Unnamed: 0
int64 0
832k
| id
float64 2.49B
32.1B
| type
stringclasses 1
value | created_at
stringlengths 19
19
| repo
stringlengths 5
112
| repo_url
stringlengths 34
141
| action
stringclasses 3
values | title
stringlengths 1
1k
| labels
stringlengths 4
1.38k
| body
stringlengths 1
262k
| index
stringclasses 16
values | text_combine
stringlengths 96
262k
| label
stringclasses 2
values | text
stringlengths 96
252k
| binary_label
int64 0
1
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
243,039
| 7,852,626,691
|
IssuesEvent
|
2018-06-20 15:04:11
|
Microsoft/PTVS
|
https://api.github.com/repos/Microsoft/PTVS
|
closed
|
Manually invoke completions with Ctrl+Space, most appropriate completion not selected
|
area:IntelliSense bug priority:P1 regression
|
Using latest from master
I have no choice but to use the arrow keys in order to complete `assertEquals`

|
1.0
|
Manually invoke completions with Ctrl+Space, most appropriate completion not selected - Using latest from master
I have no choice but to use the arrow keys in order to complete `assertEquals`

|
priority
|
manually invoke completions with ctrl space most appropriate completion not selected using latest from master i have no choice but to use the arrow keys in order to complete assertequals
| 1
|
207,320
| 7,127,204,881
|
IssuesEvent
|
2018-01-20 19:03:19
|
buttercup/buttercup-browser-extension
|
https://api.github.com/repos/buttercup/buttercup-browser-extension
|
closed
|
Currently failing in Firefox - v1.0+
|
Priority: Critical Type: Bug
|
Due to connectivity issues (sending information between components), the browser extension does not work in firefox.
|
1.0
|
Currently failing in Firefox - v1.0+ - Due to connectivity issues (sending information between components), the browser extension does not work in firefox.
|
priority
|
currently failing in firefox due to connectivity issues sending information between components the browser extension does not work in firefox
| 1
|
79,104
| 15,586,101,511
|
IssuesEvent
|
2021-03-18 01:10:36
|
Farsene1/Object-Oriented-Programming-Project
|
https://api.github.com/repos/Farsene1/Object-Oriented-Programming-Project
|
opened
|
CVE-2020-36179 (High) detected in jackson-databind-2.9.6.jar
|
security vulnerability
|
## CVE-2020-36179 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jackson-databind-2.9.6.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /Object-Oriented-Programming-Project/_2_client/pom.xml</p>
<p>Path to vulnerable library: /root/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.6/jackson-databind-2.9.6.jar,/root/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.6/jackson-databind-2.9.6.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.0.5.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.0.5.RELEASE.jar
- :x: **jackson-databind-2.9.6.jar** (Vulnerable Library)
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
FasterXML jackson-databind 2.x before 2.9.10.8 mishandles the interaction between serialization gadgets and typing, related to oadd.org.apache.commons.dbcp.cpdsadapter.DriverAdapterCPDS.
<p>Publish Date: 2021-01-07
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-36179>CVE-2020-36179</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>8.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/FasterXML/jackson-databind/issues/3004">https://github.com/FasterXML/jackson-databind/issues/3004</a></p>
<p>Release Date: 2021-01-07</p>
<p>Fix Resolution: com.fasterxml.jackson.core:jackson-databind:2.9.10.8</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2020-36179 (High) detected in jackson-databind-2.9.6.jar - ## CVE-2020-36179 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jackson-databind-2.9.6.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /Object-Oriented-Programming-Project/_2_client/pom.xml</p>
<p>Path to vulnerable library: /root/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.6/jackson-databind-2.9.6.jar,/root/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.9.6/jackson-databind-2.9.6.jar</p>
<p>
Dependency Hierarchy:
- spring-boot-starter-web-2.0.5.RELEASE.jar (Root Library)
- spring-boot-starter-json-2.0.5.RELEASE.jar
- :x: **jackson-databind-2.9.6.jar** (Vulnerable Library)
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
FasterXML jackson-databind 2.x before 2.9.10.8 mishandles the interaction between serialization gadgets and typing, related to oadd.org.apache.commons.dbcp.cpdsadapter.DriverAdapterCPDS.
<p>Publish Date: 2021-01-07
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2020-36179>CVE-2020-36179</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>8.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/FasterXML/jackson-databind/issues/3004">https://github.com/FasterXML/jackson-databind/issues/3004</a></p>
<p>Release Date: 2021-01-07</p>
<p>Fix Resolution: com.fasterxml.jackson.core:jackson-databind:2.9.10.8</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
non_priority
|
cve high detected in jackson databind jar cve high severity vulnