.c
- /Postgres-11.3/preproc/type.h
- /Postgres-11.3/include/sqlda-compat.h
- /Postgres-11.3/fe_utils/conditional.c
- /Postgres-11.3/libpq/pqmq.c
- /Postgres-11.3/cube/cube.c
- /Postgres-11.3/optimizer/geqo/geqo_pool.c
- /Postgres-11.3/replication/logical/message.c
- /Postgres-11.3/common/pg_lzcompress.c
- /Postgres-11.3/tools/msvc/config_default.pl
- /Postgres-11.3/include/pgtypes_date.h
- /Postgres-11.3/adt/json.c
- /Postgres-11.3/ecpglib/data.c
- /Postgres-11.3/btree_bytea.c
- /Postgres-11.3/pg_archivecleanup/t/010_pg_archivecleanup.pl
- /Postgres-11.3/executor/nodeSubplan.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_swedish.c
- /Postgres-11.3/tcn/tcn.c
- /Postgres-11.3/optimizer/geqo/geqo_recombination.c
- /Postgres-11.3/pg_rewind/t/002_databases.pl
- /Postgres-11.3/pgcrypto/pgp-pubkey.c
- /Postgres-11.3/pg_ctl/t/003_promote.pl
- /Postgres-11.3/common/unicode/generate-norm_test_table.pl
- /Postgres-11.3/ltree/_ltree_gist.c
- /Postgres-11.3/mmgr/generation.c
- /Postgres-11.3/timezone/strftime.c
- /Postgres-11.3/adt/network.c
- /Postgres-11.3/nodes/read.c
- /Postgres-11.3/tutorial/funcs_new.c
- /Postgres-11.3/adt/expandeddatum.c
- /Postgres-11.3/pg_config/t/001_pg_config.pl
- /Postgres-11.3/pg_dump/parallel.c
- /Postgres-11.3/replication/logical/snapbuild.c
- /Postgres-11.3/nodes/bitmapset.c
- /Postgres-11.3/adt/jsonb_op.c
- /Postgres-11.3/pg_basebackup/streamutil.c
- /Postgres-11.3/rewrite/rewriteHandler.c
- /Postgres-11.3/pgtypeslib/dt.h
- /Postgres-11.3/storage/freespace/indexfsm.c
- /Postgres-11.3/pg_config/pg_config.c
- /Postgres-11.3/plperl/text2macro.pl
- /Postgres-11.3/nodes/nodeFuncs.c
- /Postgres-11.3/mmgr/memdebug.c
- /Postgres-11.3/pg_basebackup/t/020_pg_receivewal.pl
- /Postgres-11.3/pgcrypto/sha1.h
- /Postgres-11.3/intarray/_intbig_gist.c
- /Postgres-11.3/storage/ipc/shm_mq.c
- /Postgres-11.3/pgcrypto/pgp-compress.c
- /Postgres-11.3/port/getopt_long.c
- /Postgres-11.3/port/noblock.c
- /Postgres-11.3/catalog/index.c
- /Postgres-11.3/port/getpeereid.c
- /Postgres-11.3/pg_trgm/trgm_regexp.c
- /Postgres-11.3/commands/dbcommands.c
- /Postgres-11.3/adt/tsvector_op.c
- /Postgres-11.3/plpy_typeio.c
- /Postgres-11.3/libpq/pqcomm.c
- /Postgres-11.3/storage/buffer/buf_init.c
- /Postgres-11.3/pgtypeslib/datetime.c
- /Postgres-11.3/adt/trigfuncs.c
- /Postgres-11.3/libpq/crypt.c
- /Postgres-11.3/pg_basebackup/t/010_pg_basebackup.pl
- /Postgres-11.3/port/fls.c
- /Postgres-11.3/nodes/extensible.c
- /Postgres-11.3/catalog/pg_aggregate.c
- /Postgres-11.3/adt/regexp.c
- /Postgres-11.3/regex/regc_cvec.c
- /Postgres-11.3/error/assert.c
- /Postgres-11.3/scripts/t/100_vacuumdb.pl
- /Postgres-11.3/cube/cubedata.h
- /Postgres-11.3/adt/rangetypes_selfuncs.c
- /Postgres-11.3/optimizer/path/tidpath.c
- /Postgres-11.3/pg_dump/pg_backup_tar.h
- /Postgres-11.3/sepgsql/relation.c
- /Postgres-11.3/nodes/nodes.c
- /Postgres-11.3/port/chklocale.c
- /Postgres-11.3/misc/rls.c
- /Postgres-11.3/rewrite/rewriteRemove.c
- /Postgres-11.3/libpq/fe-auth.c
- /Postgres-11.3/snowball/libstemmer/stem_KOI8_R_russian.c
- /Postgres-11.3/catalog/indexing.c
- /Postgres-11.3/libpq/libpq-events.c
- /Postgres-11.3/initdb/findtimezone.c
- /Postgres-11.3/adt/tsvector_parser.c
- /Postgres-11.3/libpq/pqexpbuffer.h
- /Postgres-11.3/port/isinf.c
- /Postgres-11.3/pg_dump/pg_dump.h
- /Postgres-11.3/tablefunc/tablefunc.h
- /Postgres-11.3/executor/nodeFunctionscan.c
- /Postgres-11.3/cache/evtcache.c
- /Postgres-11.3/preproc/descriptor.c
- /Postgres-11.3/ecpglib/connect.c
- /Postgres-11.3/tools/msvc/gendef.pl
- /Postgres-11.3/storage/buffer/localbuf.c
- /Postgres-11.3/adt/arrayfuncs.c
- /Postgres-11.3/misc/ps_status.c
- /Postgres-11.3/psql/variables.c
- /Postgres-11.3/adt/name.c
- /Postgres-11.3/btree_cash.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_2_romanian.c
- /Postgres-11.3/lib/hyperloglog.c
- /Postgres-11.3/pgcrypto/crypt-blowfish.c
- /Postgres-11.3/storage/ipc/standby.c
- /Postgres-11.3/pg_trgm/trgm_gin.c
- /Postgres-11.3/port/quotes.c
- /Postgres-11.3/plpgsql/src/pl_scanner.c
- /Postgres-11.3/common/scram-common.c
- /Postgres-11.3/tcop/pquery.c
- /Postgres-11.3/pgcrypto/imath.h
- /Postgres-11.3/psql/command.c
- /Postgres-11.3/lib/bloomfilter.c
- /Postgres-11.3/intarray/_int_gist.c
- /Postgres-11.3/sepgsql/uavc.c
- /Postgres-11.3/adt/tsquery_cleanup.c
- /Postgres-11.3/plpy_resultobject.c
- /Postgres-11.3/storage/lmgr/lwlock.c
- /Postgres-11.3/optimizer/geqo/geqo_px.c
- /Postgres-11.3/nodes/params.c
- /Postgres-11.3/replication/logical/decode.c
- /Postgres-11.3/sepgsql/schema.c
- /Postgres-11.3/commands/operatorcmds.c
- /Postgres-11.3/executor/nodeSort.c
- /Postgres-11.3/catalog/pg_range.c
- /Postgres-11.3/adt/tsquery_util.c
- /Postgres-11.3/pg_upgrade/option.c
- /Postgres-11.3/libpq/fe-connect.c
- /Postgres-11.3/postmaster/checkpointer.c
- /Postgres-11.3/executor/execExprInterp.c
- /Postgres-11.3/jit/llvm/llvmjit.c
- /Postgres-11.3/pg_rewind/timeline.c
- /Postgres-11.3/pg_dump/pg_restore.c
- /Postgres-11.3/nodes/outfuncs.c
- /Postgres-11.3/include/sql3types.h
- /Postgres-11.3/port/atomics.c
- /Postgres-11.3/jit/llvm/llvmjit_inline.cpp
- /Postgres-11.3/scripts/createdb.c
- /Postgres-11.3/adt/tsvector.c
- /Postgres-11.3/pg_upgrade/version.c
- /Postgres-11.3/pg_prewarm/pg_prewarm.c
- /Postgres-11.3/executor/nodeIndexscan.c
- /Postgres-11.3/executor/nodeGather.c
- /Postgres-11.3/pg_basebackup/pg_receivewal.c
- /Postgres-11.3/pgcrypto/pgp-cfb.c
- /Postgres-11.3/psql/command.h
- /Postgres-11.3/btree_date.c
- /Postgres-11.3/storage/large_object/inv_api.c
- /Postgres-11.3/tools/check_bison_recursion.pl
- /Postgres-11.3/pg_dump/pg_dumpall.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_norwegian.c
- /Postgres-11.3/catalog/catalog.c
- /Postgres-11.3/cache/inval.c
- /Postgres-11.3/executor/nodeResult.c
- /Postgres-11.3/tcop/dest.c
- /Postgres-11.3/postgres_fdw/option.c
- /Postgres-11.3/executor/nodeBitmapIndexscan.c
- /Postgres-11.3/adt/tsrank.c
- /Postgres-11.3/psql/help.c
- /Postgres-11.3/tcop/fastpath.c
- /Postgres-11.3/replication/logical/logical.c
- /Postgres-11.3/port/strlcat.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_danish.c
- /Postgres-11.3/sslinfo/sslinfo.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_norwegian.c
- /Postgres-11.3/pg_standby/pg_standby.c
- /Postgres-11.3/port/crypt.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_finnish.c
- /Postgres-11.3/bloom/t/001_wal.pl
- /Postgres-11.3/postmaster/postmaster.c
- /Postgres-11.3/main/main.c
- /Postgres-11.3/pg_ctl/pg_ctl.c
- /Postgres-11.3/pgcrypto/md5.h
- /Postgres-11.3/pg_rewind/fetch.h
- /Postgres-11.3/pgstattuple/pgstatapprox.c
- /Postgres-11.3/generate-errcodes.pl
- /Postgres-11.3/executor/nodeMaterial.c
- /Postgres-11.3/tsearch/ts_locale.c
- /Postgres-11.3/common/saslprep.c
- /Postgres-11.3/storage/lmgr/deadlock.c
- /Postgres-11.3/pg_dump/t/002_pg_dump.pl
- /Postgres-11.3/tutorial/complex.c
- /Postgres-11.3/misc/help_config.c
- /Postgres-11.3/foreign/foreign.c
- /Postgres-11.3/sort/gen_qsort_tuple.pl
- /Postgres-11.3/common/restricted_token.c
- /Postgres-11.3/pgcrypto/px-hmac.c
- /Postgres-11.3/adt/txid.c
- /Postgres-11.3/ecpglib/sqlda.c
- /Postgres-11.3/btree_text.c
- /Postgres-11.3/pg_rewind/logging.h
- /Postgres-11.3/commands/tablecmds.c
- /Postgres-11.3/postgres_fdw/shippable.c
- /Postgres-11.3/sepgsql/proc.c
- /Postgres-11.3/expected/connect-test1.c
- /Postgres-11.3/mmgr/aset.c
- /Postgres-11.3/storage/ipc/barrier.c
- /Postgres-11.3/port/dynloader/win32.c
- /Postgres-11.3/adt/array_expanded.c
- /Postgres-11.3/replication/walreceiver.c
- /Postgres-11.3/partitioning/partprune.c
- /Postgres-11.3/catalog/pg_db_role_setting.c
- /Postgres-11.3/executor/nodeCustom.c
- /Postgres-11.3/lib/knapsack.c
- /Postgres-11.3/adt/datetime.c
- /Postgres-11.3/spi/moddatetime.c
- /Postgres-11.3/misc/superuser.c
- /Postgres-11.3/pg_upgrade/check.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_german.c
- /Postgres-11.3/port/pg_crc32c_sse42_choose.c
- /Postgres-11.3/replication/syncrep.c
- /Postgres-11.3/pg_waldump/rmgrdesc.c
- /Postgres-11.3/include/pgtypes_numeric.h
- /Postgres-11.3/tools/msvc/VSObjectFactory.pm
- /Postgres-11.3/plperl/plperl_opmask.pl
- /Postgres-11.3/optimizer/plan/planagg.c
- /Postgres-11.3/port/system.c
- /Postgres-11.3/plpy_spi.c
- /Postgres-11.3/btree_enum.c
- /Postgres-11.3/pg_upgrade/function.c
- /Postgres-11.3/fe_utils/string_utils.c
- /Postgres-11.3/pgcrypto/mbuf.h
- /Postgres-11.3/pg_basebackup/walmethods.c
- /Postgres-11.3/tools/msvc/Project.pm
- /Postgres-11.3/timezone/tzfile.h
- /Postgres-11.3/storage/lmgr/spin.c
- /Postgres-11.3/pg_upgrade/controldata.c
- /Postgres-11.3/src/sgml/generate-errcodes-table.pl
- /Postgres-11.3/pg_rewind/parsexlog.c
- /Postgres-11.3/libpq/win32.h
- /Postgres-11.3/libpq/be-secure-openssl.c
- /Postgres-11.3/executor/nodeBitmapHeapscan.c
- /Postgres-11.3/misc/timeout.c
- /Postgres-11.3/plpgsql/src/plpgsql.h
- /Postgres-11.3/btree_int4.c
- /Postgres-11.3/replication/logical/relation.c
- /Postgres-11.3/adt/cash.c
- /Postgres-11.3/pg_basebackup/pg_recvlogical.c
- /Postgres-11.3/pg_prewarm/autoprewarm.c
- /Postgres-11.3/storage/ipc/pmsignal.c
- /Postgres-11.3/common/pgfnames.c
- /Postgres-11.3/jit/llvm/llvmjit_deform.c
- /Postgres-11.3/commands/cluster.c
- /Postgres-11.3/commands/explain.c
- /Postgres-11.3/executor/nodeNestloop.c
- /Postgres-11.3/plpy_procedure.c
- /Postgres-11.3/port/win32/crashdump.c
- /Postgres-11.3/regex/regexport.c
- /Postgres-11.3/preproc/parse.pl
- /Postgres-11.3/tsearch/spell.c
- /Postgres-11.3/port/dynloader/hpux.c
- /Postgres-11.3/tsearch/to_tsany.c
- /Postgres-11.3/pg_regress_ecpg.c
- /Postgres-11.3/catalog/pg_collation.c
- /Postgres-11.3/catalog/objectaddress.c
- /Postgres-11.3/psql/input.c
- /Postgres-11.3/commands/foreigncmds.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_danish.c
- /Postgres-11.3/pgcrypto/rijndael.h
- /Postgres-11.3/expected/compat_informix-dec_test.c
- /Postgres-11.3/port/kill.c
- /Postgres-11.3/adminpack/adminpack.c
- /Postgres-11.3/commands/prepare.c
- /Postgres-11.3/sort/tuplesort.c
- /Postgres-11.3/catalog/partition.c
- /Postgres-11.3/parser/scansup.c
- /Postgres-11.3/expected/compat_informix-test_informix2.c
- /Postgres-11.3/pgbench/pgbench.h
- /Postgres-11.3/scripts/t/040_createuser.pl
- /Postgres-11.3/storage/ipc/ipci.c
- /Postgres-11.3/executor/nodeIndexonlyscan.c
- /Postgres-11.3/pg_verify_checksums/pg_verify_checksums.c
- /Postgres-11.3/pgtypeslib/dt_common.c
- /Postgres-11.3/adt/enum.c
- /Postgres-11.3/executor/execReplication.c
- /Postgres-11.3/executor/nodeLockRows.c
- /Postgres-11.3/intarray/_int_gin.c
- /Postgres-11.3/commands/discard.c
- /Postgres-11.3/pg_dump/t/010_dump_connstr.pl
- /Postgres-11.3/common/psprintf.c
- /Postgres-11.3/pg_dump/dumputils.h
- /Postgres-11.3/commands/subscriptioncmds.c
- /Postgres-11.3/pg_dump/t/001_basic.pl
- /Postgres-11.3/libpq/win32.c
- /Postgres-11.3/executor/nodeBitmapOr.c
- /Postgres-11.3/port/thread.c
- /Postgres-11.3/adt/rowtypes.c
- /Postgres-11.3/port/dynloader/linux.c
- /Postgres-11.3/port/unsetenv.c
- /Postgres-11.3/pgcrypto/blf.c
- /Postgres-11.3/commands/schemacmds.c
- /Postgres-11.3/port/rint.c
- /Postgres-11.3/storage/page/itemptr.c
- /Postgres-11.3/optimizer/path/allpaths.c
- /Postgres-11.3/pg_stat_statements/pg_stat_statements.c
- /Postgres-11.3/btree_macaddr.c
- /Postgres-11.3/include/ecpg-pthread-win32.h
- /Postgres-11.3/port/pqsignal.c
- /Postgres-11.3/executor/execPartition.c
- /Postgres-11.3/storage/file/copydir.c
- /Postgres-11.3/postmaster/syslogger.c
- /Postgres-11.3/pg_dump/pg_backup_utils.h
- /Postgres-11.3/storage/buffer/buf_table.c
- /Postgres-11.3/ecpglib/typename.c
- /Postgres-11.3/pg_resetwal/t/002_corrupted.pl
- /Postgres-11.3/catalog/storage.c
- /Postgres-11.3/cache/relcache.c
- /Postgres-11.3/adt/formatting.c
- /Postgres-11.3/intarray/bench/create_test.pl
- /Postgres-11.3/pg_dump/compress_io.c
- /Postgres-11.3/commands/async.c
- /Postgres-11.3/plperl/plc_trusted.pl
- /Postgres-11.3/optimizer/plan/subselect.c
- /Postgres-11.3/port/dynloader/openbsd.h
- /Postgres-11.3/tools/msvc/build.pl
- /Postgres-11.3/parser/parse_func.c
- /Postgres-11.3/replication/logical/logicalfuncs.c
- /Postgres-11.3/port/dynloader/freebsd.h
- /Postgres-11.3/pgcrypto/pgp-s2k.c
- /Postgres-11.3/nodes/makefuncs.c
- /Postgres-11.3/btree_oid.c
- /Postgres-11.3/common/sha2.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_german.c
- /Postgres-11.3/timezone/localtime.c
- /Postgres-11.3/pg_basebackup/pg_basebackup.c
- /Postgres-11.3/pgtypeslib/interval.c
- /Postgres-11.3/pgcrypto/pgp-pubenc.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_dutch.c
- /Postgres-11.3/storage/freespace/fsmpage.c
- /Postgres-11.3/port/inet_aton.c
- /Postgres-11.3/ecpglib/descriptor.c
- /Postgres-11.3/optimizer/path/costsize.c
- /Postgres-11.3/port/win32/mingwcompat.c
- /Postgres-11.3/executor/nodeSeqscan.c
- /Postgres-11.3/psql/common.c
- /Postgres-11.3/adt/like_match.c
- /Postgres-11.3/regex/rege_dfa.c
- /Postgres-11.3/adt/ascii.c
- /Postgres-11.3/catalog/pg_operator.c
- /Postgres-11.3/replication/slotfuncs.c
- /Postgres-11.3/pg_trgm/trgm_gist.c
- /Postgres-11.3/postgres_fdw/postgres_fdw.h
- /Postgres-11.3/catalog/pg_proc.c
- /Postgres-11.3/optimizer/prep/prepjointree.c
- /Postgres-11.3/btree_numeric.c
- /Postgres-11.3/pg_dump/common.c
- /Postgres-11.3/pg_upgrade/relfilenode.c
- /Postgres-11.3/port/pg_crc32c_sse42.c
- /Postgres-11.3/include/ecpg_informix.h
- /Postgres-11.3/lib/stringinfo.c
- /Postgres-11.3/pgtypeslib/timestamp.c
- /Postgres-11.3/optimizer/geqo/geqo_copy.c
- /Postgres-11.3/rewrite/rewriteManip.c
- /Postgres-11.3/adt/varbit.c
- /Postgres-11.3/misc/pg_rusage.c
- /Postgres-11.3/hash/pg_crc.c
- /Postgres-11.3/btree_bit.c
- /Postgres-11.3/port/pg_crc32c_sb8.c
- /Postgres-11.3/ltree/ltree_io.c
- /Postgres-11.3/pgcrypto/pgp-pubdec.c
- /Postgres-11.3/btree_interval.c
- /Postgres-11.3/pg_rewind/datapagemap.c
- /Postgres-11.3/pg_rewind/t/001_basic.pl
- /Postgres-11.3/adt/jsonb_gin.c
- /Postgres-11.3/pg_basebackup/receivelog.c
- /Postgres-11.3/commands/collationcmds.c
- /Postgres-11.3/port/strnlen.c
- /Postgres-11.3/adt/geo_spgist.c
- /Postgres-11.3/expected/compat_informix-sqlda.c
- /Postgres-11.3/postmaster/bgworker.c
- /Postgres-11.3/scripts/t/090_reindexdb.pl
- /Postgres-11.3/common/file_perm.c
- /Postgres-11.3/hstore/hstore_gin.c
- /Postgres-11.3/port/pgstrcasecmp.c
- /Postgres-11.3/storage/ipc/ipc.c
- /Postgres-11.3/xml2/xpath.c
- /Postgres-11.3/pgtypeslib/numeric.c
- /Postgres-11.3/ltree/ltree_op.c
- /Postgres-11.3/amcheck/verify_nbtree.c
- /Postgres-11.3/init/miscinit.c
- /Postgres-11.3/tutorial/funcs.c
- /Postgres-11.3/storage/buffer/freelist.c
- /Postgres-11.3/tsearch/dict_synonym.c
- /Postgres-11.3/adt/network_spgist.c
- /Postgres-11.3/tsearch/wparser_def.c
- /Postgres-11.3/btree_int8.c
- /Postgres-11.3/port/dynloader/aix.h
- /Postgres-11.3/storage/ipc/dsm_impl.c
- /Postgres-11.3/libpq/test/regress.pl
- /Postgres-11.3/parser/parse_utilcmd.c
- /Postgres-11.3/optimizer/geqo/geqo_eval.c
- /Postgres-11.3/tools/msvc/mkvcbuild.pl
- /Postgres-11.3/port/gettimeofday.c
- /Postgres-11.3/btree_float4.c
- /Postgres-11.3/Gen_fmgrtab.pl
- /Postgres-11.3/adt/lockfuncs.c
- /Postgres-11.3/plpgsql/src/pl_handler.c
- /Postgres-11.3/port/win32/timer.c
- /Postgres-11.3/scripts/clusterdb.c
- /Postgres-11.3/cache/relfilenodemap.c
- /Postgres-11.3/parser/parse_param.c
- /Postgres-11.3/lib/rbtree.c
- /Postgres-11.3/pgcrypto/pgp.h
- /Postgres-11.3/scripts/dropdb.c
- /Postgres-11.3/ltree_plpython/ltree_plpython.c
- /Postgres-11.3/fe_utils/print.c
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
PostgreSQL versions 10.x before 10.9 and versions 11.x before 11.4 are vulnerable to a stack-based buffer overflow. Any authenticated user can overflow a stack-based buffer by changing the user's own password to a purpose-crafted value. This often suffices to execute arbitrary code as the PostgreSQL operating system account.
<p>Publish Date: 2019-06-26
<p>URL: <a href=https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-10164>CVE-2019-10164</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>8.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2019-10164">https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2019-10164</a></p>
<p>Release Date: 2019-06-26</p>
<p>Fix Resolution: REL_10_9;REL_11_4</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2019-10164 (High) detected in postgres-REL_11_3 - ## CVE-2019-10164 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>postgresREL_11_3</b></p></summary>
<p>
<p>Mirror of the official PostgreSQL GIT repository. Note that this is just a *mirror* - we don't work with pull requests on github. To contribute, please see https://wiki.postgresql.org/wiki/Submitting_a_Patch</p>
<p>Library home page: <a href=https://github.com/postgres/postgres.git>https://github.com/postgres/postgres.git</a></p>
<p>Found in HEAD commit: <a href="https://github.com/nidhisi/Postgres-11.3/commit/5471e439dfb6d1349424c11bfae057c2c28f4e0e">5471e439dfb6d1349424c11bfae057c2c28f4e0e</a></p>
</p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Library Source Files (1118)</summary>
<p></p>
<p> * The source files were matched to this source library based on a best effort match. Source libraries are selected from a list of probable public libraries.</p>
<p>
- /Postgres-11.3/optimizer/path/equivclass.c
- /Postgres-11.3/port/inet_net_ntop.c
- /Postgres-11.3/pg_basebackup/t/030_pg_recvlogical.pl
- /Postgres-11.3/postmaster/startup.c
- /Postgres-11.3/pg_dump/dumputils.c
- /Postgres-11.3/adt/misc.c
- /Postgres-11.3/pg_upgrade/pg_upgrade.h
- /Postgres-11.3/xml2/xslt_proc.c
- /Postgres-11.3/adt/oracle_compat.c
- /Postgres-11.3/postmaster/pgstat.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_english.c
- /Postgres-11.3/adt/tsginidx.c
- /Postgres-11.3/cache/catcache.c
- /Postgres-11.3/tsearch/dict_thesaurus.c
- /Postgres-11.3/common/controldata_utils.c
- /Postgres-11.3/earthdistance/earthdistance.c
- /Postgres-11.3/pgbench/t/001_pgbench_with_server.pl
- /Postgres-11.3/adt/pg_upgrade_support.c
- /Postgres-11.3/port/win32/socket.c
- /Postgres-11.3/pg_upgrade/util.c
- /Postgres-11.3/scripts/dropuser.c
- /Postgres-11.3/psql/crosstabview.c
- /Postgres-11.3/lib/bipartite_match.c
- /Postgres-11.3/adt/char.c
- /Postgres-11.3/nodes/value.c
- /Postgres-11.3/optimizer/geqo/geqo_misc.c
- /Postgres-11.3/adt/expandedrecord.c
- /Postgres-11.3/cache/attoptcache.c
- /Postgres-11.3/sepgsql/selinux.c
- /Postgres-11.3/executor/nodeRecursiveunion.c
- /Postgres-11.3/rewrite/rewriteSupport.c
- /Postgres-11.3/hstore/hstore.h
- /Postgres-11.3/preproc/ecpg_keywords.c
- /Postgres-11.3/bloom/blvalidate.c
- /Postgres-11.3/bloom/blutils.c
- /Postgres-11.3/port/dirent.c
- /Postgres-11.3/bloom/blcost.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_portuguese.c
- /Postgres-11.3/storage/page/bufpage.c
- /Postgres-11.3/common/unicode/generate-unicode_norm_table.pl
- /Postgres-11.3/pg_dump/parallel.h
- /Postgres-11.3/test_decoding/test_decoding.c
- /Postgres-11.3/ltree/ltree_gist.c
- /Postgres-11.3/catalog/genbki.pl
- /Postgres-11.3/catalog/pg_inherits.c
- /Postgres-11.3/pg_upgrade/parallel.c
- /Postgres-11.3/mmgr/dsa.c
- /Postgres-11.3/misc/backend_random.c
- /Postgres-11.3/common/unicode_norm.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_romanian.c
- /Postgres-11.3/commands/constraint.c
- /Postgres-11.3/commands/extension.c
- /Postgres-11.3/psql/common.h
- /Postgres-11.3/time/combocid.c
- /Postgres-11.3/tools/copyright.pl
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_portuguese.c
- /Postgres-11.3/adt/quote.c
- /Postgres-11.3/plpy_exec.c
- /Postgres-11.3/commands/lockcmds.c
- /Postgres-11.3/common/string.c
- /Postgres-11.3/replication/logical/reorderbuffer.c
- /Postgres-11.3/parser/parse_agg.c
- /Postgres-11.3/pgcrypto/internal.c
- /Postgres-11.3/libpq/fe-protocol2.c
- /Postgres-11.3/ecpglib/extern.h
- /Postgres-11.3/commands/portalcmds.c
- /Postgres-11.3/adt/amutils.c
- /Postgres-11.3/pgcrypto/pgp-mpi.c
- /Postgres-11.3/jsonb_plpython/jsonb_plpython.c
- /Postgres-11.3/cache/syscache.c
- /Postgres-11.3/parser/parse_type.c
- /Postgres-11.3/libpq/fe-print.c
- /Postgres-11.3/plperl/plperl_helpers.h
- /Postgres-11.3/parser/parse_oper.c
- /Postgres-11.3/scripts/pg_isready.c
- /Postgres-11.3/nodes/readfuncs.c
- /Postgres-11.3/tools/msvc/builddoc.pl
- /Postgres-11.3/common/unicode/norm_test.c
- /Postgres-11.3/pgcrypto/crypt-gensalt.c
- /Postgres-11.3/commands/user.c
- /Postgres-11.3/parser/parse_cte.c
- /Postgres-11.3/optimizer/geqo/geqo_erx.c
- /Postgres-11.3/pgcrypto/pgp-mpi-openssl.c
- /Postgres-11.3/libpq/pqsignal.c
- /Postgres-11.3/plpy_planobject.c
- /Postgres-11.3/pg_dump/pg_backup_db.h
- /Postgres-11.3/catalog/pg_enum.c
- /Postgres-11.3/port/dynloader/netbsd.c
- /Postgres-11.3/replication/logical/launcher.c
- /Postgres-11.3/executor/nodeSubqueryscan.c
- /Postgres-11.3/snowball/dict_snowball.c
- /Postgres-11.3/storage/lmgr/lock.c
- /Postgres-11.3/preproc/ecpg.c
- /Postgres-11.3/regex/regprefix.c
- /Postgres-11.3/vacuumlo/vacuumlo.c
- /Postgres-11.3/plpy_spi.h
- /Postgres-11.3/init/postinit.c
- /Postgres-11.3/psql/startup.c
- /Postgres-11.3/include/sqlca.h
- /Postgres-11.3/storage/smgr/smgrtype.c
- /Postgres-11.3/initdb/t/001_initdb.pl
- /Postgres-11.3/preproc/extern.h
- /Postgres-11.3/port/qsort.c
- /Postgres-11.3/psql/describe.c
- /Postgres-11.3/adt/array_typanalyze.c
- /Postgres-11.3/expected/compat_informix-rfmtdate.c
- /Postgres-11.3/pg_ctl/t/001_start_stop.pl
- /Postgres-11.3/adt/cryptohashes.c
- /Postgres-11.3/cache/relmapper.c
- /Postgres-11.3/regex/regexec.c
- /Postgres-11.3/catalog/heap.c
- /Postgres-11.3/catalog/toasting.c
- /Postgres-11.3/parser/check_keywords.pl
- /Postgres-11.3/pgcrypto/pgp-mpi-internal.c
- /Postgres-11.3/regex/regc_nfa.c
- /Postgres-11.3/adt/dbsize.c
- /Postgres-11.3/adt/mac8.c
- /Postgres-11.3/executor/nodeLimit.c
- /Postgres-11.3/lib/binaryheap.c
- /Postgres-11.3/pgbench/t/002_pgbench_no_server.pl
- /Postgres-11.3/optimizer/geqo/geqo_selection.c
- /Postgres-11.3/executor/nodeSamplescan.c
- /Postgres-11.3/pgbench/pgbench.c
- /Postgres-11.3/pg_rewind/fetch.c
- /Postgres-11.3/psql/psqlscanslash.h
- /Postgres-11.3/libpq/pqexpbuffer.c
- /Postgres-11.3/plpgsql/src/generate-plerrcodes.pl
- /Postgres-11.3/pg_test_fsync/pg_test_fsync.c
- /Postgres-11.3/common/sha2_openssl.c
- /Postgres-11.3/commands/functioncmds.c
- /Postgres-11.3/adt/encode.c
- /Postgres-11.3/bootstrap/bootstrap.c
- /Postgres-11.3/catalog/pg_conversion.c
- /Postgres-11.3/jit/jit.c
- /Postgres-11.3/executor/execGrouping.c
- /Postgres-11.3/replication/walsender.c
- /Postgres-11.3/port/win32_sema.c
- /Postgres-11.3/adt/inet_net_pton.c
- /Postgres-11.3/adt/arrayutils.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_italian.c
- /Postgres-11.3/adt/array_selfuncs.c
- /Postgres-11.3/pg_upgrade/server.c
- /Postgres-11.3/tsearch/ts_utils.c
- /Postgres-11.3/nodes/equalfuncs.c
- /Postgres-11.3/pg_freespacemap/pg_freespacemap.c
- /Postgres-11.3/port/dynloader/darwin.c
- /Postgres-11.3/seg/seg.c
- /Postgres-11.3/sort/sortsupport.c
- /Postgres-11.3/common/ip.c
- /Postgres-11.3/scripts/t/102_vacuumdb_stages.pl
- /Postgres-11.3/tools/msvc/Mkvcbuild.pm
- /Postgres-11.3/pgcrypto/pgp-encrypt.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_spanish.c
- /Postgres-11.3/tsearch/dict_simple.c
- /Postgres-11.3/pgstattuple/pgstatindex.c
- /Postgres-11.3/adt/orderedsetaggs.c
- /Postgres-11.3/pg_dump/pg_backup_null.c
- /Postgres-11.3/executor/nodeNamedtuplestorescan.c
- /Postgres-11.3/ecpglib/misc.c
- /Postgres-11.3/btree_inet.c
- /Postgres-11.3/rewrite/rowsecurity.c
- /Postgres-11.3/tools/msvc/pgflex.pl
- /Postgres-11.3/unaccent/unaccent.c
- /Postgres-11.3/commands/comment.c
- /Postgres-11.3/port/dynloader/netbsd.h
- /Postgres-11.3/ltree/ltxtquery_op.c
- /Postgres-11.3/libpq/libpq-events.h
- /Postgres-11.3/executor/execProcnode.c
- /Postgres-11.3/pg_rewind/t/RewindTest.pm
- /Postgres-11.3/executor/nodeAgg.c
- /Postgres-11.3/port/win32error.c
- /Postgres-11.3/adt/uuid.c
- /Postgres-11.3/optimizer/geqo/geqo_main.c
- /Postgres-11.3/pgcrypto/px.c
- /Postgres-11.3/pg_dump/pg_dump_sort.c
- /Postgres-11.3/port/win32setlocale.c
- /Postgres-11.3/pg_dump/pg_backup_directory.c
- /Postgres-11.3/commands/typecmds.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_french.c
- /Postgres-11.3/replication/pgoutput/pgoutput.c
- /Postgres-11.3/citext/citext.c
- /Postgres-11.3/port/pg_crc32c_armv8.c
- /Postgres-11.3/pg_rewind/t/003_extrafiles.pl
- /Postgres-11.3/port/mkdtemp.c
- /Postgres-11.3/commands/indexcmds.c
- /Postgres-11.3/pgtypeslib/common.c
- /Postgres-11.3/ltree/crc32.c
- /Postgres-11.3/storage/page/checksum.c
- /Postgres-11.3/bloom/blinsert.c
- /Postgres-11.3/postmaster/fork_process.c
- /Postgres-11.3/spi/autoinc.c
- /Postgres-11.3/hash/hashfn.c
- /Postgres-11.3/plpgsql/src/pl_funcs.c
- /Postgres-11.3/sepgsql/label.c
- /Postgres-11.3/storage/ipc/procsignal.c
- /Postgres-11.3/spi/timetravel.c
- /Postgres-11.3/commands/vacuum.c
- /Postgres-11.3/misc/tzparser.c
- /Postgres-11.3/tsearch/ts_parse.c
- /Postgres-11.3/snowball/libstemmer/utilities.c
- /Postgres-11.3/adt/acl.c
- /Postgres-11.3/commands/amcmds.c
- /Postgres-11.3/initdb/initdb.c
- /Postgres-11.3/optimizer/geqo/geqo_cx.c
- /Postgres-11.3/executor/execUtils.c
- /Postgres-11.3/port/pgsleep.c
- /Postgres-11.3/tcop/utility.c
- /Postgres-11.3/pg_ctl/t/002_status.pl
- /Postgres-11.3/plpgsql/src/pl_exec.c
- /Postgres-11.3/plperl/ppport.h
- /Postgres-11.3/replication/logical/tablesync.c
- /Postgres-11.3/tsearch/regis.c
- /Postgres-11.3/pg_dump/pg_backup_tar.c
- /Postgres-11.3/btree_utils_var.c
- /Postgres-11.3/postmaster/walwriter.c
- /Postgres-11.3/libpq/libpq-fe.h
- /Postgres-11.3/commands/variable.c
- /Postgres-11.3/pg_waldump/compat.c
- /Postgres-11.3/sepgsql/dml.c
- /Postgres-11.3/scripts/t/010_clusterdb.pl
- /Postgres-11.3/plpy_subxactobject.c
- /Postgres-11.3/port/dynloader/openbsd.c
- /Postgres-11.3/port/dynloader/hpux.h
- /Postgres-11.3/tools/fix-old-flex-code.pl
- /Postgres-11.3/ecpglib/execute.c
- /Postgres-11.3/tablefunc/tablefunc.c
- /Postgres-11.3/dict_xsyn/dict_xsyn.c
- /Postgres-11.3/pg_basebackup/walmethods.h
- /Postgres-11.3/sepgsql/database.c
- /Postgres-11.3/storage/lmgr/predicate.c
- /Postgres-11.3/pgcrypto/pgcrypto.h
- /Postgres-11.3/libpq/fe-auth.h
- /Postgres-11.3/pageinspect/hashfuncs.c
- /Postgres-11.3/common/keywords.c
- /Postgres-11.3/port/getrusage.c
- /Postgres-11.3/common/username.c
- /Postgres-11.3/pg_rewind/libpq_fetch.c
- /Postgres-11.3/pgcrypto/pgp-info.c
- /Postgres-11.3/file_fdw/file_fdw.c
- /Postgres-11.3/uuid-ossp/uuid-ossp.c
- /Postgres-11.3/mmgr/portalmem.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_english.c
- /Postgres-11.3/adt/numutils.c
- /Postgres-11.3/port/pg_strong_random.c
- /Postgres-11.3/pg_controldata/t/001_pg_controldata.pl
- /Postgres-11.3/parser/analyze.c
- /Postgres-11.3/pg_waldump/pg_waldump.c
- /Postgres-11.3/commands/seclabel.c
- /Postgres-11.3/pg_trgm/trgm.h
- /Postgres-11.3/adt/levenshtein.c
- /Postgres-11.3/psql/crosstabview.h
- /Postgres-11.3/adt/float.c
- /Postgres-11.3/resowner/resowner.c
- /Postgres-11.3/intarray/_int_bool.c
- /Postgres-11.3/port/win32security.c
- /Postgres-11.3/pg_rewind/file_ops.h
- /Postgres-11.3/pg_rewind/pg_rewind.c
- /Postgres-11.3/port/tar.c
- /Postgres-11.3/executor/functions.c
- /Postgres-11.3/storage/freespace/freespace.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_spanish.c
- /Postgres-11.3/storage/file/buffile.c
- /Postgres-11.3/catalog/Catalog.pm
- /Postgres-11.3/btree_uuid.c
- /Postgres-11.3/storage/lmgr/proc.c
- /Postgres-11.3/regex/regc_lex.c
- /Postgres-11.3/regex/regc_color.c
- /Postgres-11.3/port/win32env.c
- /Postgres-11.3/libpq/fe-secure-openssl.c
- /Postgres-11.3/commands/statscmds.c
- /Postgres-11.3/parser/parse_node.c
- /Postgres-11.3/port/dynloader/cygwin.h
- /Postgres-11.3/common/file_utils.c
- /Postgres-11.3/storage/ipc/sinval.c
- /Postgres-11.3/libpq/ifaddr.c
- /Postgres-11.3/adt/like.c
- /Postgres-11.3/pg_dump/pg_backup.h
- /Postgres-11.3/adt/rangetypes_spgist.c
- /Postgres-11.3/scripts/reindexdb.c
- /Postgres-11.3/btree_ts.c
- /Postgres-11.3/bloom/blvacuum.c
- /Postgres-11.3/pgcrypto/px-crypt.h
- /Postgres-11.3/jit/llvm/llvmjit_wrap.cpp
- /Postgres-11.3/commands/aggregatecmds.c
- /Postgres-11.3/lib/dshash.c
- /Postgres-11.3/bloom/bloom.h
- /Postgres-11.3/pgcrypto/sha1.c
- /Postgres-11.3/executor/nodeForeignscan.c
- /Postgres-11.3/jit/llvm/llvmjit_error.cpp
- /Postgres-11.3/pgcrypto/pgp-armor.c
- /Postgres-11.3/parser/parser.c
- /Postgres-11.3/btree_utils_num.h
- /Postgres-11.3/pgcrypto/openssl.c
- /Postgres-11.3/tsearch/wparser.c
- /Postgres-11.3/scripts/vacuumdb.c
- /Postgres-11.3/optimizer/path/clausesel.c
- /Postgres-11.3/libpq/fe-secure.c
- /Postgres-11.3/executor/execJunk.c
- /Postgres-11.3/executor/nodeModifyTable.c
- /Postgres-11.3/btree_macaddr8.c
- /Postgres-11.3/common/exec.c
- /Postgres-11.3/plperl/plperl.c
- /Postgres-11.3/pg_dump/compress_io.h
- /Postgres-11.3/adt/jsonfuncs.c
- /Postgres-11.3/postgres_fdw/deparse.c
- /Postgres-11.3/adt/rangetypes_typanalyze.c
- /Postgres-11.3/plpy_util.c
- /Postgres-11.3/pg_controldata/pg_controldata.c
- /Postgres-11.3/commands/matview.c
- /Postgres-11.3/executor/execAmi.c
- /Postgres-11.3/libpq/pqformat.c
- /Postgres-11.3/storage/smgr/smgr.c
- /Postgres-11.3/storage/lmgr/condition_variable.c
- /Postgres-11.3/executor/execParallel.c
- /Postgres-11.3/port/win32/signal.c
- /Postgres-11.3/storage/ipc/procarray.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_finnish.c
- /Postgres-11.3/optimizer/path/joinrels.c
- /Postgres-11.3/libpq/fe-auth-scram.c
- /Postgres-11.3/statistics/mvdistinct.c
- /Postgres-11.3/adt/network_selfuncs.c
- /Postgres-11.3/pg_upgrade/pg_upgrade.c
- /Postgres-11.3/adt/tid.c
- /Postgres-11.3/mmgr/mcxt.c
- /Postgres-11.3/adt/int.c
- /Postgres-11.3/commands/proclang.c
- /Postgres-11.3/tsearch/ts_selfuncs.c
- /Postgres-11.3/adt/oid.c
- /Postgres-11.3/executor/execSRF.c
- /Postgres-11.3/fmgr/fmgr.c
- /Postgres-11.3/port/erand48.c
- /Postgres-11.3/executor/execCurrent.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_hungarian.c
- /Postgres-11.3/libpq/auth.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_turkish.c
- /Postgres-11.3/port/sysv_shmem.c
- /Postgres-11.3/commands/conversioncmds.c
- /Postgres-11.3/storage/lmgr/generate-lwlocknames.pl
- /Postgres-11.3/jsonb_plperl/jsonb_plperl.c
- /Postgres-11.3/tools/ifaddrs/test_ifaddrs.c
- /Postgres-11.3/preproc/check_rules.pl
- /Postgres-11.3/adt/int8.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_russian.c
- /Postgres-11.3/pg_upgrade/info.c
- /Postgres-11.3/parser/parse_clause.c
- /Postgres-11.3/executor/nodeCtescan.c
- /Postgres-11.3/adt/rangetypes_gist.c
- /Postgres-11.3/oid2name/oid2name.c
- /Postgres-11.3/preproc/parser.c
- /Postgres-11.3/pg_archivecleanup/pg_archivecleanup.c
- /Postgres-11.3/adt/regproc.c
- /Postgres-11.3/common/wait_error.c
- /Postgres-11.3/ltree/lquery_op.c
- /Postgres-11.3/misc/queryenvironment.c
- /Postgres-11.3/include/ecpglib.h
- /Postgres-11.3/storage/ipc/dsm.c
- /Postgres-11.3/storage/buffer/bufmgr.c
- /Postgres-11.3/common/md5.c
- /Postgres-11.3/port/getaddrinfo.c
- /Postgres-11.3/misc/guc.c
- /Postgres-11.3/auto_explain/auto_explain.c
- /Postgres-11.3/hstore_plpython/hstore_plpython.c
- /Postgres-11.3/storage/ipc/latch.c
- /Postgres-11.3/pageinspect/brinfuncs.c
- /Postgres-11.3/adt/varchar.c
- /Postgres-11.3/rewrite/rewriteDefine.c
- /Postgres-11.3/psql/create_help.pl
- /Postgres-11.3/plpython.h
- /Postgres-11.3/preproc/output.c
- /Postgres-11.3/executor/nodeSetOp.c
- /Postgres-11.3/adt/tsquery_gist.c
- /Postgres-11.3/pageinspect/btreefuncs.c
- /Postgres-11.3/snowball/libstemmer/api.c
- /Postgres-11.3/commands/trigger.c
- /Postgres-11.3/pgcrypto/imath.c
- /Postgres-11.3/regex/regerror.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_porter.c
- /Postgres-11.3/port/posix_sema.c
- /Postgres-11.3/plpy_plpymodule.c
- /Postgres-11.3/executor/nodeHashjoin.c
- /Postgres-11.3/replication/logical/worker.c
- /Postgres-11.3/tools/msvc/vcregress.pl
- /Postgres-11.3/adt/mac.c
- /Postgres-11.3/tsearch/dict_ispell.c
- /Postgres-11.3/include/pgtypes_interval.h
- /Postgres-11.3/include/ecpgerrno.h
- /Postgres-11.3/plpy_elog.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_french.c
- /Postgres-11.3/time/snapmgr.c
- /Postgres-11.3/pg_dump/pg_backup_archiver.h
- /Postgres-11.3/tcop/postgres.c
- /Postgres-11.3/catalog/objectaccess.c
- /Postgres-11.3/commands/dropcmds.c
- /Postgres-11.3/optimizer/plan/planmain.c
- /Postgres-11.3/pgcrypto/internal-sha2.c
- /Postgres-11.3/pg_rewind/file_ops.c
- /Postgres-11.3/commands/alter.c
- /Postgres-11.3/libpq/fe-lobj.c
- /Postgres-11.3/common/fe_memutils.c
- /Postgres-11.3/include/sqlda-native.h
- /Postgres-11.3/optimizer/plan/setrefs.c
- /Postgres-11.3/optimizer/plan/analyzejoins.c
- /Postgres-11.3/pg_rewind/logging.c
- /Postgres-11.3/pageinspect/ginfuncs.c
- /Postgres-11.3/regex/regc_pg_locale.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_italian.c
- /Postgres-11.3/intarray/bench/bench.pl
- /Postgres-11.3/preproc/variable.c
- /Postgres-11.3/misc/pg_controldata.c
- /Postgres-11.3/psql/large_obj.c
- /Postgres-11.3/catalog/pg_namespace.c
- /Postgres-11.3/partitioning/partbounds.c
- /Postgres-11.3/storage/ipc/shmqueue.c
- /Postgres-11.3/commands/event_trigger.c
- /Postgres-11.3/nodes/copyfuncs.c
- /Postgres-11.3/spi/insert_username.c
- /Postgres-11.3/replication/walreceiverfuncs.c
- /Postgres-11.3/fuzzystrmatch/dmetaphone.c
- /Postgres-11.3/hstore/hstore_op.c
- /Postgres-11.3/postgres_fdw/connection.c
- /Postgres-11.3/adt/network_gist.c
- /Postgres-11.3/cache/partcache.c
- /Postgres-11.3/ltree/_ltree_op.c
- /Postgres-11.3/error/elog.c
- /Postgres-11.3/pg_dump/pg_backup_archiver.c
- /Postgres-11.3/seg/seg-validate.pl
- /Postgres-11.3/libpq/fe-secure-common.h
- /Postgres-11.3/nodes/print.c
- /Postgres-11.3/port/qsort_arg.c
- /Postgres-11.3/nodes/tidbitmap.c
- /Postgres-11.3/hstore/hstore_gist.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_dutch.c
- /Postgres-11.3/pgrowlocks/pgrowlocks.c
- /Postgres-11.3/commands/vacuumlazy.c
- /Postgres-11.3/adt/nabstime.c
- /Postgres-11.3/psql/mainloop.c
- /Postgres-11.3/executor/nodeMergeAppend.c
- /Postgres-11.3/adt/domains.c
- /Postgres-11.3/tsm_system_time/tsm_system_time.c
- /Postgres-11.3/plpy_typeio.h
- /Postgres-11.3/pg_rewind/pg_rewind.h
- /Postgres-11.3/scripts/common.h
- /Postgres-11.3/timezone/pgtz.h
- /Postgres-11.3/catalog/pg_publication.c
- /Postgres-11.3/time/tqual.c
- /Postgres-11.3/expected/compat_informix-charfuncs.c
- /Postgres-11.3/pgcrypto/rijndael.c
- /Postgres-11.3/postmaster/bgwriter.c
- /Postgres-11.3/adt/varlena.c
- /Postgres-11.3/libpq/libpq-int.h
- /Postgres-11.3/adt/geo_ops.c
- /Postgres-11.3/expected/compat_informix-describe.c
- /Postgres-11.3/cache/plancache.c
- /Postgres-11.3/sort/sharedtuplestore.c
- /Postgres-11.3/fmgr/dfmgr.c
- /Postgres-11.3/Gen_dummy_probes.pl
- /Postgres-11.3/executor/nodeMergejoin.c
- /Postgres-11.3/pg_rewind/filemap.c
- /Postgres-11.3/psql/settings.h
- /Postgres-11.3/unaccent/generate_unaccent_rules.py
- /Postgres-11.3/scripts/createuser.c
- /Postgres-11.3/cache/lsyscache.c
- /Postgres-11.3/scripts/t/020_createdb.pl
- /Postgres-11.3/port/win32_shmem.c
- /Postgres-11.3/plpy_procedure.h
- /Postgres-11.3/port/sysv_sema.c
- /Postgres-11.3/pg_resetwal/pg_resetwal.c
- /Postgres-11.3/expected/compat_oracle-char_array.c
- /Postgres-11.3/optimizer/geqo/geqo_ox2.c
- /Postgres-11.3/ltree/ltxtquery_io.c
- /Postgres-11.3/adt/datum.c
- /Postgres-11.3/timezone/pgtz.c
- /Postgres-11.3/pg_rewind/copy_fetch.c
- /Postgres-11.3/mmgr/slab.c
- /Postgres-11.3/pageinspect/heapfuncs.c
- /Postgres-11.3/scripts/common.c
- /Postgres-11.3/pg_rewind/filemap.h
- /Postgres-11.3/tools/msvc/Solution.pm
- /Postgres-11.3/timezone/private.h
- /Postgres-11.3/adt/format_type.c
- /Postgres-11.3/sort/tuplestore.c
- /Postgres-11.3/catalog/pg_constraint.c
- /Postgres-11.3/port/dirmod.c
- /Postgres-11.3/jit/llvm/llvmjit_types.c
- /Postgres-11.3/regex/regfree.c
- /Postgres-11.3/replication/logical/origin.c
- /Postgres-11.3/storage/file/fd.c
- /Postgres-11.3/catalog/pg_shdepend.c
- /Postgres-11.3/tsearch/ts_typanalyze.c
- /Postgres-11.3/hstore_plperl/hstore_plperl.c
- /Postgres-11.3/spi/refint.c
- /Postgres-11.3/expected/compat_informix-rfmtlong.c
- /Postgres-11.3/adt/geo_selfuncs.c
- /Postgres-11.3/postmaster/autovacuum.c
- /Postgres-11.3/commands/analyze.c
- /Postgres-11.3/lib/ilist.c
- /Postgres-11.3/bloom/blscan.c
- /Postgres-11.3/lib/pairingheap.c
- /Postgres-11.3/commands/tsearchcmds.c
- /Postgres-11.3/port/pgcheckdir.c
- /Postgres-11.3/hstore/hstore_compat.c
- /Postgres-11.3/regex/regcomp.c
- /Postgres-11.3/intarray/_int.h
- /Postgres-11.3/adt/jsonb.c
- /Postgres-11.3/adt/tsquery.c
- /Postgres-11.3/pg_dump/pg_backup_utils.c
- /Postgres-11.3/preproc/c_keywords.c
- /Postgres-11.3/pg_visibility/pg_visibility.c
- /Postgres-11.3/port/getopt.c
- /Postgres-11.3/misc/pg_config.c
- /Postgres-11.3/include/pgtypes_timestamp.h
- /Postgres-11.3/hstore/hstore_io.c
- /Postgres-11.3/auth_delay/auth_delay.c
- /Postgres-11.3/catalog/pg_depend.c
- /Postgres-11.3/pgcrypto/mbuf.c
- /Postgres-11.3/plpgsql/src/pl_comp.c
- /Postgres-11.3/tools/msvc/pgbison.pl
- /Postgres-11.3/pageinspect/fsmfuncs.c
- /Postgres-11.3/psql/prompt.c
- /Postgres-11.3/optimizer/geqo/geqo_mutation.c
- /Postgres-11.3/adt/tsquery_op.c
- /Postgres-11.3/pgcrypto/pgp.c
- /Postgres-11.3/catalog/pg_type.c
- /Postgres-11.3/statistics/dependencies.c
- /Postgres-11.3/pgcrypto/crypt-md5.c
- /Postgres-11.3/pgcrypto/crypt-des.c
- /Postgres-11.3/optimizer/plan/initsplan.c
- /Postgres-11.3/expected/compat_informix-test_informix.c
- /Postgres-11.3/port/snprintf.c
- /Postgres-11.3/mmgr/freepage.c
- /Postgres-11.3/sepgsql/sepgsql.h
- /Postgres-11.3/adt/jsonb_util.c
- /Postgres-11.3/fe_utils/mbprint.c
- /Postgres-11.3/src/sgml/mk_feature_tables.pl
- /Postgres-11.3/pg_trgm/trgm_op.c
- /Postgres-11.3/pg_rewind/datapagemap.h
- /Postgres-11.3/common/relpath.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_porter.c
- /Postgres-11.3/preproc/type.c
- /Postgres-11.3/executor/nodeGroup.c
- /Postgres-11.3/init/globals.c
- /Postgres-11.3/parser/parse_coerce.c
- /Postgres-11.3/tools/msvc/Install.pm
- /Postgres-11.3/pgcrypto/blf.h
- /Postgres-11.3/adt/ri_triggers.c
- /Postgres-11.3/common/rmtree.c
- /Postgres-11.3/port/strlcpy.c
- /Postgres-11.3/storage/smgr/md.c
- /Postgres-11.3/parser/parse_target.c
- /Postgres-11.3/optimizer/path/joinpath.c
- /Postgres-11.3/fuzzystrmatch/fuzzystrmatch.c
- /Postgres-11.3/libpq/fe-exec.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_swedish.c
- /Postgres-11.3/pg_basebackup/streamutil.h
- /Postgres-11.3/btree_utils_num.c
- /Postgres-11.3/optimizer/plan/planner.c
- /Postgres-11.3/pg_upgrade/file.c
- /Postgres-11.3/common/config_info.c
- /Postgres-11.3/fmgr/funcapi.c
- /Postgres-11.3/include/ecpgtype.h
- /Postgres-11.3/catalog/namespace.c
- /Postgres-11.3/adt/pgstatfuncs.c
- /Postgres-11.3/optimizer/plan/createplan.c
- /Postgres-11.3/jit/llvm/llvmjit_expr.c
- /Postgres-11.3/parser/parse_expr.c
- /Postgres-11.3/libpq/test/uri-regress.c
- /Postgres-11.3/hash/dynahash.c
- /Postgres-11.3/expected/compat_informix-rnull.c
- /Postgres-11.3/port/fseeko.c
- /Postgres-11.3/libpq/fe-protocol3.c
- /Postgres-11.3/ecpglib/prepare.c
- /Postgres-11.3/tools/msvc/install.pl
- /Postgres-11.3/optimizer/geqo/geqo_ox1.c
- /Postgres-11.3/pg_dump/pg_backup_db.c
- /Postgres-11.3/commands/createas.c
- /Postgres-11.3/executor/execScan.c
- /Postgres-11.3/sepgsql/hooks.c
- /Postgres-11.3/libpq/fe-secure-common.c
- /Postgres-11.3/plpy_main.c
- /Postgres-11.3/port/pg_crc32c_armv8_choose.c
- /Postgres-11.3/ecpglib/memory.c
- /Postgres-11.3/psql/describe.h
- /Postgres-11.3/pgcrypto/px.h
- /Postgres-11.3/adt/pg_lsn.c
- /Postgres-11.3/replication/slot.c
- /Postgres-11.3/pg_dump/pg_dump.c
- /Postgres-11.3/libpq/auth-scram.c
- /Postgres-11.3/executor/nodeProjectSet.c
- /Postgres-11.3/executor/execExpr.c
- /Postgres-11.3/cache/spccache.c
- /Postgres-11.3/statistics/extended_stats.c
- /Postgres-11.3/executor/nodeAppend.c
- /Postgres-11.3/pgstattuple/pgstattuple.c
- /Postgres-11.3/plpy_main.h
- /Postgres-11.3/adt/ruleutils.c
- /Postgres-11.3/plperl/plc_perlboot.pl
- /Postgres-11.3/pg_buffercache/pg_buffercache_pages.c
- /Postgres-11.3/adt/tsquery_rewrite.c
- /Postgres-11.3/preproc/keywords.c
- /Postgres-11.3/libpq/fe-misc.c
- /Postgres-11.3/commands/define.c
- /Postgres-11.3/port/dynloader/freebsd.c
- /Postgres-11.3/ecpglib/error.c
- /Postgres-11.3/pgcrypto/pgcrypto.c
- /Postgres-11.3/optimizer/geqo/geqo_pmx.c
- /Postgres-11.3/scripts/t/200_connstr.pl
- /Postgres-11.3/regex/regc_locale.c
- /Postgres-11.3/executor/nodeHash.c
- /Postgres-11.3/catalog/pg_subscription.c
- /Postgres-11.3/misc/sampling.c
- /Postgres-11.3/compatlib/informix.c
- /Postgres-11.3/psql/stringutils.c
- /Postgres-11.3/port/open.c
- /Postgres-11.3/replication/basebackup.c
- /Postgres-11.3/psql/copy.c
- /Postgres-11.3/pgcrypto/pgp-pgsql.c
- /Postgres-11.3/ltree/ltree.h
- /Postgres-11.3/pageinspect/rawpage.c
- /Postgres-11.3/commands/opclasscmds.c
- /Postgres-11.3/psql/input.h
- /Postgres-11.3/pg_basebackup/receivelog.h
- /Postgres-11.3/optimizer/geqo/geqo_random.c
- /Postgres-11.3/adt/pseudotypes.c
- /Postgres-11.3/plpy_subxactobject.h
- /Postgres-11.3/libpq/pthread-win32.c
- /Postgres-11.3/replication/libpqwalreceiver/libpqwalreceiver.c
- /Postgres-11.3/commands/sequence.c
- /Postgres-11.3/adt/bool.c
- /Postgres-11.3/storage/file/reinit.c
- /Postgres-11.3/port/dynloader/linux.h
- /Postgres-11.3/adt/array_userfuncs.c
- /Postgres-11.3/port/dynloader/solaris.h
- /Postgres-11.3/pg_dump/pg_backup_custom.c
- /Postgres-11.3/parser/parse_relation.c
- /Postgres-11.3/tools/findoidjoins/findoidjoins.c
- /Postgres-11.3/parser/parse_enr.c
- /Postgres-11.3/pgcrypto/pgp-decrypt.c
- /Postgres-11.3/psql/stringutils.h
- /Postgres-11.3/libpq/be-secure.c
- /Postgres-11.3/btree_time.c
- /Postgres-11.3/plpy_elog.h
- /Postgres-11.3/pg_upgrade/tablespace.c
- /Postgres-11.3/executor/nodeGatherMerge.c
- /Postgres-11.3/pgtypeslib/extern.h
- /Postgres-11.3/libpq/be-fsstubs.c
- /Postgres-11.3/replication/logical/proto.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_hungarian.c
- /Postgres-11.3/port/sprompt.c
- /Postgres-11.3/libpq/be-secure-common.c
- /Postgres-11.3/pgevent/pgevent.c
- /Postgres-11.3/btree_gist.c
- /Postgres-11.3/executor/nodeBitmapAnd.c
- /Postgres-11.3/plperl/plperl.h
- /Postgres-11.3/adt/date.c
- /Postgres-11.3/nodes/list.c
- /Postgres-11.3/optimizer/path/indxpath.c
- /Postgres-11.3/adt/timestamp.c
- /Postgres-11.3/btree_float8.c
- /Postgres-11.3/tsearch/dict.c
- /Postgres-11.3/catalog/pg_largeobject.c
- /Postgres-11.3/intarray/_int_op.c
- /Postgres-11.3/executor/execIndexing.c
- /Postgres-11.3/timezone/zic.c
- /Postgres-11.3/pg_rewind/t/004_pg_xlog_symlink.pl
- /Postgres-11.3/generate-spiexceptions.pl
- /Postgres-11.3/adt/inet_cidr_ntop.c
- /Postgres-11.3/commands/policy.c
- /Postgres-11.3/commands/tablespace.c
- /Postgres-11.3/adt/numeric.c
- /Postgres-11.3/storage/ipc/shmem.c
- /Postgres-11.3/lo/lo.c
- /Postgres-11.3/btree_int2.c
- /Postgres-11.3/adt/pg_locale.c
- /Postgres-11.3/sort/logtape.c
- /Postgres-11.3/libpq/hba.c
- /Postgres-11.3/cache/ts_cache.c
- /Postgres-11.3/pgevent/pgmsgevent.h
- /Postgres-11.3/storage/ipc/sinvaladt.c
- /Postgres-11.3/btree_utils_var.h
- /Postgres-11.3/port/pgmkdirp.c
- /Postgres-11.3/fe_utils/simple_list.c
- /Postgres-11.3/psql/variables.h
- /Postgres-11.3/postgres_fdw/postgres_fdw.c
- /Postgres-11.3/plpy_cursorobject.c
- /Postgres-11.3/commands/publicationcmds.c
- /Postgres-11.3/optimizer/path/pathkeys.c
- /Postgres-11.3/postmaster/pgarch.c
- /Postgres-11.3/commands/view.c
- /Postgres-11.3/storage/ipc/shm_toc.c
- /Postgres-11.3/common/base64.c
- /Postgres-11.3/adt/rangetypes.c
- /Postgres-11.3/tools/msvc/VCBuildProject.pm
- /Postgres-11.3/commands/copy.c
- /Postgres-11.3/tools/msvc/MSBuildProject.pm
- /Postgres-11.3/storage/file/sharedfileset.c
- /Postgres-11.3/adt/selfuncs.c
- /Postgres-11.3/parser/parse_collate.c
- /Postgres-11.3/cache/typcache.c
- /Postgres-11.3/psql/tab-complete.c
- /Postgres-11.3/pg_test_timing/pg_test_timing.c
- /Postgres-11.3/executor/instrument.c
- /Postgres-11.3/tsm_system_rows/tsm_system_rows.c
- /Postgres-11.3/storage/lmgr/s_lock.c
- /Postgres-11.3/adt/genfile.c
- /Postgres-11.3/pgcrypto/md5.c
- /Postgres-11.3/catalog/aclchk.c
- /Postgres-11.3/port/path.c
- /Postgres-11.3/executor/execMain.c
- /Postgres-11.3/adt/tsgistidx.c
- /Postgres-11.3/pgcrypto/px-crypt.c
- /Postgres-11.3/pg_upgrade/exec.c
- /Postgres-11.3/executor/execTuples.c
- /Postgres-11.3/catalog/dependency.c
- /Postgres-11.3/pg_upgrade/dump.c
- /Postgres-11.3/storage/lmgr/lmgr.c
- /Postgres-11.3/preproc/type.h
- /Postgres-11.3/include/sqlda-compat.h
- /Postgres-11.3/fe_utils/conditional.c
- /Postgres-11.3/libpq/pqmq.c
- /Postgres-11.3/cube/cube.c
- /Postgres-11.3/optimizer/geqo/geqo_pool.c
- /Postgres-11.3/replication/logical/message.c
- /Postgres-11.3/common/pg_lzcompress.c
- /Postgres-11.3/tools/msvc/config_default.pl
- /Postgres-11.3/include/pgtypes_date.h
- /Postgres-11.3/adt/json.c
- /Postgres-11.3/ecpglib/data.c
- /Postgres-11.3/btree_bytea.c
- /Postgres-11.3/pg_archivecleanup/t/010_pg_archivecleanup.pl
- /Postgres-11.3/executor/nodeSubplan.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_swedish.c
- /Postgres-11.3/tcn/tcn.c
- /Postgres-11.3/optimizer/geqo/geqo_recombination.c
- /Postgres-11.3/pg_rewind/t/002_databases.pl
- /Postgres-11.3/pgcrypto/pgp-pubkey.c
- /Postgres-11.3/pg_ctl/t/003_promote.pl
- /Postgres-11.3/common/unicode/generate-norm_test_table.pl
- /Postgres-11.3/ltree/_ltree_gist.c
- /Postgres-11.3/mmgr/generation.c
- /Postgres-11.3/timezone/strftime.c
- /Postgres-11.3/adt/network.c
- /Postgres-11.3/nodes/read.c
- /Postgres-11.3/tutorial/funcs_new.c
- /Postgres-11.3/adt/expandeddatum.c
- /Postgres-11.3/pg_config/t/001_pg_config.pl
- /Postgres-11.3/pg_dump/parallel.c
- /Postgres-11.3/replication/logical/snapbuild.c
- /Postgres-11.3/nodes/bitmapset.c
- /Postgres-11.3/adt/jsonb_op.c
- /Postgres-11.3/pg_basebackup/streamutil.c
- /Postgres-11.3/rewrite/rewriteHandler.c
- /Postgres-11.3/pgtypeslib/dt.h
- /Postgres-11.3/storage/freespace/indexfsm.c
- /Postgres-11.3/pg_config/pg_config.c
- /Postgres-11.3/plperl/text2macro.pl
- /Postgres-11.3/nodes/nodeFuncs.c
- /Postgres-11.3/mmgr/memdebug.c
- /Postgres-11.3/pg_basebackup/t/020_pg_receivewal.pl
- /Postgres-11.3/pgcrypto/sha1.h
- /Postgres-11.3/intarray/_intbig_gist.c
- /Postgres-11.3/storage/ipc/shm_mq.c
- /Postgres-11.3/pgcrypto/pgp-compress.c
- /Postgres-11.3/port/getopt_long.c
- /Postgres-11.3/port/noblock.c
- /Postgres-11.3/catalog/index.c
- /Postgres-11.3/port/getpeereid.c
- /Postgres-11.3/pg_trgm/trgm_regexp.c
- /Postgres-11.3/commands/dbcommands.c
- /Postgres-11.3/adt/tsvector_op.c
- /Postgres-11.3/plpy_typeio.c
- /Postgres-11.3/libpq/pqcomm.c
- /Postgres-11.3/storage/buffer/buf_init.c
- /Postgres-11.3/pgtypeslib/datetime.c
- /Postgres-11.3/adt/trigfuncs.c
- /Postgres-11.3/libpq/crypt.c
- /Postgres-11.3/pg_basebackup/t/010_pg_basebackup.pl
- /Postgres-11.3/port/fls.c
- /Postgres-11.3/nodes/extensible.c
- /Postgres-11.3/catalog/pg_aggregate.c
- /Postgres-11.3/adt/regexp.c
- /Postgres-11.3/regex/regc_cvec.c
- /Postgres-11.3/error/assert.c
- /Postgres-11.3/scripts/t/100_vacuumdb.pl
- /Postgres-11.3/cube/cubedata.h
- /Postgres-11.3/adt/rangetypes_selfuncs.c
- /Postgres-11.3/optimizer/path/tidpath.c
- /Postgres-11.3/pg_dump/pg_backup_tar.h
- /Postgres-11.3/sepgsql/relation.c
- /Postgres-11.3/nodes/nodes.c
- /Postgres-11.3/port/chklocale.c
- /Postgres-11.3/misc/rls.c
- /Postgres-11.3/rewrite/rewriteRemove.c
- /Postgres-11.3/libpq/fe-auth.c
- /Postgres-11.3/snowball/libstemmer/stem_KOI8_R_russian.c
- /Postgres-11.3/catalog/indexing.c
- /Postgres-11.3/libpq/libpq-events.c
- /Postgres-11.3/initdb/findtimezone.c
- /Postgres-11.3/adt/tsvector_parser.c
- /Postgres-11.3/libpq/pqexpbuffer.h
- /Postgres-11.3/port/isinf.c
- /Postgres-11.3/pg_dump/pg_dump.h
- /Postgres-11.3/tablefunc/tablefunc.h
- /Postgres-11.3/executor/nodeFunctionscan.c
- /Postgres-11.3/cache/evtcache.c
- /Postgres-11.3/preproc/descriptor.c
- /Postgres-11.3/ecpglib/connect.c
- /Postgres-11.3/tools/msvc/gendef.pl
- /Postgres-11.3/storage/buffer/localbuf.c
- /Postgres-11.3/adt/arrayfuncs.c
- /Postgres-11.3/misc/ps_status.c
- /Postgres-11.3/psql/variables.c
- /Postgres-11.3/adt/name.c
- /Postgres-11.3/btree_cash.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_2_romanian.c
- /Postgres-11.3/lib/hyperloglog.c
- /Postgres-11.3/pgcrypto/crypt-blowfish.c
- /Postgres-11.3/storage/ipc/standby.c
- /Postgres-11.3/pg_trgm/trgm_gin.c
- /Postgres-11.3/port/quotes.c
- /Postgres-11.3/plpgsql/src/pl_scanner.c
- /Postgres-11.3/common/scram-common.c
- /Postgres-11.3/tcop/pquery.c
- /Postgres-11.3/pgcrypto/imath.h
- /Postgres-11.3/psql/command.c
- /Postgres-11.3/lib/bloomfilter.c
- /Postgres-11.3/intarray/_int_gist.c
- /Postgres-11.3/sepgsql/uavc.c
- /Postgres-11.3/adt/tsquery_cleanup.c
- /Postgres-11.3/plpy_resultobject.c
- /Postgres-11.3/storage/lmgr/lwlock.c
- /Postgres-11.3/optimizer/geqo/geqo_px.c
- /Postgres-11.3/nodes/params.c
- /Postgres-11.3/replication/logical/decode.c
- /Postgres-11.3/sepgsql/schema.c
- /Postgres-11.3/commands/operatorcmds.c
- /Postgres-11.3/executor/nodeSort.c
- /Postgres-11.3/catalog/pg_range.c
- /Postgres-11.3/adt/tsquery_util.c
- /Postgres-11.3/pg_upgrade/option.c
- /Postgres-11.3/libpq/fe-connect.c
- /Postgres-11.3/postmaster/checkpointer.c
- /Postgres-11.3/executor/execExprInterp.c
- /Postgres-11.3/jit/llvm/llvmjit.c
- /Postgres-11.3/pg_rewind/timeline.c
- /Postgres-11.3/pg_dump/pg_restore.c
- /Postgres-11.3/nodes/outfuncs.c
- /Postgres-11.3/include/sql3types.h
- /Postgres-11.3/port/atomics.c
- /Postgres-11.3/jit/llvm/llvmjit_inline.cpp
- /Postgres-11.3/scripts/createdb.c
- /Postgres-11.3/adt/tsvector.c
- /Postgres-11.3/pg_upgrade/version.c
- /Postgres-11.3/pg_prewarm/pg_prewarm.c
- /Postgres-11.3/executor/nodeIndexscan.c
- /Postgres-11.3/executor/nodeGather.c
- /Postgres-11.3/pg_basebackup/pg_receivewal.c
- /Postgres-11.3/pgcrypto/pgp-cfb.c
- /Postgres-11.3/psql/command.h
- /Postgres-11.3/btree_date.c
- /Postgres-11.3/storage/large_object/inv_api.c
- /Postgres-11.3/tools/check_bison_recursion.pl
- /Postgres-11.3/pg_dump/pg_dumpall.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_norwegian.c
- /Postgres-11.3/catalog/catalog.c
- /Postgres-11.3/cache/inval.c
- /Postgres-11.3/executor/nodeResult.c
- /Postgres-11.3/tcop/dest.c
- /Postgres-11.3/postgres_fdw/option.c
- /Postgres-11.3/executor/nodeBitmapIndexscan.c
- /Postgres-11.3/adt/tsrank.c
- /Postgres-11.3/psql/help.c
- /Postgres-11.3/tcop/fastpath.c
- /Postgres-11.3/replication/logical/logical.c
- /Postgres-11.3/port/strlcat.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_danish.c
- /Postgres-11.3/sslinfo/sslinfo.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_norwegian.c
- /Postgres-11.3/pg_standby/pg_standby.c
- /Postgres-11.3/port/crypt.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_finnish.c
- /Postgres-11.3/bloom/t/001_wal.pl
- /Postgres-11.3/postmaster/postmaster.c
- /Postgres-11.3/main/main.c
- /Postgres-11.3/pg_ctl/pg_ctl.c
- /Postgres-11.3/pgcrypto/md5.h
- /Postgres-11.3/pg_rewind/fetch.h
- /Postgres-11.3/pgstattuple/pgstatapprox.c
- /Postgres-11.3/generate-errcodes.pl
- /Postgres-11.3/executor/nodeMaterial.c
- /Postgres-11.3/tsearch/ts_locale.c
- /Postgres-11.3/common/saslprep.c
- /Postgres-11.3/storage/lmgr/deadlock.c
- /Postgres-11.3/pg_dump/t/002_pg_dump.pl
- /Postgres-11.3/tutorial/complex.c
- /Postgres-11.3/misc/help_config.c
- /Postgres-11.3/foreign/foreign.c
- /Postgres-11.3/sort/gen_qsort_tuple.pl
- /Postgres-11.3/common/restricted_token.c
- /Postgres-11.3/pgcrypto/px-hmac.c
- /Postgres-11.3/adt/txid.c
- /Postgres-11.3/ecpglib/sqlda.c
- /Postgres-11.3/btree_text.c
- /Postgres-11.3/pg_rewind/logging.h
- /Postgres-11.3/commands/tablecmds.c
- /Postgres-11.3/postgres_fdw/shippable.c
- /Postgres-11.3/sepgsql/proc.c
- /Postgres-11.3/expected/connect-test1.c
- /Postgres-11.3/mmgr/aset.c
- /Postgres-11.3/storage/ipc/barrier.c
- /Postgres-11.3/port/dynloader/win32.c
- /Postgres-11.3/adt/array_expanded.c
- /Postgres-11.3/replication/walreceiver.c
- /Postgres-11.3/partitioning/partprune.c
- /Postgres-11.3/catalog/pg_db_role_setting.c
- /Postgres-11.3/executor/nodeCustom.c
- /Postgres-11.3/lib/knapsack.c
- /Postgres-11.3/adt/datetime.c
- /Postgres-11.3/spi/moddatetime.c
- /Postgres-11.3/misc/superuser.c
- /Postgres-11.3/pg_upgrade/check.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_german.c
- /Postgres-11.3/port/pg_crc32c_sse42_choose.c
- /Postgres-11.3/replication/syncrep.c
- /Postgres-11.3/pg_waldump/rmgrdesc.c
- /Postgres-11.3/include/pgtypes_numeric.h
- /Postgres-11.3/tools/msvc/VSObjectFactory.pm
- /Postgres-11.3/plperl/plperl_opmask.pl
- /Postgres-11.3/optimizer/plan/planagg.c
- /Postgres-11.3/port/system.c
- /Postgres-11.3/plpy_spi.c
- /Postgres-11.3/btree_enum.c
- /Postgres-11.3/pg_upgrade/function.c
- /Postgres-11.3/fe_utils/string_utils.c
- /Postgres-11.3/pgcrypto/mbuf.h
- /Postgres-11.3/pg_basebackup/walmethods.c
- /Postgres-11.3/tools/msvc/Project.pm
- /Postgres-11.3/timezone/tzfile.h
- /Postgres-11.3/storage/lmgr/spin.c
- /Postgres-11.3/pg_upgrade/controldata.c
- /Postgres-11.3/src/sgml/generate-errcodes-table.pl
- /Postgres-11.3/pg_rewind/parsexlog.c
- /Postgres-11.3/libpq/win32.h
- /Postgres-11.3/libpq/be-secure-openssl.c
- /Postgres-11.3/executor/nodeBitmapHeapscan.c
- /Postgres-11.3/misc/timeout.c
- /Postgres-11.3/plpgsql/src/plpgsql.h
- /Postgres-11.3/btree_int4.c
- /Postgres-11.3/replication/logical/relation.c
- /Postgres-11.3/adt/cash.c
- /Postgres-11.3/pg_basebackup/pg_recvlogical.c
- /Postgres-11.3/pg_prewarm/autoprewarm.c
- /Postgres-11.3/storage/ipc/pmsignal.c
- /Postgres-11.3/common/pgfnames.c
- /Postgres-11.3/jit/llvm/llvmjit_deform.c
- /Postgres-11.3/commands/cluster.c
- /Postgres-11.3/commands/explain.c
- /Postgres-11.3/executor/nodeNestloop.c
- /Postgres-11.3/plpy_procedure.c
- /Postgres-11.3/port/win32/crashdump.c
- /Postgres-11.3/regex/regexport.c
- /Postgres-11.3/preproc/parse.pl
- /Postgres-11.3/tsearch/spell.c
- /Postgres-11.3/port/dynloader/hpux.c
- /Postgres-11.3/tsearch/to_tsany.c
- /Postgres-11.3/pg_regress_ecpg.c
- /Postgres-11.3/catalog/pg_collation.c
- /Postgres-11.3/catalog/objectaddress.c
- /Postgres-11.3/psql/input.c
- /Postgres-11.3/commands/foreigncmds.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_danish.c
- /Postgres-11.3/pgcrypto/rijndael.h
- /Postgres-11.3/expected/compat_informix-dec_test.c
- /Postgres-11.3/port/kill.c
- /Postgres-11.3/adminpack/adminpack.c
- /Postgres-11.3/commands/prepare.c
- /Postgres-11.3/sort/tuplesort.c
- /Postgres-11.3/catalog/partition.c
- /Postgres-11.3/parser/scansup.c
- /Postgres-11.3/expected/compat_informix-test_informix2.c
- /Postgres-11.3/pgbench/pgbench.h
- /Postgres-11.3/scripts/t/040_createuser.pl
- /Postgres-11.3/storage/ipc/ipci.c
- /Postgres-11.3/executor/nodeIndexonlyscan.c
- /Postgres-11.3/pg_verify_checksums/pg_verify_checksums.c
- /Postgres-11.3/pgtypeslib/dt_common.c
- /Postgres-11.3/adt/enum.c
- /Postgres-11.3/executor/execReplication.c
- /Postgres-11.3/executor/nodeLockRows.c
- /Postgres-11.3/intarray/_int_gin.c
- /Postgres-11.3/commands/discard.c
- /Postgres-11.3/pg_dump/t/010_dump_connstr.pl
- /Postgres-11.3/common/psprintf.c
- /Postgres-11.3/pg_dump/dumputils.h
- /Postgres-11.3/commands/subscriptioncmds.c
- /Postgres-11.3/pg_dump/t/001_basic.pl
- /Postgres-11.3/libpq/win32.c
- /Postgres-11.3/executor/nodeBitmapOr.c
- /Postgres-11.3/port/thread.c
- /Postgres-11.3/adt/rowtypes.c
- /Postgres-11.3/port/dynloader/linux.c
- /Postgres-11.3/port/unsetenv.c
- /Postgres-11.3/pgcrypto/blf.c
- /Postgres-11.3/commands/schemacmds.c
- /Postgres-11.3/port/rint.c
- /Postgres-11.3/storage/page/itemptr.c
- /Postgres-11.3/optimizer/path/allpaths.c
- /Postgres-11.3/pg_stat_statements/pg_stat_statements.c
- /Postgres-11.3/btree_macaddr.c
- /Postgres-11.3/include/ecpg-pthread-win32.h
- /Postgres-11.3/port/pqsignal.c
- /Postgres-11.3/executor/execPartition.c
- /Postgres-11.3/storage/file/copydir.c
- /Postgres-11.3/postmaster/syslogger.c
- /Postgres-11.3/pg_dump/pg_backup_utils.h
- /Postgres-11.3/storage/buffer/buf_table.c
- /Postgres-11.3/ecpglib/typename.c
- /Postgres-11.3/pg_resetwal/t/002_corrupted.pl
- /Postgres-11.3/catalog/storage.c
- /Postgres-11.3/cache/relcache.c
- /Postgres-11.3/adt/formatting.c
- /Postgres-11.3/intarray/bench/create_test.pl
- /Postgres-11.3/pg_dump/compress_io.c
- /Postgres-11.3/commands/async.c
- /Postgres-11.3/plperl/plc_trusted.pl
- /Postgres-11.3/optimizer/plan/subselect.c
- /Postgres-11.3/port/dynloader/openbsd.h
- /Postgres-11.3/tools/msvc/build.pl
- /Postgres-11.3/parser/parse_func.c
- /Postgres-11.3/replication/logical/logicalfuncs.c
- /Postgres-11.3/port/dynloader/freebsd.h
- /Postgres-11.3/pgcrypto/pgp-s2k.c
- /Postgres-11.3/nodes/makefuncs.c
- /Postgres-11.3/btree_oid.c
- /Postgres-11.3/common/sha2.c
- /Postgres-11.3/snowball/libstemmer/stem_ISO_8859_1_german.c
- /Postgres-11.3/timezone/localtime.c
- /Postgres-11.3/pg_basebackup/pg_basebackup.c
- /Postgres-11.3/pgtypeslib/interval.c
- /Postgres-11.3/pgcrypto/pgp-pubenc.c
- /Postgres-11.3/snowball/libstemmer/stem_UTF_8_dutch.c
- /Postgres-11.3/storage/freespace/fsmpage.c
- /Postgres-11.3/port/inet_aton.c
- /Postgres-11.3/ecpglib/descriptor.c
- /Postgres-11.3/optimizer/path/costsize.c
- /Postgres-11.3/port/win32/mingwcompat.c
- /Postgres-11.3/executor/nodeSeqscan.c
- /Postgres-11.3/psql/common.c
- /Postgres-11.3/adt/like_match.c
- /Postgres-11.3/regex/rege_dfa.c
- /Postgres-11.3/adt/ascii.c
- /Postgres-11.3/catalog/pg_operator.c
- /Postgres-11.3/replication/slotfuncs.c
- /Postgres-11.3/pg_trgm/trgm_gist.c
- /Postgres-11.3/postgres_fdw/postgres_fdw.h
- /Postgres-11.3/catalog/pg_proc.c
- /Postgres-11.3/optimizer/prep/prepjointree.c
- /Postgres-11.3/btree_numeric.c
- /Postgres-11.3/pg_dump/common.c
- /Postgres-11.3/pg_upgrade/relfilenode.c
- /Postgres-11.3/port/pg_crc32c_sse42.c
- /Postgres-11.3/include/ecpg_informix.h
- /Postgres-11.3/lib/stringinfo.c
- /Postgres-11.3/pgtypeslib/timestamp.c
- /Postgres-11.3/optimizer/geqo/geqo_copy.c
- /Postgres-11.3/rewrite/rewriteManip.c
- /Postgres-11.3/adt/varbit.c
- /Postgres-11.3/misc/pg_rusage.c
- /Postgres-11.3/hash/pg_crc.c
- /Postgres-11.3/btree_bit.c
- /Postgres-11.3/port/pg_crc32c_sb8.c
- /Postgres-11.3/ltree/ltree_io.c
- /Postgres-11.3/pgcrypto/pgp-pubdec.c
- /Postgres-11.3/btree_interval.c
- /Postgres-11.3/pg_rewind/datapagemap.c
- /Postgres-11.3/pg_rewind/t/001_basic.pl
- /Postgres-11.3/adt/jsonb_gin.c
- /Postgres-11.3/pg_basebackup/receivelog.c
- /Postgres-11.3/commands/collationcmds.c
- /Postgres-11.3/port/strnlen.c
- /Postgres-11.3/adt/geo_spgist.c
- /Postgres-11.3/expected/compat_informix-sqlda.c
- /Postgres-11.3/postmaster/bgworker.c
- /Postgres-11.3/scripts/t/090_reindexdb.pl
- /Postgres-11.3/common/file_perm.c
- /Postgres-11.3/hstore/hstore_gin.c
- /Postgres-11.3/port/pgstrcasecmp.c
- /Postgres-11.3/storage/ipc/ipc.c
- /Postgres-11.3/xml2/xpath.c
- /Postgres-11.3/pgtypeslib/numeric.c
- /Postgres-11.3/ltree/ltree_op.c
- /Postgres-11.3/amcheck/verify_nbtree.c
- /Postgres-11.3/init/miscinit.c
- /Postgres-11.3/tutorial/funcs.c
- /Postgres-11.3/storage/buffer/freelist.c
- /Postgres-11.3/tsearch/dict_synonym.c
- /Postgres-11.3/adt/network_spgist.c
- /Postgres-11.3/tsearch/wparser_def.c
- /Postgres-11.3/btree_int8.c
- /Postgres-11.3/port/dynloader/aix.h
- /Postgres-11.3/storage/ipc/dsm_impl.c
- /Postgres-11.3/libpq/test/regress.pl
- /Postgres-11.3/parser/parse_utilcmd.c
- /Postgres-11.3/optimizer/geqo/geqo_eval.c
- /Postgres-11.3/tools/msvc/mkvcbuild.pl
- /Postgres-11.3/port/gettimeofday.c
- /Postgres-11.3/btree_float4.c
- /Postgres-11.3/Gen_fmgrtab.pl
- /Postgres-11.3/adt/lockfuncs.c
- /Postgres-11.3/plpgsql/src/pl_handler.c
- /Postgres-11.3/port/win32/timer.c
- /Postgres-11.3/scripts/clusterdb.c
- /Postgres-11.3/cache/relfilenodemap.c
- /Postgres-11.3/parser/parse_param.c
- /Postgres-11.3/lib/rbtree.c
- /Postgres-11.3/pgcrypto/pgp.h
- /Postgres-11.3/scripts/dropdb.c
- /Postgres-11.3/ltree_plpython/ltree_plpython.c
- /Postgres-11.3/fe_utils/print.c
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
PostgreSQL versions 10.x before 10.9 and versions 11.x before 11.4 are vulnerable to a stack-based buffer overflow. Any authenticated user can overflow a stack-based buffer by changing the user's own password to a purpose-crafted value. This often suffices to execute arbitrary code as the PostgreSQL operating system account.
<p>Publish Date: 2019-06-26
<p>URL: <a href=https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-10164>CVE-2019-10164</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>8.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2019-10164">https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2019-10164</a></p>
<p>Release Date: 2019-06-26</p>
<p>Fix Resolution: REL_10_9;REL_11_4</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve high detected in postgres rel cve high severity vulnerability vulnerable library postgresrel mirror of the official postgresql git repository note that this is just a mirror we don t work with pull requests on github to contribute please see library home page a href found in head commit a href library source files the source files were matched to this source library based on a best effort match source libraries are selected from a list of probable public libraries postgres optimizer path equivclass c postgres port inet net ntop c postgres pg basebackup t pg recvlogical pl postgres postmaster startup c postgres pg dump dumputils c postgres adt misc c postgres pg upgrade pg upgrade h postgres xslt proc c postgres adt oracle compat c postgres postmaster pgstat c postgres snowball libstemmer stem iso english c postgres adt tsginidx c postgres cache catcache c postgres tsearch dict thesaurus c postgres common controldata utils c postgres earthdistance earthdistance c postgres pgbench t pgbench with server pl postgres adt pg upgrade support c postgres port socket c postgres pg upgrade util c postgres scripts dropuser c postgres psql crosstabview c postgres lib bipartite match c postgres adt char c postgres nodes value c postgres optimizer geqo geqo misc c postgres adt expandedrecord c postgres cache attoptcache c postgres sepgsql selinux c postgres executor noderecursiveunion c postgres rewrite rewritesupport c postgres hstore hstore h postgres preproc ecpg keywords c postgres bloom blvalidate c postgres bloom blutils c postgres port dirent c postgres bloom blcost c postgres snowball libstemmer stem utf portuguese c postgres storage page bufpage c postgres common unicode generate unicode norm table pl postgres pg dump parallel h postgres test decoding test decoding c postgres ltree ltree gist c postgres catalog genbki pl postgres catalog pg inherits c postgres pg upgrade parallel c postgres mmgr dsa c postgres misc backend random c postgres common unicode norm c postgres snowball libstemmer stem utf romanian c postgres commands constraint c postgres commands extension c postgres psql common h postgres time combocid c postgres tools copyright pl postgres snowball libstemmer stem iso portuguese c postgres adt quote c postgres plpy exec c postgres commands lockcmds c postgres common string c postgres replication logical reorderbuffer c postgres parser parse agg c postgres pgcrypto internal c postgres libpq fe c postgres ecpglib extern h postgres commands portalcmds c postgres adt amutils c postgres pgcrypto pgp mpi c postgres jsonb plpython jsonb plpython c postgres cache syscache c postgres parser parse type c postgres libpq fe print c postgres plperl plperl helpers h postgres parser parse oper c postgres scripts pg isready c postgres nodes readfuncs c postgres tools msvc builddoc pl postgres common unicode norm test c postgres pgcrypto crypt gensalt c postgres commands user c postgres parser parse cte c postgres optimizer geqo geqo erx c postgres pgcrypto pgp mpi openssl c postgres libpq pqsignal c postgres plpy planobject c postgres pg dump pg backup db h postgres catalog pg enum c postgres port dynloader netbsd c postgres replication logical launcher c postgres executor nodesubqueryscan c postgres snowball dict snowball c postgres storage lmgr lock c postgres preproc ecpg c postgres regex regprefix c postgres vacuumlo vacuumlo c postgres plpy spi h postgres init postinit c postgres psql startup c postgres include sqlca h postgres storage smgr smgrtype c postgres initdb t initdb pl postgres preproc extern h postgres port qsort c postgres psql describe c postgres adt array typanalyze c postgres expected compat informix rfmtdate c postgres pg ctl t start stop pl postgres adt cryptohashes c postgres cache relmapper c postgres regex regexec c postgres catalog heap c postgres catalog toasting c postgres parser check keywords pl postgres pgcrypto pgp mpi internal c postgres regex regc nfa c postgres adt dbsize c postgres adt c postgres executor nodelimit c postgres lib binaryheap c postgres pgbench t pgbench no server pl postgres optimizer geqo geqo selection c postgres executor nodesamplescan c postgres pgbench pgbench c postgres pg rewind fetch c postgres psql psqlscanslash h postgres libpq pqexpbuffer c postgres plpgsql src generate plerrcodes pl postgres pg test fsync pg test fsync c postgres common openssl c postgres commands functioncmds c postgres adt encode c postgres bootstrap bootstrap c postgres catalog pg conversion c postgres jit jit c postgres executor execgrouping c postgres replication walsender c postgres port sema c postgres adt inet net pton c postgres adt arrayutils c postgres snowball libstemmer stem iso italian c postgres adt array selfuncs c postgres pg upgrade server c postgres tsearch ts utils c postgres nodes equalfuncs c postgres pg freespacemap pg freespacemap c postgres port dynloader darwin c postgres seg seg c postgres sort sortsupport c postgres common ip c postgres scripts t vacuumdb stages pl postgres tools msvc mkvcbuild pm postgres pgcrypto pgp encrypt c postgres snowball libstemmer stem utf spanish c postgres tsearch dict simple c postgres pgstattuple pgstatindex c postgres adt orderedsetaggs c postgres pg dump pg backup null c postgres executor nodenamedtuplestorescan c postgres ecpglib misc c postgres btree inet c postgres rewrite rowsecurity c postgres tools msvc pgflex pl postgres unaccent unaccent c postgres commands comment c postgres port dynloader netbsd h postgres ltree ltxtquery op c postgres libpq libpq events h postgres executor execprocnode c postgres pg rewind t rewindtest pm postgres executor nodeagg c postgres port c postgres adt uuid c postgres optimizer geqo geqo main c postgres pgcrypto px c postgres pg dump pg dump sort c postgres port c postgres pg dump pg backup directory c postgres commands typecmds c postgres snowball libstemmer stem utf french c postgres replication pgoutput pgoutput c postgres citext citext c postgres port pg c postgres pg rewind t extrafiles pl postgres port mkdtemp c postgres commands indexcmds c postgres pgtypeslib common c postgres ltree c postgres storage page checksum c postgres bloom blinsert c postgres postmaster fork process c postgres spi autoinc c postgres hash hashfn c postgres plpgsql src pl funcs c postgres sepgsql label c postgres storage ipc procsignal c postgres spi timetravel c postgres commands vacuum c postgres misc tzparser c postgres tsearch ts parse c postgres snowball libstemmer utilities c postgres adt acl c postgres commands amcmds c postgres initdb initdb c postgres optimizer geqo geqo cx c postgres executor executils c postgres port pgsleep c postgres tcop utility c postgres pg ctl t status pl postgres plpgsql src pl exec c postgres plperl ppport h postgres replication logical tablesync c postgres tsearch regis c postgres pg dump pg backup tar c postgres btree utils var c postgres postmaster walwriter c postgres libpq libpq fe h postgres commands variable c postgres pg waldump compat c postgres sepgsql dml c postgres scripts t clusterdb pl postgres plpy subxactobject c postgres port dynloader openbsd c postgres port dynloader hpux h postgres tools fix old flex code pl postgres ecpglib execute c postgres tablefunc tablefunc c postgres dict xsyn dict xsyn c postgres pg basebackup walmethods h postgres sepgsql database c postgres storage lmgr predicate c postgres pgcrypto pgcrypto h postgres libpq fe auth h postgres pageinspect hashfuncs c postgres common keywords c postgres port getrusage c postgres common username c postgres pg rewind libpq fetch c postgres pgcrypto pgp info c postgres file fdw file fdw c postgres uuid ossp uuid ossp c postgres mmgr portalmem c postgres snowball libstemmer stem utf english c postgres adt numutils c postgres port pg strong random c postgres pg controldata t pg controldata pl postgres parser analyze c postgres pg waldump pg waldump c postgres commands seclabel c postgres pg trgm trgm h postgres adt levenshtein c postgres psql crosstabview h postgres adt float c postgres resowner resowner c postgres intarray int bool c postgres port c postgres pg rewind file ops h postgres pg rewind pg rewind c postgres port tar c postgres executor functions c postgres storage freespace freespace c postgres snowball libstemmer stem iso spanish c postgres storage file buffile c postgres catalog catalog pm postgres btree uuid c postgres storage lmgr proc c postgres regex regc lex c postgres regex regc color c postgres port c postgres libpq fe secure openssl c postgres commands statscmds c postgres parser parse node c postgres port dynloader cygwin h postgres common file utils c postgres storage ipc sinval c postgres libpq ifaddr c postgres adt like c postgres pg dump pg backup h postgres adt rangetypes spgist c postgres scripts reindexdb c postgres btree ts c postgres bloom blvacuum c postgres pgcrypto px crypt h postgres jit llvm llvmjit wrap cpp postgres commands aggregatecmds c postgres lib dshash c postgres bloom bloom h postgres pgcrypto c postgres executor nodeforeignscan c postgres jit llvm llvmjit error cpp postgres pgcrypto pgp armor c postgres parser parser c postgres btree utils num h postgres pgcrypto openssl c postgres tsearch wparser c postgres scripts vacuumdb c postgres optimizer path clausesel c postgres libpq fe secure c postgres executor execjunk c postgres executor nodemodifytable c postgres btree c postgres common exec c postgres plperl plperl c postgres pg dump compress io h postgres adt jsonfuncs c postgres postgres fdw deparse c postgres adt rangetypes typanalyze c postgres plpy util c postgres pg controldata pg controldata c postgres commands matview c postgres executor execami c postgres libpq pqformat c postgres storage smgr smgr c postgres storage lmgr condition variable c postgres executor execparallel c postgres port signal c postgres storage ipc procarray c postgres snowball libstemmer stem utf finnish c postgres optimizer path joinrels c postgres libpq fe auth scram c postgres statistics mvdistinct c postgres adt network selfuncs c postgres pg upgrade pg upgrade c postgres adt tid c postgres mmgr mcxt c postgres adt int c postgres commands proclang c postgres tsearch ts selfuncs c postgres adt oid c postgres executor execsrf c postgres fmgr fmgr c postgres port c postgres executor execcurrent c postgres snowball libstemmer stem iso hungarian c postgres libpq auth c postgres snowball libstemmer stem utf turkish c postgres port sysv shmem c postgres commands conversioncmds c postgres storage lmgr generate lwlocknames pl postgres jsonb plperl jsonb plperl c postgres tools ifaddrs test ifaddrs c postgres preproc check rules pl postgres adt c postgres snowball libstemmer stem utf russian c postgres pg upgrade info c postgres parser parse clause c postgres executor nodectescan c postgres adt rangetypes gist c postgres c postgres preproc parser c postgres pg archivecleanup pg archivecleanup c postgres adt regproc c postgres common wait error c postgres ltree lquery op c postgres misc queryenvironment c postgres include ecpglib h postgres storage ipc dsm c postgres storage buffer bufmgr c postgres common c postgres port getaddrinfo c postgres misc guc c postgres auto explain auto explain c postgres hstore plpython hstore plpython c postgres storage ipc latch c postgres pageinspect brinfuncs c postgres adt varchar c postgres rewrite rewritedefine c postgres psql create help pl postgres plpython h postgres preproc output c postgres executor nodesetop c postgres adt tsquery gist c postgres pageinspect btreefuncs c postgres snowball libstemmer api c postgres commands trigger c postgres pgcrypto imath c postgres regex regerror c postgres snowball libstemmer stem iso porter c postgres port posix sema c postgres plpy plpymodule c postgres executor nodehashjoin c postgres replication logical worker c postgres tools msvc vcregress pl postgres adt mac c postgres tsearch dict ispell c postgres include pgtypes interval h postgres include ecpgerrno h postgres plpy elog c postgres snowball libstemmer stem iso french c postgres time snapmgr c postgres pg dump pg backup archiver h postgres tcop postgres c postgres catalog objectaccess c postgres commands dropcmds c postgres optimizer plan planmain c postgres pgcrypto internal c postgres pg rewind file ops c postgres commands alter c postgres libpq fe lobj c postgres common fe memutils c postgres include sqlda native h postgres optimizer plan setrefs c postgres optimizer plan analyzejoins c postgres pg rewind logging c postgres pageinspect ginfuncs c postgres regex regc pg locale c postgres snowball libstemmer stem utf italian c postgres intarray bench bench pl postgres preproc variable c postgres misc pg controldata c postgres psql large obj c postgres catalog pg namespace c postgres partitioning partbounds c postgres storage ipc shmqueue c postgres commands event trigger c postgres nodes copyfuncs c postgres spi insert username c postgres replication walreceiverfuncs c postgres fuzzystrmatch dmetaphone c postgres hstore hstore op c postgres postgres fdw connection c postgres adt network gist c postgres cache partcache c postgres ltree ltree op c postgres error elog c postgres pg dump pg backup archiver c postgres seg seg validate pl postgres libpq fe secure common h postgres nodes print c postgres port qsort arg c postgres nodes tidbitmap c postgres hstore hstore gist c postgres snowball libstemmer stem iso dutch c postgres pgrowlocks pgrowlocks c postgres commands vacuumlazy c postgres adt nabstime c postgres psql mainloop c postgres executor nodemergeappend c postgres adt domains c postgres tsm system time tsm system time c postgres plpy typeio h postgres pg rewind pg rewind h postgres scripts common h postgres timezone pgtz h postgres catalog pg publication c postgres time tqual c postgres expected compat informix charfuncs c postgres pgcrypto rijndael c postgres postmaster bgwriter c postgres adt varlena c postgres libpq libpq int h postgres adt geo ops c postgres expected compat informix describe c postgres cache plancache c postgres sort sharedtuplestore c postgres fmgr dfmgr c postgres gen dummy probes pl postgres executor nodemergejoin c postgres pg rewind filemap c postgres psql settings h postgres unaccent generate unaccent rules py postgres scripts createuser c postgres cache lsyscache c postgres scripts t createdb pl postgres port shmem c postgres plpy procedure h postgres port sysv sema c postgres pg resetwal pg resetwal c postgres expected compat oracle char array c postgres optimizer geqo geqo c postgres ltree ltxtquery io c postgres adt datum c postgres timezone pgtz c postgres pg rewind copy fetch c postgres mmgr slab c postgres pageinspect heapfuncs c postgres scripts common c postgres pg rewind filemap h postgres tools msvc solution pm postgres timezone private h postgres adt format type c postgres sort tuplestore c postgres catalog pg constraint c postgres port dirmod c postgres jit llvm llvmjit types c postgres regex regfree c postgres replication logical origin c postgres storage file fd c postgres catalog pg shdepend c postgres tsearch ts typanalyze c postgres hstore plperl hstore plperl c postgres spi refint c postgres expected compat informix rfmtlong c postgres adt geo selfuncs c postgres postmaster autovacuum c postgres commands analyze c postgres lib ilist c postgres bloom blscan c postgres lib pairingheap c postgres commands tsearchcmds c postgres port pgcheckdir c postgres hstore hstore compat c postgres regex regcomp c postgres intarray int h postgres adt jsonb c postgres adt tsquery c postgres pg dump pg backup utils c postgres preproc c keywords c postgres pg visibility pg visibility c postgres port getopt c postgres misc pg config c postgres include pgtypes timestamp h postgres hstore hstore io c postgres auth delay auth delay c postgres catalog pg depend c postgres pgcrypto mbuf c postgres plpgsql src pl comp c postgres tools msvc pgbison pl postgres pageinspect fsmfuncs c postgres psql prompt c postgres optimizer geqo geqo mutation c postgres adt tsquery op c postgres pgcrypto pgp c postgres catalog pg type c postgres statistics dependencies c postgres pgcrypto crypt c postgres pgcrypto crypt des c postgres optimizer plan initsplan c postgres expected compat informix test informix c postgres port snprintf c postgres mmgr freepage c postgres sepgsql sepgsql h postgres adt jsonb util c postgres fe utils mbprint c postgres src sgml mk feature tables pl postgres pg trgm trgm op c postgres pg rewind datapagemap h postgres common relpath c postgres snowball libstemmer stem utf porter c postgres preproc type c postgres executor nodegroup c postgres init globals c postgres parser parse coerce c postgres tools msvc install pm postgres pgcrypto blf h postgres adt ri triggers c postgres common rmtree c postgres port strlcpy c postgres storage smgr md c postgres parser parse target c postgres optimizer path joinpath c postgres fuzzystrmatch fuzzystrmatch c postgres libpq fe exec c postgres snowball libstemmer stem iso swedish c postgres pg basebackup streamutil h postgres btree utils num c postgres optimizer plan planner c postgres pg upgrade file c postgres common config info c postgres fmgr funcapi c postgres include ecpgtype h postgres catalog namespace c postgres adt pgstatfuncs c postgres optimizer plan createplan c postgres jit llvm llvmjit expr c postgres parser parse expr c postgres libpq test uri regress c postgres hash dynahash c postgres expected compat informix rnull c postgres port fseeko c postgres libpq fe c postgres ecpglib prepare c postgres tools msvc install pl postgres optimizer geqo geqo c postgres pg dump pg backup db c postgres commands createas c postgres executor execscan c postgres sepgsql hooks c postgres libpq fe secure common c postgres plpy main c postgres port pg choose c postgres ecpglib memory c postgres psql describe h postgres pgcrypto px h postgres adt pg lsn c postgres replication slot c postgres pg dump pg dump c postgres libpq auth scram c postgres executor nodeprojectset c postgres executor execexpr c postgres cache spccache c postgres statistics extended stats c postgres executor nodeappend c postgres pgstattuple pgstattuple c postgres plpy main h postgres adt ruleutils c postgres plperl plc perlboot pl postgres pg buffercache pg buffercache pages c postgres adt tsquery rewrite c postgres preproc keywords c postgres libpq fe misc c postgres commands define c postgres port dynloader freebsd c postgres ecpglib error c postgres pgcrypto pgcrypto c postgres optimizer geqo geqo pmx c postgres scripts t connstr pl postgres regex regc locale c postgres executor nodehash c postgres catalog pg subscription c postgres misc sampling c postgres compatlib informix c postgres psql stringutils c postgres port open c postgres replication basebackup c postgres psql copy c postgres pgcrypto pgp pgsql c postgres ltree ltree h postgres pageinspect rawpage c postgres commands opclasscmds c postgres psql input h postgres pg basebackup receivelog h postgres optimizer geqo geqo random c postgres adt pseudotypes c postgres plpy subxactobject h postgres libpq pthread c postgres replication libpqwalreceiver libpqwalreceiver c postgres commands sequence c postgres adt bool c postgres storage file reinit c postgres port dynloader linux h postgres adt array userfuncs c postgres port dynloader solaris h postgres pg dump pg backup custom c postgres parser parse relation c postgres tools findoidjoins findoidjoins c postgres parser parse enr c postgres pgcrypto pgp decrypt c postgres psql stringutils h postgres libpq be secure c postgres btree time c postgres plpy elog h postgres pg upgrade tablespace c postgres executor nodegathermerge c postgres pgtypeslib extern h postgres libpq be fsstubs c postgres replication logical proto c postgres snowball libstemmer stem utf hungarian c postgres port sprompt c postgres libpq be secure common c postgres pgevent pgevent c postgres btree gist c postgres executor nodebitmapand c postgres plperl plperl h postgres adt date c postgres nodes list c postgres optimizer path indxpath c postgres adt timestamp c postgres btree c postgres tsearch dict c postgres catalog pg largeobject c postgres intarray int op c postgres executor execindexing c postgres timezone zic c postgres pg rewind t pg xlog symlink pl postgres generate spiexceptions pl postgres adt inet cidr ntop c postgres commands policy c postgres commands tablespace c postgres adt numeric c postgres storage ipc shmem c postgres lo lo c postgres btree c postgres adt pg locale c postgres sort logtape c postgres libpq hba c postgres cache ts cache c postgres pgevent pgmsgevent h postgres storage ipc sinvaladt c postgres btree utils var h postgres port pgmkdirp c postgres fe utils simple list c postgres psql variables h postgres postgres fdw postgres fdw c postgres plpy cursorobject c postgres commands publicationcmds c postgres optimizer path pathkeys c postgres postmaster pgarch c postgres commands view c postgres storage ipc shm toc c postgres common c postgres adt rangetypes c postgres tools msvc vcbuildproject pm postgres commands copy c postgres tools msvc msbuildproject pm postgres storage file sharedfileset c postgres adt selfuncs c postgres parser parse collate c postgres cache typcache c postgres psql tab complete c postgres pg test timing pg test timing c postgres executor instrument c postgres tsm system rows tsm system rows c postgres storage lmgr s lock c postgres adt genfile c postgres pgcrypto c postgres catalog aclchk c postgres port path c postgres executor execmain c postgres adt tsgistidx c postgres pgcrypto px crypt c postgres pg upgrade exec c postgres executor exectuples c postgres catalog dependency c postgres pg upgrade dump c postgres storage lmgr lmgr c postgres preproc type h postgres include sqlda compat h postgres fe utils conditional c postgres libpq pqmq c postgres cube cube c postgres optimizer geqo geqo pool c postgres replication logical message c postgres common pg lzcompress c postgres tools msvc config default pl postgres include pgtypes date h postgres adt json c postgres ecpglib data c postgres btree bytea c postgres pg archivecleanup t pg archivecleanup pl postgres executor nodesubplan c postgres snowball libstemmer stem utf swedish c postgres tcn tcn c postgres optimizer geqo geqo recombination c postgres pg rewind t databases pl postgres pgcrypto pgp pubkey c postgres pg ctl t promote pl postgres common unicode generate norm test table pl postgres ltree ltree gist c postgres mmgr generation c postgres timezone strftime c postgres adt network c postgres nodes read c postgres tutorial funcs new c postgres adt expandeddatum c postgres pg config t pg config pl postgres pg dump parallel c postgres replication logical snapbuild c postgres nodes bitmapset c postgres adt jsonb op c postgres pg basebackup streamutil c postgres rewrite rewritehandler c postgres pgtypeslib dt h postgres storage freespace indexfsm c postgres pg config pg config c postgres plperl pl postgres nodes nodefuncs c postgres mmgr memdebug c postgres pg basebackup t pg receivewal pl postgres pgcrypto h postgres intarray intbig gist c postgres storage ipc shm mq c postgres pgcrypto pgp compress c postgres port getopt long c postgres port noblock c postgres catalog index c postgres port getpeereid c postgres pg trgm trgm regexp c postgres commands dbcommands c postgres adt tsvector op c postgres plpy typeio c postgres libpq pqcomm c postgres storage buffer buf init c postgres pgtypeslib datetime c postgres adt trigfuncs c postgres libpq crypt c postgres pg basebackup t pg basebackup pl postgres port fls c postgres nodes extensible c postgres catalog pg aggregate c postgres adt regexp c postgres regex regc cvec c postgres error assert c postgres scripts t vacuumdb pl postgres cube cubedata h postgres adt rangetypes selfuncs c postgres optimizer path tidpath c postgres pg dump pg backup tar h postgres sepgsql relation c postgres nodes nodes c postgres port chklocale c postgres misc rls c postgres rewrite rewriteremove c postgres libpq fe auth c postgres snowball libstemmer stem r russian c postgres catalog indexing c postgres libpq libpq events c postgres initdb findtimezone c postgres adt tsvector parser c postgres libpq pqexpbuffer h postgres port isinf c postgres pg dump pg dump h postgres tablefunc tablefunc h postgres executor nodefunctionscan c postgres cache evtcache c postgres preproc descriptor c postgres ecpglib connect c postgres tools msvc gendef pl postgres storage buffer localbuf c postgres adt arrayfuncs c postgres misc ps status c postgres psql variables c postgres adt name c postgres btree cash c postgres snowball libstemmer stem iso romanian c postgres lib hyperloglog c postgres pgcrypto crypt blowfish c postgres storage ipc standby c postgres pg trgm trgm gin c postgres port quotes c postgres plpgsql src pl scanner c postgres common scram common c postgres tcop pquery c postgres pgcrypto imath h postgres psql command c postgres lib bloomfilter c postgres intarray int gist c postgres sepgsql uavc c postgres adt tsquery cleanup c postgres plpy resultobject c postgres storage lmgr lwlock c postgres optimizer geqo geqo px c postgres nodes params c postgres replication logical decode c postgres sepgsql schema c postgres commands operatorcmds c postgres executor nodesort c postgres catalog pg range c postgres adt tsquery util c postgres pg upgrade option c postgres libpq fe connect c postgres postmaster checkpointer c postgres executor execexprinterp c postgres jit llvm llvmjit c postgres pg rewind timeline c postgres pg dump pg restore c postgres nodes outfuncs c postgres include h postgres port atomics c postgres jit llvm llvmjit inline cpp postgres scripts createdb c postgres adt tsvector c postgres pg upgrade version c postgres pg prewarm pg prewarm c postgres executor nodeindexscan c postgres executor nodegather c postgres pg basebackup pg receivewal c postgres pgcrypto pgp cfb c postgres psql command h postgres btree date c postgres storage large object inv api c postgres tools check bison recursion pl postgres pg dump pg dumpall c postgres snowball libstemmer stem iso norwegian c postgres catalog catalog c postgres cache inval c postgres executor noderesult c postgres tcop dest c postgres postgres fdw option c postgres executor nodebitmapindexscan c postgres adt tsrank c postgres psql help c postgres tcop fastpath c postgres replication logical logical c postgres port strlcat c postgres snowball libstemmer stem iso danish c postgres sslinfo sslinfo c postgres snowball libstemmer stem utf norwegian c postgres pg standby pg standby c postgres port crypt c postgres snowball libstemmer stem iso finnish c postgres bloom t wal pl postgres postmaster postmaster c postgres main main c postgres pg ctl pg ctl c postgres pgcrypto h postgres pg rewind fetch h postgres pgstattuple pgstatapprox c postgres generate errcodes pl postgres executor nodematerial c postgres tsearch ts locale c postgres common saslprep c postgres storage lmgr deadlock c postgres pg dump t pg dump pl postgres tutorial complex c postgres misc help config c postgres foreign foreign c postgres sort gen qsort tuple pl postgres common restricted token c postgres pgcrypto px hmac c postgres adt txid c postgres ecpglib sqlda c postgres btree text c postgres pg rewind logging h postgres commands tablecmds c postgres postgres fdw shippable c postgres sepgsql proc c postgres expected connect c postgres mmgr aset c postgres storage ipc barrier c postgres port dynloader c postgres adt array expanded c postgres replication walreceiver c postgres partitioning partprune c postgres catalog pg db role setting c postgres executor nodecustom c postgres lib knapsack c postgres adt datetime c postgres spi moddatetime c postgres misc superuser c postgres pg upgrade check c postgres snowball libstemmer stem utf german c postgres port pg choose c postgres replication syncrep c postgres pg waldump rmgrdesc c postgres include pgtypes numeric h postgres tools msvc vsobjectfactory pm postgres plperl plperl opmask pl postgres optimizer plan planagg c postgres port system c postgres plpy spi c postgres btree enum c postgres pg upgrade function c postgres fe utils string utils c postgres pgcrypto mbuf h postgres pg basebackup walmethods c postgres tools msvc project pm postgres timezone tzfile h postgres storage lmgr spin c postgres pg upgrade controldata c postgres src sgml generate errcodes table pl postgres pg rewind parsexlog c postgres libpq h postgres libpq be secure openssl c postgres executor nodebitmapheapscan c postgres misc timeout c postgres plpgsql src plpgsql h postgres btree c postgres replication logical relation c postgres adt cash c postgres pg basebackup pg recvlogical c postgres pg prewarm autoprewarm c postgres storage ipc pmsignal c postgres common pgfnames c postgres jit llvm llvmjit deform c postgres commands cluster c postgres commands explain c postgres executor nodenestloop c postgres plpy procedure c postgres port crashdump c postgres regex regexport c postgres preproc parse pl postgres tsearch spell c postgres port dynloader hpux c postgres tsearch to tsany c postgres pg regress ecpg c postgres catalog pg collation c postgres catalog objectaddress c postgres psql input c postgres commands foreigncmds c postgres snowball libstemmer stem utf danish c postgres pgcrypto rijndael h postgres expected compat informix dec test c postgres port kill c postgres adminpack adminpack c postgres commands prepare c postgres sort tuplesort c postgres catalog partition c postgres parser scansup c postgres expected compat informix test c postgres pgbench pgbench h postgres scripts t createuser pl postgres storage ipc ipci c postgres executor nodeindexonlyscan c postgres pg verify checksums pg verify checksums c postgres pgtypeslib dt common c postgres adt enum c postgres executor execreplication c postgres executor nodelockrows c postgres intarray int gin c postgres commands discard c postgres pg dump t dump connstr pl postgres common psprintf c postgres pg dump dumputils h postgres commands subscriptioncmds c postgres pg dump t basic pl postgres libpq c postgres executor nodebitmapor c postgres port thread c postgres adt rowtypes c postgres port dynloader linux c postgres port unsetenv c postgres pgcrypto blf c postgres commands schemacmds c postgres port rint c postgres storage page itemptr c postgres optimizer path allpaths c postgres pg stat statements pg stat statements c postgres btree macaddr c postgres include ecpg pthread h postgres port pqsignal c postgres executor execpartition c postgres storage file copydir c postgres postmaster syslogger c postgres pg dump pg backup utils h postgres storage buffer buf table c postgres ecpglib typename c postgres pg resetwal t corrupted pl postgres catalog storage c postgres cache relcache c postgres adt formatting c postgres intarray bench create test pl postgres pg dump compress io c postgres commands async c postgres plperl plc trusted pl postgres optimizer plan subselect c postgres port dynloader openbsd h postgres tools msvc build pl postgres parser parse func c postgres replication logical logicalfuncs c postgres port dynloader freebsd h postgres pgcrypto pgp c postgres nodes makefuncs c postgres btree oid c postgres common c postgres snowball libstemmer stem iso german c postgres timezone localtime c postgres pg basebackup pg basebackup c postgres pgtypeslib interval c postgres pgcrypto pgp pubenc c postgres snowball libstemmer stem utf dutch c postgres storage freespace fsmpage c postgres port inet aton c postgres ecpglib descriptor c postgres optimizer path costsize c postgres port mingwcompat c postgres executor nodeseqscan c postgres psql common c postgres adt like match c postgres regex rege dfa c postgres adt ascii c postgres catalog pg operator c postgres replication slotfuncs c postgres pg trgm trgm gist c postgres postgres fdw postgres fdw h postgres catalog pg proc c postgres optimizer prep prepjointree c postgres btree numeric c postgres pg dump common c postgres pg upgrade relfilenode c postgres port pg c postgres include ecpg informix h postgres lib stringinfo c postgres pgtypeslib timestamp c postgres optimizer geqo geqo copy c postgres rewrite rewritemanip c postgres adt varbit c postgres misc pg rusage c postgres hash pg crc c postgres btree bit c postgres port pg c postgres ltree ltree io c postgres pgcrypto pgp pubdec c postgres btree interval c postgres pg rewind datapagemap c postgres pg rewind t basic pl postgres adt jsonb gin c postgres pg basebackup receivelog c postgres commands collationcmds c postgres port strnlen c postgres adt geo spgist c postgres expected compat informix sqlda c postgres postmaster bgworker c postgres scripts t reindexdb pl postgres common file perm c postgres hstore hstore gin c postgres port pgstrcasecmp c postgres storage ipc ipc c postgres xpath c postgres pgtypeslib numeric c postgres ltree ltree op c postgres amcheck verify nbtree c postgres init miscinit c postgres tutorial funcs c postgres storage buffer freelist c postgres tsearch dict synonym c postgres adt network spgist c postgres tsearch wparser def c postgres btree c postgres port dynloader aix h postgres storage ipc dsm impl c postgres libpq test regress pl postgres parser parse utilcmd c postgres optimizer geqo geqo eval c postgres tools msvc mkvcbuild pl postgres port gettimeofday c postgres btree c postgres gen fmgrtab pl postgres adt lockfuncs c postgres plpgsql src pl handler c postgres port timer c postgres scripts clusterdb c postgres cache relfilenodemap c postgres parser parse param c postgres lib rbtree c postgres pgcrypto pgp h postgres scripts dropdb c postgres ltree plpython ltree plpython c postgres fe utils print c vulnerability details postgresql versions x before and versions x before are vulnerable to a stack based buffer overflow any authenticated user can overflow a stack based buffer by changing the user s own password to a purpose crafted value this often suffices to execute arbitrary code as the postgresql operating system account publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required low user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution rel rel step up your open source security game with whitesource
| 1
|
16,250
| 9,744,713,282
|
IssuesEvent
|
2019-06-03 07:47:57
|
jamijam/example-php
|
https://api.github.com/repos/jamijam/example-php
|
opened
|
CVE-2015-3176 (Medium) detected in moodle/moodle-v2.6.2
|
security vulnerability
|
## CVE-2015-3176 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>moodle/moodle-v2.6.2</b></p></summary>
<p>Moodle - the world's open source learning platform</p>
<p>
Dependency Hierarchy:
- :x: **moodle/moodle-v2.6.2** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://api.github.com/repos/jamijam/example-php/commits/aeb8c0291b95008a9cef67b35b89c22f5054b58d">aeb8c0291b95008a9cef67b35b89c22f5054b58d</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
The account-confirmation feature in login/confirm.php in Moodle through 2.5.9, 2.6.x before 2.6.11, 2.7.x before 2.7.8, and 2.8.x before 2.8.6 allows remote attackers to obtain sensitive full-name information by attempting to self-register.
<p>Publish Date: 2015-06-01
<p>URL: <a href=https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3176>CVE-2015-3176</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 2 Score Details (<b>4.3</b>)</summary>
<p>
Base Score Metrics not available</p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2015-3176">https://nvd.nist.gov/vuln/detail/CVE-2015-3176</a></p>
<p>Release Date: 2015-06-01</p>
<p>Fix Resolution: 2.6.11,2.7.8,2.8.6</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2015-3176 (Medium) detected in moodle/moodle-v2.6.2 - ## CVE-2015-3176 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>moodle/moodle-v2.6.2</b></p></summary>
<p>Moodle - the world's open source learning platform</p>
<p>
Dependency Hierarchy:
- :x: **moodle/moodle-v2.6.2** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://api.github.com/repos/jamijam/example-php/commits/aeb8c0291b95008a9cef67b35b89c22f5054b58d">aeb8c0291b95008a9cef67b35b89c22f5054b58d</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
The account-confirmation feature in login/confirm.php in Moodle through 2.5.9, 2.6.x before 2.6.11, 2.7.x before 2.7.8, and 2.8.x before 2.8.6 allows remote attackers to obtain sensitive full-name information by attempting to self-register.
<p>Publish Date: 2015-06-01
<p>URL: <a href=https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3176>CVE-2015-3176</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 2 Score Details (<b>4.3</b>)</summary>
<p>
Base Score Metrics not available</p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2015-3176">https://nvd.nist.gov/vuln/detail/CVE-2015-3176</a></p>
<p>Release Date: 2015-06-01</p>
<p>Fix Resolution: 2.6.11,2.7.8,2.8.6</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve medium detected in moodle moodle cve medium severity vulnerability vulnerable library moodle moodle moodle the world s open source learning platform dependency hierarchy x moodle moodle vulnerable library found in head commit a href vulnerability details the account confirmation feature in login confirm php in moodle through x before x before and x before allows remote attackers to obtain sensitive full name information by attempting to self register publish date url a href cvss score details base score metrics not available suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource
| 1
|
184,627
| 32,021,763,138
|
IssuesEvent
|
2023-09-22 05:30:05
|
energizer-develop/Y_FE_WIKI
|
https://api.github.com/repos/energizer-develop/Y_FE_WIKI
|
closed
|
Wiki Component Responsive Design
|
design
|
## 설명
- 위키 컴포넌트 모바일 반응형 디자인 구현
## 할 일
- [ ] 위키 컴포넌트 반응형 구현
- [ ] 네비게이션 바 반응형 구현
|
1.0
|
Wiki Component Responsive Design - ## 설명
- 위키 컴포넌트 모바일 반응형 디자인 구현
## 할 일
- [ ] 위키 컴포넌트 반응형 구현
- [ ] 네비게이션 바 반응형 구현
|
non_secu
|
wiki component responsive design 설명 위키 컴포넌트 모바일 반응형 디자인 구현 할 일 위키 컴포넌트 반응형 구현 네비게이션 바 반응형 구현
| 0
|
261,977
| 27,831,507,112
|
IssuesEvent
|
2023-03-20 05:32:14
|
ministryofjustice/hmpps-probation-integration-services
|
https://api.github.com/repos/ministryofjustice/hmpps-probation-integration-services
|
opened
|
CVE-2023-24998 (tier-to-delius)
|
dependencies security
|
Apache Commons FileUpload: FileUpload DoS with excessive parts
* Project: tier-to-delius
* Package: `commons-fileupload:commons-fileupload:1.4`
* Location: `app/libs/commons-fileupload-1.4.jar`
>Apache Commons FileUpload before 1.5 does not limit the number of request parts to be processed resulting in the possibility of an attacker triggering a DoS with a malicious upload or series of uploads. Note that, like all of the file upload limits, the new configuration option (FileUploadBase#setFileCountMax) is not enabled by default and must be explicitly configured.
https://avd.aquasec.com/nvd/cve-2023-24998
If the vulnerability does not impact the `tier-to-delius` project, you can suppress this alert by adding a comment starting with `Suppress`. For example, "Suppressed because we do not process any untrusted XML content".
|
True
|
CVE-2023-24998 (tier-to-delius) - Apache Commons FileUpload: FileUpload DoS with excessive parts
* Project: tier-to-delius
* Package: `commons-fileupload:commons-fileupload:1.4`
* Location: `app/libs/commons-fileupload-1.4.jar`
>Apache Commons FileUpload before 1.5 does not limit the number of request parts to be processed resulting in the possibility of an attacker triggering a DoS with a malicious upload or series of uploads. Note that, like all of the file upload limits, the new configuration option (FileUploadBase#setFileCountMax) is not enabled by default and must be explicitly configured.
https://avd.aquasec.com/nvd/cve-2023-24998
If the vulnerability does not impact the `tier-to-delius` project, you can suppress this alert by adding a comment starting with `Suppress`. For example, "Suppressed because we do not process any untrusted XML content".
|
secu
|
cve tier to delius apache commons fileupload fileupload dos with excessive parts project tier to delius package commons fileupload commons fileupload location app libs commons fileupload jar apache commons fileupload before does not limit the number of request parts to be processed resulting in the possibility of an attacker triggering a dos with a malicious upload or series of uploads note that like all of the file upload limits the new configuration option fileuploadbase setfilecountmax is not enabled by default and must be explicitly configured if the vulnerability does not impact the tier to delius project you can suppress this alert by adding a comment starting with suppress for example suppressed because we do not process any untrusted xml content
| 1
|
266,077
| 28,298,895,305
|
IssuesEvent
|
2023-04-10 02:52:49
|
nidhi7598/linux-4.19.72
|
https://api.github.com/repos/nidhi7598/linux-4.19.72
|
closed
|
CVE-2020-24394 (High) detected in linuxlinux-4.19.254 - autoclosed
|
Mend: dependency security vulnerability
|
## CVE-2020-24394 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linuxlinux-4.19.254</b></p></summary>
<p>
<p>The Linux Kernel</p>
<p>Library home page: <a href=https://mirrors.edge.kernel.org/pub/linux/kernel/v4.x/?wsslib=linux>https://mirrors.edge.kernel.org/pub/linux/kernel/v4.x/?wsslib=linux</a></p>
<p>Found in HEAD commit: <a href="https://github.com/nidhi7598/linux-4.19.72/commit/10a8c99e4f60044163c159867bc6f5452c1c36e5">10a8c99e4f60044163c159867bc6f5452c1c36e5</a></p>
<p>Found in base branch: <b>master</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (2)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/fs/nfsd/vfs.c</b>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/fs/nfsd/vfs.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
In the Linux kernel before 5.7.8, fs/nfsd/vfs.c (in the NFS server) can set incorrect permissions on new filesystem objects when the filesystem lacks ACL support, aka CID-22cf8419f131. This occurs because the current umask is not considered.
<p>Publish Date: 2020-08-19
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-24394>CVE-2020-24394</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.linuxkernelcves.com/cves/CVE-2020-24394">https://www.linuxkernelcves.com/cves/CVE-2020-24394</a></p>
<p>Release Date: 2020-08-19</p>
<p>Fix Resolution: v5.8-rc4,v4.14.188,v4.19.132,v5.4.51,v5.7.8</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2020-24394 (High) detected in linuxlinux-4.19.254 - autoclosed - ## CVE-2020-24394 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linuxlinux-4.19.254</b></p></summary>
<p>
<p>The Linux Kernel</p>
<p>Library home page: <a href=https://mirrors.edge.kernel.org/pub/linux/kernel/v4.x/?wsslib=linux>https://mirrors.edge.kernel.org/pub/linux/kernel/v4.x/?wsslib=linux</a></p>
<p>Found in HEAD commit: <a href="https://github.com/nidhi7598/linux-4.19.72/commit/10a8c99e4f60044163c159867bc6f5452c1c36e5">10a8c99e4f60044163c159867bc6f5452c1c36e5</a></p>
<p>Found in base branch: <b>master</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (2)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/fs/nfsd/vfs.c</b>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/fs/nfsd/vfs.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
In the Linux kernel before 5.7.8, fs/nfsd/vfs.c (in the NFS server) can set incorrect permissions on new filesystem objects when the filesystem lacks ACL support, aka CID-22cf8419f131. This occurs because the current umask is not considered.
<p>Publish Date: 2020-08-19
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-24394>CVE-2020-24394</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.linuxkernelcves.com/cves/CVE-2020-24394">https://www.linuxkernelcves.com/cves/CVE-2020-24394</a></p>
<p>Release Date: 2020-08-19</p>
<p>Fix Resolution: v5.8-rc4,v4.14.188,v4.19.132,v5.4.51,v5.7.8</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve high detected in linuxlinux autoclosed cve high severity vulnerability vulnerable library linuxlinux the linux kernel library home page a href found in head commit a href found in base branch master vulnerable source files fs nfsd vfs c fs nfsd vfs c vulnerability details in the linux kernel before fs nfsd vfs c in the nfs server can set incorrect permissions on new filesystem objects when the filesystem lacks acl support aka cid this occurs because the current umask is not considered publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required low user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with mend
| 1
|
94,414
| 19,542,991,477
|
IssuesEvent
|
2022-01-01 09:11:19
|
joomla/joomla-cms
|
https://api.github.com/repos/joomla/joomla-cms
|
closed
|
[4.1] Error: 0 in the frontend after installing nightly build + demo data
|
No Code Attached Yet
|
### Steps to reproduce the issue
Used the latest nightly build which is available on 01.01. All I did was install the build, tested the PR https://github.com/joomla/joomla-cms/pull/36515 (i.e. created 1 task) and then installed the demo data (NOT multilingual). Everything, the frontend fell off.

### System information (as much as possible)
Joomla 4.1 Nightly Builds on 01.01
PHP 7.2.34
|
1.0
|
[4.1] Error: 0 in the frontend after installing nightly build + demo data - ### Steps to reproduce the issue
Used the latest nightly build which is available on 01.01. All I did was install the build, tested the PR https://github.com/joomla/joomla-cms/pull/36515 (i.e. created 1 task) and then installed the demo data (NOT multilingual). Everything, the frontend fell off.

### System information (as much as possible)
Joomla 4.1 Nightly Builds on 01.01
PHP 7.2.34
|
non_secu
|
error in the frontend after installing nightly build demo data steps to reproduce the issue used the latest nightly build which is available on all i did was install the build tested the pr i e created task and then installed the demo data not multilingual everything the frontend fell off system information as much as possible joomla nightly builds on php
| 0
|
147,929
| 19,526,167,190
|
IssuesEvent
|
2021-12-30 08:13:59
|
panasalap/linux-4.1.15
|
https://api.github.com/repos/panasalap/linux-4.1.15
|
opened
|
CVE-2015-8812 (High) detected in linuxv4.4.3
|
security vulnerability
|
## CVE-2015-8812 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linuxv4.4.3</b></p></summary>
<p>
<p>Library home page: <a href=https://git.kernel.org/pub/scm/linux/kernel/git/kees/linux.git>https://git.kernel.org/pub/scm/linux/kernel/git/kees/linux.git</a></p>
<p>Found in HEAD commit: <a href="https://github.com/panasalap/linux-4.1.15/commit/9c15ec31637ff4ee4a4c14fb9b3264a31f75aa69">9c15ec31637ff4ee4a4c14fb9b3264a31f75aa69</a></p>
<p>Found in base branch: <b>master</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (2)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/drivers/infiniband/hw/cxgb3/iwch_cm.c</b>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/drivers/infiniband/hw/cxgb3/iwch_cm.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
drivers/infiniband/hw/cxgb3/iwch_cm.c in the Linux kernel before 4.5 does not properly identify error conditions, which allows remote attackers to execute arbitrary code or cause a denial of service (use-after-free) via crafted packets.
<p>Publish Date: 2016-04-27
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2015-8812>CVE-2015-8812</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>9.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2015-8812">https://nvd.nist.gov/vuln/detail/CVE-2015-8812</a></p>
<p>Release Date: 2016-04-27</p>
<p>Fix Resolution: 4.5</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2015-8812 (High) detected in linuxv4.4.3 - ## CVE-2015-8812 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linuxv4.4.3</b></p></summary>
<p>
<p>Library home page: <a href=https://git.kernel.org/pub/scm/linux/kernel/git/kees/linux.git>https://git.kernel.org/pub/scm/linux/kernel/git/kees/linux.git</a></p>
<p>Found in HEAD commit: <a href="https://github.com/panasalap/linux-4.1.15/commit/9c15ec31637ff4ee4a4c14fb9b3264a31f75aa69">9c15ec31637ff4ee4a4c14fb9b3264a31f75aa69</a></p>
<p>Found in base branch: <b>master</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (2)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/drivers/infiniband/hw/cxgb3/iwch_cm.c</b>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/drivers/infiniband/hw/cxgb3/iwch_cm.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
drivers/infiniband/hw/cxgb3/iwch_cm.c in the Linux kernel before 4.5 does not properly identify error conditions, which allows remote attackers to execute arbitrary code or cause a denial of service (use-after-free) via crafted packets.
<p>Publish Date: 2016-04-27
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2015-8812>CVE-2015-8812</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>9.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2015-8812">https://nvd.nist.gov/vuln/detail/CVE-2015-8812</a></p>
<p>Release Date: 2016-04-27</p>
<p>Fix Resolution: 4.5</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve high detected in cve high severity vulnerability vulnerable library library home page a href found in head commit a href found in base branch master vulnerable source files drivers infiniband hw iwch cm c drivers infiniband hw iwch cm c vulnerability details drivers infiniband hw iwch cm c in the linux kernel before does not properly identify error conditions which allows remote attackers to execute arbitrary code or cause a denial of service use after free via crafted packets publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource
| 1
|
268,756
| 20,360,817,344
|
IssuesEvent
|
2022-02-20 17:01:22
|
scikit-image/scikit-image
|
https://api.github.com/repos/scikit-image/scikit-image
|
reopened
|
Clarification: coordinate conventions in watershed example
|
type: documentation
|
I have been frequently referring to [this watershed segmentation example](https://scikit-image.org/docs/stable/auto_examples/segmentation/plot_watershed.html#sphx-glr-auto-examples-segmentation-plot-watershed-py). The second centroid in the docs uses the naming convention `(x2, y2)` to represent the point `(44, 52)`. If you then use `mask[tuple(coords.T)]` to set labels to the centroids on the image, the labelled centroid is present at `row = 44` and `col = 52`, wheras the naming convention suggests that the indexing happen at `row = 52` and `col = 44` instead.
Would it be better to name all coords `(r*, c*)` in the example, or is this the expected behaviour?
|
1.0
|
Clarification: coordinate conventions in watershed example - I have been frequently referring to [this watershed segmentation example](https://scikit-image.org/docs/stable/auto_examples/segmentation/plot_watershed.html#sphx-glr-auto-examples-segmentation-plot-watershed-py). The second centroid in the docs uses the naming convention `(x2, y2)` to represent the point `(44, 52)`. If you then use `mask[tuple(coords.T)]` to set labels to the centroids on the image, the labelled centroid is present at `row = 44` and `col = 52`, wheras the naming convention suggests that the indexing happen at `row = 52` and `col = 44` instead.
Would it be better to name all coords `(r*, c*)` in the example, or is this the expected behaviour?
|
non_secu
|
clarification coordinate conventions in watershed example i have been frequently referring to the second centroid in the docs uses the naming convention to represent the point if you then use mask to set labels to the centroids on the image the labelled centroid is present at row and col wheras the naming convention suggests that the indexing happen at row and col instead would it be better to name all coords r c in the example or is this the expected behaviour
| 0
|
273,716
| 29,831,069,665
|
IssuesEvent
|
2023-06-18 09:26:59
|
RG4421/ampere-centos-kernel
|
https://api.github.com/repos/RG4421/ampere-centos-kernel
|
closed
|
CVE-2019-15921 (Medium) detected in linuxv5.2 - autoclosed
|
Mend: dependency security vulnerability
|
## CVE-2019-15921 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linuxv5.2</b></p></summary>
<p>
<p>Linux kernel source tree</p>
<p>Library home page: <a href=https://github.com/torvalds/linux.git>https://github.com/torvalds/linux.git</a></p>
<p>Found in base branch: <b>amp-centos-8.0-kernel</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (2)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/net/netlink/genetlink.c</b>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/net/netlink/genetlink.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png?' width=19 height=20> Vulnerability Details</summary>
<p>
An issue was discovered in the Linux kernel before 5.0.6. There is a memory leak issue when idr_alloc() fails in genl_register_family() in net/netlink/genetlink.c.
<p>Publish Date: 2019-09-04
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-15921>CVE-2019-15921</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>4.7</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: High
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cdn.kernel.org/pub/linux/kernel/v5.x/ChangeLog-5.0.6">https://cdn.kernel.org/pub/linux/kernel/v5.x/ChangeLog-5.0.6</a></p>
<p>Release Date: 2019-09-04</p>
<p>Fix Resolution: v5.1-rc3</p>
</p>
</details>
<p></p>
|
True
|
CVE-2019-15921 (Medium) detected in linuxv5.2 - autoclosed - ## CVE-2019-15921 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linuxv5.2</b></p></summary>
<p>
<p>Linux kernel source tree</p>
<p>Library home page: <a href=https://github.com/torvalds/linux.git>https://github.com/torvalds/linux.git</a></p>
<p>Found in base branch: <b>amp-centos-8.0-kernel</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (2)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/net/netlink/genetlink.c</b>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/net/netlink/genetlink.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png?' width=19 height=20> Vulnerability Details</summary>
<p>
An issue was discovered in the Linux kernel before 5.0.6. There is a memory leak issue when idr_alloc() fails in genl_register_family() in net/netlink/genetlink.c.
<p>Publish Date: 2019-09-04
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-15921>CVE-2019-15921</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>4.7</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: High
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cdn.kernel.org/pub/linux/kernel/v5.x/ChangeLog-5.0.6">https://cdn.kernel.org/pub/linux/kernel/v5.x/ChangeLog-5.0.6</a></p>
<p>Release Date: 2019-09-04</p>
<p>Fix Resolution: v5.1-rc3</p>
</p>
</details>
<p></p>
|
secu
|
cve medium detected in autoclosed cve medium severity vulnerability vulnerable library linux kernel source tree library home page a href found in base branch amp centos kernel vulnerable source files net netlink genetlink c net netlink genetlink c vulnerability details an issue was discovered in the linux kernel before there is a memory leak issue when idr alloc fails in genl register family in net netlink genetlink c publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity high privileges required low user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution
| 1
|
40,445
| 12,794,037,715
|
IssuesEvent
|
2020-07-02 05:55:15
|
mgh3326/railbook
|
https://api.github.com/repos/mgh3326/railbook
|
opened
|
CVE-2020-7656 (Medium) detected in jquery-1.7.1.min.js
|
security vulnerability
|
## CVE-2020-7656 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jquery-1.7.1.min.js</b></p></summary>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/1.7.1/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/1.7.1/jquery.min.js</a></p>
<p>Path to dependency file: /tmp/ws-scm/railbook/node_modules/sockjs/examples/hapi/html/index.html</p>
<p>Path to vulnerable library: /railbook/node_modules/sockjs/examples/hapi/html/index.html,/railbook/node_modules/sockjs/examples/express-3.x/index.html,/railbook/node_modules/sockjs/examples/multiplex/index.html,/railbook/node_modules/sockjs/examples/echo/index.html,/railbook/node_modules/sockjs/examples/express/index.html</p>
<p>
Dependency Hierarchy:
- :x: **jquery-1.7.1.min.js** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/mgh3326/railbook/commit/63689d4b179b863980f4168df3758dfcc0c37358">63689d4b179b863980f4168df3758dfcc0c37358</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
jquery prior to 1.9.0 allows Cross-site Scripting attacks via the load method. The load method fails to recognize and remove "<script>" HTML tags that contain a whitespace character, i.e: "</script >", which results in the enclosed script logic to be executed.
<p>Publish Date: 2020-05-19
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-7656>CVE-2020-7656</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/rails/jquery-rails/commit/8f601cbfa08749ee5bbd2bffb6e509db9d753568">https://github.com/rails/jquery-rails/commit/8f601cbfa08749ee5bbd2bffb6e509db9d753568</a></p>
<p>Release Date: 2020-05-19</p>
<p>Fix Resolution: jquery-rails - 2.2.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2020-7656 (Medium) detected in jquery-1.7.1.min.js - ## CVE-2020-7656 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jquery-1.7.1.min.js</b></p></summary>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/1.7.1/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/1.7.1/jquery.min.js</a></p>
<p>Path to dependency file: /tmp/ws-scm/railbook/node_modules/sockjs/examples/hapi/html/index.html</p>
<p>Path to vulnerable library: /railbook/node_modules/sockjs/examples/hapi/html/index.html,/railbook/node_modules/sockjs/examples/express-3.x/index.html,/railbook/node_modules/sockjs/examples/multiplex/index.html,/railbook/node_modules/sockjs/examples/echo/index.html,/railbook/node_modules/sockjs/examples/express/index.html</p>
<p>
Dependency Hierarchy:
- :x: **jquery-1.7.1.min.js** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/mgh3326/railbook/commit/63689d4b179b863980f4168df3758dfcc0c37358">63689d4b179b863980f4168df3758dfcc0c37358</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
jquery prior to 1.9.0 allows Cross-site Scripting attacks via the load method. The load method fails to recognize and remove "<script>" HTML tags that contain a whitespace character, i.e: "</script >", which results in the enclosed script logic to be executed.
<p>Publish Date: 2020-05-19
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-7656>CVE-2020-7656</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/rails/jquery-rails/commit/8f601cbfa08749ee5bbd2bffb6e509db9d753568">https://github.com/rails/jquery-rails/commit/8f601cbfa08749ee5bbd2bffb6e509db9d753568</a></p>
<p>Release Date: 2020-05-19</p>
<p>Fix Resolution: jquery-rails - 2.2.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve medium detected in jquery min js cve medium severity vulnerability vulnerable library jquery min js javascript library for dom operations library home page a href path to dependency file tmp ws scm railbook node modules sockjs examples hapi html index html path to vulnerable library railbook node modules sockjs examples hapi html index html railbook node modules sockjs examples express x index html railbook node modules sockjs examples multiplex index html railbook node modules sockjs examples echo index html railbook node modules sockjs examples express index html dependency hierarchy x jquery min js vulnerable library found in head commit a href vulnerability details jquery prior to allows cross site scripting attacks via the load method the load method fails to recognize and remove html tags that contain a whitespace character i e which results in the enclosed script logic to be executed publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope changed impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution jquery rails step up your open source security game with whitesource
| 1
|
427,284
| 12,393,943,400
|
IssuesEvent
|
2020-05-20 16:10:04
|
googleapis/elixir-google-api
|
https://api.github.com/repos/googleapis/elixir-google-api
|
closed
|
Synthesis failed for Jobs
|
api: jobs autosynth failure priority: p1 type: bug
|
Hello! Autosynth couldn't regenerate Jobs. :broken_heart:
Here's the output from running `synth.py`:
```
ning: failed to remove deps/parse_trans/ebin/parse_trans.app: Permission denied
warning: failed to remove deps/parse_trans/ebin/parse_trans_mod.beam: Permission denied
warning: failed to remove deps/parse_trans/ebin/parse_trans_codegen.beam: Permission denied
warning: failed to remove deps/parse_trans/ebin/ct_expand.beam: Permission denied
warning: failed to remove deps/parse_trans/ebin/parse_trans.beam: Permission denied
warning: failed to remove deps/parse_trans/ebin/exprecs.beam: Permission denied
warning: failed to remove deps/parse_trans/ebin/parse_trans_pp.beam: Permission denied
warning: failed to remove deps/parse_trans/.rebar3/erlcinfo: Permission denied
warning: failed to remove deps/parse_trans/hex_metadata.config: Permission denied
warning: failed to remove deps/parse_trans/README.md: Permission denied
warning: failed to remove deps/parse_trans/rebar.config: Permission denied
warning: failed to remove deps/parse_trans/include/codegen.hrl: Permission denied
warning: failed to remove deps/parse_trans/include/exprecs.hrl: Permission denied
warning: failed to remove deps/parse_trans/.fetch: Permission denied
warning: failed to remove deps/parse_trans/.hex: Permission denied
warning: failed to remove deps/idna/LICENSE: Permission denied
warning: failed to remove deps/idna/rebar.lock: Permission denied
warning: failed to remove deps/idna/src/idna.erl: Permission denied
warning: failed to remove deps/idna/src/idna_logger.hrl: Permission denied
warning: failed to remove deps/idna/src/idna_ucs.erl: Permission denied
warning: failed to remove deps/idna/src/punycode.erl: Permission denied
warning: failed to remove deps/idna/src/idna_table.erl: Permission denied
warning: failed to remove deps/idna/src/idna_context.erl: Permission denied
warning: failed to remove deps/idna/src/idna.app.src: Permission denied
warning: failed to remove deps/idna/src/idna_mapping.erl: Permission denied
warning: failed to remove deps/idna/src/idna_data.erl: Permission denied
warning: failed to remove deps/idna/src/idna_bidi.erl: Permission denied
warning: failed to remove deps/idna/ebin/idna_mapping.beam: Permission denied
warning: failed to remove deps/idna/ebin/idna_context.beam: Permission denied
warning: failed to remove deps/idna/ebin/idna_bidi.beam: Permission denied
warning: failed to remove deps/idna/ebin/punycode.beam: Permission denied
warning: failed to remove deps/idna/ebin/idna_table.beam: Permission denied
warning: failed to remove deps/idna/ebin/idna_data.beam: Permission denied
warning: failed to remove deps/idna/ebin/idna_ucs.beam: Permission denied
warning: failed to remove deps/idna/ebin/idna.app: Permission denied
warning: failed to remove deps/idna/ebin/idna.beam: Permission denied
warning: failed to remove deps/idna/.rebar3/erlcinfo: Permission denied
warning: failed to remove deps/idna/hex_metadata.config: Permission denied
warning: failed to remove deps/idna/README.md: Permission denied
warning: failed to remove deps/idna/rebar.config: Permission denied
warning: failed to remove deps/idna/.fetch: Permission denied
warning: failed to remove deps/idna/rebar.config.script: Permission denied
warning: failed to remove deps/idna/.hex: Permission denied
warning: failed to remove deps/hackney/MAINTAINERS: Permission denied
warning: failed to remove deps/hackney/LICENSE: Permission denied
warning: failed to remove deps/hackney/rebar.lock: Permission denied
warning: failed to remove deps/hackney/src/hackney_ssl.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_response.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_tcp.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_http.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_cookie.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_url.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_headers.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney.app.src: Permission denied
warning: failed to remove deps/hackney/src/hackney_pool_handler.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_trace.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_multipart.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_headers_new.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_http_connect.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_util.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_socks5.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_request.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_app.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_internal.hrl: Permission denied
warning: failed to remove deps/hackney/src/hackney_date.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_manager.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_connect.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_bstr.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_sup.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_local_tcp.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_stream.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_pool.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_metrics.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_methods.hrl: Permission denied
warning: failed to remove deps/hackney/NOTICE: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_pool.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_trace.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_pool_handler.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_headers.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_url.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_manager.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_metrics.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_stream.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_sup.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_multipart.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_http.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_socks5.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_app.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_http_connect.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_response.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney.app: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_headers_new.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_cookie.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_request.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_util.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_connect.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_date.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_ssl.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_bstr.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_tcp.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_local_tcp.beam: Permission denied
warning: failed to remove deps/hackney/.rebar3/erlcinfo: Permission denied
warning: failed to remove deps/hackney/hex_metadata.config: Permission denied
warning: failed to remove deps/hackney/README.md: Permission denied
warning: failed to remove deps/hackney/rebar.config: Permission denied
warning: failed to remove deps/hackney/include/hackney.hrl: Permission denied
warning: failed to remove deps/hackney/include/hackney_lib.hrl: Permission denied
warning: failed to remove deps/hackney/.fetch: Permission denied
warning: failed to remove deps/hackney/.hex: Permission denied
warning: failed to remove deps/hackney/NEWS.md: Permission denied
Removing __pycache__/
Removing specifications/gdd/Jobs-v3.json
Traceback (most recent call last):
File "/tmpfs/src/github/synthtool/autosynth/synth.py", line 559, in _inner_main
sys.exit(EXIT_CODE_SKIPPED)
SystemExit: 28
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "/home/kbuilder/.pyenv/versions/3.6.9/lib/python3.6/runpy.py", line 193, in _run_module_as_main
"__main__", mod_spec)
File "/home/kbuilder/.pyenv/versions/3.6.9/lib/python3.6/runpy.py", line 85, in _run_code
exec(code, run_globals)
File "/tmpfs/src/github/synthtool/autosynth/synth.py", line 615, in <module>
main()
File "/tmpfs/src/github/synthtool/autosynth/synth.py", line 476, in main
return _inner_main(temp_dir)
File "/tmpfs/src/github/synthtool/autosynth/synth.py", line 611, in _inner_main
executor.check_call(["git", "clean", "-fdx"], cwd=working_repo_path)
File "/tmpfs/src/github/synthtool/autosynth/executor.py", line 29, in check_call
subprocess.check_call(command, **args)
File "/home/kbuilder/.pyenv/versions/3.6.9/lib/python3.6/subprocess.py", line 311, in check_call
raise CalledProcessError(retcode, cmd)
subprocess.CalledProcessError: Command '['git', 'clean', '-fdx']' returned non-zero exit status 1.
```
Google internal developers can see the full log [here](http://sponge/c19bc74d-4d42-4305-94c3-323bf90f3ebc).
|
1.0
|
Synthesis failed for Jobs - Hello! Autosynth couldn't regenerate Jobs. :broken_heart:
Here's the output from running `synth.py`:
```
ning: failed to remove deps/parse_trans/ebin/parse_trans.app: Permission denied
warning: failed to remove deps/parse_trans/ebin/parse_trans_mod.beam: Permission denied
warning: failed to remove deps/parse_trans/ebin/parse_trans_codegen.beam: Permission denied
warning: failed to remove deps/parse_trans/ebin/ct_expand.beam: Permission denied
warning: failed to remove deps/parse_trans/ebin/parse_trans.beam: Permission denied
warning: failed to remove deps/parse_trans/ebin/exprecs.beam: Permission denied
warning: failed to remove deps/parse_trans/ebin/parse_trans_pp.beam: Permission denied
warning: failed to remove deps/parse_trans/.rebar3/erlcinfo: Permission denied
warning: failed to remove deps/parse_trans/hex_metadata.config: Permission denied
warning: failed to remove deps/parse_trans/README.md: Permission denied
warning: failed to remove deps/parse_trans/rebar.config: Permission denied
warning: failed to remove deps/parse_trans/include/codegen.hrl: Permission denied
warning: failed to remove deps/parse_trans/include/exprecs.hrl: Permission denied
warning: failed to remove deps/parse_trans/.fetch: Permission denied
warning: failed to remove deps/parse_trans/.hex: Permission denied
warning: failed to remove deps/idna/LICENSE: Permission denied
warning: failed to remove deps/idna/rebar.lock: Permission denied
warning: failed to remove deps/idna/src/idna.erl: Permission denied
warning: failed to remove deps/idna/src/idna_logger.hrl: Permission denied
warning: failed to remove deps/idna/src/idna_ucs.erl: Permission denied
warning: failed to remove deps/idna/src/punycode.erl: Permission denied
warning: failed to remove deps/idna/src/idna_table.erl: Permission denied
warning: failed to remove deps/idna/src/idna_context.erl: Permission denied
warning: failed to remove deps/idna/src/idna.app.src: Permission denied
warning: failed to remove deps/idna/src/idna_mapping.erl: Permission denied
warning: failed to remove deps/idna/src/idna_data.erl: Permission denied
warning: failed to remove deps/idna/src/idna_bidi.erl: Permission denied
warning: failed to remove deps/idna/ebin/idna_mapping.beam: Permission denied
warning: failed to remove deps/idna/ebin/idna_context.beam: Permission denied
warning: failed to remove deps/idna/ebin/idna_bidi.beam: Permission denied
warning: failed to remove deps/idna/ebin/punycode.beam: Permission denied
warning: failed to remove deps/idna/ebin/idna_table.beam: Permission denied
warning: failed to remove deps/idna/ebin/idna_data.beam: Permission denied
warning: failed to remove deps/idna/ebin/idna_ucs.beam: Permission denied
warning: failed to remove deps/idna/ebin/idna.app: Permission denied
warning: failed to remove deps/idna/ebin/idna.beam: Permission denied
warning: failed to remove deps/idna/.rebar3/erlcinfo: Permission denied
warning: failed to remove deps/idna/hex_metadata.config: Permission denied
warning: failed to remove deps/idna/README.md: Permission denied
warning: failed to remove deps/idna/rebar.config: Permission denied
warning: failed to remove deps/idna/.fetch: Permission denied
warning: failed to remove deps/idna/rebar.config.script: Permission denied
warning: failed to remove deps/idna/.hex: Permission denied
warning: failed to remove deps/hackney/MAINTAINERS: Permission denied
warning: failed to remove deps/hackney/LICENSE: Permission denied
warning: failed to remove deps/hackney/rebar.lock: Permission denied
warning: failed to remove deps/hackney/src/hackney_ssl.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_response.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_tcp.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_http.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_cookie.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_url.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_headers.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney.app.src: Permission denied
warning: failed to remove deps/hackney/src/hackney_pool_handler.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_trace.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_multipart.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_headers_new.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_http_connect.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_util.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_socks5.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_request.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_app.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_internal.hrl: Permission denied
warning: failed to remove deps/hackney/src/hackney_date.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_manager.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_connect.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_bstr.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_sup.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_local_tcp.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_stream.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_pool.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_metrics.erl: Permission denied
warning: failed to remove deps/hackney/src/hackney_methods.hrl: Permission denied
warning: failed to remove deps/hackney/NOTICE: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_pool.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_trace.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_pool_handler.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_headers.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_url.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_manager.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_metrics.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_stream.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_sup.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_multipart.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_http.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_socks5.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_app.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_http_connect.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_response.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney.app: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_headers_new.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_cookie.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_request.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_util.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_connect.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_date.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_ssl.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_bstr.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_tcp.beam: Permission denied
warning: failed to remove deps/hackney/ebin/hackney_local_tcp.beam: Permission denied
warning: failed to remove deps/hackney/.rebar3/erlcinfo: Permission denied
warning: failed to remove deps/hackney/hex_metadata.config: Permission denied
warning: failed to remove deps/hackney/README.md: Permission denied
warning: failed to remove deps/hackney/rebar.config: Permission denied
warning: failed to remove deps/hackney/include/hackney.hrl: Permission denied
warning: failed to remove deps/hackney/include/hackney_lib.hrl: Permission denied
warning: failed to remove deps/hackney/.fetch: Permission denied
warning: failed to remove deps/hackney/.hex: Permission denied
warning: failed to remove deps/hackney/NEWS.md: Permission denied
Removing __pycache__/
Removing specifications/gdd/Jobs-v3.json
Traceback (most recent call last):
File "/tmpfs/src/github/synthtool/autosynth/synth.py", line 559, in _inner_main
sys.exit(EXIT_CODE_SKIPPED)
SystemExit: 28
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "/home/kbuilder/.pyenv/versions/3.6.9/lib/python3.6/runpy.py", line 193, in _run_module_as_main
"__main__", mod_spec)
File "/home/kbuilder/.pyenv/versions/3.6.9/lib/python3.6/runpy.py", line 85, in _run_code
exec(code, run_globals)
File "/tmpfs/src/github/synthtool/autosynth/synth.py", line 615, in <module>
main()
File "/tmpfs/src/github/synthtool/autosynth/synth.py", line 476, in main
return _inner_main(temp_dir)
File "/tmpfs/src/github/synthtool/autosynth/synth.py", line 611, in _inner_main
executor.check_call(["git", "clean", "-fdx"], cwd=working_repo_path)
File "/tmpfs/src/github/synthtool/autosynth/executor.py", line 29, in check_call
subprocess.check_call(command, **args)
File "/home/kbuilder/.pyenv/versions/3.6.9/lib/python3.6/subprocess.py", line 311, in check_call
raise CalledProcessError(retcode, cmd)
subprocess.CalledProcessError: Command '['git', 'clean', '-fdx']' returned non-zero exit status 1.
```
Google internal developers can see the full log [here](http://sponge/c19bc74d-4d42-4305-94c3-323bf90f3ebc).
|
non_secu
|
synthesis failed for jobs hello autosynth couldn t regenerate jobs broken heart here s the output from running synth py ning failed to remove deps parse trans ebin parse trans app permission denied warning failed to remove deps parse trans ebin parse trans mod beam permission denied warning failed to remove deps parse trans ebin parse trans codegen beam permission denied warning failed to remove deps parse trans ebin ct expand beam permission denied warning failed to remove deps parse trans ebin parse trans beam permission denied warning failed to remove deps parse trans ebin exprecs beam permission denied warning failed to remove deps parse trans ebin parse trans pp beam permission denied warning failed to remove deps parse trans erlcinfo permission denied warning failed to remove deps parse trans hex metadata config permission denied warning failed to remove deps parse trans readme md permission denied warning failed to remove deps parse trans rebar config permission denied warning failed to remove deps parse trans include codegen hrl permission denied warning failed to remove deps parse trans include exprecs hrl permission denied warning failed to remove deps parse trans fetch permission denied warning failed to remove deps parse trans hex permission denied warning failed to remove deps idna license permission denied warning failed to remove deps idna rebar lock permission denied warning failed to remove deps idna src idna erl permission denied warning failed to remove deps idna src idna logger hrl permission denied warning failed to remove deps idna src idna ucs erl permission denied warning failed to remove deps idna src punycode erl permission denied warning failed to remove deps idna src idna table erl permission denied warning failed to remove deps idna src idna context erl permission denied warning failed to remove deps idna src idna app src permission denied warning failed to remove deps idna src idna mapping erl permission denied warning failed to remove deps idna src idna data erl permission denied warning failed to remove deps idna src idna bidi erl permission denied warning failed to remove deps idna ebin idna mapping beam permission denied warning failed to remove deps idna ebin idna context beam permission denied warning failed to remove deps idna ebin idna bidi beam permission denied warning failed to remove deps idna ebin punycode beam permission denied warning failed to remove deps idna ebin idna table beam permission denied warning failed to remove deps idna ebin idna data beam permission denied warning failed to remove deps idna ebin idna ucs beam permission denied warning failed to remove deps idna ebin idna app permission denied warning failed to remove deps idna ebin idna beam permission denied warning failed to remove deps idna erlcinfo permission denied warning failed to remove deps idna hex metadata config permission denied warning failed to remove deps idna readme md permission denied warning failed to remove deps idna rebar config permission denied warning failed to remove deps idna fetch permission denied warning failed to remove deps idna rebar config script permission denied warning failed to remove deps idna hex permission denied warning failed to remove deps hackney maintainers permission denied warning failed to remove deps hackney license permission denied warning failed to remove deps hackney rebar lock permission denied warning failed to remove deps hackney src hackney ssl erl permission denied warning failed to remove deps hackney src hackney response erl permission denied warning failed to remove deps hackney src hackney tcp erl permission denied warning failed to remove deps hackney src hackney http erl permission denied warning failed to remove deps hackney src hackney cookie erl permission denied warning failed to remove deps hackney src hackney url erl permission denied warning failed to remove deps hackney src hackney headers erl permission denied warning failed to remove deps hackney src hackney app src permission denied warning failed to remove deps hackney src hackney pool handler erl permission denied warning failed to remove deps hackney src hackney trace erl permission denied warning failed to remove deps hackney src hackney multipart erl permission denied warning failed to remove deps hackney src hackney headers new erl permission denied warning failed to remove deps hackney src hackney http connect erl permission denied warning failed to remove deps hackney src hackney util erl permission denied warning failed to remove deps hackney src hackney erl permission denied warning failed to remove deps hackney src hackney request erl permission denied warning failed to remove deps hackney src hackney app erl permission denied warning failed to remove deps hackney src hackney internal hrl permission denied warning failed to remove deps hackney src hackney date erl permission denied warning failed to remove deps hackney src hackney manager erl permission denied warning failed to remove deps hackney src hackney connect erl permission denied warning failed to remove deps hackney src hackney bstr erl permission denied warning failed to remove deps hackney src hackney sup erl permission denied warning failed to remove deps hackney src hackney erl permission denied warning failed to remove deps hackney src hackney local tcp erl permission denied warning failed to remove deps hackney src hackney stream erl permission denied warning failed to remove deps hackney src hackney pool erl permission denied warning failed to remove deps hackney src hackney metrics erl permission denied warning failed to remove deps hackney src hackney methods hrl permission denied warning failed to remove deps hackney notice permission denied warning failed to remove deps hackney ebin hackney pool beam permission denied warning failed to remove deps hackney ebin hackney trace beam permission denied warning failed to remove deps hackney ebin hackney pool handler beam permission denied warning failed to remove deps hackney ebin hackney beam permission denied warning failed to remove deps hackney ebin hackney headers beam permission denied warning failed to remove deps hackney ebin hackney url beam permission denied warning failed to remove deps hackney ebin hackney manager beam permission denied warning failed to remove deps hackney ebin hackney metrics beam permission denied warning failed to remove deps hackney ebin hackney stream beam permission denied warning failed to remove deps hackney ebin hackney sup beam permission denied warning failed to remove deps hackney ebin hackney multipart beam permission denied warning failed to remove deps hackney ebin hackney http beam permission denied warning failed to remove deps hackney ebin hackney beam permission denied warning failed to remove deps hackney ebin hackney app beam permission denied warning failed to remove deps hackney ebin hackney http connect beam permission denied warning failed to remove deps hackney ebin hackney response beam permission denied warning failed to remove deps hackney ebin hackney app permission denied warning failed to remove deps hackney ebin hackney headers new beam permission denied warning failed to remove deps hackney ebin hackney cookie beam permission denied warning failed to remove deps hackney ebin hackney request beam permission denied warning failed to remove deps hackney ebin hackney util beam permission denied warning failed to remove deps hackney ebin hackney connect beam permission denied warning failed to remove deps hackney ebin hackney date beam permission denied warning failed to remove deps hackney ebin hackney ssl beam permission denied warning failed to remove deps hackney ebin hackney bstr beam permission denied warning failed to remove deps hackney ebin hackney tcp beam permission denied warning failed to remove deps hackney ebin hackney local tcp beam permission denied warning failed to remove deps hackney erlcinfo permission denied warning failed to remove deps hackney hex metadata config permission denied warning failed to remove deps hackney readme md permission denied warning failed to remove deps hackney rebar config permission denied warning failed to remove deps hackney include hackney hrl permission denied warning failed to remove deps hackney include hackney lib hrl permission denied warning failed to remove deps hackney fetch permission denied warning failed to remove deps hackney hex permission denied warning failed to remove deps hackney news md permission denied removing pycache removing specifications gdd jobs json traceback most recent call last file tmpfs src github synthtool autosynth synth py line in inner main sys exit exit code skipped systemexit during handling of the above exception another exception occurred traceback most recent call last file home kbuilder pyenv versions lib runpy py line in run module as main main mod spec file home kbuilder pyenv versions lib runpy py line in run code exec code run globals file tmpfs src github synthtool autosynth synth py line in main file tmpfs src github synthtool autosynth synth py line in main return inner main temp dir file tmpfs src github synthtool autosynth synth py line in inner main executor check call cwd working repo path file tmpfs src github synthtool autosynth executor py line in check call subprocess check call command args file home kbuilder pyenv versions lib subprocess py line in check call raise calledprocesserror retcode cmd subprocess calledprocesserror command returned non zero exit status google internal developers can see the full log
| 0
|
687,026
| 23,511,516,256
|
IssuesEvent
|
2022-08-18 17:00:40
|
asosnovsky/Shortumation
|
https://api.github.com/repos/asosnovsky/Shortumation
|
closed
|
Internal Server Error
|
bug high priority
|
**Describe the bug**
Internal server error when opening web UI.
It might be something in my config file but I am unsure where to look. I have split up my config and automations into separate folders/files.
**To Reproduce**
Steps to reproduce the behavior:
1. Go to 'Web UI'
2. Click on 'Web UI'
3. ???
4. Look at Error message
**Expected behavior**
See UI
**Screenshots**
<img width="324" alt="image" src="https://user-images.githubusercontent.com/45756272/183263687-3b7520e6-c7d4-44ef-9777-1540067bbf4f.png">
**Desktop (please complete the following information):**
- OS: Windows 11
- Browser: Chrome
- Version 104.0.5112.80 (Official Build) (64-bit)
**Additional context**
```bash
File "/usr/local/lib/python3.9/site-packages/fastapi/applications.py", line 269, in __call__
await super().__call__(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/applications.py", line 124, in __call__
await self.middleware_stack(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/middleware/errors.py", line 184, in __call__
raise exc
File "/usr/local/lib/python3.9/site-packages/starlette/middleware/errors.py", line 162, in __call__
await self.app(scope, receive, _send)
File "/usr/local/lib/python3.9/site-packages/starlette/middleware/cors.py", line 92, in __call__
await self.simple_response(scope, receive, send, request_headers=headers)
File "/usr/local/lib/python3.9/site-packages/starlette/middleware/cors.py", line 147, in simple_response
await self.app(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/exceptions.py", line 93, in __call__
raise exc
File "/usr/local/lib/python3.9/site-packages/starlette/exceptions.py", line 82, in __call__
await self.app(scope, receive, sender)
File "/usr/local/lib/python3.9/site-packages/fastapi/middleware/asyncexitstack.py", line 21, in __call__
raise e
File "/usr/local/lib/python3.9/site-packages/fastapi/middleware/asyncexitstack.py", line 18, in __call__
await self.app(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/routing.py", line 670, in __call__
await route.handle(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/routing.py", line 266, in handle
await self.app(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/routing.py", line 65, in app
response = await func(request)
File "/usr/local/lib/python3.9/site-packages/fastapi/routing.py", line 227, in app
raw_response = await run_endpoint_function(
File "/usr/local/lib/python3.9/site-packages/fastapi/routing.py", line 162, in run_endpoint_function
return await run_in_threadpool(dependant.call, **values)
File "/usr/local/lib/python3.9/site-packages/starlette/concurrency.py", line 41, in run_in_threadpool
return await anyio.to_thread.run_sync(func, *args)
File "/usr/local/lib/python3.9/site-packages/anyio/to_thread.py", line 31, in run_sync
return await get_asynclib().run_sync_in_worker_thread(
File "/usr/local/lib/python3.9/site-packages/anyio/_backends/_asyncio.py", line 937, in run_sync_in_worker_thread
return await future
File "/usr/local/lib/python3.9/site-packages/anyio/_backends/_asyncio.py", line 867, in run
result = context.run(func, *args)
File "/app/src/api/routes/automations.py", line 20, in list_autos
return ListData(
File "pydantic/main.py", line 339, in pydantic.main.BaseModel.__init__
File "pydantic/main.py", line 1038, in pydantic.main.validate_model
File "pydantic/fields.py", line 868, in pydantic.fields.ModelField.validate
File "pydantic/fields.py", line 899, in pydantic.fields.ModelField._validate_sequence_like
File "/app/src/automations/manager.py", line 25, in find
yield from load_automation(auto, tags.get(auto.get("id", ""), {}))
AttributeError: 'str' object has no attribute 'get'
ERROR:hypercorn.error:Error in ASGI Framework
Traceback (most recent call last):
File "/usr/local/lib/python3.9/site-packages/hypercorn/asyncio/task_group.py", line 21, in _handle
await invoke_asgi(app, scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/hypercorn/utils.py", line 247, in invoke_asgi
await app(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/fastapi/applications.py", line 269, in __call__
await super().__call__(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/applications.py", line 124, in __call__
await self.middleware_stack(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/middleware/errors.py", line 184, in __call__
raise exc
File "/usr/local/lib/python3.9/site-packages/starlette/middleware/errors.py", line 162, in __call__
await self.app(scope, receive, _send)
File "/usr/local/lib/python3.9/site-packages/starlette/middleware/cors.py", line 92, in __call__
await self.simple_response(scope, receive, send, request_headers=headers)
File "/usr/local/lib/python3.9/site-packages/starlette/middleware/cors.py", line 147, in simple_response
await self.app(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/exceptions.py", line 93, in __call__
raise exc
File "/usr/local/lib/python3.9/site-packages/starlette/exceptions.py", line 82, in __call__
await self.app(scope, receive, sender)
File "/usr/local/lib/python3.9/site-packages/fastapi/middleware/asyncexitstack.py", line 21, in __call__
raise e
File "/usr/local/lib/python3.9/site-packages/fastapi/middleware/asyncexitstack.py", line 18, in __call__
await self.app(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/routing.py", line 670, in __call__
await route.handle(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/routing.py", line 266, in handle
await self.app(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/routing.py", line 65, in app
response = await func(request)
File "/usr/local/lib/python3.9/site-packages/fastapi/routing.py", line 227, in app
raw_response = await run_endpoint_function(
File "/usr/local/lib/python3.9/site-packages/fastapi/routing.py", line 162, in run_endpoint_function
return await run_in_threadpool(dependant.call, **values)
File "/usr/local/lib/python3.9/site-packages/starlette/concurrency.py", line 41, in run_in_threadpool
return await anyio.to_thread.run_sync(func, *args)
File "/usr/local/lib/python3.9/site-packages/anyio/to_thread.py", line 31, in run_sync
return await get_asynclib().run_sync_in_worker_thread(
File "/usr/local/lib/python3.9/site-packages/anyio/_backends/_asyncio.py", line 937, in run_sync_in_worker_thread
return await future
File "/usr/local/lib/python3.9/site-packages/anyio/_backends/_asyncio.py", line 867, in run
result = context.run(func, *args)
File "/app/src/api/routes/automations.py", line 20, in list_autos
return ListData(
File "pydantic/main.py", line 339, in pydantic.main.BaseModel.__init__
File "pydantic/main.py", line 1038, in pydantic.main.validate_model
File "pydantic/fields.py", line 868, in pydantic.fields.ModelField.validate
File "pydantic/fields.py", line 899, in pydantic.fields.ModelField._validate_sequence_like
File "/app/src/automations/manager.py", line 25, in find
yield from load_automation(auto, tags.get(auto.get("id", ""), {}))
AttributeError: 'str' object has no attribute 'get'
```
|
1.0
|
Internal Server Error - **Describe the bug**
Internal server error when opening web UI.
It might be something in my config file but I am unsure where to look. I have split up my config and automations into separate folders/files.
**To Reproduce**
Steps to reproduce the behavior:
1. Go to 'Web UI'
2. Click on 'Web UI'
3. ???
4. Look at Error message
**Expected behavior**
See UI
**Screenshots**
<img width="324" alt="image" src="https://user-images.githubusercontent.com/45756272/183263687-3b7520e6-c7d4-44ef-9777-1540067bbf4f.png">
**Desktop (please complete the following information):**
- OS: Windows 11
- Browser: Chrome
- Version 104.0.5112.80 (Official Build) (64-bit)
**Additional context**
```bash
File "/usr/local/lib/python3.9/site-packages/fastapi/applications.py", line 269, in __call__
await super().__call__(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/applications.py", line 124, in __call__
await self.middleware_stack(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/middleware/errors.py", line 184, in __call__
raise exc
File "/usr/local/lib/python3.9/site-packages/starlette/middleware/errors.py", line 162, in __call__
await self.app(scope, receive, _send)
File "/usr/local/lib/python3.9/site-packages/starlette/middleware/cors.py", line 92, in __call__
await self.simple_response(scope, receive, send, request_headers=headers)
File "/usr/local/lib/python3.9/site-packages/starlette/middleware/cors.py", line 147, in simple_response
await self.app(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/exceptions.py", line 93, in __call__
raise exc
File "/usr/local/lib/python3.9/site-packages/starlette/exceptions.py", line 82, in __call__
await self.app(scope, receive, sender)
File "/usr/local/lib/python3.9/site-packages/fastapi/middleware/asyncexitstack.py", line 21, in __call__
raise e
File "/usr/local/lib/python3.9/site-packages/fastapi/middleware/asyncexitstack.py", line 18, in __call__
await self.app(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/routing.py", line 670, in __call__
await route.handle(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/routing.py", line 266, in handle
await self.app(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/routing.py", line 65, in app
response = await func(request)
File "/usr/local/lib/python3.9/site-packages/fastapi/routing.py", line 227, in app
raw_response = await run_endpoint_function(
File "/usr/local/lib/python3.9/site-packages/fastapi/routing.py", line 162, in run_endpoint_function
return await run_in_threadpool(dependant.call, **values)
File "/usr/local/lib/python3.9/site-packages/starlette/concurrency.py", line 41, in run_in_threadpool
return await anyio.to_thread.run_sync(func, *args)
File "/usr/local/lib/python3.9/site-packages/anyio/to_thread.py", line 31, in run_sync
return await get_asynclib().run_sync_in_worker_thread(
File "/usr/local/lib/python3.9/site-packages/anyio/_backends/_asyncio.py", line 937, in run_sync_in_worker_thread
return await future
File "/usr/local/lib/python3.9/site-packages/anyio/_backends/_asyncio.py", line 867, in run
result = context.run(func, *args)
File "/app/src/api/routes/automations.py", line 20, in list_autos
return ListData(
File "pydantic/main.py", line 339, in pydantic.main.BaseModel.__init__
File "pydantic/main.py", line 1038, in pydantic.main.validate_model
File "pydantic/fields.py", line 868, in pydantic.fields.ModelField.validate
File "pydantic/fields.py", line 899, in pydantic.fields.ModelField._validate_sequence_like
File "/app/src/automations/manager.py", line 25, in find
yield from load_automation(auto, tags.get(auto.get("id", ""), {}))
AttributeError: 'str' object has no attribute 'get'
ERROR:hypercorn.error:Error in ASGI Framework
Traceback (most recent call last):
File "/usr/local/lib/python3.9/site-packages/hypercorn/asyncio/task_group.py", line 21, in _handle
await invoke_asgi(app, scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/hypercorn/utils.py", line 247, in invoke_asgi
await app(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/fastapi/applications.py", line 269, in __call__
await super().__call__(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/applications.py", line 124, in __call__
await self.middleware_stack(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/middleware/errors.py", line 184, in __call__
raise exc
File "/usr/local/lib/python3.9/site-packages/starlette/middleware/errors.py", line 162, in __call__
await self.app(scope, receive, _send)
File "/usr/local/lib/python3.9/site-packages/starlette/middleware/cors.py", line 92, in __call__
await self.simple_response(scope, receive, send, request_headers=headers)
File "/usr/local/lib/python3.9/site-packages/starlette/middleware/cors.py", line 147, in simple_response
await self.app(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/exceptions.py", line 93, in __call__
raise exc
File "/usr/local/lib/python3.9/site-packages/starlette/exceptions.py", line 82, in __call__
await self.app(scope, receive, sender)
File "/usr/local/lib/python3.9/site-packages/fastapi/middleware/asyncexitstack.py", line 21, in __call__
raise e
File "/usr/local/lib/python3.9/site-packages/fastapi/middleware/asyncexitstack.py", line 18, in __call__
await self.app(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/routing.py", line 670, in __call__
await route.handle(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/routing.py", line 266, in handle
await self.app(scope, receive, send)
File "/usr/local/lib/python3.9/site-packages/starlette/routing.py", line 65, in app
response = await func(request)
File "/usr/local/lib/python3.9/site-packages/fastapi/routing.py", line 227, in app
raw_response = await run_endpoint_function(
File "/usr/local/lib/python3.9/site-packages/fastapi/routing.py", line 162, in run_endpoint_function
return await run_in_threadpool(dependant.call, **values)
File "/usr/local/lib/python3.9/site-packages/starlette/concurrency.py", line 41, in run_in_threadpool
return await anyio.to_thread.run_sync(func, *args)
File "/usr/local/lib/python3.9/site-packages/anyio/to_thread.py", line 31, in run_sync
return await get_asynclib().run_sync_in_worker_thread(
File "/usr/local/lib/python3.9/site-packages/anyio/_backends/_asyncio.py", line 937, in run_sync_in_worker_thread
return await future
File "/usr/local/lib/python3.9/site-packages/anyio/_backends/_asyncio.py", line 867, in run
result = context.run(func, *args)
File "/app/src/api/routes/automations.py", line 20, in list_autos
return ListData(
File "pydantic/main.py", line 339, in pydantic.main.BaseModel.__init__
File "pydantic/main.py", line 1038, in pydantic.main.validate_model
File "pydantic/fields.py", line 868, in pydantic.fields.ModelField.validate
File "pydantic/fields.py", line 899, in pydantic.fields.ModelField._validate_sequence_like
File "/app/src/automations/manager.py", line 25, in find
yield from load_automation(auto, tags.get(auto.get("id", ""), {}))
AttributeError: 'str' object has no attribute 'get'
```
|
non_secu
|
internal server error describe the bug internal server error when opening web ui it might be something in my config file but i am unsure where to look i have split up my config and automations into separate folders files to reproduce steps to reproduce the behavior go to web ui click on web ui look at error message expected behavior see ui screenshots img width alt image src desktop please complete the following information os windows browser chrome version official build bit additional context bash file usr local lib site packages fastapi applications py line in call await super call scope receive send file usr local lib site packages starlette applications py line in call await self middleware stack scope receive send file usr local lib site packages starlette middleware errors py line in call raise exc file usr local lib site packages starlette middleware errors py line in call await self app scope receive send file usr local lib site packages starlette middleware cors py line in call await self simple response scope receive send request headers headers file usr local lib site packages starlette middleware cors py line in simple response await self app scope receive send file usr local lib site packages starlette exceptions py line in call raise exc file usr local lib site packages starlette exceptions py line in call await self app scope receive sender file usr local lib site packages fastapi middleware asyncexitstack py line in call raise e file usr local lib site packages fastapi middleware asyncexitstack py line in call await self app scope receive send file usr local lib site packages starlette routing py line in call await route handle scope receive send file usr local lib site packages starlette routing py line in handle await self app scope receive send file usr local lib site packages starlette routing py line in app response await func request file usr local lib site packages fastapi routing py line in app raw response await run endpoint function file usr local lib site packages fastapi routing py line in run endpoint function return await run in threadpool dependant call values file usr local lib site packages starlette concurrency py line in run in threadpool return await anyio to thread run sync func args file usr local lib site packages anyio to thread py line in run sync return await get asynclib run sync in worker thread file usr local lib site packages anyio backends asyncio py line in run sync in worker thread return await future file usr local lib site packages anyio backends asyncio py line in run result context run func args file app src api routes automations py line in list autos return listdata file pydantic main py line in pydantic main basemodel init file pydantic main py line in pydantic main validate model file pydantic fields py line in pydantic fields modelfield validate file pydantic fields py line in pydantic fields modelfield validate sequence like file app src automations manager py line in find yield from load automation auto tags get auto get id attributeerror str object has no attribute get error hypercorn error error in asgi framework traceback most recent call last file usr local lib site packages hypercorn asyncio task group py line in handle await invoke asgi app scope receive send file usr local lib site packages hypercorn utils py line in invoke asgi await app scope receive send file usr local lib site packages fastapi applications py line in call await super call scope receive send file usr local lib site packages starlette applications py line in call await self middleware stack scope receive send file usr local lib site packages starlette middleware errors py line in call raise exc file usr local lib site packages starlette middleware errors py line in call await self app scope receive send file usr local lib site packages starlette middleware cors py line in call await self simple response scope receive send request headers headers file usr local lib site packages starlette middleware cors py line in simple response await self app scope receive send file usr local lib site packages starlette exceptions py line in call raise exc file usr local lib site packages starlette exceptions py line in call await self app scope receive sender file usr local lib site packages fastapi middleware asyncexitstack py line in call raise e file usr local lib site packages fastapi middleware asyncexitstack py line in call await self app scope receive send file usr local lib site packages starlette routing py line in call await route handle scope receive send file usr local lib site packages starlette routing py line in handle await self app scope receive send file usr local lib site packages starlette routing py line in app response await func request file usr local lib site packages fastapi routing py line in app raw response await run endpoint function file usr local lib site packages fastapi routing py line in run endpoint function return await run in threadpool dependant call values file usr local lib site packages starlette concurrency py line in run in threadpool return await anyio to thread run sync func args file usr local lib site packages anyio to thread py line in run sync return await get asynclib run sync in worker thread file usr local lib site packages anyio backends asyncio py line in run sync in worker thread return await future file usr local lib site packages anyio backends asyncio py line in run result context run func args file app src api routes automations py line in list autos return listdata file pydantic main py line in pydantic main basemodel init file pydantic main py line in pydantic main validate model file pydantic fields py line in pydantic fields modelfield validate file pydantic fields py line in pydantic fields modelfield validate sequence like file app src automations manager py line in find yield from load automation auto tags get auto get id attributeerror str object has no attribute get
| 0
|
306,585
| 26,482,414,970
|
IssuesEvent
|
2023-01-17 15:33:53
|
red-hat-storage/ocs-ci
|
https://api.github.com/repos/red-hat-storage/ocs-ci
|
closed
|
test_bucket_creation failed with ocs_ci.ocs.exceptions.CommandFailed: Error during execution of command: /home/jenkins/workspace/qe-deploy-ocs-cluster-prod/ocs-ci/data/mcg-cli backingstore create pv-pool pv-backingstore-216e7721521d4379baea7305 --num-volumes 1 --pv-size-gb 50 --storage-class ocs-storagecluster-ceph-rbd -n openshift-storage.
|
High Priority TestCase failing Squad/Red
|
Run details:
URL: https://reportportal-ocs4.apps.ocp-c1.prod.psi.redhat.com/ui/#OCS/launches/362/6633/272793/272796/272802/log
Run ID: 1669598191
Test Case: test_bucket_creation
ODF Build: 4.12.0-120
OCP Version: 4.12
Job name: VSPHERE6 UPI 1AZ RHCOS MCG Only Deployment 3M 3W tier1
Jenkins job: https://ocs4-jenkins-csb-odf-qe.apps.ocp-c1.prod.psi.redhat.com/job/qe-deploy-ocs-cluster-prod/6146/
Logs URL: http://magna002.ceph.redhat.com/ocsci-jenkins/openshift-clusters/j-005vu1rmcg33-t1/j-005vu1rmcg33-t1_20221128T003211/logs/
Failure Details:
```
Message: ocs_ci.ocs.exceptions.CommandFailed: Error during execution of command: /home/jenkins/workspace/qe-deploy-ocs-cluster-prod/ocs-ci/data/mcg-cli backingstore create pv-pool pv-backingstore-216e7721521d4379baea7305 --num-volumes 1 --pv-size-gb 50 --storage-class ocs-storagecluster-ceph-rbd -n openshift-storage.
Error is time="2022-11-28T01:32:25Z" level=info msg="✅ Exists: NooBaa \"noobaa\"\n"
time="2022-11-28T01:32:25Z" level=info msg="❌ Not Found: StorageClass \"ocs-storagecluster-ceph-rbd\"\n"
time="2022-11-28T01:32:25Z" level=fatal msg="❌ Could not get StorageClass \"ocs-storagecluster-ceph-rbd\" for system in namespace \"openshift-storage\""
Type: None
Text:
self = <tests.manage.mcg.test_bucket_creation.TestBucketCreation object at 0x7f4d6a8398e0>
bucket_class_factory = <function bucket_class_factory.<locals>._create_bucket_class at 0x7f4d6baee8b0>
bucket_factory = <function bucket_factory_fixture.<locals>._create_buckets at 0x7f4d6baee9d0>
amount = 1, interface = 'CLI'
bucketclass_dict = {'backingstore_dict': {'pv': [(1, 50, 'ocs-storagecluster-ceph-rbd')]}, 'interface': 'CLI'}
@pytest.mark.parametrize(
argnames="amount,interface,bucketclass_dict",
argvalues=[
pytest.param(
*[3, "S3", None],
marks=[pytest.mark.polarion_id("OCS-1298"), tier1, acceptance],
),
pytest.param(
*[100, "S3", None],
marks=[
pytest.mark.skip(ERRATIC_TIMEOUTS_SKIP_REASON),
performance,
pytest.mark.polarion_id("OCS-1823"),
],
),
pytest.param(
*[1000, "S3", None],
marks=[
pytest.mark.skip(ERRATIC_TIMEOUTS_SKIP_REASON),
performance,
pytest.mark.polarion_id("OCS-1824"),
],
),
pytest.param(
*[3, "OC", None],
marks=[tier1, acceptance, pytest.mark.polarion_id("OCS-1298")],
),
pytest.param(
*[100, "OC", None],
marks=[
pytest.mark.skip(ERRATIC_TIMEOUTS_SKIP_REASON),
performance,
pytest.mark.polarion_id("OCS-1826"),
],
),
pytest.param(
*[1000, "OC", None],
marks=[
pytest.mark.skip(ERRATIC_TIMEOUTS_SKIP_REASON),
performance,
pytest.mark.polarion_id("OCS-1827"),
],
),
pytest.param(
*[3, "CLI", None],
marks=[tier1, acceptance, pytest.mark.polarion_id("OCS-1298")],
),
pytest.param(
*[100, "CLI", None],
marks=[
pytest.mark.skip(ERRATIC_TIMEOUTS_SKIP_REASON),
performance,
pytest.mark.polarion_id("OCS-1825"),
],
),
pytest.param(
*[1000, "CLI", None],
marks=[
pytest.mark.skip(ERRATIC_TIMEOUTS_SKIP_REASON),
performance,
pytest.mark.polarion_id("OCS-1828"),
],
),
pytest.param(
*[
1,
"OC",
{
"interface": "OC",
"backingstore_dict": {
"pv": [(1, 50, DEFAULT_STORAGECLASS_RBD)]
},
},
],
marks=[tier1, pytest.mark.polarion_id("OCS-2331")],
),
pytest.param(
*[
1,
"CLI",
{
"interface": "CLI",
"backingstore_dict": {
"pv": [(1, 50, DEFAULT_STORAGECLASS_RBD)]
},
},
],
marks=[tier1, pytest.mark.polarion_id("OCS-2331")],
),
],
ids=[
"3-S3-DEFAULT-BACKINGSTORE",
"100-S3-DEFAULT-BACKINGSTORE",
"1000-S3-DEFAULT-BACKINGSTORE",
"3-OC-DEFAULT-BACKINGSTORE",
"100-OC-DEFAULT-BACKINGSTORE",
"1000-OC-DEFAULT-BACKINGSTORE",
"3-CLI-DEFAULT-BACKINGSTORE",
"100-CLI-DEFAULT-BACKINGSTORE",
"1000-CLI-DEFAULT-BACKINGSTORE",
"1-OC-PVPOOL",
"1-CLI-PVPOOL",
],
)
def test_bucket_creation(
self, bucket_class_factory, bucket_factory, amount, interface, bucketclass_dict
):
"""
Test bucket creation using the S3 SDK, OC command or MCG CLI.
The factory checks the bucket's health by default.
"""
> bucket_factory(amount, interface, bucketclass=bucketclass_dict)
tests/manage/mcg/test_bucket_creation.py:141:
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
tests/conftest.py:2557: in _create_buckets
bucketclass if bucketclass is None else bucket_class_factory(bucketclass)
ocs_ci/ocs/resources/bucketclass.py:169: in _create_bucket_class
for backingstore in backingstore_factory(
ocs_ci/ocs/resources/backingstore.py:316: in _create_backingstore
cmdMap[method.lower()][cloud.lower()](
ocs_ci/ocs/bucket_utils.py:738: in cli_create_pv_backingstore
mcg_obj.exec_mcg_cmd(cmd)
ocs_ci/ocs/resources/mcg.py:875: in exec_mcg_cmd
result = exec_cmd(
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
cmd = ['/home/jenkins/workspace/qe-deploy-ocs-cluster-prod/ocs-ci/data/mcg-cli', 'backingstore', 'create', 'pv-pool', 'pv-backingstore-216e7721521d4379baea7305', '--num-volumes', ...]
secrets = None, timeout = 600, ignore_error = False, threading_lock = None
silent = False, kwargs = {}
masked_cmd = '/home/jenkins/workspace/qe-deploy-ocs-cluster-prod/ocs-ci/data/mcg-cli backingstore create pv-pool pv-backingstore-216e7721521d4379baea7305 --num-volumes 1 --pv-size-gb 50 --storage-class ocs-storagecluster-ceph-rbd -n openshift-storage'
completed_process = CompletedProcess(args=['/home/jenkins/workspace/qe-deploy-ocs-cluster-prod/ocs-ci/data/mcg-cli', 'backingstore', 'crea...d\x8c Could not get StorageClass \\"ocs-storagecluster-ceph-rbd\\" for system in namespace \\"openshift-storage\\""\n')
masked_stdout = ''
masked_stderr = 'time="2022-11-28T01:32:25Z" level=info msg="✅ Exists: NooBaa \\"noobaa\\"\\n"\ntime="2022-11-28T01:32:25Z" level=info...msg="❌ Could not get StorageClass \\"ocs-storagecluster-ceph-rbd\\" for system in namespace \\"openshift-storage\\""\n'
def exec_cmd(
cmd,
secrets=None,
timeout=600,
ignore_error=False,
threading_lock=None,
silent=False,
**kwargs,
):
"""
Run an arbitrary command locally
If the command is grep and matching pattern is not found, then this function
returns "command terminated with exit code 1" in stderr.
Args:
cmd (str): command to run
secrets (list): A list of secrets to be masked with asterisks
This kwarg is popped in order to not interfere with
subprocess.run(``**kwargs``)
timeout (int): Timeout for the command, defaults to 600 seconds.
ignore_error (bool): True if ignore non zero return code and do not
raise the exception.
threading_lock (threading.Lock): threading.Lock object that is used
for handling concurrent oc commands
silent (bool): If True will silent errors from the server, default false
Raises:
CommandFailed: In case the command execution fails
Returns:
(CompletedProcess) A CompletedProcess object of the command that was executed
CompletedProcess attributes:
args: The list or str args passed to run().
returncode (str): The exit code of the process, negative for signals.
stdout (str): The standard output (None if not captured).
stderr (str): The standard error (None if not captured).
"""
masked_cmd = mask_secrets(cmd, secrets)
log.info(f"Executing command: {masked_cmd}")
if isinstance(cmd, str):
cmd = shlex.split(cmd)
if threading_lock and cmd[0] == "oc":
threading_lock.acquire()
completed_process = subprocess.run(
cmd,
stdout=subprocess.PIPE,
stderr=subprocess.PIPE,
stdin=subprocess.PIPE,
timeout=timeout,
**kwargs,
)
if threading_lock and cmd[0] == "oc":
threading_lock.release()
masked_stdout = mask_secrets(completed_process.stdout.decode(), secrets)
if len(completed_process.stdout) > 0:
log.debug(f"Command stdout: {masked_stdout}")
else:
log.debug("Command stdout is empty")
masked_stderr = mask_secrets(completed_process.stderr.decode(), secrets)
if len(completed_process.stderr) > 0:
if not silent:
log.warning(f"Command stderr: {masked_stderr}")
else:
log.debug("Command stderr is empty")
log.debug(f"Command return code: {completed_process.returncode}")
if completed_process.returncode and not ignore_error:
if (
"grep" in masked_cmd
and b"command terminated with exit code 1" in completed_process.stderr
):
log.info(f"No results found for grep command: {masked_cmd}")
else:
> raise CommandFailed(
f"Error during execution of command: {masked_cmd}."
f"\nError is {masked_stderr}"
)
E ocs_ci.ocs.exceptions.CommandFailed: Error during execution of command: /home/jenkins/workspace/qe-deploy-ocs-cluster-prod/ocs-ci/data/mcg-cli backingstore create pv-pool pv-backingstore-216e7721521d4379baea7305 --num-volumes 1 --pv-size-gb 50 --storage-class ocs-storagecluster-ceph-rbd -n openshift-storage.
E Error is time="2022-11-28T01:32:25Z" level=info msg="✅ Exists: NooBaa \"noobaa\"\n"
E time="2022-11-28T01:32:25Z" level=info msg="❌ Not Found: StorageClass \"ocs-storagecluster-ceph-rbd\"\n"
E time="2022-11-28T01:32:25Z" level=fatal msg="❌ Could not get StorageClass \"ocs-storagecluster-ceph-rbd\" for system in namespace \"openshift-storage\""
ocs_ci/utility/utils.py:636: CommandFailed
```
|
1.0
|
test_bucket_creation failed with ocs_ci.ocs.exceptions.CommandFailed: Error during execution of command: /home/jenkins/workspace/qe-deploy-ocs-cluster-prod/ocs-ci/data/mcg-cli backingstore create pv-pool pv-backingstore-216e7721521d4379baea7305 --num-volumes 1 --pv-size-gb 50 --storage-class ocs-storagecluster-ceph-rbd -n openshift-storage. - Run details:
URL: https://reportportal-ocs4.apps.ocp-c1.prod.psi.redhat.com/ui/#OCS/launches/362/6633/272793/272796/272802/log
Run ID: 1669598191
Test Case: test_bucket_creation
ODF Build: 4.12.0-120
OCP Version: 4.12
Job name: VSPHERE6 UPI 1AZ RHCOS MCG Only Deployment 3M 3W tier1
Jenkins job: https://ocs4-jenkins-csb-odf-qe.apps.ocp-c1.prod.psi.redhat.com/job/qe-deploy-ocs-cluster-prod/6146/
Logs URL: http://magna002.ceph.redhat.com/ocsci-jenkins/openshift-clusters/j-005vu1rmcg33-t1/j-005vu1rmcg33-t1_20221128T003211/logs/
Failure Details:
```
Message: ocs_ci.ocs.exceptions.CommandFailed: Error during execution of command: /home/jenkins/workspace/qe-deploy-ocs-cluster-prod/ocs-ci/data/mcg-cli backingstore create pv-pool pv-backingstore-216e7721521d4379baea7305 --num-volumes 1 --pv-size-gb 50 --storage-class ocs-storagecluster-ceph-rbd -n openshift-storage.
Error is time="2022-11-28T01:32:25Z" level=info msg="✅ Exists: NooBaa \"noobaa\"\n"
time="2022-11-28T01:32:25Z" level=info msg="❌ Not Found: StorageClass \"ocs-storagecluster-ceph-rbd\"\n"
time="2022-11-28T01:32:25Z" level=fatal msg="❌ Could not get StorageClass \"ocs-storagecluster-ceph-rbd\" for system in namespace \"openshift-storage\""
Type: None
Text:
self = <tests.manage.mcg.test_bucket_creation.TestBucketCreation object at 0x7f4d6a8398e0>
bucket_class_factory = <function bucket_class_factory.<locals>._create_bucket_class at 0x7f4d6baee8b0>
bucket_factory = <function bucket_factory_fixture.<locals>._create_buckets at 0x7f4d6baee9d0>
amount = 1, interface = 'CLI'
bucketclass_dict = {'backingstore_dict': {'pv': [(1, 50, 'ocs-storagecluster-ceph-rbd')]}, 'interface': 'CLI'}
@pytest.mark.parametrize(
argnames="amount,interface,bucketclass_dict",
argvalues=[
pytest.param(
*[3, "S3", None],
marks=[pytest.mark.polarion_id("OCS-1298"), tier1, acceptance],
),
pytest.param(
*[100, "S3", None],
marks=[
pytest.mark.skip(ERRATIC_TIMEOUTS_SKIP_REASON),
performance,
pytest.mark.polarion_id("OCS-1823"),
],
),
pytest.param(
*[1000, "S3", None],
marks=[
pytest.mark.skip(ERRATIC_TIMEOUTS_SKIP_REASON),
performance,
pytest.mark.polarion_id("OCS-1824"),
],
),
pytest.param(
*[3, "OC", None],
marks=[tier1, acceptance, pytest.mark.polarion_id("OCS-1298")],
),
pytest.param(
*[100, "OC", None],
marks=[
pytest.mark.skip(ERRATIC_TIMEOUTS_SKIP_REASON),
performance,
pytest.mark.polarion_id("OCS-1826"),
],
),
pytest.param(
*[1000, "OC", None],
marks=[
pytest.mark.skip(ERRATIC_TIMEOUTS_SKIP_REASON),
performance,
pytest.mark.polarion_id("OCS-1827"),
],
),
pytest.param(
*[3, "CLI", None],
marks=[tier1, acceptance, pytest.mark.polarion_id("OCS-1298")],
),
pytest.param(
*[100, "CLI", None],
marks=[
pytest.mark.skip(ERRATIC_TIMEOUTS_SKIP_REASON),
performance,
pytest.mark.polarion_id("OCS-1825"),
],
),
pytest.param(
*[1000, "CLI", None],
marks=[
pytest.mark.skip(ERRATIC_TIMEOUTS_SKIP_REASON),
performance,
pytest.mark.polarion_id("OCS-1828"),
],
),
pytest.param(
*[
1,
"OC",
{
"interface": "OC",
"backingstore_dict": {
"pv": [(1, 50, DEFAULT_STORAGECLASS_RBD)]
},
},
],
marks=[tier1, pytest.mark.polarion_id("OCS-2331")],
),
pytest.param(
*[
1,
"CLI",
{
"interface": "CLI",
"backingstore_dict": {
"pv": [(1, 50, DEFAULT_STORAGECLASS_RBD)]
},
},
],
marks=[tier1, pytest.mark.polarion_id("OCS-2331")],
),
],
ids=[
"3-S3-DEFAULT-BACKINGSTORE",
"100-S3-DEFAULT-BACKINGSTORE",
"1000-S3-DEFAULT-BACKINGSTORE",
"3-OC-DEFAULT-BACKINGSTORE",
"100-OC-DEFAULT-BACKINGSTORE",
"1000-OC-DEFAULT-BACKINGSTORE",
"3-CLI-DEFAULT-BACKINGSTORE",
"100-CLI-DEFAULT-BACKINGSTORE",
"1000-CLI-DEFAULT-BACKINGSTORE",
"1-OC-PVPOOL",
"1-CLI-PVPOOL",
],
)
def test_bucket_creation(
self, bucket_class_factory, bucket_factory, amount, interface, bucketclass_dict
):
"""
Test bucket creation using the S3 SDK, OC command or MCG CLI.
The factory checks the bucket's health by default.
"""
> bucket_factory(amount, interface, bucketclass=bucketclass_dict)
tests/manage/mcg/test_bucket_creation.py:141:
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
tests/conftest.py:2557: in _create_buckets
bucketclass if bucketclass is None else bucket_class_factory(bucketclass)
ocs_ci/ocs/resources/bucketclass.py:169: in _create_bucket_class
for backingstore in backingstore_factory(
ocs_ci/ocs/resources/backingstore.py:316: in _create_backingstore
cmdMap[method.lower()][cloud.lower()](
ocs_ci/ocs/bucket_utils.py:738: in cli_create_pv_backingstore
mcg_obj.exec_mcg_cmd(cmd)
ocs_ci/ocs/resources/mcg.py:875: in exec_mcg_cmd
result = exec_cmd(
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
cmd = ['/home/jenkins/workspace/qe-deploy-ocs-cluster-prod/ocs-ci/data/mcg-cli', 'backingstore', 'create', 'pv-pool', 'pv-backingstore-216e7721521d4379baea7305', '--num-volumes', ...]
secrets = None, timeout = 600, ignore_error = False, threading_lock = None
silent = False, kwargs = {}
masked_cmd = '/home/jenkins/workspace/qe-deploy-ocs-cluster-prod/ocs-ci/data/mcg-cli backingstore create pv-pool pv-backingstore-216e7721521d4379baea7305 --num-volumes 1 --pv-size-gb 50 --storage-class ocs-storagecluster-ceph-rbd -n openshift-storage'
completed_process = CompletedProcess(args=['/home/jenkins/workspace/qe-deploy-ocs-cluster-prod/ocs-ci/data/mcg-cli', 'backingstore', 'crea...d\x8c Could not get StorageClass \\"ocs-storagecluster-ceph-rbd\\" for system in namespace \\"openshift-storage\\""\n')
masked_stdout = ''
masked_stderr = 'time="2022-11-28T01:32:25Z" level=info msg="✅ Exists: NooBaa \\"noobaa\\"\\n"\ntime="2022-11-28T01:32:25Z" level=info...msg="❌ Could not get StorageClass \\"ocs-storagecluster-ceph-rbd\\" for system in namespace \\"openshift-storage\\""\n'
def exec_cmd(
cmd,
secrets=None,
timeout=600,
ignore_error=False,
threading_lock=None,
silent=False,
**kwargs,
):
"""
Run an arbitrary command locally
If the command is grep and matching pattern is not found, then this function
returns "command terminated with exit code 1" in stderr.
Args:
cmd (str): command to run
secrets (list): A list of secrets to be masked with asterisks
This kwarg is popped in order to not interfere with
subprocess.run(``**kwargs``)
timeout (int): Timeout for the command, defaults to 600 seconds.
ignore_error (bool): True if ignore non zero return code and do not
raise the exception.
threading_lock (threading.Lock): threading.Lock object that is used
for handling concurrent oc commands
silent (bool): If True will silent errors from the server, default false
Raises:
CommandFailed: In case the command execution fails
Returns:
(CompletedProcess) A CompletedProcess object of the command that was executed
CompletedProcess attributes:
args: The list or str args passed to run().
returncode (str): The exit code of the process, negative for signals.
stdout (str): The standard output (None if not captured).
stderr (str): The standard error (None if not captured).
"""
masked_cmd = mask_secrets(cmd, secrets)
log.info(f"Executing command: {masked_cmd}")
if isinstance(cmd, str):
cmd = shlex.split(cmd)
if threading_lock and cmd[0] == "oc":
threading_lock.acquire()
completed_process = subprocess.run(
cmd,
stdout=subprocess.PIPE,
stderr=subprocess.PIPE,
stdin=subprocess.PIPE,
timeout=timeout,
**kwargs,
)
if threading_lock and cmd[0] == "oc":
threading_lock.release()
masked_stdout = mask_secrets(completed_process.stdout.decode(), secrets)
if len(completed_process.stdout) > 0:
log.debug(f"Command stdout: {masked_stdout}")
else:
log.debug("Command stdout is empty")
masked_stderr = mask_secrets(completed_process.stderr.decode(), secrets)
if len(completed_process.stderr) > 0:
if not silent:
log.warning(f"Command stderr: {masked_stderr}")
else:
log.debug("Command stderr is empty")
log.debug(f"Command return code: {completed_process.returncode}")
if completed_process.returncode and not ignore_error:
if (
"grep" in masked_cmd
and b"command terminated with exit code 1" in completed_process.stderr
):
log.info(f"No results found for grep command: {masked_cmd}")
else:
> raise CommandFailed(
f"Error during execution of command: {masked_cmd}."
f"\nError is {masked_stderr}"
)
E ocs_ci.ocs.exceptions.CommandFailed: Error during execution of command: /home/jenkins/workspace/qe-deploy-ocs-cluster-prod/ocs-ci/data/mcg-cli backingstore create pv-pool pv-backingstore-216e7721521d4379baea7305 --num-volumes 1 --pv-size-gb 50 --storage-class ocs-storagecluster-ceph-rbd -n openshift-storage.
E Error is time="2022-11-28T01:32:25Z" level=info msg="✅ Exists: NooBaa \"noobaa\"\n"
E time="2022-11-28T01:32:25Z" level=info msg="❌ Not Found: StorageClass \"ocs-storagecluster-ceph-rbd\"\n"
E time="2022-11-28T01:32:25Z" level=fatal msg="❌ Could not get StorageClass \"ocs-storagecluster-ceph-rbd\" for system in namespace \"openshift-storage\""
ocs_ci/utility/utils.py:636: CommandFailed
```
|
non_secu
|
test bucket creation failed with ocs ci ocs exceptions commandfailed error during execution of command home jenkins workspace qe deploy ocs cluster prod ocs ci data mcg cli backingstore create pv pool pv backingstore num volumes pv size gb storage class ocs storagecluster ceph rbd n openshift storage run details url run id test case test bucket creation odf build ocp version job name upi rhcos mcg only deployment jenkins job logs url failure details message ocs ci ocs exceptions commandfailed error during execution of command home jenkins workspace qe deploy ocs cluster prod ocs ci data mcg cli backingstore create pv pool pv backingstore num volumes pv size gb storage class ocs storagecluster ceph rbd n openshift storage error is time level info msg ✅ exists noobaa noobaa n time level info msg ❌ not found storageclass ocs storagecluster ceph rbd n time level fatal msg ❌ could not get storageclass ocs storagecluster ceph rbd for system in namespace openshift storage type none text self bucket class factory create bucket class at bucket factory create buckets at amount interface cli bucketclass dict backingstore dict pv interface cli pytest mark parametrize argnames amount interface bucketclass dict argvalues pytest param marks pytest param marks pytest mark skip erratic timeouts skip reason performance pytest mark polarion id ocs pytest param marks pytest mark skip erratic timeouts skip reason performance pytest mark polarion id ocs pytest param marks pytest param marks pytest mark skip erratic timeouts skip reason performance pytest mark polarion id ocs pytest param marks pytest mark skip erratic timeouts skip reason performance pytest mark polarion id ocs pytest param marks pytest param marks pytest mark skip erratic timeouts skip reason performance pytest mark polarion id ocs pytest param marks pytest mark skip erratic timeouts skip reason performance pytest mark polarion id ocs pytest param oc interface oc backingstore dict pv marks pytest param cli interface cli backingstore dict pv marks ids default backingstore default backingstore default backingstore oc default backingstore oc default backingstore oc default backingstore cli default backingstore cli default backingstore cli default backingstore oc pvpool cli pvpool def test bucket creation self bucket class factory bucket factory amount interface bucketclass dict test bucket creation using the sdk oc command or mcg cli the factory checks the bucket s health by default bucket factory amount interface bucketclass bucketclass dict tests manage mcg test bucket creation py tests conftest py in create buckets bucketclass if bucketclass is none else bucket class factory bucketclass ocs ci ocs resources bucketclass py in create bucket class for backingstore in backingstore factory ocs ci ocs resources backingstore py in create backingstore cmdmap ocs ci ocs bucket utils py in cli create pv backingstore mcg obj exec mcg cmd cmd ocs ci ocs resources mcg py in exec mcg cmd result exec cmd cmd secrets none timeout ignore error false threading lock none silent false kwargs masked cmd home jenkins workspace qe deploy ocs cluster prod ocs ci data mcg cli backingstore create pv pool pv backingstore num volumes pv size gb storage class ocs storagecluster ceph rbd n openshift storage completed process completedprocess args home jenkins workspace qe deploy ocs cluster prod ocs ci data mcg cli backingstore crea d could not get storageclass ocs storagecluster ceph rbd for system in namespace openshift storage n masked stdout masked stderr time level info msg ✅ exists noobaa noobaa n ntime level info msg ❌ could not get storageclass ocs storagecluster ceph rbd for system in namespace openshift storage n def exec cmd cmd secrets none timeout ignore error false threading lock none silent false kwargs run an arbitrary command locally if the command is grep and matching pattern is not found then this function returns command terminated with exit code in stderr args cmd str command to run secrets list a list of secrets to be masked with asterisks this kwarg is popped in order to not interfere with subprocess run kwargs timeout int timeout for the command defaults to seconds ignore error bool true if ignore non zero return code and do not raise the exception threading lock threading lock threading lock object that is used for handling concurrent oc commands silent bool if true will silent errors from the server default false raises commandfailed in case the command execution fails returns completedprocess a completedprocess object of the command that was executed completedprocess attributes args the list or str args passed to run returncode str the exit code of the process negative for signals stdout str the standard output none if not captured stderr str the standard error none if not captured masked cmd mask secrets cmd secrets log info f executing command masked cmd if isinstance cmd str cmd shlex split cmd if threading lock and cmd oc threading lock acquire completed process subprocess run cmd stdout subprocess pipe stderr subprocess pipe stdin subprocess pipe timeout timeout kwargs if threading lock and cmd oc threading lock release masked stdout mask secrets completed process stdout decode secrets if len completed process stdout log debug f command stdout masked stdout else log debug command stdout is empty masked stderr mask secrets completed process stderr decode secrets if len completed process stderr if not silent log warning f command stderr masked stderr else log debug command stderr is empty log debug f command return code completed process returncode if completed process returncode and not ignore error if grep in masked cmd and b command terminated with exit code in completed process stderr log info f no results found for grep command masked cmd else raise commandfailed f error during execution of command masked cmd f nerror is masked stderr e ocs ci ocs exceptions commandfailed error during execution of command home jenkins workspace qe deploy ocs cluster prod ocs ci data mcg cli backingstore create pv pool pv backingstore num volumes pv size gb storage class ocs storagecluster ceph rbd n openshift storage e error is time level info msg ✅ exists noobaa noobaa n e time level info msg ❌ not found storageclass ocs storagecluster ceph rbd n e time level fatal msg ❌ could not get storageclass ocs storagecluster ceph rbd for system in namespace openshift storage ocs ci utility utils py commandfailed
| 0
|
59,497
| 3,113,936,772
|
IssuesEvent
|
2015-09-03 04:11:13
|
AutomationSolutionz/Framework_0.1
|
https://api.github.com/repos/AutomationSolutionz/Framework_0.1
|
closed
|
Common tab is not considering all the other status that were added later.
|
bug Priority 2 (High) Release Gating Shetu
|
Common tab is not considering all the other status that we added new.
Please make sure all status are grouped together and user can view full detail.
|
1.0
|
Common tab is not considering all the other status that were added later. - Common tab is not considering all the other status that we added new.
Please make sure all status are grouped together and user can view full detail.
|
non_secu
|
common tab is not considering all the other status that were added later common tab is not considering all the other status that we added new please make sure all status are grouped together and user can view full detail
| 0
|
34,577
| 12,293,475,879
|
IssuesEvent
|
2020-05-10 19:10:46
|
heholek/better-onetab
|
https://api.github.com/repos/heholek/better-onetab
|
opened
|
WS-2020-0068 (High) detected in yargs-parser-13.1.2.tgz
|
security vulnerability
|
## WS-2020-0068 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>yargs-parser-13.1.2.tgz</b></p></summary>
<p>the mighty option parser used by yargs</p>
<p>Library home page: <a href="https://registry.npmjs.org/yargs-parser/-/yargs-parser-13.1.2.tgz">https://registry.npmjs.org/yargs-parser/-/yargs-parser-13.1.2.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/better-onetab/package.json</p>
<p>Path to vulnerable library: /tmp/ws-scm/better-onetab/node_modules/yargs-parser/package.json</p>
<p>
Dependency Hierarchy:
- webpack-cli-3.3.11.tgz (Root Library)
- yargs-13.2.4.tgz
- :x: **yargs-parser-13.1.2.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/heholek/better-onetab/commit/34ef2ec6547275b25ebbcfdab80f0894bbeac266">34ef2ec6547275b25ebbcfdab80f0894bbeac266</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Affected versions of yargs-parser are vulnerable to prototype pollution. Arguments are not properly sanitized, allowing an attacker to modify the prototype of Object, causing the addition or modification of an existing property that will exist on all objects. Parsing the argument --foo.__proto__.bar baz' adds a bar property with value baz to all objects. This is only exploitable if attackers have control over the arguments being passed to yargs-parser.
<p>Publish Date: 2020-05-01
<p>URL: <a href=https://www.npmjs.com/advisories/1500>WS-2020-0068</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Adjacent
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/package/yargs-parser">https://www.npmjs.com/package/yargs-parser</a></p>
<p>Release Date: 2020-05-04</p>
<p>Fix Resolution: https://www.npmjs.com/package/yargs-parser/v/18.1.2,https://www.npmjs.com/package/yargs-parser/v/15.0.1</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
WS-2020-0068 (High) detected in yargs-parser-13.1.2.tgz - ## WS-2020-0068 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>yargs-parser-13.1.2.tgz</b></p></summary>
<p>the mighty option parser used by yargs</p>
<p>Library home page: <a href="https://registry.npmjs.org/yargs-parser/-/yargs-parser-13.1.2.tgz">https://registry.npmjs.org/yargs-parser/-/yargs-parser-13.1.2.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/better-onetab/package.json</p>
<p>Path to vulnerable library: /tmp/ws-scm/better-onetab/node_modules/yargs-parser/package.json</p>
<p>
Dependency Hierarchy:
- webpack-cli-3.3.11.tgz (Root Library)
- yargs-13.2.4.tgz
- :x: **yargs-parser-13.1.2.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/heholek/better-onetab/commit/34ef2ec6547275b25ebbcfdab80f0894bbeac266">34ef2ec6547275b25ebbcfdab80f0894bbeac266</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Affected versions of yargs-parser are vulnerable to prototype pollution. Arguments are not properly sanitized, allowing an attacker to modify the prototype of Object, causing the addition or modification of an existing property that will exist on all objects. Parsing the argument --foo.__proto__.bar baz' adds a bar property with value baz to all objects. This is only exploitable if attackers have control over the arguments being passed to yargs-parser.
<p>Publish Date: 2020-05-01
<p>URL: <a href=https://www.npmjs.com/advisories/1500>WS-2020-0068</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Adjacent
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/package/yargs-parser">https://www.npmjs.com/package/yargs-parser</a></p>
<p>Release Date: 2020-05-04</p>
<p>Fix Resolution: https://www.npmjs.com/package/yargs-parser/v/18.1.2,https://www.npmjs.com/package/yargs-parser/v/15.0.1</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
ws high detected in yargs parser tgz ws high severity vulnerability vulnerable library yargs parser tgz the mighty option parser used by yargs library home page a href path to dependency file tmp ws scm better onetab package json path to vulnerable library tmp ws scm better onetab node modules yargs parser package json dependency hierarchy webpack cli tgz root library yargs tgz x yargs parser tgz vulnerable library found in head commit a href vulnerability details affected versions of yargs parser are vulnerable to prototype pollution arguments are not properly sanitized allowing an attacker to modify the prototype of object causing the addition or modification of an existing property that will exist on all objects parsing the argument foo proto bar baz adds a bar property with value baz to all objects this is only exploitable if attackers have control over the arguments being passed to yargs parser publish date url a href cvss score details base score metrics exploitability metrics attack vector adjacent attack complexity high privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource
| 1
|
197,484
| 6,955,823,853
|
IssuesEvent
|
2017-12-07 09:20:22
|
Sinapse-Energia/AP-Sinapse
|
https://api.github.com/repos/Sinapse-Energia/AP-Sinapse
|
opened
|
[ML 8 - RF] The command 126; is not sending the correct data
|
enhancement High Priority
|
The configure radio command is built with the following frame:
0C 16 00 00 01 00 00 02 RC 01 06 CS
The value RC indicates if the EPD should be a master or not and the number of transmissions of a command is the device is a master.
Now, is possible to set the EPD as a master but the number of transmissions is always zero. This is not correct. The number of transmissions should be set to 7.
So, now RC = 80 (1000 0000) but should be 87 (1000 0111)
|
1.0
|
[ML 8 - RF] The command 126; is not sending the correct data - The configure radio command is built with the following frame:
0C 16 00 00 01 00 00 02 RC 01 06 CS
The value RC indicates if the EPD should be a master or not and the number of transmissions of a command is the device is a master.
Now, is possible to set the EPD as a master but the number of transmissions is always zero. This is not correct. The number of transmissions should be set to 7.
So, now RC = 80 (1000 0000) but should be 87 (1000 0111)
|
non_secu
|
the command is not sending the correct data the configure radio command is built with the following frame rc cs the value rc indicates if the epd should be a master or not and the number of transmissions of a command is the device is a master now is possible to set the epd as a master but the number of transmissions is always zero this is not correct the number of transmissions should be set to so now rc but should be
| 0
|
12,670
| 8,710,323,234
|
IssuesEvent
|
2018-12-06 16:09:05
|
adempiere/adempiere
|
https://api.github.com/repos/adempiere/adempiere
|
closed
|
Improve default features for XML importer
|
(SC) System Core (SE) Security 01 enhancement
|
This issue is for set a default features for XML importers from ADempiere
|
True
|
Improve default features for XML importer - This issue is for set a default features for XML importers from ADempiere
|
secu
|
improve default features for xml importer this issue is for set a default features for xml importers from adempiere
| 1
|
45,987
| 13,147,793,305
|
IssuesEvent
|
2020-08-08 17:36:53
|
dotnet/runtime
|
https://api.github.com/repos/dotnet/runtime
|
closed
|
Make SSL handshake exceptions and logging useful
|
area-System.Net.Security enhancement
|
There is growing number of cases (like #27703) where uses see something like:
```
---> System.Security.Authentication.AuthenticationException: The remote certificate is invalid according to the validation procedure.
at System.Net.Security.SslState.StartSendAuthResetSignal(ProtocolToken message, AsyncProtocolRequest asyncRequest, ExceptionDispatchInfo exception)
```
From that, it is very difficult to diagnose real root cause
It would be nice if the exception can provide more specific reason. This may not be complete list but it would be nice to distinguish following cases:
- wrong time
- unknown/untrusted CA
- name mismatch
- CRL/OSCP revocation issues
- custom verification callback denial
- extended key usage violation or other attribute problems
|
True
|
Make SSL handshake exceptions and logging useful - There is growing number of cases (like #27703) where uses see something like:
```
---> System.Security.Authentication.AuthenticationException: The remote certificate is invalid according to the validation procedure.
at System.Net.Security.SslState.StartSendAuthResetSignal(ProtocolToken message, AsyncProtocolRequest asyncRequest, ExceptionDispatchInfo exception)
```
From that, it is very difficult to diagnose real root cause
It would be nice if the exception can provide more specific reason. This may not be complete list but it would be nice to distinguish following cases:
- wrong time
- unknown/untrusted CA
- name mismatch
- CRL/OSCP revocation issues
- custom verification callback denial
- extended key usage violation or other attribute problems
|
secu
|
make ssl handshake exceptions and logging useful there is growing number of cases like where uses see something like system security authentication authenticationexception the remote certificate is invalid according to the validation procedure at system net security sslstate startsendauthresetsignal protocoltoken message asyncprotocolrequest asyncrequest exceptiondispatchinfo exception from that it is very difficult to diagnose real root cause it would be nice if the exception can provide more specific reason this may not be complete list but it would be nice to distinguish following cases wrong time unknown untrusted ca name mismatch crl oscp revocation issues custom verification callback denial extended key usage violation or other attribute problems
| 1
|
149,544
| 11,905,264,596
|
IssuesEvent
|
2020-03-30 18:15:47
|
IntellectualSites/FastAsyncWorldEdit
|
https://api.github.com/repos/IntellectualSites/FastAsyncWorldEdit
|
closed
|
FAWE returns wrong version on server start
|
Requires Testing
|
**[REQUIRED] FastAsyncWorldEdit Configuration Files:** n/a
<!--- Issue /fawe debugpaste in game or in your console and copy the supplied URL here -->
<!--- If you cannot perform the above, we require logs/latest.log; config.yml and config-legacy.yml -->
<!--- If you are unwilling to supply the information we need, we reserve the right to not assist you. Redact IP addresses if you need to. -->
**[REQUIRED] FastAsyncWorldEdit Version Number:** Build 155
<!--- Enter /fawe version in game or in your console and copy the full output here -->
**[REQUIRED] Spigot/Paper Version Number:** n/a
<!--- Enter /version ingame or in your console and paste the full output here -->
**[REQUIRED] Description of the problem:**
<!--- Check your console for errors while testing -->
<!--- Include relevant information like errors or a picture of the problem -->
<!--- Be as specific as possible. Don't lie, redact information, or use false names/situations. -->
<!--- Who, What, When, Where, Why, How, Expected behavior, Resultant behavior, etc -->
When you start your server, you get
[FastAsyncWorldEdit] Loading FastAsyncWorldEdit v1.14
[FastAsyncWorldEdit] Enabling FastAsyncWorldEdit v1.14
This is the wrong version when using the 1.15 builds. Looking into the code I lost my will to live, so instead of a PR here is an issue for that.
Would also be cool to have the current build number displayed there as well
**How to replicate**:
<!--- If you can reproduce the issue please tell us as detailed as possible step by step how to do that -->
Put Fawe in your plugins folder
Start your server
**Checklist**:
<!--- Make sure you've completed the following steps (put an "X" between of brackets): -->
- [] I included all information required in the sections above
- [x] I made sure there are no duplicates of this report [(Use Search)](https://github.com/IntellectualSites/FastAsyncWorldEdit-1.13/issues?utf8=%E2%9C%93&q=is%3Aissue)
- [x] I made sure I am using an up-to-date version of [FastAsyncWorldEdit for 1.14.4](https://ci.athion.net/job/FastAsyncWorldEdit-pipeline/)
- [] I made sure the bug/error is not caused by any other plugin
|
1.0
|
FAWE returns wrong version on server start -
**[REQUIRED] FastAsyncWorldEdit Configuration Files:** n/a
<!--- Issue /fawe debugpaste in game or in your console and copy the supplied URL here -->
<!--- If you cannot perform the above, we require logs/latest.log; config.yml and config-legacy.yml -->
<!--- If you are unwilling to supply the information we need, we reserve the right to not assist you. Redact IP addresses if you need to. -->
**[REQUIRED] FastAsyncWorldEdit Version Number:** Build 155
<!--- Enter /fawe version in game or in your console and copy the full output here -->
**[REQUIRED] Spigot/Paper Version Number:** n/a
<!--- Enter /version ingame or in your console and paste the full output here -->
**[REQUIRED] Description of the problem:**
<!--- Check your console for errors while testing -->
<!--- Include relevant information like errors or a picture of the problem -->
<!--- Be as specific as possible. Don't lie, redact information, or use false names/situations. -->
<!--- Who, What, When, Where, Why, How, Expected behavior, Resultant behavior, etc -->
When you start your server, you get
[FastAsyncWorldEdit] Loading FastAsyncWorldEdit v1.14
[FastAsyncWorldEdit] Enabling FastAsyncWorldEdit v1.14
This is the wrong version when using the 1.15 builds. Looking into the code I lost my will to live, so instead of a PR here is an issue for that.
Would also be cool to have the current build number displayed there as well
**How to replicate**:
<!--- If you can reproduce the issue please tell us as detailed as possible step by step how to do that -->
Put Fawe in your plugins folder
Start your server
**Checklist**:
<!--- Make sure you've completed the following steps (put an "X" between of brackets): -->
- [] I included all information required in the sections above
- [x] I made sure there are no duplicates of this report [(Use Search)](https://github.com/IntellectualSites/FastAsyncWorldEdit-1.13/issues?utf8=%E2%9C%93&q=is%3Aissue)
- [x] I made sure I am using an up-to-date version of [FastAsyncWorldEdit for 1.14.4](https://ci.athion.net/job/FastAsyncWorldEdit-pipeline/)
- [] I made sure the bug/error is not caused by any other plugin
|
non_secu
|
fawe returns wrong version on server start fastasyncworldedit configuration files n a fastasyncworldedit version number build spigot paper version number n a description of the problem when you start your server you get loading fastasyncworldedit enabling fastasyncworldedit this is the wrong version when using the builds looking into the code i lost my will to live so instead of a pr here is an issue for that would also be cool to have the current build number displayed there as well how to replicate put fawe in your plugins folder start your server checklist i included all information required in the sections above i made sure there are no duplicates of this report i made sure i am using an up to date version of i made sure the bug error is not caused by any other plugin
| 0
|
267,869
| 28,509,429,880
|
IssuesEvent
|
2023-04-19 02:02:47
|
RG4421/ampere-centos-kernel
|
https://api.github.com/repos/RG4421/ampere-centos-kernel
|
closed
|
CVE-2020-27825 (Medium) detected in linuxv5.2 - autoclosed
|
Mend: dependency security vulnerability
|
## CVE-2020-27825 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linuxv5.2</b></p></summary>
<p>
<p>Linux kernel source tree</p>
<p>Library home page: <a href=https://github.com/torvalds/linux.git>https://github.com/torvalds/linux.git</a></p>
<p>Found in base branch: <b>amp-centos-8.0-kernel</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (1)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/kernel/trace/ring_buffer.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png?' width=19 height=20> Vulnerability Details</summary>
<p>
A use-after-free flaw was found in kernel/trace/ring_buffer.c in Linux kernel (before 5.10-rc1). There was a race problem in trace_open and resize of cpu buffer running parallely on different cpus, may cause a denial of service problem (DOS). This flaw could even allow a local attacker with special user privilege to a kernel information leak threat.
<p>Publish Date: 2020-12-11
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-27825>CVE-2020-27825</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.7</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: High
- Privileges Required: High
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-12-11</p>
<p>Fix Resolution: v5.9.5</p>
</p>
</details>
<p></p>
|
True
|
CVE-2020-27825 (Medium) detected in linuxv5.2 - autoclosed - ## CVE-2020-27825 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linuxv5.2</b></p></summary>
<p>
<p>Linux kernel source tree</p>
<p>Library home page: <a href=https://github.com/torvalds/linux.git>https://github.com/torvalds/linux.git</a></p>
<p>Found in base branch: <b>amp-centos-8.0-kernel</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (1)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/kernel/trace/ring_buffer.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png?' width=19 height=20> Vulnerability Details</summary>
<p>
A use-after-free flaw was found in kernel/trace/ring_buffer.c in Linux kernel (before 5.10-rc1). There was a race problem in trace_open and resize of cpu buffer running parallely on different cpus, may cause a denial of service problem (DOS). This flaw could even allow a local attacker with special user privilege to a kernel information leak threat.
<p>Publish Date: 2020-12-11
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-27825>CVE-2020-27825</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.7</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: High
- Privileges Required: High
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2020-12-11</p>
<p>Fix Resolution: v5.9.5</p>
</p>
</details>
<p></p>
|
secu
|
cve medium detected in autoclosed cve medium severity vulnerability vulnerable library linux kernel source tree library home page a href found in base branch amp centos kernel vulnerable source files kernel trace ring buffer c vulnerability details a use after free flaw was found in kernel trace ring buffer c in linux kernel before there was a race problem in trace open and resize of cpu buffer running parallely on different cpus may cause a denial of service problem dos this flaw could even allow a local attacker with special user privilege to a kernel information leak threat publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity high privileges required high user interaction none scope unchanged impact metrics confidentiality impact high integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version release date fix resolution
| 1
|
303,532
| 26,215,353,688
|
IssuesEvent
|
2023-01-04 10:29:13
|
saleor/saleor-dashboard
|
https://api.github.com/repos/saleor/saleor-dashboard
|
closed
|
Cypress test fail: should be able to sort products by price. TC: SALEOR_2607
|
tests
|
**Known bug for versions:**
v34: true
**Additional Info:**
Spec: As an admin I should be able to sort products
|
1.0
|
Cypress test fail: should be able to sort products by price. TC: SALEOR_2607 - **Known bug for versions:**
v34: true
**Additional Info:**
Spec: As an admin I should be able to sort products
|
non_secu
|
cypress test fail should be able to sort products by price tc saleor known bug for versions true additional info spec as an admin i should be able to sort products
| 0
|
9,521
| 13,508,556,670
|
IssuesEvent
|
2020-09-14 07:54:26
|
hajke-gu/text-mod
|
https://api.github.com/repos/hajke-gu/text-mod
|
opened
|
It must be possible to view texts that are longer than fits in the allocated space, or even the screen.
|
Requirement
|
# Requirement 2
## Description
"It must be possible to view texts that are longer than fits in the allocated space, or even the screen."
## Acceptance criteria
- Acceptance criteria 1
- Acceptance criteria 2
|
1.0
|
It must be possible to view texts that are longer than fits in the allocated space, or even the screen. - # Requirement 2
## Description
"It must be possible to view texts that are longer than fits in the allocated space, or even the screen."
## Acceptance criteria
- Acceptance criteria 1
- Acceptance criteria 2
|
non_secu
|
it must be possible to view texts that are longer than fits in the allocated space or even the screen requirement description it must be possible to view texts that are longer than fits in the allocated space or even the screen acceptance criteria acceptance criteria acceptance criteria
| 0
|
205,160
| 23,303,527,302
|
IssuesEvent
|
2022-08-07 17:29:12
|
rsoreq/NodeGoat
|
https://api.github.com/repos/rsoreq/NodeGoat
|
closed
|
CVE-2016-1000232 (Low) detected in tough-cookie-2.2.2.tgz - autoclosed
|
security vulnerability
|
## CVE-2016-1000232 - Low Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>tough-cookie-2.2.2.tgz</b></p></summary>
<p>RFC6265 Cookies and Cookie Jar for node.js</p>
<p>Library home page: <a href="https://registry.npmjs.org/tough-cookie/-/tough-cookie-2.2.2.tgz">https://registry.npmjs.org/tough-cookie/-/tough-cookie-2.2.2.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/grunt-retire/node_modules/tough-cookie/package.json</p>
<p>
Dependency Hierarchy:
- grunt-retire-0.3.12.tgz (Root Library)
- request-2.67.0.tgz
- :x: **tough-cookie-2.2.2.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/rsoreq/NodeGoat/commit/30db8811fba7f9bab1b860cabc70c1795eac29e9">30db8811fba7f9bab1b860cabc70c1795eac29e9</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/low_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
NodeJS Tough-Cookie version 2.2.2 contains a Regular Expression Parsing vulnerability in HTTP request Cookie Header parsing that can result in Denial of Service. This attack appear to be exploitable via Custom HTTP header passed by client. This vulnerability appears to have been fixed in 2.3.0.
<p>Publish Date: 2018-09-05
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2016-1000232>CVE-2016-1000232</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>3.7</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/advisories/130">https://www.npmjs.com/advisories/130</a></p>
<p>Release Date: 2018-09-05</p>
<p>Fix Resolution (tough-cookie): 2.3.0</p>
<p>Direct dependency fix Resolution (grunt-retire): 1.0.4</p>
</p>
</details>
<p></p>
***
<!-- REMEDIATE-OPEN-PR-START -->
- [ ] Check this box to open an automated fix PR
<!-- REMEDIATE-OPEN-PR-END -->
|
True
|
CVE-2016-1000232 (Low) detected in tough-cookie-2.2.2.tgz - autoclosed - ## CVE-2016-1000232 - Low Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>tough-cookie-2.2.2.tgz</b></p></summary>
<p>RFC6265 Cookies and Cookie Jar for node.js</p>
<p>Library home page: <a href="https://registry.npmjs.org/tough-cookie/-/tough-cookie-2.2.2.tgz">https://registry.npmjs.org/tough-cookie/-/tough-cookie-2.2.2.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/grunt-retire/node_modules/tough-cookie/package.json</p>
<p>
Dependency Hierarchy:
- grunt-retire-0.3.12.tgz (Root Library)
- request-2.67.0.tgz
- :x: **tough-cookie-2.2.2.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/rsoreq/NodeGoat/commit/30db8811fba7f9bab1b860cabc70c1795eac29e9">30db8811fba7f9bab1b860cabc70c1795eac29e9</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/low_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
NodeJS Tough-Cookie version 2.2.2 contains a Regular Expression Parsing vulnerability in HTTP request Cookie Header parsing that can result in Denial of Service. This attack appear to be exploitable via Custom HTTP header passed by client. This vulnerability appears to have been fixed in 2.3.0.
<p>Publish Date: 2018-09-05
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2016-1000232>CVE-2016-1000232</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>3.7</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.npmjs.com/advisories/130">https://www.npmjs.com/advisories/130</a></p>
<p>Release Date: 2018-09-05</p>
<p>Fix Resolution (tough-cookie): 2.3.0</p>
<p>Direct dependency fix Resolution (grunt-retire): 1.0.4</p>
</p>
</details>
<p></p>
***
<!-- REMEDIATE-OPEN-PR-START -->
- [ ] Check this box to open an automated fix PR
<!-- REMEDIATE-OPEN-PR-END -->
|
secu
|
cve low detected in tough cookie tgz autoclosed cve low severity vulnerability vulnerable library tough cookie tgz cookies and cookie jar for node js library home page a href path to dependency file package json path to vulnerable library node modules grunt retire node modules tough cookie package json dependency hierarchy grunt retire tgz root library request tgz x tough cookie tgz vulnerable library found in head commit a href found in base branch master vulnerability details nodejs tough cookie version contains a regular expression parsing vulnerability in http request cookie header parsing that can result in denial of service this attack appear to be exploitable via custom http header passed by client this vulnerability appears to have been fixed in publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact low for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution tough cookie direct dependency fix resolution grunt retire check this box to open an automated fix pr
| 1
|
134,617
| 5,231,637,714
|
IssuesEvent
|
2017-01-30 04:17:09
|
talonbragg/Custom-Markup
|
https://api.github.com/repos/talonbragg/Custom-Markup
|
closed
|
XHTML
|
Done enhancement help wanted Pending Priority: Low question wontfix
|
Should we use XHTML instead of HTML? XHTML is like HTML and XML mushed together. It has stricter rules and is the better option for services with SSL encryptions. It also offers better support for Internet Explorer.
Read more [here](http://stackoverflow.com/questions/1969290/what-is-the-difference-between-html-and-xhtml-extension-xhtml-is-a-markup-lan)
|
1.0
|
XHTML - Should we use XHTML instead of HTML? XHTML is like HTML and XML mushed together. It has stricter rules and is the better option for services with SSL encryptions. It also offers better support for Internet Explorer.
Read more [here](http://stackoverflow.com/questions/1969290/what-is-the-difference-between-html-and-xhtml-extension-xhtml-is-a-markup-lan)
|
non_secu
|
xhtml should we use xhtml instead of html xhtml is like html and xml mushed together it has stricter rules and is the better option for services with ssl encryptions it also offers better support for internet explorer read more
| 0
|
98,256
| 16,361,477,439
|
IssuesEvent
|
2021-05-14 10:08:29
|
Galaxy-Software-Service/Maven_Pom_Demo
|
https://api.github.com/repos/Galaxy-Software-Service/Maven_Pom_Demo
|
opened
|
CVE-2016-3093 (Medium) detected in struts2-core-2.3.15.jar, ognl-3.0.6.jar
|
security vulnerability
|
## CVE-2016-3093 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>struts2-core-2.3.15.jar</b>, <b>ognl-3.0.6.jar</b></p></summary>
<p>
<details><summary><b>struts2-core-2.3.15.jar</b></p></summary>
<p>Apache Struts 2</p>
<p>Path to dependency file: Maven_Pom_Demo/pom.xml</p>
<p>Path to vulnerable library: canner/.m2/repository/org/apache/struts/struts2-core/2.3.15/struts2-core-2.3.15.jar</p>
<p>
Dependency Hierarchy:
- :x: **struts2-core-2.3.15.jar** (Vulnerable Library)
</details>
<details><summary><b>ognl-3.0.6.jar</b></p></summary>
<p>OGNL - Object Graph Navigation Library</p>
<p>Library home page: <a href="http://ognl.org">http://ognl.org</a></p>
<p>Path to dependency file: Maven_Pom_Demo/pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/ognl/ognl/3.0.6/ognl-3.0.6.jar</p>
<p>
Dependency Hierarchy:
- struts2-core-2.3.15.jar (Root Library)
- :x: **ognl-3.0.6.jar** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/Galaxy-Software-Service/Maven_Pom_Demo/commit/3774e4b6d3e5f4ad3fa9f69e93f2b07cf1b66027">3774e4b6d3e5f4ad3fa9f69e93f2b07cf1b66027</a></p>
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Apache Struts 2.0.0 through 2.3.24.1 does not properly cache method references when used with OGNL before 3.0.12, which allows remote attackers to cause a denial of service (block access to a web site) via unspecified vectors.
<p>Publish Date: 2016-06-07
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2016-3093>CVE-2016-3093</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2016-3093">https://nvd.nist.gov/vuln/detail/CVE-2016-3093</a></p>
<p>Release Date: 2016-06-07</p>
<p>Fix Resolution: org.apache.struts:struts2-core:2.3.28,ognl:ognl:3.0.12</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"Java","groupId":"org.apache.struts","packageName":"struts2-core","packageVersion":"2.3.15","packageFilePaths":["/pom.xml"],"isTransitiveDependency":false,"dependencyTree":"org.apache.struts:struts2-core:2.3.15","isMinimumFixVersionAvailable":true,"minimumFixVersion":"org.apache.struts:struts2-core:2.3.28,ognl:ognl:3.0.12"},{"packageType":"Java","groupId":"ognl","packageName":"ognl","packageVersion":"3.0.6","packageFilePaths":["/pom.xml"],"isTransitiveDependency":true,"dependencyTree":"org.apache.struts:struts2-core:2.3.15;ognl:ognl:3.0.6","isMinimumFixVersionAvailable":true,"minimumFixVersion":"org.apache.struts:struts2-core:2.3.28,ognl:ognl:3.0.12"}],"baseBranches":["main"],"vulnerabilityIdentifier":"CVE-2016-3093","vulnerabilityDetails":"Apache Struts 2.0.0 through 2.3.24.1 does not properly cache method references when used with OGNL before 3.0.12, which allows remote attackers to cause a denial of service (block access to a web site) via unspecified vectors.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2016-3093","cvss3Severity":"medium","cvss3Score":"5.3","cvss3Metrics":{"A":"Low","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}}</REMEDIATE> -->
|
True
|
CVE-2016-3093 (Medium) detected in struts2-core-2.3.15.jar, ognl-3.0.6.jar - ## CVE-2016-3093 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>struts2-core-2.3.15.jar</b>, <b>ognl-3.0.6.jar</b></p></summary>
<p>
<details><summary><b>struts2-core-2.3.15.jar</b></p></summary>
<p>Apache Struts 2</p>
<p>Path to dependency file: Maven_Pom_Demo/pom.xml</p>
<p>Path to vulnerable library: canner/.m2/repository/org/apache/struts/struts2-core/2.3.15/struts2-core-2.3.15.jar</p>
<p>
Dependency Hierarchy:
- :x: **struts2-core-2.3.15.jar** (Vulnerable Library)
</details>
<details><summary><b>ognl-3.0.6.jar</b></p></summary>
<p>OGNL - Object Graph Navigation Library</p>
<p>Library home page: <a href="http://ognl.org">http://ognl.org</a></p>
<p>Path to dependency file: Maven_Pom_Demo/pom.xml</p>
<p>Path to vulnerable library: /home/wss-scanner/.m2/repository/ognl/ognl/3.0.6/ognl-3.0.6.jar</p>
<p>
Dependency Hierarchy:
- struts2-core-2.3.15.jar (Root Library)
- :x: **ognl-3.0.6.jar** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/Galaxy-Software-Service/Maven_Pom_Demo/commit/3774e4b6d3e5f4ad3fa9f69e93f2b07cf1b66027">3774e4b6d3e5f4ad3fa9f69e93f2b07cf1b66027</a></p>
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Apache Struts 2.0.0 through 2.3.24.1 does not properly cache method references when used with OGNL before 3.0.12, which allows remote attackers to cause a denial of service (block access to a web site) via unspecified vectors.
<p>Publish Date: 2016-06-07
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2016-3093>CVE-2016-3093</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2016-3093">https://nvd.nist.gov/vuln/detail/CVE-2016-3093</a></p>
<p>Release Date: 2016-06-07</p>
<p>Fix Resolution: org.apache.struts:struts2-core:2.3.28,ognl:ognl:3.0.12</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"Java","groupId":"org.apache.struts","packageName":"struts2-core","packageVersion":"2.3.15","packageFilePaths":["/pom.xml"],"isTransitiveDependency":false,"dependencyTree":"org.apache.struts:struts2-core:2.3.15","isMinimumFixVersionAvailable":true,"minimumFixVersion":"org.apache.struts:struts2-core:2.3.28,ognl:ognl:3.0.12"},{"packageType":"Java","groupId":"ognl","packageName":"ognl","packageVersion":"3.0.6","packageFilePaths":["/pom.xml"],"isTransitiveDependency":true,"dependencyTree":"org.apache.struts:struts2-core:2.3.15;ognl:ognl:3.0.6","isMinimumFixVersionAvailable":true,"minimumFixVersion":"org.apache.struts:struts2-core:2.3.28,ognl:ognl:3.0.12"}],"baseBranches":["main"],"vulnerabilityIdentifier":"CVE-2016-3093","vulnerabilityDetails":"Apache Struts 2.0.0 through 2.3.24.1 does not properly cache method references when used with OGNL before 3.0.12, which allows remote attackers to cause a denial of service (block access to a web site) via unspecified vectors.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2016-3093","cvss3Severity":"medium","cvss3Score":"5.3","cvss3Metrics":{"A":"Low","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}}</REMEDIATE> -->
|
secu
|
cve medium detected in core jar ognl jar cve medium severity vulnerability vulnerable libraries core jar ognl jar core jar apache struts path to dependency file maven pom demo pom xml path to vulnerable library canner repository org apache struts core core jar dependency hierarchy x core jar vulnerable library ognl jar ognl object graph navigation library library home page a href path to dependency file maven pom demo pom xml path to vulnerable library home wss scanner repository ognl ognl ognl jar dependency hierarchy core jar root library x ognl jar vulnerable library found in head commit a href found in base branch main vulnerability details apache struts through does not properly cache method references when used with ognl before which allows remote attackers to cause a denial of service block access to a web site via unspecified vectors publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact low for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution org apache struts core ognl ognl isopenpronvulnerability true ispackagebased true isdefaultbranch true packages istransitivedependency false dependencytree org apache struts core isminimumfixversionavailable true minimumfixversion org apache struts core ognl ognl packagetype java groupid ognl packagename ognl packageversion packagefilepaths istransitivedependency true dependencytree org apache struts core ognl ognl isminimumfixversionavailable true minimumfixversion org apache struts core ognl ognl basebranches vulnerabilityidentifier cve vulnerabilitydetails apache struts through does not properly cache method references when used with ognl before which allows remote attackers to cause a denial of service block access to a web site via unspecified vectors vulnerabilityurl
| 1
|
268,820
| 28,862,542,949
|
IssuesEvent
|
2023-05-05 00:19:55
|
Carbonable/carbon-protocol
|
https://api.github.com/repos/Carbonable/carbon-protocol
|
reopened
|
Smart Contract - Transfer ownership improvement
|
Type: Security Component: Smart Contract Readiness: To be defineds Complexity: Complex Epic: Launchpad
|
**Description**
---
To secure ownership transfer, we can add a feature to ask the new owner to accept the ownership before processing the transfer.
Feature: [OpenZeppelin!505](https://github.com/OpenZeppelin/cairo-contracts/pull/505)
**Acceptance Criteria**
---
- [ ] Relevant smart contracts adopts the new feature.
|
True
|
Smart Contract - Transfer ownership improvement - **Description**
---
To secure ownership transfer, we can add a feature to ask the new owner to accept the ownership before processing the transfer.
Feature: [OpenZeppelin!505](https://github.com/OpenZeppelin/cairo-contracts/pull/505)
**Acceptance Criteria**
---
- [ ] Relevant smart contracts adopts the new feature.
|
secu
|
smart contract transfer ownership improvement description to secure ownership transfer we can add a feature to ask the new owner to accept the ownership before processing the transfer feature acceptance criteria relevant smart contracts adopts the new feature
| 1
|
221,530
| 24,642,877,896
|
IssuesEvent
|
2022-10-17 12:58:52
|
MValle21/circonus-unified-agent
|
https://api.github.com/repos/MValle21/circonus-unified-agent
|
opened
|
CVE-2021-38561 (High) detected in golang.org/x/text/language-v0.3.5
|
security vulnerability
|
## CVE-2021-38561 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>golang.org/x/text/language-v0.3.5</b></p></summary>
<p>Package language implements BCP 47 language tags and related functionality.</p>
<p>Library home page: <a href="https://proxy.golang.org/golang.org/x/text/@v/v0.3.5.zip">https://proxy.golang.org/golang.org/x/text/@v/v0.3.5.zip</a></p>
<p>
Dependency Hierarchy:
- github.com/circonus-labs/circonus-unified-agent/plugins/inputs/openldap-v0.0.10 (Root Library)
- github.com/circonus-labs/circonus-unified-agent/plugins/inputs-v0.0.10
- github.com/circonus-labs/circonus-unified-agent/plugins/inputs/postgresql_extensible-v0.0.10
- github.com/jackc/pgx/stdlib-v4.11.0
- github.com/Jackc/pgconn-v1.8.1
- golang.org/x/text/secure/precis-75a595aef632b07c6eeaaa805adb6f0f66e4130e
- :x: **golang.org/x/text/language-v0.3.5** (Vulnerable Library)
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Due to improper index calculation, an incorrectly formatted language tag can cause Parse
to panic, due to an out of bounds read. If Parse is used to process untrusted user inputs,
this may be used as a vector for a denial of service attack.
<p>Publish Date: 2021-08-12
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-38561>CVE-2021-38561</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://osv.dev/vulnerability/GO-2021-0113">https://osv.dev/vulnerability/GO-2021-0113</a></p>
<p>Release Date: 2021-08-12</p>
<p>Fix Resolution: v0.3.7</p>
</p>
</details>
<p></p>
|
True
|
CVE-2021-38561 (High) detected in golang.org/x/text/language-v0.3.5 - ## CVE-2021-38561 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>golang.org/x/text/language-v0.3.5</b></p></summary>
<p>Package language implements BCP 47 language tags and related functionality.</p>
<p>Library home page: <a href="https://proxy.golang.org/golang.org/x/text/@v/v0.3.5.zip">https://proxy.golang.org/golang.org/x/text/@v/v0.3.5.zip</a></p>
<p>
Dependency Hierarchy:
- github.com/circonus-labs/circonus-unified-agent/plugins/inputs/openldap-v0.0.10 (Root Library)
- github.com/circonus-labs/circonus-unified-agent/plugins/inputs-v0.0.10
- github.com/circonus-labs/circonus-unified-agent/plugins/inputs/postgresql_extensible-v0.0.10
- github.com/jackc/pgx/stdlib-v4.11.0
- github.com/Jackc/pgconn-v1.8.1
- golang.org/x/text/secure/precis-75a595aef632b07c6eeaaa805adb6f0f66e4130e
- :x: **golang.org/x/text/language-v0.3.5** (Vulnerable Library)
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Due to improper index calculation, an incorrectly formatted language tag can cause Parse
to panic, due to an out of bounds read. If Parse is used to process untrusted user inputs,
this may be used as a vector for a denial of service attack.
<p>Publish Date: 2021-08-12
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-38561>CVE-2021-38561</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://osv.dev/vulnerability/GO-2021-0113">https://osv.dev/vulnerability/GO-2021-0113</a></p>
<p>Release Date: 2021-08-12</p>
<p>Fix Resolution: v0.3.7</p>
</p>
</details>
<p></p>
|
secu
|
cve high detected in golang org x text language cve high severity vulnerability vulnerable library golang org x text language package language implements bcp language tags and related functionality library home page a href dependency hierarchy github com circonus labs circonus unified agent plugins inputs openldap root library github com circonus labs circonus unified agent plugins inputs github com circonus labs circonus unified agent plugins inputs postgresql extensible github com jackc pgx stdlib github com jackc pgconn golang org x text secure precis x golang org x text language vulnerable library found in base branch master vulnerability details due to improper index calculation an incorrectly formatted language tag can cause parse to panic due to an out of bounds read if parse is used to process untrusted user inputs this may be used as a vector for a denial of service attack publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution
| 1
|
337,265
| 24,532,684,138
|
IssuesEvent
|
2022-10-11 17:50:05
|
strangelove-ventures/graz
|
https://api.github.com/repos/strangelove-ventures/graz
|
opened
|
Docs: Leap wallet cannot support suggest chain
|
documentation
|
We need to inform our user, that leap wallet not support suggest chain, in jsdoc and website documentation
|
1.0
|
Docs: Leap wallet cannot support suggest chain - We need to inform our user, that leap wallet not support suggest chain, in jsdoc and website documentation
|
non_secu
|
docs leap wallet cannot support suggest chain we need to inform our user that leap wallet not support suggest chain in jsdoc and website documentation
| 0
|
123,968
| 17,772,422,625
|
IssuesEvent
|
2021-08-30 15:03:52
|
kapseliboi/nuxt-client
|
https://api.github.com/repos/kapseliboi/nuxt-client
|
opened
|
CVE-2021-24033 (Medium) detected in react-dev-utils-9.1.0.tgz
|
security vulnerability
|
## CVE-2021-24033 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>react-dev-utils-9.1.0.tgz</b></p></summary>
<p>Webpack utilities used by Create React App</p>
<p>Library home page: <a href="https://registry.npmjs.org/react-dev-utils/-/react-dev-utils-9.1.0.tgz">https://registry.npmjs.org/react-dev-utils/-/react-dev-utils-9.1.0.tgz</a></p>
<p>Path to dependency file: nuxt-client/package.json</p>
<p>Path to vulnerable library: nuxt-client/node_modules/react-dev-utils/package.json</p>
<p>
Dependency Hierarchy:
- vue-5.3.19.tgz (Root Library)
- core-5.3.19.tgz
- :x: **react-dev-utils-9.1.0.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/kapseliboi/nuxt-client/commit/554beeea1c9adbc89fa96b47029ccd9d81aa99b1">554beeea1c9adbc89fa96b47029ccd9d81aa99b1</a></p>
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
react-dev-utils prior to v11.0.4 exposes a function, getProcessForPort, where an input argument is concatenated into a command string to be executed. This function is typically used from react-scripts (in Create React App projects), where the usage is safe. Only when this function is manually invoked with user-provided values (ie: by custom code) is there the potential for command injection. If you're consuming it from react-scripts then this issue does not affect you.
<p>Publish Date: 2021-03-09
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-24033>CVE-2021-24033</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.6</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.facebook.com/security/advisories/cve-2021-24033">https://www.facebook.com/security/advisories/cve-2021-24033</a></p>
<p>Release Date: 2021-03-09</p>
<p>Fix Resolution: react-dev-utils-11.0.4</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2021-24033 (Medium) detected in react-dev-utils-9.1.0.tgz - ## CVE-2021-24033 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>react-dev-utils-9.1.0.tgz</b></p></summary>
<p>Webpack utilities used by Create React App</p>
<p>Library home page: <a href="https://registry.npmjs.org/react-dev-utils/-/react-dev-utils-9.1.0.tgz">https://registry.npmjs.org/react-dev-utils/-/react-dev-utils-9.1.0.tgz</a></p>
<p>Path to dependency file: nuxt-client/package.json</p>
<p>Path to vulnerable library: nuxt-client/node_modules/react-dev-utils/package.json</p>
<p>
Dependency Hierarchy:
- vue-5.3.19.tgz (Root Library)
- core-5.3.19.tgz
- :x: **react-dev-utils-9.1.0.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/kapseliboi/nuxt-client/commit/554beeea1c9adbc89fa96b47029ccd9d81aa99b1">554beeea1c9adbc89fa96b47029ccd9d81aa99b1</a></p>
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
react-dev-utils prior to v11.0.4 exposes a function, getProcessForPort, where an input argument is concatenated into a command string to be executed. This function is typically used from react-scripts (in Create React App projects), where the usage is safe. Only when this function is manually invoked with user-provided values (ie: by custom code) is there the potential for command injection. If you're consuming it from react-scripts then this issue does not affect you.
<p>Publish Date: 2021-03-09
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-24033>CVE-2021-24033</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.6</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.facebook.com/security/advisories/cve-2021-24033">https://www.facebook.com/security/advisories/cve-2021-24033</a></p>
<p>Release Date: 2021-03-09</p>
<p>Fix Resolution: react-dev-utils-11.0.4</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve medium detected in react dev utils tgz cve medium severity vulnerability vulnerable library react dev utils tgz webpack utilities used by create react app library home page a href path to dependency file nuxt client package json path to vulnerable library nuxt client node modules react dev utils package json dependency hierarchy vue tgz root library core tgz x react dev utils tgz vulnerable library found in head commit a href found in base branch main vulnerability details react dev utils prior to exposes a function getprocessforport where an input argument is concatenated into a command string to be executed this function is typically used from react scripts in create react app projects where the usage is safe only when this function is manually invoked with user provided values ie by custom code is there the potential for command injection if you re consuming it from react scripts then this issue does not affect you publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required none user interaction none scope unchanged impact metrics confidentiality impact low integrity impact low availability impact low for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution react dev utils step up your open source security game with whitesource
| 1
|
88,456
| 25,408,874,232
|
IssuesEvent
|
2022-11-22 17:14:31
|
mautic/mautic
|
https://api.github.com/repos/mautic/mautic
|
closed
|
Reproducing <!doctype html> on every save of the email
|
T1 bug ready-to-test builder-legacy stale
|
[//]: # ( Invisible comment:
IIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIII
Before you create the issue:
IIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIII
Search for similar report among other reported issues.
Learn how to troubleshoot at https://www.mautic.org/docs/en/tips/troubleshooting.html
Use drag&drop to attach images or other files )
## Bug Description
The more details the better...
| Q | A
| --- | ---
| Mautic version | 3.2.1
| PHP version | 7.3.23
| Browser | Google Chrome
### Steps to reproduce
1. Open code mode email
2. Save the email
3. Every save will add exactly 1 more <!doctype html> tag to the begginig of the email
4. You will see the reproducing <!doctype html> tags in the beginning of the email.
### Log errors
No logs, here is the screenshot.
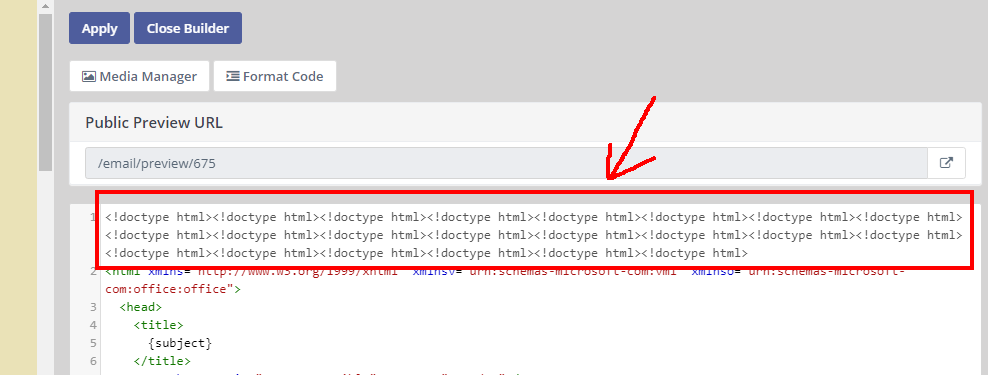
The issue is appeared with Mauitc 3.1.x and still exists with Mauitc 3.2.1
Pull https://github.com/mautic/mautic/pull/669 handled the opposite of this issue.
[//]: # ( Invisible comment:
Please check for related errors in the latest log file in [mautic root]/app/log/ and/or the web server's logs and post them here. Be sure to remove sensitive information if applicable. )
<bountysource-plugin>
---
Want to back this issue? **[Post a bounty on it!](https://app.bountysource.com/issues/95192972-reproducing-doctype-html-on-every-save-of-the-email?utm_campaign=plugin&utm_content=tracker%2F5355074&utm_medium=issues&utm_source=github)** We accept bounties via [Bountysource](https://app.bountysource.com/?utm_campaign=plugin&utm_content=tracker%2F5355074&utm_medium=issues&utm_source=github).
</bountysource-plugin>
|
1.0
|
Reproducing <!doctype html> on every save of the email - [//]: # ( Invisible comment:
IIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIII
Before you create the issue:
IIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIIII
Search for similar report among other reported issues.
Learn how to troubleshoot at https://www.mautic.org/docs/en/tips/troubleshooting.html
Use drag&drop to attach images or other files )
## Bug Description
The more details the better...
| Q | A
| --- | ---
| Mautic version | 3.2.1
| PHP version | 7.3.23
| Browser | Google Chrome
### Steps to reproduce
1. Open code mode email
2. Save the email
3. Every save will add exactly 1 more <!doctype html> tag to the begginig of the email
4. You will see the reproducing <!doctype html> tags in the beginning of the email.
### Log errors
No logs, here is the screenshot.

The issue is appeared with Mauitc 3.1.x and still exists with Mauitc 3.2.1
Pull https://github.com/mautic/mautic/pull/669 handled the opposite of this issue.
[//]: # ( Invisible comment:
Please check for related errors in the latest log file in [mautic root]/app/log/ and/or the web server's logs and post them here. Be sure to remove sensitive information if applicable. )
<bountysource-plugin>
---
Want to back this issue? **[Post a bounty on it!](https://app.bountysource.com/issues/95192972-reproducing-doctype-html-on-every-save-of-the-email?utm_campaign=plugin&utm_content=tracker%2F5355074&utm_medium=issues&utm_source=github)** We accept bounties via [Bountysource](https://app.bountysource.com/?utm_campaign=plugin&utm_content=tracker%2F5355074&utm_medium=issues&utm_source=github).
</bountysource-plugin>
|
non_secu
|
reproducing on every save of the email invisible comment iiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiii before you create the issue iiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiii search for similar report among other reported issues learn how to troubleshoot at use drag drop to attach images or other files bug description the more details the better q a mautic version php version browser google chrome steps to reproduce open code mode email save the email every save will add exactly more tag to the begginig of the email you will see the reproducing tags in the beginning of the email log errors no logs here is the screenshot the issue is appeared with mauitc x and still exists with mauitc pull handled the opposite of this issue invisible comment please check for related errors in the latest log file in app log and or the web server s logs and post them here be sure to remove sensitive information if applicable want to back this issue we accept bounties via
| 0
|
66,297
| 12,745,084,169
|
IssuesEvent
|
2020-06-26 13:40:10
|
AurityLab/graphql-kotlin-toolkit
|
https://api.github.com/repos/AurityLab/graphql-kotlin-toolkit
|
closed
|
Usage of existing enums
|
enhancement module: codegen
|
Sometimes there are already existing enums for the ones used in the GraphQL schema.
The code generator will currently always generate a new enum, which matches the one defined in the schema.
This behavior sometimes results in unnecessarily ugly code, therefore there should be an easier way to do that.
Possible fixes:
- Allow `kRepresentation` on Enums to directly use the existing enum.
- Is there a way to guarantee that the given enum contains the required values? (Would break type safety and runtime otherwise)
|
1.0
|
Usage of existing enums - Sometimes there are already existing enums for the ones used in the GraphQL schema.
The code generator will currently always generate a new enum, which matches the one defined in the schema.
This behavior sometimes results in unnecessarily ugly code, therefore there should be an easier way to do that.
Possible fixes:
- Allow `kRepresentation` on Enums to directly use the existing enum.
- Is there a way to guarantee that the given enum contains the required values? (Would break type safety and runtime otherwise)
|
non_secu
|
usage of existing enums sometimes there are already existing enums for the ones used in the graphql schema the code generator will currently always generate a new enum which matches the one defined in the schema this behavior sometimes results in unnecessarily ugly code therefore there should be an easier way to do that possible fixes allow krepresentation on enums to directly use the existing enum is there a way to guarantee that the given enum contains the required values would break type safety and runtime otherwise
| 0
|
684,935
| 23,438,791,448
|
IssuesEvent
|
2022-08-15 12:59:16
|
flant/negentropy
|
https://api.github.com/repos/flant/negentropy
|
opened
|
documenting
|
area/docs priority/backlog source/internal-client type/epic
|
### Usecase. Why is this important?
System should have documentation for users
### Proposed Solution
1) Repeat deckhouse autodocumenatation:
- deploy components
- write scripts
- implement ci/cd
2) Add needed information into code.
3) Organise third party checking readability and undestandability
### Additional Information
No response
|
1.0
|
documenting - ### Usecase. Why is this important?
System should have documentation for users
### Proposed Solution
1) Repeat deckhouse autodocumenatation:
- deploy components
- write scripts
- implement ci/cd
2) Add needed information into code.
3) Organise third party checking readability and undestandability
### Additional Information
No response
|
non_secu
|
documenting usecase why is this important system should have documentation for users proposed solution repeat deckhouse autodocumenatation deploy components write scripts implement ci cd add needed information into code organise third party checking readability and undestandability additional information no response
| 0
|
210,988
| 23,778,951,928
|
IssuesEvent
|
2022-09-02 01:06:33
|
Vali00/serverless-full-stack-apps-azure-sql
|
https://api.github.com/repos/Vali00/serverless-full-stack-apps-azure-sql
|
closed
|
CVE-2017-0247 (High) detected in system.net.http.4.3.0.nupkg - autoclosed
|
security vulnerability
|
## CVE-2017-0247 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>system.net.http.4.3.0.nupkg</b></p></summary>
<p>Provides a programming interface for modern HTTP applications, including HTTP client components that...</p>
<p>Library home page: <a href="https://api.nuget.org/packages/system.net.http.4.3.0.nupkg">https://api.nuget.org/packages/system.net.http.4.3.0.nupkg</a></p>
<p>Path to dependency file: /azure-function/dotnet/GetBusData.csproj</p>
<p>Path to vulnerable library: /usr/share/dotnet/sdk/NuGetFallbackFolder/system.net.http/4.3.0/system.net.http.4.3.0.nupkg</p>
<p>
Dependency Hierarchy:
- microsoft.azure.webjobs.extensions.storage.3.0.10.nupkg (Root Library)
- windowsazure.storage.9.3.1.nupkg
- netstandard.library.1.6.1.nupkg
- :x: **system.net.http.4.3.0.nupkg** (Vulnerable Library)
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
A denial of service vulnerability exists when the ASP.NET Core fails to properly validate web requests. NOTE: Microsoft has not commented on third-party claims that the issue is that the TextEncoder.EncodeCore function in the System.Text.Encodings.Web package in ASP.NET Core Mvc before 1.0.4 and 1.1.x before 1.1.3 allows remote attackers to cause a denial of service by leveraging failure to properly calculate the length of 4-byte characters in the Unicode Non-Character range.
<p>Publish Date: 2017-05-12
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2017-0247>CVE-2017-0247</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: High
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2017-05-12</p>
<p>Fix Resolution: System.Text.Encodings.Web - 4.0.1,4.3.1;System.Net.Http - 4.1.2,4.3.2;System.Net.Http.WinHttpHandler - 4.0.2,4.5.4;System.Net.Security - 4.0.1,4.3.1;System.Net.WebSockets.Client - 4.0.1,4.3.1;Microsoft.AspNetCore.Mvc - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.Core - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.Abstractions - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.ApiExplorer - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.Cors - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.DataAnnotations - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.Formatters.Json - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.Formatters.Xml - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.Localization - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.Razor.Host - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.Razor - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.TagHelpers - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.ViewFeatures - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.WebApiCompatShim - 1.0.4,1.1.3</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2017-0247 (High) detected in system.net.http.4.3.0.nupkg - autoclosed - ## CVE-2017-0247 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>system.net.http.4.3.0.nupkg</b></p></summary>
<p>Provides a programming interface for modern HTTP applications, including HTTP client components that...</p>
<p>Library home page: <a href="https://api.nuget.org/packages/system.net.http.4.3.0.nupkg">https://api.nuget.org/packages/system.net.http.4.3.0.nupkg</a></p>
<p>Path to dependency file: /azure-function/dotnet/GetBusData.csproj</p>
<p>Path to vulnerable library: /usr/share/dotnet/sdk/NuGetFallbackFolder/system.net.http/4.3.0/system.net.http.4.3.0.nupkg</p>
<p>
Dependency Hierarchy:
- microsoft.azure.webjobs.extensions.storage.3.0.10.nupkg (Root Library)
- windowsazure.storage.9.3.1.nupkg
- netstandard.library.1.6.1.nupkg
- :x: **system.net.http.4.3.0.nupkg** (Vulnerable Library)
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
A denial of service vulnerability exists when the ASP.NET Core fails to properly validate web requests. NOTE: Microsoft has not commented on third-party claims that the issue is that the TextEncoder.EncodeCore function in the System.Text.Encodings.Web package in ASP.NET Core Mvc before 1.0.4 and 1.1.x before 1.1.3 allows remote attackers to cause a denial of service by leveraging failure to properly calculate the length of 4-byte characters in the Unicode Non-Character range.
<p>Publish Date: 2017-05-12
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2017-0247>CVE-2017-0247</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: High
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Release Date: 2017-05-12</p>
<p>Fix Resolution: System.Text.Encodings.Web - 4.0.1,4.3.1;System.Net.Http - 4.1.2,4.3.2;System.Net.Http.WinHttpHandler - 4.0.2,4.5.4;System.Net.Security - 4.0.1,4.3.1;System.Net.WebSockets.Client - 4.0.1,4.3.1;Microsoft.AspNetCore.Mvc - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.Core - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.Abstractions - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.ApiExplorer - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.Cors - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.DataAnnotations - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.Formatters.Json - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.Formatters.Xml - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.Localization - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.Razor.Host - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.Razor - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.TagHelpers - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.ViewFeatures - 1.0.4,1.1.3;Microsoft.AspNetCore.Mvc.WebApiCompatShim - 1.0.4,1.1.3</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve high detected in system net http nupkg autoclosed cve high severity vulnerability vulnerable library system net http nupkg provides a programming interface for modern http applications including http client components that library home page a href path to dependency file azure function dotnet getbusdata csproj path to vulnerable library usr share dotnet sdk nugetfallbackfolder system net http system net http nupkg dependency hierarchy microsoft azure webjobs extensions storage nupkg root library windowsazure storage nupkg netstandard library nupkg x system net http nupkg vulnerable library found in base branch main vulnerability details a denial of service vulnerability exists when the asp net core fails to properly validate web requests note microsoft has not commented on third party claims that the issue is that the textencoder encodecore function in the system text encodings web package in asp net core mvc before and x before allows remote attackers to cause a denial of service by leveraging failure to properly calculate the length of byte characters in the unicode non character range publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact high availability impact none for more information on scores click a href suggested fix type upgrade version release date fix resolution system text encodings web system net http system net http winhttphandler system net security system net websockets client microsoft aspnetcore mvc microsoft aspnetcore mvc core microsoft aspnetcore mvc abstractions microsoft aspnetcore mvc apiexplorer microsoft aspnetcore mvc cors microsoft aspnetcore mvc dataannotations microsoft aspnetcore mvc formatters json microsoft aspnetcore mvc formatters xml microsoft aspnetcore mvc localization microsoft aspnetcore mvc razor host microsoft aspnetcore mvc razor microsoft aspnetcore mvc taghelpers microsoft aspnetcore mvc viewfeatures microsoft aspnetcore mvc webapicompatshim step up your open source security game with mend
| 1
|
167,590
| 26,518,272,993
|
IssuesEvent
|
2023-01-18 23:00:12
|
flutter/flutter
|
https://api.github.com/repos/flutter/flutter
|
closed
|
App bar leading theme overrides should apply to all widgets with IconButton children
|
f: material design
|
Relates to https://github.com/flutter/flutter/pull/118216.
This fix allowed users to supply values to `appBarTheme.iconTheme` and `appBarTheme.actionsIconTheme`, which would override any `theme.iconButtonTheme` also set in the theme.
However, this fix only applies to widgets that are directly `IconButtons`. If, for example, our app bar was defined with these theme overrides:
```
return Theme(
data: theme.copyWith(
iconButtonTheme: IconButtonThemeData(
style: IconButton.styleFrom(
foregroundColor: Colors.yellow,
),
),
appBarTheme: theme.appBarTheme.copyWith(
actionsIconTheme: actionTheme!.copyWith(color: Colors.blue),
iconTheme: leadingTheme!.copyWith(color: Colors.blue),
),
),
child: Scaffold(
appBar: AppBar(
actions: [
IconButton(
icon: Icon(Icons.favorite),
onPressed: () {},
),
BackButton(), // this takes actionsIconTheme color value as expected
],
leading: BackButton(), // this takes iconButtonTheme color value, not iconTheme
title: Text('title'),
),
body: body,
```
We get this result:
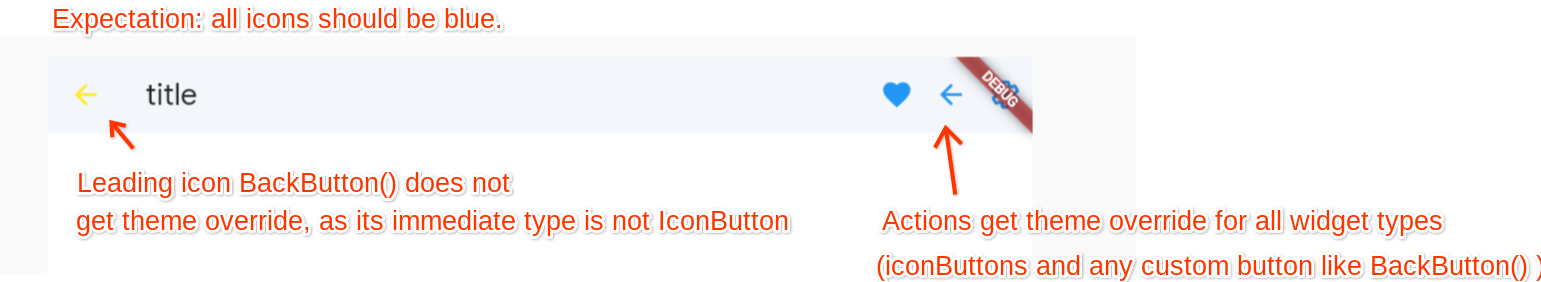
This is due to `app_bar.dart` checking for an exact widget type of `IconButton` before it applies the local theme override. So, it doesn't get applied to widgets like `BackButton`, or any other custom widget which contains an icon button.
|
1.0
|
App bar leading theme overrides should apply to all widgets with IconButton children - Relates to https://github.com/flutter/flutter/pull/118216.
This fix allowed users to supply values to `appBarTheme.iconTheme` and `appBarTheme.actionsIconTheme`, which would override any `theme.iconButtonTheme` also set in the theme.
However, this fix only applies to widgets that are directly `IconButtons`. If, for example, our app bar was defined with these theme overrides:
```
return Theme(
data: theme.copyWith(
iconButtonTheme: IconButtonThemeData(
style: IconButton.styleFrom(
foregroundColor: Colors.yellow,
),
),
appBarTheme: theme.appBarTheme.copyWith(
actionsIconTheme: actionTheme!.copyWith(color: Colors.blue),
iconTheme: leadingTheme!.copyWith(color: Colors.blue),
),
),
child: Scaffold(
appBar: AppBar(
actions: [
IconButton(
icon: Icon(Icons.favorite),
onPressed: () {},
),
BackButton(), // this takes actionsIconTheme color value as expected
],
leading: BackButton(), // this takes iconButtonTheme color value, not iconTheme
title: Text('title'),
),
body: body,
```
We get this result:

This is due to `app_bar.dart` checking for an exact widget type of `IconButton` before it applies the local theme override. So, it doesn't get applied to widgets like `BackButton`, or any other custom widget which contains an icon button.
|
non_secu
|
app bar leading theme overrides should apply to all widgets with iconbutton children relates to this fix allowed users to supply values to appbartheme icontheme and appbartheme actionsicontheme which would override any theme iconbuttontheme also set in the theme however this fix only applies to widgets that are directly iconbuttons if for example our app bar was defined with these theme overrides return theme data theme copywith iconbuttontheme iconbuttonthemedata style iconbutton stylefrom foregroundcolor colors yellow appbartheme theme appbartheme copywith actionsicontheme actiontheme copywith color colors blue icontheme leadingtheme copywith color colors blue child scaffold appbar appbar actions iconbutton icon icon icons favorite onpressed backbutton this takes actionsicontheme color value as expected leading backbutton this takes iconbuttontheme color value not icontheme title text title body body we get this result this is due to app bar dart checking for an exact widget type of iconbutton before it applies the local theme override so it doesn t get applied to widgets like backbutton or any other custom widget which contains an icon button
| 0
|
204,692
| 23,272,119,355
|
IssuesEvent
|
2022-08-05 01:05:06
|
snykiotcubedev/reactos-0.4.13-release
|
https://api.github.com/repos/snykiotcubedev/reactos-0.4.13-release
|
opened
|
CVE-2016-3709 (Medium) detected in reactosReactOS-0.4.13-release-28-g5724391-src
|
security vulnerability
|
## CVE-2016-3709 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>reactosReactOS-0.4.13-release-28-g5724391-src</b></p></summary>
<p>
<p>An operating system based on the best Windows NT design principles</p>
<p>Library home page: <a href=https://sourceforge.net/projects/reactos/>https://sourceforge.net/projects/reactos/</a></p>
<p>Found in HEAD commit: <a href="https://github.com/snykiotcubedev/reactos-0.4.13-release/commit/53d912968350dc9f53d47b0479a18abff1adc0e0">53d912968350dc9f53d47b0479a18abff1adc0e0</a></p>
<p>Found in base branch: <b>main</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (2)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/sdk/lib/3rdparty/libxml2/HTMLtree.c</b>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/sdk/lib/3rdparty/libxml2/HTMLtree.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Possible cross-site scripting vulnerability in libxml after commit 960f0e2.
<p>Publish Date: 2022-07-28
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2016-3709>CVE-2016-3709</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.4</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: Low
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2016-3709">https://nvd.nist.gov/vuln/detail/CVE-2016-3709</a></p>
<p>Release Date: 2022-07-28</p>
<p>Fix Resolution: gettext - 0.20.2;libxml2 - 2.9.12</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2016-3709 (Medium) detected in reactosReactOS-0.4.13-release-28-g5724391-src - ## CVE-2016-3709 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>reactosReactOS-0.4.13-release-28-g5724391-src</b></p></summary>
<p>
<p>An operating system based on the best Windows NT design principles</p>
<p>Library home page: <a href=https://sourceforge.net/projects/reactos/>https://sourceforge.net/projects/reactos/</a></p>
<p>Found in HEAD commit: <a href="https://github.com/snykiotcubedev/reactos-0.4.13-release/commit/53d912968350dc9f53d47b0479a18abff1adc0e0">53d912968350dc9f53d47b0479a18abff1adc0e0</a></p>
<p>Found in base branch: <b>main</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (2)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/sdk/lib/3rdparty/libxml2/HTMLtree.c</b>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/sdk/lib/3rdparty/libxml2/HTMLtree.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Possible cross-site scripting vulnerability in libxml after commit 960f0e2.
<p>Publish Date: 2022-07-28
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2016-3709>CVE-2016-3709</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.4</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: Low
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2016-3709">https://nvd.nist.gov/vuln/detail/CVE-2016-3709</a></p>
<p>Release Date: 2022-07-28</p>
<p>Fix Resolution: gettext - 0.20.2;libxml2 - 2.9.12</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve medium detected in reactosreactos release src cve medium severity vulnerability vulnerable library reactosreactos release src an operating system based on the best windows nt design principles library home page a href found in head commit a href found in base branch main vulnerable source files sdk lib htmltree c sdk lib htmltree c vulnerability details possible cross site scripting vulnerability in libxml after commit publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required low user interaction none scope unchanged impact metrics confidentiality impact none integrity impact low availability impact low for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution gettext step up your open source security game with mend
| 1
|
123,720
| 17,772,304,356
|
IssuesEvent
|
2021-08-30 14:57:03
|
kapseliboi/platform-status
|
https://api.github.com/repos/kapseliboi/platform-status
|
opened
|
CVE-2020-7656 (Medium) detected in jquery-1.7.1.min.js
|
security vulnerability
|
## CVE-2020-7656 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jquery-1.7.1.min.js</b></p></summary>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/1.7.1/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/1.7.1/jquery.min.js</a></p>
<p>Path to dependency file: platform-status/node_modules/vm-browserify/example/run/index.html</p>
<p>Path to vulnerable library: /node_modules/vm-browserify/example/run/index.html</p>
<p>
Dependency Hierarchy:
- :x: **jquery-1.7.1.min.js** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/kapseliboi/platform-status/commit/f1843ccb4f9fa8cac219c196c9bcceb734286e98">f1843ccb4f9fa8cac219c196c9bcceb734286e98</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
jquery prior to 1.9.0 allows Cross-site Scripting attacks via the load method. The load method fails to recognize and remove "<script>" HTML tags that contain a whitespace character, i.e: "</script >", which results in the enclosed script logic to be executed.
<p>Publish Date: 2020-05-19
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-7656>CVE-2020-7656</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/advisories/GHSA-q4m3-2j7h-f7xw">https://github.com/advisories/GHSA-q4m3-2j7h-f7xw</a></p>
<p>Release Date: 2020-05-28</p>
<p>Fix Resolution: jquery - 1.9.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2020-7656 (Medium) detected in jquery-1.7.1.min.js - ## CVE-2020-7656 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jquery-1.7.1.min.js</b></p></summary>
<p>JavaScript library for DOM operations</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/jquery/1.7.1/jquery.min.js">https://cdnjs.cloudflare.com/ajax/libs/jquery/1.7.1/jquery.min.js</a></p>
<p>Path to dependency file: platform-status/node_modules/vm-browserify/example/run/index.html</p>
<p>Path to vulnerable library: /node_modules/vm-browserify/example/run/index.html</p>
<p>
Dependency Hierarchy:
- :x: **jquery-1.7.1.min.js** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/kapseliboi/platform-status/commit/f1843ccb4f9fa8cac219c196c9bcceb734286e98">f1843ccb4f9fa8cac219c196c9bcceb734286e98</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
jquery prior to 1.9.0 allows Cross-site Scripting attacks via the load method. The load method fails to recognize and remove "<script>" HTML tags that contain a whitespace character, i.e: "</script >", which results in the enclosed script logic to be executed.
<p>Publish Date: 2020-05-19
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-7656>CVE-2020-7656</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/advisories/GHSA-q4m3-2j7h-f7xw">https://github.com/advisories/GHSA-q4m3-2j7h-f7xw</a></p>
<p>Release Date: 2020-05-28</p>
<p>Fix Resolution: jquery - 1.9.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve medium detected in jquery min js cve medium severity vulnerability vulnerable library jquery min js javascript library for dom operations library home page a href path to dependency file platform status node modules vm browserify example run index html path to vulnerable library node modules vm browserify example run index html dependency hierarchy x jquery min js vulnerable library found in head commit a href found in base branch master vulnerability details jquery prior to allows cross site scripting attacks via the load method the load method fails to recognize and remove html tags that contain a whitespace character i e which results in the enclosed script logic to be executed publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope changed impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution jquery step up your open source security game with whitesource
| 1
|
24,467
| 12,302,098,557
|
IssuesEvent
|
2020-05-11 16:24:34
|
golang/go
|
https://api.github.com/repos/golang/go
|
closed
|
cmd/compile: optimize division for positive integers
|
NeedsInvestigation Performance
|
<!-- Please answer these questions before submitting your issue. Thanks! -->
### What version of Go are you using (`go version`)?
go version go1.13.1 windows/amd64
### Does this issue reproduce with the latest release?
yes
### What did you do?
~~~go
func Indent(width int) string {
const tabsAndSpaces = "\t\t\t\t\t\t\t\t\t "
middle := len(tabsAndSpaces) - 7
if width >= 0 && width <= 8*middle+7 {
start := middle - width/8
end := middle + width%8
return tabsAndSpaces[start:end]
}
return strings.Repeat("\t", width/8) + " "[:width%8]
}
~~~
### What did you expect to see?
Since the variable `width` has bounds checks and is thus guaranteed to be positive, the generated code omits the extra instructions for negative numbers.
In general, I prefer to write arithmetic expressions in my code instead of bit manipulations because the expressions `width/8` and `width%8` pair up nicely. In contrast, `width>>3` and `width&7` requires more thought.
### What did you see instead?
~~~text
util.go:7 MOVQ BX, SI
util.go:7 SARQ $0x3f, BX
util.go:7 SHRQ $0x3d, BX
util.go:7 ADDQ SI, BX
util.go:7 SARQ $0x3, BX
util.go:8 MOVQ BX, DI
util.go:8 SHLQ $0x3, BX
util.go:8 SUBQ BX, SI
util.go:8 LEAQ 0x9(SI), CX
~~~
The `SARQ` and `SHRQ` are not necessary here.
|
True
|
cmd/compile: optimize division for positive integers - <!-- Please answer these questions before submitting your issue. Thanks! -->
### What version of Go are you using (`go version`)?
go version go1.13.1 windows/amd64
### Does this issue reproduce with the latest release?
yes
### What did you do?
~~~go
func Indent(width int) string {
const tabsAndSpaces = "\t\t\t\t\t\t\t\t\t "
middle := len(tabsAndSpaces) - 7
if width >= 0 && width <= 8*middle+7 {
start := middle - width/8
end := middle + width%8
return tabsAndSpaces[start:end]
}
return strings.Repeat("\t", width/8) + " "[:width%8]
}
~~~
### What did you expect to see?
Since the variable `width` has bounds checks and is thus guaranteed to be positive, the generated code omits the extra instructions for negative numbers.
In general, I prefer to write arithmetic expressions in my code instead of bit manipulations because the expressions `width/8` and `width%8` pair up nicely. In contrast, `width>>3` and `width&7` requires more thought.
### What did you see instead?
~~~text
util.go:7 MOVQ BX, SI
util.go:7 SARQ $0x3f, BX
util.go:7 SHRQ $0x3d, BX
util.go:7 ADDQ SI, BX
util.go:7 SARQ $0x3, BX
util.go:8 MOVQ BX, DI
util.go:8 SHLQ $0x3, BX
util.go:8 SUBQ BX, SI
util.go:8 LEAQ 0x9(SI), CX
~~~
The `SARQ` and `SHRQ` are not necessary here.
|
non_secu
|
cmd compile optimize division for positive integers what version of go are you using go version go version windows does this issue reproduce with the latest release yes what did you do go func indent width int string const tabsandspaces t t t t t t t t t middle len tabsandspaces if width width middle start middle width end middle width return tabsandspaces return strings repeat t width what did you expect to see since the variable width has bounds checks and is thus guaranteed to be positive the generated code omits the extra instructions for negative numbers in general i prefer to write arithmetic expressions in my code instead of bit manipulations because the expressions width and width pair up nicely in contrast width and width requires more thought what did you see instead text util go movq bx si util go sarq bx util go shrq bx util go addq si bx util go sarq bx util go movq bx di util go shlq bx util go subq bx si util go leaq si cx the sarq and shrq are not necessary here
| 0
|
83,008
| 15,683,138,024
|
IssuesEvent
|
2021-03-25 08:22:27
|
raindigi/site-preview
|
https://api.github.com/repos/raindigi/site-preview
|
opened
|
CVE-2020-36048 (High) detected in engine.io-3.5.0.tgz
|
security vulnerability
|
## CVE-2020-36048 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>engine.io-3.5.0.tgz</b></p></summary>
<p>The realtime engine behind Socket.IO. Provides the foundation of a bidirectional connection between client and server</p>
<p>Library home page: <a href="https://registry.npmjs.org/engine.io/-/engine.io-3.5.0.tgz">https://registry.npmjs.org/engine.io/-/engine.io-3.5.0.tgz</a></p>
<p>Path to dependency file: site-preview/package.json</p>
<p>Path to vulnerable library: site-preview/node_modules/engine.io/package.json</p>
<p>
Dependency Hierarchy:
- gatsby-2.0.0.tgz (Root Library)
- socket.io-2.4.1.tgz
- :x: **engine.io-3.5.0.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/raindigi/site-preview/commit/571a3f327188e9f4e3fce2de73330afa0c4ababe">571a3f327188e9f4e3fce2de73330afa0c4ababe</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Engine.IO before 4.0.0 allows attackers to cause a denial of service (resource consumption) via a POST request to the long polling transport.
<p>Publish Date: 2021-01-08
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-36048>CVE-2020-36048</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-36048">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-36048</a></p>
<p>Release Date: 2021-01-08</p>
<p>Fix Resolution: engine.io - 4.0.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2020-36048 (High) detected in engine.io-3.5.0.tgz - ## CVE-2020-36048 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>engine.io-3.5.0.tgz</b></p></summary>
<p>The realtime engine behind Socket.IO. Provides the foundation of a bidirectional connection between client and server</p>
<p>Library home page: <a href="https://registry.npmjs.org/engine.io/-/engine.io-3.5.0.tgz">https://registry.npmjs.org/engine.io/-/engine.io-3.5.0.tgz</a></p>
<p>Path to dependency file: site-preview/package.json</p>
<p>Path to vulnerable library: site-preview/node_modules/engine.io/package.json</p>
<p>
Dependency Hierarchy:
- gatsby-2.0.0.tgz (Root Library)
- socket.io-2.4.1.tgz
- :x: **engine.io-3.5.0.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/raindigi/site-preview/commit/571a3f327188e9f4e3fce2de73330afa0c4ababe">571a3f327188e9f4e3fce2de73330afa0c4ababe</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Engine.IO before 4.0.0 allows attackers to cause a denial of service (resource consumption) via a POST request to the long polling transport.
<p>Publish Date: 2021-01-08
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-36048>CVE-2020-36048</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-36048">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-36048</a></p>
<p>Release Date: 2021-01-08</p>
<p>Fix Resolution: engine.io - 4.0.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve high detected in engine io tgz cve high severity vulnerability vulnerable library engine io tgz the realtime engine behind socket io provides the foundation of a bidirectional connection between client and server library home page a href path to dependency file site preview package json path to vulnerable library site preview node modules engine io package json dependency hierarchy gatsby tgz root library socket io tgz x engine io tgz vulnerable library found in head commit a href vulnerability details engine io before allows attackers to cause a denial of service resource consumption via a post request to the long polling transport publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution engine io step up your open source security game with whitesource
| 1
|
243,683
| 26,287,391,090
|
IssuesEvent
|
2023-01-08 01:04:36
|
kaidisn/twilio-video.js
|
https://api.github.com/repos/kaidisn/twilio-video.js
|
opened
|
CVE-2022-0536 (Medium) detected in follow-redirects-1.14.5.tgz
|
security vulnerability
|
## CVE-2022-0536 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>follow-redirects-1.14.5.tgz</b></p></summary>
<p>HTTP and HTTPS modules that follow redirects.</p>
<p>Library home page: <a href="https://registry.npmjs.org/follow-redirects/-/follow-redirects-1.14.5.tgz">https://registry.npmjs.org/follow-redirects/-/follow-redirects-1.14.5.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/follow-redirects/package.json</p>
<p>
Dependency Hierarchy:
- karma-5.2.3.tgz (Root Library)
- http-proxy-1.18.1.tgz
- :x: **follow-redirects-1.14.5.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/kaidisn/twilio-video.js/commit/186f901ae9b3b0fb26f7e79e6a301ab7109c6f03">186f901ae9b3b0fb26f7e79e6a301ab7109c6f03</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Exposure of Sensitive Information to an Unauthorized Actor in NPM follow-redirects prior to 1.14.8.
<p>Publish Date: 2022-02-09
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2022-0536>CVE-2022-0536</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.9</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: None
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0536">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0536</a></p>
<p>Release Date: 2022-02-09</p>
<p>Fix Resolution (follow-redirects): 1.14.8</p>
<p>Direct dependency fix Resolution (karma): 6.0.0</p>
</p>
</details>
<p></p>
***
:rescue_worker_helmet: Automatic Remediation is available for this issue
|
True
|
CVE-2022-0536 (Medium) detected in follow-redirects-1.14.5.tgz - ## CVE-2022-0536 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>follow-redirects-1.14.5.tgz</b></p></summary>
<p>HTTP and HTTPS modules that follow redirects.</p>
<p>Library home page: <a href="https://registry.npmjs.org/follow-redirects/-/follow-redirects-1.14.5.tgz">https://registry.npmjs.org/follow-redirects/-/follow-redirects-1.14.5.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/follow-redirects/package.json</p>
<p>
Dependency Hierarchy:
- karma-5.2.3.tgz (Root Library)
- http-proxy-1.18.1.tgz
- :x: **follow-redirects-1.14.5.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/kaidisn/twilio-video.js/commit/186f901ae9b3b0fb26f7e79e6a301ab7109c6f03">186f901ae9b3b0fb26f7e79e6a301ab7109c6f03</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Exposure of Sensitive Information to an Unauthorized Actor in NPM follow-redirects prior to 1.14.8.
<p>Publish Date: 2022-02-09
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2022-0536>CVE-2022-0536</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.9</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: None
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0536">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0536</a></p>
<p>Release Date: 2022-02-09</p>
<p>Fix Resolution (follow-redirects): 1.14.8</p>
<p>Direct dependency fix Resolution (karma): 6.0.0</p>
</p>
</details>
<p></p>
***
:rescue_worker_helmet: Automatic Remediation is available for this issue
|
secu
|
cve medium detected in follow redirects tgz cve medium severity vulnerability vulnerable library follow redirects tgz http and https modules that follow redirects library home page a href path to dependency file package json path to vulnerable library node modules follow redirects package json dependency hierarchy karma tgz root library http proxy tgz x follow redirects tgz vulnerable library found in head commit a href found in base branch master vulnerability details exposure of sensitive information to an unauthorized actor in npm follow redirects prior to publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact none availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution follow redirects direct dependency fix resolution karma rescue worker helmet automatic remediation is available for this issue
| 1
|
232,984
| 25,719,001,883
|
IssuesEvent
|
2022-12-07 12:24:42
|
RG4421/mmRTLS
|
https://api.github.com/repos/RG4421/mmRTLS
|
opened
|
CVE-2022-37603 (High) detected in loader-utils-1.4.0.tgz
|
security vulnerability
|
## CVE-2022-37603 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>loader-utils-1.4.0.tgz</b></p></summary>
<p>utils for webpack loaders</p>
<p>Library home page: <a href="https://registry.npmjs.org/loader-utils/-/loader-utils-1.4.0.tgz">https://registry.npmjs.org/loader-utils/-/loader-utils-1.4.0.tgz</a></p>
<p>
Dependency Hierarchy:
- smelte-1.1.6.tgz (Root Library)
- rollup-plugin-postcss-4.0.1.tgz
- postcss-modules-4.2.2.tgz
- generic-names-2.0.1.tgz
- :x: **loader-utils-1.4.0.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/RG4421/mmRTLS/commit/d1a62beea812a21243e0462c86cd2d183efcd723">d1a62beea812a21243e0462c86cd2d183efcd723</a></p>
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
A Regular expression denial of service (ReDoS) flaw was found in Function interpolateName in interpolateName.js in webpack loader-utils 2.0.0 via the url variable in interpolateName.js.
<p>Publish Date: 2022-10-14
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2022-37603>CVE-2022-37603</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/advisories/GHSA-3rfm-jhwj-7488">https://github.com/advisories/GHSA-3rfm-jhwj-7488</a></p>
<p>Release Date: 2022-10-14</p>
<p>Fix Resolution (loader-utils): 2.0.4</p>
<p>Direct dependency fix Resolution (smelte): 1.1.7</p>
</p>
</details>
<p></p>
|
True
|
CVE-2022-37603 (High) detected in loader-utils-1.4.0.tgz - ## CVE-2022-37603 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>loader-utils-1.4.0.tgz</b></p></summary>
<p>utils for webpack loaders</p>
<p>Library home page: <a href="https://registry.npmjs.org/loader-utils/-/loader-utils-1.4.0.tgz">https://registry.npmjs.org/loader-utils/-/loader-utils-1.4.0.tgz</a></p>
<p>
Dependency Hierarchy:
- smelte-1.1.6.tgz (Root Library)
- rollup-plugin-postcss-4.0.1.tgz
- postcss-modules-4.2.2.tgz
- generic-names-2.0.1.tgz
- :x: **loader-utils-1.4.0.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/RG4421/mmRTLS/commit/d1a62beea812a21243e0462c86cd2d183efcd723">d1a62beea812a21243e0462c86cd2d183efcd723</a></p>
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
A Regular expression denial of service (ReDoS) flaw was found in Function interpolateName in interpolateName.js in webpack loader-utils 2.0.0 via the url variable in interpolateName.js.
<p>Publish Date: 2022-10-14
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2022-37603>CVE-2022-37603</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/advisories/GHSA-3rfm-jhwj-7488">https://github.com/advisories/GHSA-3rfm-jhwj-7488</a></p>
<p>Release Date: 2022-10-14</p>
<p>Fix Resolution (loader-utils): 2.0.4</p>
<p>Direct dependency fix Resolution (smelte): 1.1.7</p>
</p>
</details>
<p></p>
|
secu
|
cve high detected in loader utils tgz cve high severity vulnerability vulnerable library loader utils tgz utils for webpack loaders library home page a href dependency hierarchy smelte tgz root library rollup plugin postcss tgz postcss modules tgz generic names tgz x loader utils tgz vulnerable library found in head commit a href found in base branch main vulnerability details a regular expression denial of service redos flaw was found in function interpolatename in interpolatename js in webpack loader utils via the url variable in interpolatename js publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution loader utils direct dependency fix resolution smelte
| 1
|
12,189
| 8,636,080,360
|
IssuesEvent
|
2018-11-23 04:46:34
|
AOSC-Dev/aosc-os-abbs
|
https://api.github.com/repos/AOSC-Dev/aosc-os-abbs
|
closed
|
flashplayer-ppapi: security update to 31.0.0.148
|
security to-stable upgrade
|
<!-- Please remove items do not apply. -->
**CVE IDs:** CVE-2018-15978
**Other security advisory IDs:** APSB18-39, MGASA-2018-0453, RHSA-2018:3618-01
**Descriptions:**
An important vulnerability in Adobe Flash Player 31.0.0.122 and earlier
versions. Successful exploitation could lead to information disclosure.
(CVE-2018-15978)
**Architectural progress:**
<!-- Please remove any architecture to which the security vulnerabilities do not apply. -->
- [x] AMD64 `amd64`
|
True
|
flashplayer-ppapi: security update to 31.0.0.148 - <!-- Please remove items do not apply. -->
**CVE IDs:** CVE-2018-15978
**Other security advisory IDs:** APSB18-39, MGASA-2018-0453, RHSA-2018:3618-01
**Descriptions:**
An important vulnerability in Adobe Flash Player 31.0.0.122 and earlier
versions. Successful exploitation could lead to information disclosure.
(CVE-2018-15978)
**Architectural progress:**
<!-- Please remove any architecture to which the security vulnerabilities do not apply. -->
- [x] AMD64 `amd64`
|
secu
|
flashplayer ppapi security update to cve ids cve other security advisory ids mgasa rhsa descriptions an important vulnerability in adobe flash player and earlier versions successful exploitation could lead to information disclosure cve architectural progress
| 1
|
147,578
| 19,522,846,333
|
IssuesEvent
|
2021-12-29 22:30:50
|
swagger-api/swagger-codegen
|
https://api.github.com/repos/swagger-api/swagger-codegen
|
opened
|
CVE-2018-12023 (High) detected in multiple libraries
|
security vulnerability
|
## CVE-2018-12023 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>jackson-databind-2.8.9.jar</b>, <b>jackson-databind-2.4.5.jar</b>, <b>jackson-databind-2.6.4.jar</b>, <b>jackson-databind-2.8.8.jar</b>, <b>jackson-databind-2.7.8.jar</b></p></summary>
<p>
<details><summary><b>jackson-databind-2.8.9.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to vulnerable library: /home/wss-scanner/.ivy2/cache/com.fasterxml.jackson.core/jackson-databind/bundles/jackson-databind-2.8.9.jar</p>
<p>
Dependency Hierarchy:
- play-guice_2.12-2.6.3.jar (Root Library)
- play_2.12-2.6.3.jar
- :x: **jackson-databind-2.8.9.jar** (Vulnerable Library)
</details>
<details><summary><b>jackson-databind-2.4.5.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /samples/client/petstore/scala/build.gradle</p>
<p>Path to vulnerable library: /home/wss-scanner/.gradle/caches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.4.5/c69c0cb613128c69d84a6a0304ddb9fce82e8242/jackson-databind-2.4.5.jar,/home/wss-scanner/.gradle/caches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.4.5/c69c0cb613128c69d84a6a0304ddb9fce82e8242/jackson-databind-2.4.5.jar</p>
<p>
Dependency Hierarchy:
- swagger-core-1.5.8.jar (Root Library)
- :x: **jackson-databind-2.4.5.jar** (Vulnerable Library)
</details>
<details><summary><b>jackson-databind-2.6.4.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /samples/client/petstore/java/jersey1/build.gradle</p>
<p>Path to vulnerable library: /home/wss-scanner/.gradle/caches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.6.4/f2abadd10891512268b16a1a1a6f81890f3e2976/jackson-databind-2.6.4.jar,/aches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.6.4/f2abadd10891512268b16a1a1a6f81890f3e2976/jackson-databind-2.6.4.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.6.4.jar** (Vulnerable Library)
</details>
<details><summary><b>jackson-databind-2.8.8.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to vulnerable library: /home/wss-scanner/.ivy2/cache/com.fasterxml.jackson.core/jackson-databind/bundles/jackson-databind-2.8.8.jar</p>
<p>
Dependency Hierarchy:
- finch-circe_2.11-0.15.1.jar (Root Library)
- circe-jackson28_2.11-0.8.0.jar
- :x: **jackson-databind-2.8.8.jar** (Vulnerable Library)
</details>
<details><summary><b>jackson-databind-2.7.8.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to vulnerable library: /home/wss-scanner/.ivy2/cache/com.fasterxml.jackson.core/jackson-databind/bundles/jackson-databind-2.7.8.jar</p>
<p>
Dependency Hierarchy:
- lagom-scaladsl-api_2.11-1.3.8.jar (Root Library)
- lagom-api_2.11-1.3.8.jar
- play_2.11-2.5.13.jar
- :x: **jackson-databind-2.7.8.jar** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/swagger-api/swagger-codegen/commit/4b7a8d7d7384aa6a27d6309c35ade0916edae7ed">4b7a8d7d7384aa6a27d6309c35ade0916edae7ed</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
An issue was discovered in FasterXML jackson-databind prior to 2.7.9.4, 2.8.11.2, and 2.9.6. When Default Typing is enabled (either globally or for a specific property), the service has the Oracle JDBC jar in the classpath, and an attacker can provide an LDAP service to access, it is possible to make the service execute a malicious payload.
<p>Publish Date: 2019-03-21
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-12023>CVE-2018-12023</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-12022">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-12022</a></p>
<p>Release Date: 2019-03-21</p>
<p>Fix Resolution: 2.7.9.4, 2.8.11.2, 2.9.6</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":false,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"Java","groupId":"com.fasterxml.jackson.core","packageName":"jackson-databind","packageVersion":"2.8.9","packageFilePaths":[null],"isTransitiveDependency":true,"dependencyTree":"com.typesafe.play:play-guice_2.12:2.6.3;com.typesafe.play:play_2.12:2.6.3;com.fasterxml.jackson.core:jackson-databind:2.8.9","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.7.9.4, 2.8.11.2, 2.9.6","isBinary":false},{"packageType":"Java","groupId":"com.fasterxml.jackson.core","packageName":"jackson-databind","packageVersion":"2.4.5","packageFilePaths":["/samples/client/petstore/scala/build.gradle"],"isTransitiveDependency":true,"dependencyTree":"io.swagger:swagger-core:1.5.8;com.fasterxml.jackson.core:jackson-databind:2.4.5","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.7.9.4, 2.8.11.2, 2.9.6","isBinary":false},{"packageType":"Java","groupId":"com.fasterxml.jackson.core","packageName":"jackson-databind","packageVersion":"2.6.4","packageFilePaths":["/samples/client/petstore/java/jersey1/build.gradle"],"isTransitiveDependency":false,"dependencyTree":"com.fasterxml.jackson.core:jackson-databind:2.6.4","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.7.9.4, 2.8.11.2, 2.9.6","isBinary":false},{"packageType":"Java","groupId":"com.fasterxml.jackson.core","packageName":"jackson-databind","packageVersion":"2.8.8","packageFilePaths":[null],"isTransitiveDependency":true,"dependencyTree":"com.github.finagle:finch-circe_2.11:0.15.1;io.circe:circe-jackson28_2.11:0.8.0;com.fasterxml.jackson.core:jackson-databind:2.8.8","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.7.9.4, 2.8.11.2, 2.9.6","isBinary":false},{"packageType":"Java","groupId":"com.fasterxml.jackson.core","packageName":"jackson-databind","packageVersion":"2.7.8","packageFilePaths":[null],"isTransitiveDependency":true,"dependencyTree":"com.lightbend.lagom:lagom-scaladsl-api_2.11:1.3.8;com.lightbend.lagom:lagom-api_2.11:1.3.8;com.typesafe.play:play_2.11:2.5.13;com.fasterxml.jackson.core:jackson-databind:2.7.8","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.7.9.4, 2.8.11.2, 2.9.6","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2018-12023","vulnerabilityDetails":"An issue was discovered in FasterXML jackson-databind prior to 2.7.9.4, 2.8.11.2, and 2.9.6. When Default Typing is enabled (either globally or for a specific property), the service has the Oracle JDBC jar in the classpath, and an attacker can provide an LDAP service to access, it is possible to make the service execute a malicious payload.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-12023","cvss3Severity":"high","cvss3Score":"7.5","cvss3Metrics":{"A":"High","AC":"High","PR":"None","S":"Unchanged","C":"High","UI":"Required","AV":"Network","I":"High"},"extraData":{}}</REMEDIATE> -->
|
True
|
CVE-2018-12023 (High) detected in multiple libraries - ## CVE-2018-12023 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>jackson-databind-2.8.9.jar</b>, <b>jackson-databind-2.4.5.jar</b>, <b>jackson-databind-2.6.4.jar</b>, <b>jackson-databind-2.8.8.jar</b>, <b>jackson-databind-2.7.8.jar</b></p></summary>
<p>
<details><summary><b>jackson-databind-2.8.9.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to vulnerable library: /home/wss-scanner/.ivy2/cache/com.fasterxml.jackson.core/jackson-databind/bundles/jackson-databind-2.8.9.jar</p>
<p>
Dependency Hierarchy:
- play-guice_2.12-2.6.3.jar (Root Library)
- play_2.12-2.6.3.jar
- :x: **jackson-databind-2.8.9.jar** (Vulnerable Library)
</details>
<details><summary><b>jackson-databind-2.4.5.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /samples/client/petstore/scala/build.gradle</p>
<p>Path to vulnerable library: /home/wss-scanner/.gradle/caches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.4.5/c69c0cb613128c69d84a6a0304ddb9fce82e8242/jackson-databind-2.4.5.jar,/home/wss-scanner/.gradle/caches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.4.5/c69c0cb613128c69d84a6a0304ddb9fce82e8242/jackson-databind-2.4.5.jar</p>
<p>
Dependency Hierarchy:
- swagger-core-1.5.8.jar (Root Library)
- :x: **jackson-databind-2.4.5.jar** (Vulnerable Library)
</details>
<details><summary><b>jackson-databind-2.6.4.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /samples/client/petstore/java/jersey1/build.gradle</p>
<p>Path to vulnerable library: /home/wss-scanner/.gradle/caches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.6.4/f2abadd10891512268b16a1a1a6f81890f3e2976/jackson-databind-2.6.4.jar,/aches/modules-2/files-2.1/com.fasterxml.jackson.core/jackson-databind/2.6.4/f2abadd10891512268b16a1a1a6f81890f3e2976/jackson-databind-2.6.4.jar</p>
<p>
Dependency Hierarchy:
- :x: **jackson-databind-2.6.4.jar** (Vulnerable Library)
</details>
<details><summary><b>jackson-databind-2.8.8.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to vulnerable library: /home/wss-scanner/.ivy2/cache/com.fasterxml.jackson.core/jackson-databind/bundles/jackson-databind-2.8.8.jar</p>
<p>
Dependency Hierarchy:
- finch-circe_2.11-0.15.1.jar (Root Library)
- circe-jackson28_2.11-0.8.0.jar
- :x: **jackson-databind-2.8.8.jar** (Vulnerable Library)
</details>
<details><summary><b>jackson-databind-2.7.8.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to vulnerable library: /home/wss-scanner/.ivy2/cache/com.fasterxml.jackson.core/jackson-databind/bundles/jackson-databind-2.7.8.jar</p>
<p>
Dependency Hierarchy:
- lagom-scaladsl-api_2.11-1.3.8.jar (Root Library)
- lagom-api_2.11-1.3.8.jar
- play_2.11-2.5.13.jar
- :x: **jackson-databind-2.7.8.jar** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/swagger-api/swagger-codegen/commit/4b7a8d7d7384aa6a27d6309c35ade0916edae7ed">4b7a8d7d7384aa6a27d6309c35ade0916edae7ed</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
An issue was discovered in FasterXML jackson-databind prior to 2.7.9.4, 2.8.11.2, and 2.9.6. When Default Typing is enabled (either globally or for a specific property), the service has the Oracle JDBC jar in the classpath, and an attacker can provide an LDAP service to access, it is possible to make the service execute a malicious payload.
<p>Publish Date: 2019-03-21
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-12023>CVE-2018-12023</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-12022">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-12022</a></p>
<p>Release Date: 2019-03-21</p>
<p>Fix Resolution: 2.7.9.4, 2.8.11.2, 2.9.6</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":false,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"Java","groupId":"com.fasterxml.jackson.core","packageName":"jackson-databind","packageVersion":"2.8.9","packageFilePaths":[null],"isTransitiveDependency":true,"dependencyTree":"com.typesafe.play:play-guice_2.12:2.6.3;com.typesafe.play:play_2.12:2.6.3;com.fasterxml.jackson.core:jackson-databind:2.8.9","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.7.9.4, 2.8.11.2, 2.9.6","isBinary":false},{"packageType":"Java","groupId":"com.fasterxml.jackson.core","packageName":"jackson-databind","packageVersion":"2.4.5","packageFilePaths":["/samples/client/petstore/scala/build.gradle"],"isTransitiveDependency":true,"dependencyTree":"io.swagger:swagger-core:1.5.8;com.fasterxml.jackson.core:jackson-databind:2.4.5","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.7.9.4, 2.8.11.2, 2.9.6","isBinary":false},{"packageType":"Java","groupId":"com.fasterxml.jackson.core","packageName":"jackson-databind","packageVersion":"2.6.4","packageFilePaths":["/samples/client/petstore/java/jersey1/build.gradle"],"isTransitiveDependency":false,"dependencyTree":"com.fasterxml.jackson.core:jackson-databind:2.6.4","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.7.9.4, 2.8.11.2, 2.9.6","isBinary":false},{"packageType":"Java","groupId":"com.fasterxml.jackson.core","packageName":"jackson-databind","packageVersion":"2.8.8","packageFilePaths":[null],"isTransitiveDependency":true,"dependencyTree":"com.github.finagle:finch-circe_2.11:0.15.1;io.circe:circe-jackson28_2.11:0.8.0;com.fasterxml.jackson.core:jackson-databind:2.8.8","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.7.9.4, 2.8.11.2, 2.9.6","isBinary":false},{"packageType":"Java","groupId":"com.fasterxml.jackson.core","packageName":"jackson-databind","packageVersion":"2.7.8","packageFilePaths":[null],"isTransitiveDependency":true,"dependencyTree":"com.lightbend.lagom:lagom-scaladsl-api_2.11:1.3.8;com.lightbend.lagom:lagom-api_2.11:1.3.8;com.typesafe.play:play_2.11:2.5.13;com.fasterxml.jackson.core:jackson-databind:2.7.8","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.7.9.4, 2.8.11.2, 2.9.6","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2018-12023","vulnerabilityDetails":"An issue was discovered in FasterXML jackson-databind prior to 2.7.9.4, 2.8.11.2, and 2.9.6. When Default Typing is enabled (either globally or for a specific property), the service has the Oracle JDBC jar in the classpath, and an attacker can provide an LDAP service to access, it is possible to make the service execute a malicious payload.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-12023","cvss3Severity":"high","cvss3Score":"7.5","cvss3Metrics":{"A":"High","AC":"High","PR":"None","S":"Unchanged","C":"High","UI":"Required","AV":"Network","I":"High"},"extraData":{}}</REMEDIATE> -->
|
secu
|
cve high detected in multiple libraries cve high severity vulnerability vulnerable libraries jackson databind jar jackson databind jar jackson databind jar jackson databind jar jackson databind jar jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to vulnerable library home wss scanner cache com fasterxml jackson core jackson databind bundles jackson databind jar dependency hierarchy play guice jar root library play jar x jackson databind jar vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file samples client petstore scala build gradle path to vulnerable library home wss scanner gradle caches modules files com fasterxml jackson core jackson databind jackson databind jar home wss scanner gradle caches modules files com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy swagger core jar root library x jackson databind jar vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file samples client petstore java build gradle path to vulnerable library home wss scanner gradle caches modules files com fasterxml jackson core jackson databind jackson databind jar aches modules files com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy x jackson databind jar vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to vulnerable library home wss scanner cache com fasterxml jackson core jackson databind bundles jackson databind jar dependency hierarchy finch circe jar root library circe jar x jackson databind jar vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to vulnerable library home wss scanner cache com fasterxml jackson core jackson databind bundles jackson databind jar dependency hierarchy lagom scaladsl api jar root library lagom api jar play jar x jackson databind jar vulnerable library found in head commit a href found in base branch master vulnerability details an issue was discovered in fasterxml jackson databind prior to and when default typing is enabled either globally or for a specific property the service has the oracle jdbc jar in the classpath and an attacker can provide an ldap service to access it is possible to make the service execute a malicious payload publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required none user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution isopenpronvulnerability false ispackagebased true isdefaultbranch true packages istransitivedependency true dependencytree com typesafe play play guice com typesafe play play com fasterxml jackson core jackson databind isminimumfixversionavailable true minimumfixversion isbinary false packagetype java groupid com fasterxml jackson core packagename jackson databind packageversion packagefilepaths istransitivedependency true dependencytree io swagger swagger core com fasterxml jackson core jackson databind isminimumfixversionavailable true minimumfixversion isbinary false packagetype java groupid com fasterxml jackson core packagename jackson databind packageversion packagefilepaths istransitivedependency false dependencytree com fasterxml jackson core jackson databind isminimumfixversionavailable true minimumfixversion isbinary false packagetype java groupid com fasterxml jackson core packagename jackson databind packageversion packagefilepaths istransitivedependency true dependencytree com github finagle finch circe io circe circe com fasterxml jackson core jackson databind isminimumfixversionavailable true minimumfixversion isbinary false packagetype java groupid com fasterxml jackson core packagename jackson databind packageversion packagefilepaths istransitivedependency true dependencytree com lightbend lagom lagom scaladsl api com lightbend lagom lagom api com typesafe play play com fasterxml jackson core jackson databind isminimumfixversionavailable true minimumfixversion isbinary false basebranches vulnerabilityidentifier cve vulnerabilitydetails an issue was discovered in fasterxml jackson databind prior to and when default typing is enabled either globally or for a specific property the service has the oracle jdbc jar in the classpath and an attacker can provide an ldap service to access it is possible to make the service execute a malicious payload vulnerabilityurl
| 1
|
43,987
| 13,046,216,556
|
IssuesEvent
|
2020-07-29 08:38:03
|
orhanarifoglu/bitti
|
https://api.github.com/repos/orhanarifoglu/bitti
|
opened
|
CVE-2017-3589 (Low) detected in mysql-connector-java-5.1.6.jar
|
security vulnerability
|
## CVE-2017-3589 - Low Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>mysql-connector-java-5.1.6.jar</b></p></summary>
<p>MySQL JDBC Type 4 driver</p>
<p>Library home page: <a href="http://dev.mysql.com/doc/connector-j/en/">http://dev.mysql.com/doc/connector-j/en/</a></p>
<p>Path to dependency file: /tmp/ws-scm/bitti/build.gradle</p>
<p>Path to vulnerable library: canner/.gradle/caches/modules-2/files-2.1/mysql/mysql-connector-java/5.1.6/380ef5226de2c85ff3b38cbfefeea881c5fce09d/mysql-connector-java-5.1.6.jar,_depth_0/bitti/build/distributions/gradleproject2/gradleproject2/lib/mysql-connector-java-5.1.6.jar</p>
<p>
Dependency Hierarchy:
- :x: **mysql-connector-java-5.1.6.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/orhanarifoglu/bitti/commit/b9de9df64013494e4cad4e932f22f2c53e6e45c0">b9de9df64013494e4cad4e932f22f2c53e6e45c0</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/low_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Vulnerability in the MySQL Connectors component of Oracle MySQL (subcomponent: Connector/J). Supported versions that are affected are 5.1.41 and earlier. Easily "exploitable" vulnerability allows low privileged attacker with logon to the infrastructure where MySQL Connectors executes to compromise MySQL Connectors. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of MySQL Connectors accessible data. CVSS 3.0 Base Score 3.3 (Integrity impacts). CVSS Vector: (CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:N).
<p>Publish Date: 2017-04-24
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2017-3589>CVE-2017-3589</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>3.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-3589">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-3589</a></p>
<p>Release Date: 2017-04-24</p>
<p>Fix Resolution: 5.1.42</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2017-3589 (Low) detected in mysql-connector-java-5.1.6.jar - ## CVE-2017-3589 - Low Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>mysql-connector-java-5.1.6.jar</b></p></summary>
<p>MySQL JDBC Type 4 driver</p>
<p>Library home page: <a href="http://dev.mysql.com/doc/connector-j/en/">http://dev.mysql.com/doc/connector-j/en/</a></p>
<p>Path to dependency file: /tmp/ws-scm/bitti/build.gradle</p>
<p>Path to vulnerable library: canner/.gradle/caches/modules-2/files-2.1/mysql/mysql-connector-java/5.1.6/380ef5226de2c85ff3b38cbfefeea881c5fce09d/mysql-connector-java-5.1.6.jar,_depth_0/bitti/build/distributions/gradleproject2/gradleproject2/lib/mysql-connector-java-5.1.6.jar</p>
<p>
Dependency Hierarchy:
- :x: **mysql-connector-java-5.1.6.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/orhanarifoglu/bitti/commit/b9de9df64013494e4cad4e932f22f2c53e6e45c0">b9de9df64013494e4cad4e932f22f2c53e6e45c0</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/low_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Vulnerability in the MySQL Connectors component of Oracle MySQL (subcomponent: Connector/J). Supported versions that are affected are 5.1.41 and earlier. Easily "exploitable" vulnerability allows low privileged attacker with logon to the infrastructure where MySQL Connectors executes to compromise MySQL Connectors. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of MySQL Connectors accessible data. CVSS 3.0 Base Score 3.3 (Integrity impacts). CVSS Vector: (CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:N).
<p>Publish Date: 2017-04-24
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2017-3589>CVE-2017-3589</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>3.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-3589">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-3589</a></p>
<p>Release Date: 2017-04-24</p>
<p>Fix Resolution: 5.1.42</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve low detected in mysql connector java jar cve low severity vulnerability vulnerable library mysql connector java jar mysql jdbc type driver library home page a href path to dependency file tmp ws scm bitti build gradle path to vulnerable library canner gradle caches modules files mysql mysql connector java mysql connector java jar depth bitti build distributions lib mysql connector java jar dependency hierarchy x mysql connector java jar vulnerable library found in head commit a href vulnerability details vulnerability in the mysql connectors component of oracle mysql subcomponent connector j supported versions that are affected are and earlier easily exploitable vulnerability allows low privileged attacker with logon to the infrastructure where mysql connectors executes to compromise mysql connectors successful attacks of this vulnerability can result in unauthorized update insert or delete access to some of mysql connectors accessible data cvss base score integrity impacts cvss vector cvss av l ac l pr l ui n s u c n i l a n publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required low user interaction none scope unchanged impact metrics confidentiality impact none integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource
| 1
|
77,060
| 15,496,264,521
|
IssuesEvent
|
2021-03-11 02:21:28
|
bsbtd/Teste
|
https://api.github.com/repos/bsbtd/Teste
|
opened
|
WS-2019-0425 (Medium) detected in mocha-2.5.3.min.js
|
security vulnerability
|
## WS-2019-0425 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>mocha-2.5.3.min.js</b></p></summary>
<p>simple, flexible, fun test framework</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/mocha/2.5.3/mocha.min.js">https://cdnjs.cloudflare.com/ajax/libs/mocha/2.5.3/mocha.min.js</a></p>
<p>Path to dependency file: Teste/pro-table/node_modules/intersection-observer/intersection-observer-test.html</p>
<p>Path to vulnerable library: Teste/pro-table/node_modules/intersection-observer/intersection-observer-test.html</p>
<p>
Dependency Hierarchy:
- :x: **mocha-2.5.3.min.js** (Vulnerable Library)
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Mocha is vulnerable to ReDoS attack. If the stack trace in utils.js begins with a large error message, and full-trace is not enabled, utils.stackTraceFilter() will take exponential run time.
<p>Publish Date: 2019-01-24
<p>URL: <a href=https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559>WS-2019-0425</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="v6.0.0">v6.0.0</a></p>
<p>Release Date: 2020-05-07</p>
<p>Fix Resolution: https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
WS-2019-0425 (Medium) detected in mocha-2.5.3.min.js - ## WS-2019-0425 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>mocha-2.5.3.min.js</b></p></summary>
<p>simple, flexible, fun test framework</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/mocha/2.5.3/mocha.min.js">https://cdnjs.cloudflare.com/ajax/libs/mocha/2.5.3/mocha.min.js</a></p>
<p>Path to dependency file: Teste/pro-table/node_modules/intersection-observer/intersection-observer-test.html</p>
<p>Path to vulnerable library: Teste/pro-table/node_modules/intersection-observer/intersection-observer-test.html</p>
<p>
Dependency Hierarchy:
- :x: **mocha-2.5.3.min.js** (Vulnerable Library)
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Mocha is vulnerable to ReDoS attack. If the stack trace in utils.js begins with a large error message, and full-trace is not enabled, utils.stackTraceFilter() will take exponential run time.
<p>Publish Date: 2019-01-24
<p>URL: <a href=https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559>WS-2019-0425</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="v6.0.0">v6.0.0</a></p>
<p>Release Date: 2020-05-07</p>
<p>Fix Resolution: https://github.com/mochajs/mocha/commit/1a43d8b11a64e4e85fe2a61aed91c259bbbac559</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
ws medium detected in mocha min js ws medium severity vulnerability vulnerable library mocha min js simple flexible fun test framework library home page a href path to dependency file teste pro table node modules intersection observer intersection observer test html path to vulnerable library teste pro table node modules intersection observer intersection observer test html dependency hierarchy x mocha min js vulnerable library vulnerability details mocha is vulnerable to redos attack if the stack trace in utils js begins with a large error message and full trace is not enabled utils stacktracefilter will take exponential run time publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact low for more information on scores click a href suggested fix type upgrade version origin release date fix resolution step up your open source security game with whitesource
| 1
|
47,470
| 12,036,167,371
|
IssuesEvent
|
2020-04-13 19:16:22
|
tensorflow/tensorflow
|
https://api.github.com/repos/tensorflow/tensorflow
|
opened
|
ImportError: DLL load failed: The specified module could not be found. Failed to load the native TensorFlow runtime.
|
type:build/install
|
**System information**
- OS Platform and Distribution (e.g., Linux Ubuntu 16.04): Windows 10
- Mobile device (e.g. iPhone 8, Pixel 2, Samsung Galaxy) if the issue happens on mobile device: N/A
- TensorFlow installed from (source or binary): pip install
- TensorFlow version: 2
- Python version: 3.7
- Installed using virtualenv? pip? conda?: pip
- Bazel version (if compiling from source): N/A
- GCC/Compiler version (if compiling from source): N?A
- CUDA/cuDNN version: CUDA 10.2, cuDNN 7.6.5
- GPU model and memory: Nvidia Quadro M1200
I cannot import tensorflow
This is what I got:
Exception has occurred: ImportError
Traceback (most recent call last): File "C:\Users\khiteliv\AppData\Local\Continuum\anaconda3\lib\site-packages\tensorflow_core\python\pywrap_tensorflow.py", line 58, in <module> from tensorflow.python.pywrap_tensorflow_internal import * File "C:\Users\khiteliv\AppData\Local\Continuum\anaconda3\lib\site-packages\tensorflow_core\python\pywrap_tensorflow_internal.py", line 28, in <module> _pywrap_tensorflow_internal = swig_import_helper() File "C:\Users\khiteliv\AppData\Local\Continuum\anaconda3\lib\site-packages\tensorflow_core\python\pywrap_tensorflow_internal.py", line 24, in swig_import_helper _mod = imp.load_module('_pywrap_tensorflow_internal', fp, pathname, description) File "C:\Users\khiteliv\AppData\Local\Continuum\anaconda3\lib\imp.py", line 242, in load_module return load_dynamic(name, filename, file) File "C:\Users\khiteliv\AppData\Local\Continuum\anaconda3\lib\imp.py", line 342, in load_dynamic return _load(spec) ImportError: DLL load failed: The specified module could not be found. Failed to load the native TensorFlow runtime.
Thank you for your help!
|
1.0
|
ImportError: DLL load failed: The specified module could not be found. Failed to load the native TensorFlow runtime. - **System information**
- OS Platform and Distribution (e.g., Linux Ubuntu 16.04): Windows 10
- Mobile device (e.g. iPhone 8, Pixel 2, Samsung Galaxy) if the issue happens on mobile device: N/A
- TensorFlow installed from (source or binary): pip install
- TensorFlow version: 2
- Python version: 3.7
- Installed using virtualenv? pip? conda?: pip
- Bazel version (if compiling from source): N/A
- GCC/Compiler version (if compiling from source): N?A
- CUDA/cuDNN version: CUDA 10.2, cuDNN 7.6.5
- GPU model and memory: Nvidia Quadro M1200
I cannot import tensorflow
This is what I got:
Exception has occurred: ImportError
Traceback (most recent call last): File "C:\Users\khiteliv\AppData\Local\Continuum\anaconda3\lib\site-packages\tensorflow_core\python\pywrap_tensorflow.py", line 58, in <module> from tensorflow.python.pywrap_tensorflow_internal import * File "C:\Users\khiteliv\AppData\Local\Continuum\anaconda3\lib\site-packages\tensorflow_core\python\pywrap_tensorflow_internal.py", line 28, in <module> _pywrap_tensorflow_internal = swig_import_helper() File "C:\Users\khiteliv\AppData\Local\Continuum\anaconda3\lib\site-packages\tensorflow_core\python\pywrap_tensorflow_internal.py", line 24, in swig_import_helper _mod = imp.load_module('_pywrap_tensorflow_internal', fp, pathname, description) File "C:\Users\khiteliv\AppData\Local\Continuum\anaconda3\lib\imp.py", line 242, in load_module return load_dynamic(name, filename, file) File "C:\Users\khiteliv\AppData\Local\Continuum\anaconda3\lib\imp.py", line 342, in load_dynamic return _load(spec) ImportError: DLL load failed: The specified module could not be found. Failed to load the native TensorFlow runtime.
Thank you for your help!
|
non_secu
|
importerror dll load failed the specified module could not be found failed to load the native tensorflow runtime system information os platform and distribution e g linux ubuntu windows mobile device e g iphone pixel samsung galaxy if the issue happens on mobile device n a tensorflow installed from source or binary pip install tensorflow version python version installed using virtualenv pip conda pip bazel version if compiling from source n a gcc compiler version if compiling from source n a cuda cudnn version cuda cudnn gpu model and memory nvidia quadro i cannot import tensorflow this is what i got exception has occurred importerror traceback most recent call last file c users khiteliv appdata local continuum lib site packages tensorflow core python pywrap tensorflow py line in from tensorflow python pywrap tensorflow internal import file c users khiteliv appdata local continuum lib site packages tensorflow core python pywrap tensorflow internal py line in pywrap tensorflow internal swig import helper file c users khiteliv appdata local continuum lib site packages tensorflow core python pywrap tensorflow internal py line in swig import helper mod imp load module pywrap tensorflow internal fp pathname description file c users khiteliv appdata local continuum lib imp py line in load module return load dynamic name filename file file c users khiteliv appdata local continuum lib imp py line in load dynamic return load spec importerror dll load failed the specified module could not be found failed to load the native tensorflow runtime thank you for your help
| 0
|
112,619
| 17,093,082,574
|
IssuesEvent
|
2021-07-08 20:23:51
|
mickelsonmichael/js-snackbar
|
https://api.github.com/repos/mickelsonmichael/js-snackbar
|
opened
|
WS-2021-0154 (Medium) detected in glob-parent-3.1.0.tgz, glob-parent-5.1.1.tgz
|
security vulnerability
|
## WS-2021-0154 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>glob-parent-3.1.0.tgz</b>, <b>glob-parent-5.1.1.tgz</b></p></summary>
<p>
<details><summary><b>glob-parent-3.1.0.tgz</b></p></summary>
<p>Strips glob magic from a string to provide the parent directory path</p>
<p>Library home page: <a href="https://registry.npmjs.org/glob-parent/-/glob-parent-3.1.0.tgz">https://registry.npmjs.org/glob-parent/-/glob-parent-3.1.0.tgz</a></p>
<p>Path to dependency file: js-snackbar/package.json</p>
<p>Path to vulnerable library: js-snackbar/node_modules/glob-parent/package.json,js-snackbar/node_modules/glob-parent/package.json</p>
<p>
Dependency Hierarchy:
- cli-7.12.10.tgz (Root Library)
- chokidar-2-2.1.8-no-fsevents.tgz
- :x: **glob-parent-3.1.0.tgz** (Vulnerable Library)
</details>
<details><summary><b>glob-parent-5.1.1.tgz</b></p></summary>
<p>Extract the non-magic parent path from a glob string.</p>
<p>Library home page: <a href="https://registry.npmjs.org/glob-parent/-/glob-parent-5.1.1.tgz">https://registry.npmjs.org/glob-parent/-/glob-parent-5.1.1.tgz</a></p>
<p>Path to dependency file: js-snackbar/package.json</p>
<p>Path to vulnerable library: js-snackbar/node_modules/chokidar/node_modules/glob-parent/package.json,js-snackbar/node_modules/chokidar/node_modules/glob-parent/package.json,js-snackbar/node_modules/fast-glob/node_modules/glob-parent/package.json,js-snackbar/node_modules/fast-glob/node_modules/glob-parent/package.json</p>
<p>
Dependency Hierarchy:
- cli-7.12.10.tgz (Root Library)
- chokidar-3.5.1.tgz
- :x: **glob-parent-5.1.1.tgz** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/mickelsonmichael/js-snackbar/commit/5907d79b6a1d0acdc78422f8ebd462ef585ee119">5907d79b6a1d0acdc78422f8ebd462ef585ee119</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Regular Expression Denial of Service (ReDoS) vulnerability was found in glob-parent before 5.1.2.
<p>Publish Date: 2021-01-27
<p>URL: <a href=https://github.com/gulpjs/glob-parent/commit/f9231168b0041fea3f8f954b3cceb56269fc6366>WS-2021-0154</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/gulpjs/glob-parent/releases/tag/v5.1.2">https://github.com/gulpjs/glob-parent/releases/tag/v5.1.2</a></p>
<p>Release Date: 2021-01-27</p>
<p>Fix Resolution: glob-parent - 5.1.2</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
WS-2021-0154 (Medium) detected in glob-parent-3.1.0.tgz, glob-parent-5.1.1.tgz - ## WS-2021-0154 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>glob-parent-3.1.0.tgz</b>, <b>glob-parent-5.1.1.tgz</b></p></summary>
<p>
<details><summary><b>glob-parent-3.1.0.tgz</b></p></summary>
<p>Strips glob magic from a string to provide the parent directory path</p>
<p>Library home page: <a href="https://registry.npmjs.org/glob-parent/-/glob-parent-3.1.0.tgz">https://registry.npmjs.org/glob-parent/-/glob-parent-3.1.0.tgz</a></p>
<p>Path to dependency file: js-snackbar/package.json</p>
<p>Path to vulnerable library: js-snackbar/node_modules/glob-parent/package.json,js-snackbar/node_modules/glob-parent/package.json</p>
<p>
Dependency Hierarchy:
- cli-7.12.10.tgz (Root Library)
- chokidar-2-2.1.8-no-fsevents.tgz
- :x: **glob-parent-3.1.0.tgz** (Vulnerable Library)
</details>
<details><summary><b>glob-parent-5.1.1.tgz</b></p></summary>
<p>Extract the non-magic parent path from a glob string.</p>
<p>Library home page: <a href="https://registry.npmjs.org/glob-parent/-/glob-parent-5.1.1.tgz">https://registry.npmjs.org/glob-parent/-/glob-parent-5.1.1.tgz</a></p>
<p>Path to dependency file: js-snackbar/package.json</p>
<p>Path to vulnerable library: js-snackbar/node_modules/chokidar/node_modules/glob-parent/package.json,js-snackbar/node_modules/chokidar/node_modules/glob-parent/package.json,js-snackbar/node_modules/fast-glob/node_modules/glob-parent/package.json,js-snackbar/node_modules/fast-glob/node_modules/glob-parent/package.json</p>
<p>
Dependency Hierarchy:
- cli-7.12.10.tgz (Root Library)
- chokidar-3.5.1.tgz
- :x: **glob-parent-5.1.1.tgz** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/mickelsonmichael/js-snackbar/commit/5907d79b6a1d0acdc78422f8ebd462ef585ee119">5907d79b6a1d0acdc78422f8ebd462ef585ee119</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Regular Expression Denial of Service (ReDoS) vulnerability was found in glob-parent before 5.1.2.
<p>Publish Date: 2021-01-27
<p>URL: <a href=https://github.com/gulpjs/glob-parent/commit/f9231168b0041fea3f8f954b3cceb56269fc6366>WS-2021-0154</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/gulpjs/glob-parent/releases/tag/v5.1.2">https://github.com/gulpjs/glob-parent/releases/tag/v5.1.2</a></p>
<p>Release Date: 2021-01-27</p>
<p>Fix Resolution: glob-parent - 5.1.2</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
ws medium detected in glob parent tgz glob parent tgz ws medium severity vulnerability vulnerable libraries glob parent tgz glob parent tgz glob parent tgz strips glob magic from a string to provide the parent directory path library home page a href path to dependency file js snackbar package json path to vulnerable library js snackbar node modules glob parent package json js snackbar node modules glob parent package json dependency hierarchy cli tgz root library chokidar no fsevents tgz x glob parent tgz vulnerable library glob parent tgz extract the non magic parent path from a glob string library home page a href path to dependency file js snackbar package json path to vulnerable library js snackbar node modules chokidar node modules glob parent package json js snackbar node modules chokidar node modules glob parent package json js snackbar node modules fast glob node modules glob parent package json js snackbar node modules fast glob node modules glob parent package json dependency hierarchy cli tgz root library chokidar tgz x glob parent tgz vulnerable library found in head commit a href found in base branch master vulnerability details regular expression denial of service redos vulnerability was found in glob parent before publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact low for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution glob parent step up your open source security game with whitesource
| 1
|
719,034
| 24,743,103,113
|
IssuesEvent
|
2022-10-21 07:28:03
|
yugabyte/yugabyte-db
|
https://api.github.com/repos/yugabyte/yugabyte-db
|
opened
|
[YSQL] [Pessimistic Locking] [Colocation]: implicit-explicit and explicit-implicit locking not working for colocated tables
|
area/ysql priority/high QA status/awaiting-triage
|
### Description
Version: 2.17.0.0-b1
Observed that waiting behaviour is absent for implicit-explicit and explicit-implicit types of conflicts for colocated tables.
|
1.0
|
[YSQL] [Pessimistic Locking] [Colocation]: implicit-explicit and explicit-implicit locking not working for colocated tables - ### Description
Version: 2.17.0.0-b1
Observed that waiting behaviour is absent for implicit-explicit and explicit-implicit types of conflicts for colocated tables.
|
non_secu
|
implicit explicit and explicit implicit locking not working for colocated tables description version observed that waiting behaviour is absent for implicit explicit and explicit implicit types of conflicts for colocated tables
| 0
|
254,081
| 27,344,401,910
|
IssuesEvent
|
2023-02-27 02:50:07
|
opensearch-project/security
|
https://api.github.com/repos/opensearch-project/security
|
closed
|
CVE-2023-25194 (High) detected in kafka-clients-3.0.2.jar
|
security vulnerability triaged
|
## CVE-2023-25194 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>kafka-clients-3.0.2.jar</b></p></summary>
<p></p>
<p>Library home page: <a href="https://kafka.apache.org">https://kafka.apache.org</a></p>
<p>Path to dependency file: /build.gradle</p>
<p>Path to vulnerable library: /home/wss-scanner/.gradle/caches/modules-2/files-2.1/org.apache.kafka/kafka-clients/3.0.2/aad490436bf6fbeccb4eef8ad5606e5b8917373/kafka-clients-3.0.2.jar</p>
<p>
Dependency Hierarchy:
- :x: **kafka-clients-3.0.2.jar** (Vulnerable Library)
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
A possible security vulnerability has been identified in Apache Kafka Connect. This requires access to a Kafka Connect worker, and the ability to create/modify connectors on it with an arbitrary Kafka client SASL JAAS config and a SASL-based security protocol, which has been possible on Kafka Connect clusters since Apache Kafka 2.3.0. When configuring the connector via the Kafka Connect REST API, an authenticated operator can set the `sasl.jaas.config` property for any of the connector's Kafka clients to "com.sun.security.auth.module.JndiLoginModule", which can be done via the `producer.override.sasl.jaas.config`, `consumer.override.sasl.jaas.config`, or `admin.override.sasl.jaas.config` properties. This will allow the server to connect to the attacker's LDAP server and deserialize the LDAP response, which the attacker can use to execute java deserialization gadget chains on the Kafka connect server. Attacker can cause unrestricted deserialization of untrusted data (or) RCE vulnerability when there are gadgets in the classpath. Since Apache Kafka 3.0.0, users are allowed to specify these properties in connector configurations for Kafka Connect clusters running with out-of-the-box configurations. Before Apache Kafka 3.0.0, users may not specify these properties unless the Kafka Connect cluster has been reconfigured with a connector client override policy that permits them. Since Apache Kafka 3.4.0, we have added a system property ("-Dorg.apache.kafka.disallowed.login.modules") to disable the problematic login modules usage in SASL JAAS configuration. Also by default "com.sun.security.auth.module.JndiLoginModule" is disabled in Apache Kafka 3.4.0. We advise the Kafka Connect users to validate connector configurations and only allow trusted JNDI configurations. Also examine connector dependencies for vulnerable versions and either upgrade their connectors, upgrading that specific dependency, or removing the connectors as options for remediation. Finally, in addition to leveraging the "org.apache.kafka.disallowed.login.modules" system property, Kafka Connect users can also implement their own connector client config override policy, which can be used to control which Kafka client properties can be overridden directly in a connector config and which cannot.
<p>Publish Date: 2023-02-07
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2023-25194>CVE-2023-25194</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>8.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://kafka.apache.org/cve-list">https://kafka.apache.org/cve-list</a></p>
<p>Release Date: 2023-02-07</p>
<p>Fix Resolution: 3.4.0</p>
</p>
</details>
<p></p>
***
<!-- REMEDIATE-OPEN-PR-START -->
- [ ] Check this box to open an automated fix PR
<!-- REMEDIATE-OPEN-PR-END -->
|
True
|
CVE-2023-25194 (High) detected in kafka-clients-3.0.2.jar - ## CVE-2023-25194 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>kafka-clients-3.0.2.jar</b></p></summary>
<p></p>
<p>Library home page: <a href="https://kafka.apache.org">https://kafka.apache.org</a></p>
<p>Path to dependency file: /build.gradle</p>
<p>Path to vulnerable library: /home/wss-scanner/.gradle/caches/modules-2/files-2.1/org.apache.kafka/kafka-clients/3.0.2/aad490436bf6fbeccb4eef8ad5606e5b8917373/kafka-clients-3.0.2.jar</p>
<p>
Dependency Hierarchy:
- :x: **kafka-clients-3.0.2.jar** (Vulnerable Library)
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
A possible security vulnerability has been identified in Apache Kafka Connect. This requires access to a Kafka Connect worker, and the ability to create/modify connectors on it with an arbitrary Kafka client SASL JAAS config and a SASL-based security protocol, which has been possible on Kafka Connect clusters since Apache Kafka 2.3.0. When configuring the connector via the Kafka Connect REST API, an authenticated operator can set the `sasl.jaas.config` property for any of the connector's Kafka clients to "com.sun.security.auth.module.JndiLoginModule", which can be done via the `producer.override.sasl.jaas.config`, `consumer.override.sasl.jaas.config`, or `admin.override.sasl.jaas.config` properties. This will allow the server to connect to the attacker's LDAP server and deserialize the LDAP response, which the attacker can use to execute java deserialization gadget chains on the Kafka connect server. Attacker can cause unrestricted deserialization of untrusted data (or) RCE vulnerability when there are gadgets in the classpath. Since Apache Kafka 3.0.0, users are allowed to specify these properties in connector configurations for Kafka Connect clusters running with out-of-the-box configurations. Before Apache Kafka 3.0.0, users may not specify these properties unless the Kafka Connect cluster has been reconfigured with a connector client override policy that permits them. Since Apache Kafka 3.4.0, we have added a system property ("-Dorg.apache.kafka.disallowed.login.modules") to disable the problematic login modules usage in SASL JAAS configuration. Also by default "com.sun.security.auth.module.JndiLoginModule" is disabled in Apache Kafka 3.4.0. We advise the Kafka Connect users to validate connector configurations and only allow trusted JNDI configurations. Also examine connector dependencies for vulnerable versions and either upgrade their connectors, upgrading that specific dependency, or removing the connectors as options for remediation. Finally, in addition to leveraging the "org.apache.kafka.disallowed.login.modules" system property, Kafka Connect users can also implement their own connector client config override policy, which can be used to control which Kafka client properties can be overridden directly in a connector config and which cannot.
<p>Publish Date: 2023-02-07
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2023-25194>CVE-2023-25194</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>8.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://kafka.apache.org/cve-list">https://kafka.apache.org/cve-list</a></p>
<p>Release Date: 2023-02-07</p>
<p>Fix Resolution: 3.4.0</p>
</p>
</details>
<p></p>
***
<!-- REMEDIATE-OPEN-PR-START -->
- [ ] Check this box to open an automated fix PR
<!-- REMEDIATE-OPEN-PR-END -->
|
secu
|
cve high detected in kafka clients jar cve high severity vulnerability vulnerable library kafka clients jar library home page a href path to dependency file build gradle path to vulnerable library home wss scanner gradle caches modules files org apache kafka kafka clients kafka clients jar dependency hierarchy x kafka clients jar vulnerable library found in base branch main vulnerability details a possible security vulnerability has been identified in apache kafka connect this requires access to a kafka connect worker and the ability to create modify connectors on it with an arbitrary kafka client sasl jaas config and a sasl based security protocol which has been possible on kafka connect clusters since apache kafka when configuring the connector via the kafka connect rest api an authenticated operator can set the sasl jaas config property for any of the connector s kafka clients to com sun security auth module jndiloginmodule which can be done via the producer override sasl jaas config consumer override sasl jaas config or admin override sasl jaas config properties this will allow the server to connect to the attacker s ldap server and deserialize the ldap response which the attacker can use to execute java deserialization gadget chains on the kafka connect server attacker can cause unrestricted deserialization of untrusted data or rce vulnerability when there are gadgets in the classpath since apache kafka users are allowed to specify these properties in connector configurations for kafka connect clusters running with out of the box configurations before apache kafka users may not specify these properties unless the kafka connect cluster has been reconfigured with a connector client override policy that permits them since apache kafka we have added a system property dorg apache kafka disallowed login modules to disable the problematic login modules usage in sasl jaas configuration also by default com sun security auth module jndiloginmodule is disabled in apache kafka we advise the kafka connect users to validate connector configurations and only allow trusted jndi configurations also examine connector dependencies for vulnerable versions and either upgrade their connectors upgrading that specific dependency or removing the connectors as options for remediation finally in addition to leveraging the org apache kafka disallowed login modules system property kafka connect users can also implement their own connector client config override policy which can be used to control which kafka client properties can be overridden directly in a connector config and which cannot publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required low user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution check this box to open an automated fix pr
| 1
|
280,148
| 30,804,263,333
|
IssuesEvent
|
2023-08-01 05:40:33
|
nidhi7598/hardware_nxp_nfc_AOSP_10_r33
|
https://api.github.com/repos/nidhi7598/hardware_nxp_nfc_AOSP_10_r33
|
opened
|
CVE-2020-0153 (Medium) detected in nfcandroid-10.0.0_r1
|
Mend: dependency security vulnerability
|
## CVE-2020-0153 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>nfcandroid-10.0.0_r1</b></p></summary>
<p>
<p>Bug: 68716290</p>
<p>Library home page: <a href=https://android.googlesource.com/platform/hardware/nxp/nfc>https://android.googlesource.com/platform/hardware/nxp/nfc</a></p>
<p>Found in HEAD commit: <a href="https://github.com/nidhi7598/hardware_nxp_nfc_AOSP_10_r33/commit/9b3ebcf5d8c6518197dfe0b6171c30b586dbc65d">9b3ebcf5d8c6518197dfe0b6171c30b586dbc65d</a></p>
<p>Found in base branch: <b>main</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (1)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/halimpl/hal/phNxpNciHal_ext.cc</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png?' width=19 height=20> Vulnerability Details</summary>
<p>
In phNxpNciHal_write_ext of phNxpNciHal_ext.cc, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-10Android ID: A-139733543
<p>Publish Date: 2020-06-11
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-0153>CVE-2020-0153</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.7</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: High
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://android.googlesource.com/platform/hardware/nxp/nfc/+/refs/tags/android-10.0.0_r37">https://android.googlesource.com/platform/hardware/nxp/nfc/+/refs/tags/android-10.0.0_r37</a></p>
<p>Release Date: 2020-06-11</p>
<p>Fix Resolution: android-10.0.0_r37</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2020-0153 (Medium) detected in nfcandroid-10.0.0_r1 - ## CVE-2020-0153 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>nfcandroid-10.0.0_r1</b></p></summary>
<p>
<p>Bug: 68716290</p>
<p>Library home page: <a href=https://android.googlesource.com/platform/hardware/nxp/nfc>https://android.googlesource.com/platform/hardware/nxp/nfc</a></p>
<p>Found in HEAD commit: <a href="https://github.com/nidhi7598/hardware_nxp_nfc_AOSP_10_r33/commit/9b3ebcf5d8c6518197dfe0b6171c30b586dbc65d">9b3ebcf5d8c6518197dfe0b6171c30b586dbc65d</a></p>
<p>Found in base branch: <b>main</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (1)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/halimpl/hal/phNxpNciHal_ext.cc</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png?' width=19 height=20> Vulnerability Details</summary>
<p>
In phNxpNciHal_write_ext of phNxpNciHal_ext.cc, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-10Android ID: A-139733543
<p>Publish Date: 2020-06-11
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2020-0153>CVE-2020-0153</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.7</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: High
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://android.googlesource.com/platform/hardware/nxp/nfc/+/refs/tags/android-10.0.0_r37">https://android.googlesource.com/platform/hardware/nxp/nfc/+/refs/tags/android-10.0.0_r37</a></p>
<p>Release Date: 2020-06-11</p>
<p>Fix Resolution: android-10.0.0_r37</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve medium detected in nfcandroid cve medium severity vulnerability vulnerable library nfcandroid bug library home page a href found in head commit a href found in base branch main vulnerable source files halimpl hal phnxpncihal ext cc vulnerability details in phnxpncihal write ext of phnxpncihal ext cc there is a possible out of bounds write due to a missing bounds check this could lead to local escalation of privilege with system execution privileges needed user interaction is not needed for exploitation product androidversions android id a publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required high user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution android step up your open source security game with mend
| 1
|
88,832
| 25,515,214,910
|
IssuesEvent
|
2022-11-28 15:51:11
|
NixOS/nixpkgs
|
https://api.github.com/repos/NixOS/nixpkgs
|
opened
|
Enabling Elasticsearch (non OSS) on 22.11 fails
|
0.kind: build failure
|
### Steps To Reproduce
Steps to reproduce the behavior:
services.elasticsearch.enable = true;
### Build log
https://gist.github.com/f2k1de/73ca3ac9a74424589ad423eef1eef41f
### Additional context
If services.elasticsearch.package is set to pkgs.elasticsearch-oss it works.
### Notify maintainers
<!--
Please @ people who are in the `meta.maintainers` list of the offending package or module.
If in doubt, check `git blame` for whoever last touched something.
-->
### Metadata
Please run `nix-shell -p nix-info --run "nix-info -m"` and paste the result.
```console
nix-shell -p nix-info --run "nix-info -m"
- system: `"x86_64-linux"`
- host os: `Linux 5.15.79, NixOS, 22.11 (Raccoon), 22.11.20221126.899e7ca`
- multi-user?: `yes`
- sandbox: `yes`
- version: `nix-env (Nix) 2.11.0`
- channels(leah): `""`
- channels(root): `"home-manager-21.11, nixos-21.11.335331.8a70a6808c8"`
- nixpkgs: `/etc/src/nixpkgs`
```
|
1.0
|
Enabling Elasticsearch (non OSS) on 22.11 fails -
### Steps To Reproduce
Steps to reproduce the behavior:
services.elasticsearch.enable = true;
### Build log
https://gist.github.com/f2k1de/73ca3ac9a74424589ad423eef1eef41f
### Additional context
If services.elasticsearch.package is set to pkgs.elasticsearch-oss it works.
### Notify maintainers
<!--
Please @ people who are in the `meta.maintainers` list of the offending package or module.
If in doubt, check `git blame` for whoever last touched something.
-->
### Metadata
Please run `nix-shell -p nix-info --run "nix-info -m"` and paste the result.
```console
nix-shell -p nix-info --run "nix-info -m"
- system: `"x86_64-linux"`
- host os: `Linux 5.15.79, NixOS, 22.11 (Raccoon), 22.11.20221126.899e7ca`
- multi-user?: `yes`
- sandbox: `yes`
- version: `nix-env (Nix) 2.11.0`
- channels(leah): `""`
- channels(root): `"home-manager-21.11, nixos-21.11.335331.8a70a6808c8"`
- nixpkgs: `/etc/src/nixpkgs`
```
|
non_secu
|
enabling elasticsearch non oss on fails steps to reproduce steps to reproduce the behavior services elasticsearch enable true build log additional context if services elasticsearch package is set to pkgs elasticsearch oss it works notify maintainers please people who are in the meta maintainers list of the offending package or module if in doubt check git blame for whoever last touched something metadata please run nix shell p nix info run nix info m and paste the result console nix shell p nix info run nix info m system linux host os linux nixos raccoon multi user yes sandbox yes version nix env nix channels leah channels root home manager nixos nixpkgs etc src nixpkgs
| 0
|
58,996
| 11,935,719,619
|
IssuesEvent
|
2020-04-02 09:04:34
|
Regalis11/Barotrauma
|
https://api.github.com/repos/Regalis11/Barotrauma
|
closed
|
Small Pump does not require power
|
Bug Code
|
I have searched the issue tracker to check if the issue has already been reported.
Version: 0.9.7.1 (Window)
Reactor off, batteries drained to 0, and junction boxes say 0 power available.
Small pump is connected to power grid and its set state input is connected to a switch. It will still pump water out of the sub when switched on.
Sub is attached. Pump is at bottom right, in air lock. You can open and close the air lock to fill it with water and the pump will drain the water even with 0 power available.
[Dogfish.zip](https://github.com/Regalis11/Barotrauma/files/4406940/Dogfish.zip)
|
1.0
|
Small Pump does not require power - I have searched the issue tracker to check if the issue has already been reported.
Version: 0.9.7.1 (Window)
Reactor off, batteries drained to 0, and junction boxes say 0 power available.
Small pump is connected to power grid and its set state input is connected to a switch. It will still pump water out of the sub when switched on.
Sub is attached. Pump is at bottom right, in air lock. You can open and close the air lock to fill it with water and the pump will drain the water even with 0 power available.
[Dogfish.zip](https://github.com/Regalis11/Barotrauma/files/4406940/Dogfish.zip)
|
non_secu
|
small pump does not require power i have searched the issue tracker to check if the issue has already been reported version window reactor off batteries drained to and junction boxes say power available small pump is connected to power grid and its set state input is connected to a switch it will still pump water out of the sub when switched on sub is attached pump is at bottom right in air lock you can open and close the air lock to fill it with water and the pump will drain the water even with power available
| 0
|
136,583
| 18,750,321,313
|
IssuesEvent
|
2021-11-05 00:26:17
|
AlexRogalskiy/github-action-user-contribution
|
https://api.github.com/repos/AlexRogalskiy/github-action-user-contribution
|
closed
|
CVE-2021-32804 (High) detected in tar-2.2.2.tgz, tar-6.1.0.tgz - autoclosed
|
security vulnerability
|
## CVE-2021-32804 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>tar-2.2.2.tgz</b>, <b>tar-6.1.0.tgz</b></p></summary>
<p>
<details><summary><b>tar-2.2.2.tgz</b></p></summary>
<p>tar for node</p>
<p>Library home page: <a href="https://registry.npmjs.org/tar/-/tar-2.2.2.tgz">https://registry.npmjs.org/tar/-/tar-2.2.2.tgz</a></p>
<p>Path to dependency file: github-action-user-contribution/package.json</p>
<p>Path to vulnerable library: github-action-user-contribution/node_modules/dtslint/node_modules/tar/package.json</p>
<p>
Dependency Hierarchy:
- dtslint-4.1.6.tgz (Root Library)
- utils-0.0.91.tgz
- :x: **tar-2.2.2.tgz** (Vulnerable Library)
</details>
<details><summary><b>tar-6.1.0.tgz</b></p></summary>
<p>tar for node</p>
<p>Library home page: <a href="https://registry.npmjs.org/tar/-/tar-6.1.0.tgz">https://registry.npmjs.org/tar/-/tar-6.1.0.tgz</a></p>
<p>Path to dependency file: github-action-user-contribution/package.json</p>
<p>Path to vulnerable library: github-action-user-contribution/node_modules/tar/package.json,github-action-user-contribution/node_modules/npm/node_modules/tar/package.json</p>
<p>
Dependency Hierarchy:
- editorconfig-checker-4.0.2.tgz (Root Library)
- :x: **tar-6.1.0.tgz** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/AlexRogalskiy/github-action-user-contribution/commit/ff36aa255408dae983ba3ce55f6a432a63ee8665">ff36aa255408dae983ba3ce55f6a432a63ee8665</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
The npm package "tar" (aka node-tar) before versions 6.1.1, 5.0.6, 4.4.14, and 3.3.2 has a arbitrary File Creation/Overwrite vulnerability due to insufficient absolute path sanitization. node-tar aims to prevent extraction of absolute file paths by turning absolute paths into relative paths when the `preservePaths` flag is not set to `true`. This is achieved by stripping the absolute path root from any absolute file paths contained in a tar file. For example `/home/user/.bashrc` would turn into `home/user/.bashrc`. This logic was insufficient when file paths contained repeated path roots such as `////home/user/.bashrc`. `node-tar` would only strip a single path root from such paths. When given an absolute file path with repeating path roots, the resulting path (e.g. `///home/user/.bashrc`) would still resolve to an absolute path, thus allowing arbitrary file creation and overwrite. This issue was addressed in releases 3.2.2, 4.4.14, 5.0.6 and 6.1.1. Users may work around this vulnerability without upgrading by creating a custom `onentry` method which sanitizes the `entry.path` or a `filter` method which removes entries with absolute paths. See referenced GitHub Advisory for details. Be aware of CVE-2021-32803 which fixes a similar bug in later versions of tar.
<p>Publish Date: 2021-08-03
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-32804>CVE-2021-32804</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>8.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/npm/node-tar/security/advisories/GHSA-3jfq-g458-7qm9">https://github.com/npm/node-tar/security/advisories/GHSA-3jfq-g458-7qm9</a></p>
<p>Release Date: 2021-08-03</p>
<p>Fix Resolution: tar - 3.2.2, 4.4.14, 5.0.6, 6.1.1</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2021-32804 (High) detected in tar-2.2.2.tgz, tar-6.1.0.tgz - autoclosed - ## CVE-2021-32804 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>tar-2.2.2.tgz</b>, <b>tar-6.1.0.tgz</b></p></summary>
<p>
<details><summary><b>tar-2.2.2.tgz</b></p></summary>
<p>tar for node</p>
<p>Library home page: <a href="https://registry.npmjs.org/tar/-/tar-2.2.2.tgz">https://registry.npmjs.org/tar/-/tar-2.2.2.tgz</a></p>
<p>Path to dependency file: github-action-user-contribution/package.json</p>
<p>Path to vulnerable library: github-action-user-contribution/node_modules/dtslint/node_modules/tar/package.json</p>
<p>
Dependency Hierarchy:
- dtslint-4.1.6.tgz (Root Library)
- utils-0.0.91.tgz
- :x: **tar-2.2.2.tgz** (Vulnerable Library)
</details>
<details><summary><b>tar-6.1.0.tgz</b></p></summary>
<p>tar for node</p>
<p>Library home page: <a href="https://registry.npmjs.org/tar/-/tar-6.1.0.tgz">https://registry.npmjs.org/tar/-/tar-6.1.0.tgz</a></p>
<p>Path to dependency file: github-action-user-contribution/package.json</p>
<p>Path to vulnerable library: github-action-user-contribution/node_modules/tar/package.json,github-action-user-contribution/node_modules/npm/node_modules/tar/package.json</p>
<p>
Dependency Hierarchy:
- editorconfig-checker-4.0.2.tgz (Root Library)
- :x: **tar-6.1.0.tgz** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/AlexRogalskiy/github-action-user-contribution/commit/ff36aa255408dae983ba3ce55f6a432a63ee8665">ff36aa255408dae983ba3ce55f6a432a63ee8665</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
The npm package "tar" (aka node-tar) before versions 6.1.1, 5.0.6, 4.4.14, and 3.3.2 has a arbitrary File Creation/Overwrite vulnerability due to insufficient absolute path sanitization. node-tar aims to prevent extraction of absolute file paths by turning absolute paths into relative paths when the `preservePaths` flag is not set to `true`. This is achieved by stripping the absolute path root from any absolute file paths contained in a tar file. For example `/home/user/.bashrc` would turn into `home/user/.bashrc`. This logic was insufficient when file paths contained repeated path roots such as `////home/user/.bashrc`. `node-tar` would only strip a single path root from such paths. When given an absolute file path with repeating path roots, the resulting path (e.g. `///home/user/.bashrc`) would still resolve to an absolute path, thus allowing arbitrary file creation and overwrite. This issue was addressed in releases 3.2.2, 4.4.14, 5.0.6 and 6.1.1. Users may work around this vulnerability without upgrading by creating a custom `onentry` method which sanitizes the `entry.path` or a `filter` method which removes entries with absolute paths. See referenced GitHub Advisory for details. Be aware of CVE-2021-32803 which fixes a similar bug in later versions of tar.
<p>Publish Date: 2021-08-03
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-32804>CVE-2021-32804</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>8.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/npm/node-tar/security/advisories/GHSA-3jfq-g458-7qm9">https://github.com/npm/node-tar/security/advisories/GHSA-3jfq-g458-7qm9</a></p>
<p>Release Date: 2021-08-03</p>
<p>Fix Resolution: tar - 3.2.2, 4.4.14, 5.0.6, 6.1.1</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve high detected in tar tgz tar tgz autoclosed cve high severity vulnerability vulnerable libraries tar tgz tar tgz tar tgz tar for node library home page a href path to dependency file github action user contribution package json path to vulnerable library github action user contribution node modules dtslint node modules tar package json dependency hierarchy dtslint tgz root library utils tgz x tar tgz vulnerable library tar tgz tar for node library home page a href path to dependency file github action user contribution package json path to vulnerable library github action user contribution node modules tar package json github action user contribution node modules npm node modules tar package json dependency hierarchy editorconfig checker tgz root library x tar tgz vulnerable library found in head commit a href vulnerability details the npm package tar aka node tar before versions and has a arbitrary file creation overwrite vulnerability due to insufficient absolute path sanitization node tar aims to prevent extraction of absolute file paths by turning absolute paths into relative paths when the preservepaths flag is not set to true this is achieved by stripping the absolute path root from any absolute file paths contained in a tar file for example home user bashrc would turn into home user bashrc this logic was insufficient when file paths contained repeated path roots such as home user bashrc node tar would only strip a single path root from such paths when given an absolute file path with repeating path roots the resulting path e g home user bashrc would still resolve to an absolute path thus allowing arbitrary file creation and overwrite this issue was addressed in releases and users may work around this vulnerability without upgrading by creating a custom onentry method which sanitizes the entry path or a filter method which removes entries with absolute paths see referenced github advisory for details be aware of cve which fixes a similar bug in later versions of tar publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact none integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution tar step up your open source security game with whitesource
| 1
|
170,076
| 20,842,010,806
|
IssuesEvent
|
2022-03-21 02:04:55
|
n-devs/create-library-react
|
https://api.github.com/repos/n-devs/create-library-react
|
opened
|
CVE-2022-24772 (High) detected in node-forge-0.7.5.tgz
|
security vulnerability
|
## CVE-2022-24772 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>node-forge-0.7.5.tgz</b></p></summary>
<p>JavaScript implementations of network transports, cryptography, ciphers, PKI, message digests, and various utilities.</p>
<p>Library home page: <a href="https://registry.npmjs.org/node-forge/-/node-forge-0.7.5.tgz">https://registry.npmjs.org/node-forge/-/node-forge-0.7.5.tgz</a></p>
<p>Path to dependency file: /create-library-react/template/default/packages/package-name.1/package.json</p>
<p>Path to vulnerable library: /template/default/packages/package-name.1/node_modules/node-forge/package.json,/template/default/packages/package-name.1/node_modules/node-forge/package.json</p>
<p>
Dependency Hierarchy:
- react-scripts-1.1.5.tgz (Root Library)
- webpack-dev-server-2.11.3.tgz
- selfsigned-1.10.4.tgz
- :x: **node-forge-0.7.5.tgz** (Vulnerable Library)
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Forge (also called `node-forge`) is a native implementation of Transport Layer Security in JavaScript. Prior to version 1.3.0, RSA PKCS#1 v1.5 signature verification code does not check for tailing garbage bytes after decoding a `DigestInfo` ASN.1 structure. This can allow padding bytes to be removed and garbage data added to forge a signature when a low public exponent is being used. The issue has been addressed in `node-forge` version 1.3.0. There are currently no known workarounds.
<p>Publish Date: 2022-03-18
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2022-24772>CVE-2022-24772</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: High
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-24772">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-24772</a></p>
<p>Release Date: 2022-03-18</p>
<p>Fix Resolution: node-forge - 1.3.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2022-24772 (High) detected in node-forge-0.7.5.tgz - ## CVE-2022-24772 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>node-forge-0.7.5.tgz</b></p></summary>
<p>JavaScript implementations of network transports, cryptography, ciphers, PKI, message digests, and various utilities.</p>
<p>Library home page: <a href="https://registry.npmjs.org/node-forge/-/node-forge-0.7.5.tgz">https://registry.npmjs.org/node-forge/-/node-forge-0.7.5.tgz</a></p>
<p>Path to dependency file: /create-library-react/template/default/packages/package-name.1/package.json</p>
<p>Path to vulnerable library: /template/default/packages/package-name.1/node_modules/node-forge/package.json,/template/default/packages/package-name.1/node_modules/node-forge/package.json</p>
<p>
Dependency Hierarchy:
- react-scripts-1.1.5.tgz (Root Library)
- webpack-dev-server-2.11.3.tgz
- selfsigned-1.10.4.tgz
- :x: **node-forge-0.7.5.tgz** (Vulnerable Library)
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Forge (also called `node-forge`) is a native implementation of Transport Layer Security in JavaScript. Prior to version 1.3.0, RSA PKCS#1 v1.5 signature verification code does not check for tailing garbage bytes after decoding a `DigestInfo` ASN.1 structure. This can allow padding bytes to be removed and garbage data added to forge a signature when a low public exponent is being used. The issue has been addressed in `node-forge` version 1.3.0. There are currently no known workarounds.
<p>Publish Date: 2022-03-18
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2022-24772>CVE-2022-24772</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: High
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-24772">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-24772</a></p>
<p>Release Date: 2022-03-18</p>
<p>Fix Resolution: node-forge - 1.3.0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve high detected in node forge tgz cve high severity vulnerability vulnerable library node forge tgz javascript implementations of network transports cryptography ciphers pki message digests and various utilities library home page a href path to dependency file create library react template default packages package name package json path to vulnerable library template default packages package name node modules node forge package json template default packages package name node modules node forge package json dependency hierarchy react scripts tgz root library webpack dev server tgz selfsigned tgz x node forge tgz vulnerable library vulnerability details forge also called node forge is a native implementation of transport layer security in javascript prior to version rsa pkcs signature verification code does not check for tailing garbage bytes after decoding a digestinfo asn structure this can allow padding bytes to be removed and garbage data added to forge a signature when a low public exponent is being used the issue has been addressed in node forge version there are currently no known workarounds publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact high availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution node forge step up your open source security game with whitesource
| 1
|
265,161
| 28,244,719,405
|
IssuesEvent
|
2023-04-06 09:50:26
|
hshivhare67/platform_packages_apps_settings_AOSP10_r33
|
https://api.github.com/repos/hshivhare67/platform_packages_apps_settings_AOSP10_r33
|
closed
|
CVE-2021-0333 (High) detected in Settingsandroid-10.0.0_r33 - autoclosed
|
Mend: dependency security vulnerability
|
## CVE-2021-0333 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>Settingsandroid-10.0.0_r33</b></p></summary>
<p>
<p>Library home page: <a href=https://android.googlesource.com/platform/packages/apps/Settings>https://android.googlesource.com/platform/packages/apps/Settings</a></p>
<p>Found in HEAD commit: <a href="https://github.com/hshivhare67/platform_packages_apps_settings_AOSP10_r33/commit/7291ac75aa6d2751664c7e2230a19c28c6e54cc8">7291ac75aa6d2751664c7e2230a19c28c6e54cc8</a></p>
<p>Found in base branch: <b>main</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (1)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/src/com/android/settings/bluetooth/BluetoothPermissionActivity.java</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
In onCreate of BluetoothPermissionActivity.java, there is a possible permissions bypass due to a tapjacking overlay that obscures the phonebook permissions dialog when a Bluetooth device is connecting. This could lead to local escalation of privilege with User execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-8.1 Android-9 Android-10 Android-11Android ID: A-168504491
<p>Publish Date: 2021-02-10
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2021-0333>CVE-2021-0333</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://source.android.com/security/bulletin/2021-02-01">https://source.android.com/security/bulletin/2021-02-01</a></p>
<p>Release Date: 2021-02-10</p>
<p>Fix Resolution: android-11.0.0_r29</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2021-0333 (High) detected in Settingsandroid-10.0.0_r33 - autoclosed - ## CVE-2021-0333 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>Settingsandroid-10.0.0_r33</b></p></summary>
<p>
<p>Library home page: <a href=https://android.googlesource.com/platform/packages/apps/Settings>https://android.googlesource.com/platform/packages/apps/Settings</a></p>
<p>Found in HEAD commit: <a href="https://github.com/hshivhare67/platform_packages_apps_settings_AOSP10_r33/commit/7291ac75aa6d2751664c7e2230a19c28c6e54cc8">7291ac75aa6d2751664c7e2230a19c28c6e54cc8</a></p>
<p>Found in base branch: <b>main</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (1)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/src/com/android/settings/bluetooth/BluetoothPermissionActivity.java</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
In onCreate of BluetoothPermissionActivity.java, there is a possible permissions bypass due to a tapjacking overlay that obscures the phonebook permissions dialog when a Bluetooth device is connecting. This could lead to local escalation of privilege with User execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android-8.1 Android-9 Android-10 Android-11Android ID: A-168504491
<p>Publish Date: 2021-02-10
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2021-0333>CVE-2021-0333</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://source.android.com/security/bulletin/2021-02-01">https://source.android.com/security/bulletin/2021-02-01</a></p>
<p>Release Date: 2021-02-10</p>
<p>Fix Resolution: android-11.0.0_r29</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
secu
|
cve high detected in settingsandroid autoclosed cve high severity vulnerability vulnerable library settingsandroid library home page a href found in head commit a href found in base branch main vulnerable source files src com android settings bluetooth bluetoothpermissionactivity java vulnerability details in oncreate of bluetoothpermissionactivity java there is a possible permissions bypass due to a tapjacking overlay that obscures the phonebook permissions dialog when a bluetooth device is connecting this could lead to local escalation of privilege with user execution privileges needed user interaction is needed for exploitation product androidversions android android android android id a publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required low user interaction required scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution android step up your open source security game with mend
| 1
|
606,288
| 18,759,124,659
|
IssuesEvent
|
2021-11-05 14:32:14
|
eoscostarica/eos-rate
|
https://api.github.com/repos/eoscostarica/eos-rate
|
closed
|
Snackbar component alignment
|
low priority
|
Please make sure all snackbar components are centered horizontally. Although I do not have a screenshot I've spotted error messages showing aligned to the left. Thanks.
|
1.0
|
Snackbar component alignment - Please make sure all snackbar components are centered horizontally. Although I do not have a screenshot I've spotted error messages showing aligned to the left. Thanks.
|
non_secu
|
snackbar component alignment please make sure all snackbar components are centered horizontally although i do not have a screenshot i ve spotted error messages showing aligned to the left thanks
| 0
|
92,676
| 11,697,277,224
|
IssuesEvent
|
2020-03-06 11:27:49
|
TouK/nussknacker
|
https://api.github.com/repos/TouK/nussknacker
|
closed
|
sliding panels UX
|
design needed ui
|
- they look coarse, there are better ways (handle bars)
- right one could be reactive
|
1.0
|
sliding panels UX - - they look coarse, there are better ways (handle bars)
- right one could be reactive
|
non_secu
|
sliding panels ux they look coarse there are better ways handle bars right one could be reactive
| 0
|
157,111
| 19,914,025,232
|
IssuesEvent
|
2022-01-25 20:19:59
|
dmyers87/LetsPoint
|
https://api.github.com/repos/dmyers87/LetsPoint
|
opened
|
CVE-2020-15168 (Medium) detected in multiple libraries
|
security vulnerability
|
## CVE-2020-15168 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>node-fetch-1.7.3.tgz</b>, <b>node-fetch-2.6.0.tgz</b>, <b>node-fetch-2.3.0.tgz</b></p></summary>
<p>
<details><summary><b>node-fetch-1.7.3.tgz</b></p></summary>
<p>A light-weight module that brings window.fetch to node.js and io.js</p>
<p>Library home page: <a href="https://registry.npmjs.org/node-fetch/-/node-fetch-1.7.3.tgz">https://registry.npmjs.org/node-fetch/-/node-fetch-1.7.3.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/node-fetch/package.json</p>
<p>
Dependency Hierarchy:
- firebase-5.11.1.tgz (Root Library)
- functions-0.4.6.tgz
- isomorphic-fetch-2.2.1.tgz
- :x: **node-fetch-1.7.3.tgz** (Vulnerable Library)
</details>
<details><summary><b>node-fetch-2.6.0.tgz</b></p></summary>
<p>A light-weight module that brings window.fetch to node.js</p>
<p>Library home page: <a href="https://registry.npmjs.org/node-fetch/-/node-fetch-2.6.0.tgz">https://registry.npmjs.org/node-fetch/-/node-fetch-2.6.0.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/next/node_modules/node-fetch/package.json</p>
<p>
Dependency Hierarchy:
- next-9.3.2.tgz (Root Library)
- :x: **node-fetch-2.6.0.tgz** (Vulnerable Library)
</details>
<details><summary><b>node-fetch-2.3.0.tgz</b></p></summary>
<p>A light-weight module that brings window.fetch to node.js</p>
<p>Library home page: <a href="https://registry.npmjs.org/node-fetch/-/node-fetch-2.3.0.tgz">https://registry.npmjs.org/node-fetch/-/node-fetch-2.3.0.tgz</a></p>
<p>
Dependency Hierarchy:
- firebase-admin-6.0.0.tgz (Root Library)
- firestore-0.16.1.tgz
- google-gax-0.18.0.tgz
- google-auth-library-1.6.1.tgz
- gtoken-2.3.2.tgz
- gaxios-1.2.6.tgz
- :x: **node-fetch-2.3.0.tgz** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/dmyers87/LetsPoint/commit/ef071cedc5c90dbf675bdff906a563e386e3386a">ef071cedc5c90dbf675bdff906a563e386e3386a</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
node-fetch before versions 2.6.1 and 3.0.0-beta.9 did not honor the size option after following a redirect, which means that when a content size was over the limit, a FetchError would never get thrown and the process would end without failure. For most people, this fix will have a little or no impact. However, if you are relying on node-fetch to gate files above a size, the impact could be significant, for example: If you don't double-check the size of the data after fetch() has completed, your JS thread could get tied up doing work on a large file (DoS) and/or cost you money in computing.
<p>Publish Date: 2020-09-10
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-15168>CVE-2020-15168</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/node-fetch/node-fetch/security/advisories/GHSA-w7rc-rwvf-8q5r">https://github.com/node-fetch/node-fetch/security/advisories/GHSA-w7rc-rwvf-8q5r</a></p>
<p>Release Date: 2020-09-17</p>
<p>Fix Resolution: 2.6.1,3.0.0-beta.9</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"node-fetch","packageVersion":"1.7.3","packageFilePaths":["/package.json"],"isTransitiveDependency":true,"dependencyTree":"firebase:5.11.1;@firebase/functions:0.4.6;isomorphic-fetch:2.2.1;node-fetch:1.7.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.6.1,3.0.0-beta.9","isBinary":false},{"packageType":"javascript/Node.js","packageName":"node-fetch","packageVersion":"2.6.0","packageFilePaths":["/package.json"],"isTransitiveDependency":true,"dependencyTree":"next:9.3.2;node-fetch:2.6.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.6.1,3.0.0-beta.9","isBinary":false},{"packageType":"javascript/Node.js","packageName":"node-fetch","packageVersion":"2.3.0","packageFilePaths":[null],"isTransitiveDependency":true,"dependencyTree":"firebase-admin:6.0.0;@google-cloud/firestore:0.16.1;google-gax:0.18.0;google-auth-library:1.6.1;gtoken:2.3.2;gaxios:1.2.6;node-fetch:2.3.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.6.1,3.0.0-beta.9","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2020-15168","vulnerabilityDetails":"node-fetch before versions 2.6.1 and 3.0.0-beta.9 did not honor the size option after following a redirect, which means that when a content size was over the limit, a FetchError would never get thrown and the process would end without failure. For most people, this fix will have a little or no impact. However, if you are relying on node-fetch to gate files above a size, the impact could be significant, for example: If you don\u0027t double-check the size of the data after fetch() has completed, your JS thread could get tied up doing work on a large file (DoS) and/or cost you money in computing.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-15168","cvss3Severity":"medium","cvss3Score":"5.3","cvss3Metrics":{"A":"Low","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}}</REMEDIATE> -->
|
True
|
CVE-2020-15168 (Medium) detected in multiple libraries - ## CVE-2020-15168 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Libraries - <b>node-fetch-1.7.3.tgz</b>, <b>node-fetch-2.6.0.tgz</b>, <b>node-fetch-2.3.0.tgz</b></p></summary>
<p>
<details><summary><b>node-fetch-1.7.3.tgz</b></p></summary>
<p>A light-weight module that brings window.fetch to node.js and io.js</p>
<p>Library home page: <a href="https://registry.npmjs.org/node-fetch/-/node-fetch-1.7.3.tgz">https://registry.npmjs.org/node-fetch/-/node-fetch-1.7.3.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/node-fetch/package.json</p>
<p>
Dependency Hierarchy:
- firebase-5.11.1.tgz (Root Library)
- functions-0.4.6.tgz
- isomorphic-fetch-2.2.1.tgz
- :x: **node-fetch-1.7.3.tgz** (Vulnerable Library)
</details>
<details><summary><b>node-fetch-2.6.0.tgz</b></p></summary>
<p>A light-weight module that brings window.fetch to node.js</p>
<p>Library home page: <a href="https://registry.npmjs.org/node-fetch/-/node-fetch-2.6.0.tgz">https://registry.npmjs.org/node-fetch/-/node-fetch-2.6.0.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/next/node_modules/node-fetch/package.json</p>
<p>
Dependency Hierarchy:
- next-9.3.2.tgz (Root Library)
- :x: **node-fetch-2.6.0.tgz** (Vulnerable Library)
</details>
<details><summary><b>node-fetch-2.3.0.tgz</b></p></summary>
<p>A light-weight module that brings window.fetch to node.js</p>
<p>Library home page: <a href="https://registry.npmjs.org/node-fetch/-/node-fetch-2.3.0.tgz">https://registry.npmjs.org/node-fetch/-/node-fetch-2.3.0.tgz</a></p>
<p>
Dependency Hierarchy:
- firebase-admin-6.0.0.tgz (Root Library)
- firestore-0.16.1.tgz
- google-gax-0.18.0.tgz
- google-auth-library-1.6.1.tgz
- gtoken-2.3.2.tgz
- gaxios-1.2.6.tgz
- :x: **node-fetch-2.3.0.tgz** (Vulnerable Library)
</details>
<p>Found in HEAD commit: <a href="https://github.com/dmyers87/LetsPoint/commit/ef071cedc5c90dbf675bdff906a563e386e3386a">ef071cedc5c90dbf675bdff906a563e386e3386a</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
node-fetch before versions 2.6.1 and 3.0.0-beta.9 did not honor the size option after following a redirect, which means that when a content size was over the limit, a FetchError would never get thrown and the process would end without failure. For most people, this fix will have a little or no impact. However, if you are relying on node-fetch to gate files above a size, the impact could be significant, for example: If you don't double-check the size of the data after fetch() has completed, your JS thread could get tied up doing work on a large file (DoS) and/or cost you money in computing.
<p>Publish Date: 2020-09-10
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-15168>CVE-2020-15168</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.3</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: Low
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/node-fetch/node-fetch/security/advisories/GHSA-w7rc-rwvf-8q5r">https://github.com/node-fetch/node-fetch/security/advisories/GHSA-w7rc-rwvf-8q5r</a></p>
<p>Release Date: 2020-09-17</p>
<p>Fix Resolution: 2.6.1,3.0.0-beta.9</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"javascript/Node.js","packageName":"node-fetch","packageVersion":"1.7.3","packageFilePaths":["/package.json"],"isTransitiveDependency":true,"dependencyTree":"firebase:5.11.1;@firebase/functions:0.4.6;isomorphic-fetch:2.2.1;node-fetch:1.7.3","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.6.1,3.0.0-beta.9","isBinary":false},{"packageType":"javascript/Node.js","packageName":"node-fetch","packageVersion":"2.6.0","packageFilePaths":["/package.json"],"isTransitiveDependency":true,"dependencyTree":"next:9.3.2;node-fetch:2.6.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.6.1,3.0.0-beta.9","isBinary":false},{"packageType":"javascript/Node.js","packageName":"node-fetch","packageVersion":"2.3.0","packageFilePaths":[null],"isTransitiveDependency":true,"dependencyTree":"firebase-admin:6.0.0;@google-cloud/firestore:0.16.1;google-gax:0.18.0;google-auth-library:1.6.1;gtoken:2.3.2;gaxios:1.2.6;node-fetch:2.3.0","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.6.1,3.0.0-beta.9","isBinary":false}],"baseBranches":["master"],"vulnerabilityIdentifier":"CVE-2020-15168","vulnerabilityDetails":"node-fetch before versions 2.6.1 and 3.0.0-beta.9 did not honor the size option after following a redirect, which means that when a content size was over the limit, a FetchError would never get thrown and the process would end without failure. For most people, this fix will have a little or no impact. However, if you are relying on node-fetch to gate files above a size, the impact could be significant, for example: If you don\u0027t double-check the size of the data after fetch() has completed, your JS thread could get tied up doing work on a large file (DoS) and/or cost you money in computing.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-15168","cvss3Severity":"medium","cvss3Score":"5.3","cvss3Metrics":{"A":"Low","AC":"Low","PR":"None","S":"Unchanged","C":"None","UI":"None","AV":"Network","I":"None"},"extraData":{}}</REMEDIATE> -->
|
secu
|
cve medium detected in multiple libraries cve medium severity vulnerability vulnerable libraries node fetch tgz node fetch tgz node fetch tgz node fetch tgz a light weight module that brings window fetch to node js and io js library home page a href path to dependency file package json path to vulnerable library node modules node fetch package json dependency hierarchy firebase tgz root library functions tgz isomorphic fetch tgz x node fetch tgz vulnerable library node fetch tgz a light weight module that brings window fetch to node js library home page a href path to dependency file package json path to vulnerable library node modules next node modules node fetch package json dependency hierarchy next tgz root library x node fetch tgz vulnerable library node fetch tgz a light weight module that brings window fetch to node js library home page a href dependency hierarchy firebase admin tgz root library firestore tgz google gax tgz google auth library tgz gtoken tgz gaxios tgz x node fetch tgz vulnerable library found in head commit a href found in base branch master vulnerability details node fetch before versions and beta did not honor the size option after following a redirect which means that when a content size was over the limit a fetcherror would never get thrown and the process would end without failure for most people this fix will have a little or no impact however if you are relying on node fetch to gate files above a size the impact could be significant for example if you don t double check the size of the data after fetch has completed your js thread could get tied up doing work on a large file dos and or cost you money in computing publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact low for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution beta isopenpronvulnerability true ispackagebased true isdefaultbranch true packages istransitivedependency true dependencytree firebase firebase functions isomorphic fetch node fetch isminimumfixversionavailable true minimumfixversion beta isbinary false packagetype javascript node js packagename node fetch packageversion packagefilepaths istransitivedependency true dependencytree next node fetch isminimumfixversionavailable true minimumfixversion beta isbinary false packagetype javascript node js packagename node fetch packageversion packagefilepaths istransitivedependency true dependencytree firebase admin google cloud firestore google gax google auth library gtoken gaxios node fetch isminimumfixversionavailable true minimumfixversion beta isbinary false basebranches vulnerabilityidentifier cve vulnerabilitydetails node fetch before versions and beta did not honor the size option after following a redirect which means that when a content size was over the limit a fetcherror would never get thrown and the process would end without failure for most people this fix will have a little or no impact however if you are relying on node fetch to gate files above a size the impact could be significant for example if you don double check the size of the data after fetch has completed your js thread could get tied up doing work on a large file dos and or cost you money in computing vulnerabilityurl
| 1
|
191,301
| 15,284,214,301
|
IssuesEvent
|
2021-02-23 11:55:48
|
neuronsimulator/nrn
|
https://api.github.com/repos/neuronsimulator/nrn
|
closed
|
Linux install instructions recommend installing Python packages from apt
|
documentation enhancement
|
The section here https://github.com/neuronsimulator/nrn/blob/master/INSTALL.md#linux-1 recommends installing several Python dependencies from `apt`. This is a nono as they will always install the dependency to the system pythons, which might not be what the user wants. On top of that there is a much larger delay in releases of these distro packages than the pypi packages. I'd recommend to substitute them for a `pip install numpy scipy cython`, as the user is more likely to understand the implications of that command.
|
1.0
|
Linux install instructions recommend installing Python packages from apt - The section here https://github.com/neuronsimulator/nrn/blob/master/INSTALL.md#linux-1 recommends installing several Python dependencies from `apt`. This is a nono as they will always install the dependency to the system pythons, which might not be what the user wants. On top of that there is a much larger delay in releases of these distro packages than the pypi packages. I'd recommend to substitute them for a `pip install numpy scipy cython`, as the user is more likely to understand the implications of that command.
|
non_secu
|
linux install instructions recommend installing python packages from apt the section here recommends installing several python dependencies from apt this is a nono as they will always install the dependency to the system pythons which might not be what the user wants on top of that there is a much larger delay in releases of these distro packages than the pypi packages i d recommend to substitute them for a pip install numpy scipy cython as the user is more likely to understand the implications of that command
| 0
|
66,948
| 20,776,031,458
|
IssuesEvent
|
2022-03-16 10:33:34
|
vector-im/element-web
|
https://api.github.com/repos/vector-im/element-web
|
opened
|
Most of the timeline is missing
|
T-Defect
|
### Steps to reproduce
1. Enter a room
2. Notice there is an upward arrow to scroll up to unread messages
3. Scroll up, but there is nothing to see
### Outcome
#### What did you expect?
I know there are more messages in this room, and I expected to see them.
#### What happened instead?
I see only a couple of messages, and empty space above them.
### Operating system
Ubuntu 21.10
### Browser information
Firefox 98.0
### URL for webapp
https://develop.element.io
### Application version
Element version: 1f97bc23256a-react-26e6f8deca1d-js-18943d6519e9 Olm version: 3.2.8
### Homeserver
matrix.org
### Will you send logs?
Yes
|
1.0
|
Most of the timeline is missing - ### Steps to reproduce
1. Enter a room
2. Notice there is an upward arrow to scroll up to unread messages
3. Scroll up, but there is nothing to see
### Outcome
#### What did you expect?
I know there are more messages in this room, and I expected to see them.
#### What happened instead?
I see only a couple of messages, and empty space above them.
### Operating system
Ubuntu 21.10
### Browser information
Firefox 98.0
### URL for webapp
https://develop.element.io
### Application version
Element version: 1f97bc23256a-react-26e6f8deca1d-js-18943d6519e9 Olm version: 3.2.8
### Homeserver
matrix.org
### Will you send logs?
Yes
|
non_secu
|
most of the timeline is missing steps to reproduce enter a room notice there is an upward arrow to scroll up to unread messages scroll up but there is nothing to see outcome what did you expect i know there are more messages in this room and i expected to see them what happened instead i see only a couple of messages and empty space above them operating system ubuntu browser information firefox url for webapp application version element version react js olm version homeserver matrix org will you send logs yes
| 0
|
11,536
| 8,405,833,655
|
IssuesEvent
|
2018-10-11 16:12:58
|
MicrosoftDocs/windows-itpro-docs
|
https://api.github.com/repos/MicrosoftDocs/windows-itpro-docs
|
closed
|
Office 365 Pro Plus 1808 and ProductName
|
assigned-to-author information protection security
|
In 1808 version of Office 365 Pro Plus you updated the product name to "Microsoft Office" from "Microsoft Office 2016" which has resulted in previously working enlightened apps for WIP stopping to work if you leveraged template in ZIP.. XML linked in ZIP above also is not updated...
The root cause of this problem is that in your XML, you have an explicit DENY for "Microsoft Office" while you chose to name the latest 1808 product to Microsoft Office. For others who may have used the XML as a base template removing this DENY and updating references from Office 2016 to Office resolved any WIP issues.
---
#### Document Details
⚠ *Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.*
* ID: b5ed0150-0172-f3ad-3c7f-3a7141efbe64
* Version Independent ID: 6a978d2b-a0ff-1052-ce00-06f02f30cfa1
* Content: [List of enlightened Microsoft apps for use with Windows Information Protection (WIP) (Windows 10)](https://docs.microsoft.com/en-us/windows/security/information-protection/windows-information-protection/enlightened-microsoft-apps-and-wip)
* Content Source: [windows/security/information-protection/windows-information-protection/enlightened-microsoft-apps-and-wip.md](https://github.com/MicrosoftDocs/windows-itpro-docs/blob/master/windows/security/information-protection/windows-information-protection/enlightened-microsoft-apps-and-wip.md)
* Product: **w10**
* GitHub Login: @Justinha
* Microsoft Alias: **justinha**
|
True
|
Office 365 Pro Plus 1808 and ProductName - In 1808 version of Office 365 Pro Plus you updated the product name to "Microsoft Office" from "Microsoft Office 2016" which has resulted in previously working enlightened apps for WIP stopping to work if you leveraged template in ZIP.. XML linked in ZIP above also is not updated...
The root cause of this problem is that in your XML, you have an explicit DENY for "Microsoft Office" while you chose to name the latest 1808 product to Microsoft Office. For others who may have used the XML as a base template removing this DENY and updating references from Office 2016 to Office resolved any WIP issues.
---
#### Document Details
⚠ *Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.*
* ID: b5ed0150-0172-f3ad-3c7f-3a7141efbe64
* Version Independent ID: 6a978d2b-a0ff-1052-ce00-06f02f30cfa1
* Content: [List of enlightened Microsoft apps for use with Windows Information Protection (WIP) (Windows 10)](https://docs.microsoft.com/en-us/windows/security/information-protection/windows-information-protection/enlightened-microsoft-apps-and-wip)
* Content Source: [windows/security/information-protection/windows-information-protection/enlightened-microsoft-apps-and-wip.md](https://github.com/MicrosoftDocs/windows-itpro-docs/blob/master/windows/security/information-protection/windows-information-protection/enlightened-microsoft-apps-and-wip.md)
* Product: **w10**
* GitHub Login: @Justinha
* Microsoft Alias: **justinha**
|
secu
|
office pro plus and productname in version of office pro plus you updated the product name to microsoft office from microsoft office which has resulted in previously working enlightened apps for wip stopping to work if you leveraged template in zip xml linked in zip above also is not updated the root cause of this problem is that in your xml you have an explicit deny for microsoft office while you chose to name the latest product to microsoft office for others who may have used the xml as a base template removing this deny and updating references from office to office resolved any wip issues document details ⚠ do not edit this section it is required for docs microsoft com ➟ github issue linking id version independent id content content source product github login justinha microsoft alias justinha
| 1
|
674,900
| 23,069,440,991
|
IssuesEvent
|
2022-07-25 16:35:08
|
dotnet/runtime
|
https://api.github.com/repos/dotnet/runtime
|
closed
|
System.Text.RegularExpressions work planned for .NET 7
|
Epic area-System.Text.RegularExpressions Priority:1 Team:Libraries
|
**This issue captures the planned work for .NET 7. This list is expected to change throughout the release cycle according to ongoing planning and discussions, with possible additions and subtractions to the scope.**
## Summary
There are currently several efforts for fixing/improving our RegularExpressions engines. This includes test coverage efforts, perf-enhancing efforts, but a lot of new feature work as well. Even though we have individual issues for most of these efforts, this is meant to serve as an all-up tracking issue which shows all of these efforts and their category. Some issues could probably be placed in more than one category, but I tried to pick whichever category had the highest order bit for each. The list here will be updated with new work as it comes up, as well as with expected shipping milestones when we think some of them will land.
## Planned for .NET 7
### Main Regex Investments
- [x] P0: [NonBacktracking] #57891
- [x] P0: [Source Generator] #44676
- [x] P0: [All Engines] #59629
- [x] P0: [All Engines] #61048
- [ ] P0: [All Engines] #59492
- [x] P1: [All Engines] #62449
- [x] P1: [All Engines] #65011
- [ ] P2: [Source Generator with NonBacktracking] #61903
- [x] P1: #68147
### API Proposals
- [x] P2: #62603
- [x] P2: #61425
- [ ] P2: #62573
### General Perf Improvements
- [x] P1: #62670
- [x] P1: #62676
- [x] P2: #62723
- [x] P2: #62669
- [x] P2: #62677
- [x] P2: #62445
- [x] P2: #62450
- [x] P2: #62459
### General Improvements
- [ ] P1: #62619
- [x] P2: #62651
- [x] P2: #62650
- [ ] P2: #60917
- [ ] P2: #48972
- [ ] P2: #58786
### Improve Test Coverage
- [ ] P1: #61893
- [ ] P2: #61896
- [ ] P2: #61895
- [ ] P2: #61894
- [x] P1: #60753
- [x] P1: #60697
### Non-Backtracking Engine Fixes and Improvements
- [x] P0: #61904
- [x] P0: #60918
- [x] P1: #60645
- [x] P1: #60623
### Source Generator Fixes and Style Improvements
- [x] P0: #59491
- [x] P1: #62647
- [x] P2: #62715
- [x] P2: #62657
- [x] P2: #61666
- [ ] P2: #62441
- [x] P2: #62438
### Performance Regressions That Need Fixing
- [x] P0: #61972
### Performance Investigations
- [x] P2: #62697
- [x] P2: #62451
- [ ] P2: #62447
- [ ] P2: #62443
cc: @stephentoub @danmoseley @olsaarik @veanes
|
1.0
|
System.Text.RegularExpressions work planned for .NET 7 - **This issue captures the planned work for .NET 7. This list is expected to change throughout the release cycle according to ongoing planning and discussions, with possible additions and subtractions to the scope.**
## Summary
There are currently several efforts for fixing/improving our RegularExpressions engines. This includes test coverage efforts, perf-enhancing efforts, but a lot of new feature work as well. Even though we have individual issues for most of these efforts, this is meant to serve as an all-up tracking issue which shows all of these efforts and their category. Some issues could probably be placed in more than one category, but I tried to pick whichever category had the highest order bit for each. The list here will be updated with new work as it comes up, as well as with expected shipping milestones when we think some of them will land.
## Planned for .NET 7
### Main Regex Investments
- [x] P0: [NonBacktracking] #57891
- [x] P0: [Source Generator] #44676
- [x] P0: [All Engines] #59629
- [x] P0: [All Engines] #61048
- [ ] P0: [All Engines] #59492
- [x] P1: [All Engines] #62449
- [x] P1: [All Engines] #65011
- [ ] P2: [Source Generator with NonBacktracking] #61903
- [x] P1: #68147
### API Proposals
- [x] P2: #62603
- [x] P2: #61425
- [ ] P2: #62573
### General Perf Improvements
- [x] P1: #62670
- [x] P1: #62676
- [x] P2: #62723
- [x] P2: #62669
- [x] P2: #62677
- [x] P2: #62445
- [x] P2: #62450
- [x] P2: #62459
### General Improvements
- [ ] P1: #62619
- [x] P2: #62651
- [x] P2: #62650
- [ ] P2: #60917
- [ ] P2: #48972
- [ ] P2: #58786
### Improve Test Coverage
- [ ] P1: #61893
- [ ] P2: #61896
- [ ] P2: #61895
- [ ] P2: #61894
- [x] P1: #60753
- [x] P1: #60697
### Non-Backtracking Engine Fixes and Improvements
- [x] P0: #61904
- [x] P0: #60918
- [x] P1: #60645
- [x] P1: #60623
### Source Generator Fixes and Style Improvements
- [x] P0: #59491
- [x] P1: #62647
- [x] P2: #62715
- [x] P2: #62657
- [x] P2: #61666
- [ ] P2: #62441
- [x] P2: #62438
### Performance Regressions That Need Fixing
- [x] P0: #61972
### Performance Investigations
- [x] P2: #62697
- [x] P2: #62451
- [ ] P2: #62447
- [ ] P2: #62443
cc: @stephentoub @danmoseley @olsaarik @veanes
|
non_secu
|
system text regularexpressions work planned for net this issue captures the planned work for net this list is expected to change throughout the release cycle according to ongoing planning and discussions with possible additions and subtractions to the scope summary there are currently several efforts for fixing improving our regularexpressions engines this includes test coverage efforts perf enhancing efforts but a lot of new feature work as well even though we have individual issues for most of these efforts this is meant to serve as an all up tracking issue which shows all of these efforts and their category some issues could probably be placed in more than one category but i tried to pick whichever category had the highest order bit for each the list here will be updated with new work as it comes up as well as with expected shipping milestones when we think some of them will land planned for net main regex investments api proposals general perf improvements general improvements improve test coverage non backtracking engine fixes and improvements source generator fixes and style improvements performance regressions that need fixing performance investigations cc stephentoub danmoseley olsaarik veanes
| 0
|
21,947
| 4,759,675,171
|
IssuesEvent
|
2016-10-24 23:31:50
|
scikit-learn/scikit-learn
|
https://api.github.com/repos/scikit-learn/scikit-learn
|
closed
|
MultiTaskElasticNet User Guide links to MultiTaskLasso
|
Documentation Easy Need Contributor
|
#### Description
MultiTaskElasticNet User Guide links to MultiTaskLasso, press the "Read more in the User guide" link @ http://scikit-learn.org/dev/modules/generated/sklearn.linear_model.MultiTaskElasticNet.html#sklearn.linear_model.MultiTaskElasticNet
|
1.0
|
MultiTaskElasticNet User Guide links to MultiTaskLasso - #### Description
MultiTaskElasticNet User Guide links to MultiTaskLasso, press the "Read more in the User guide" link @ http://scikit-learn.org/dev/modules/generated/sklearn.linear_model.MultiTaskElasticNet.html#sklearn.linear_model.MultiTaskElasticNet
|
non_secu
|
multitaskelasticnet user guide links to multitasklasso description multitaskelasticnet user guide links to multitasklasso press the read more in the user guide link
| 0
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.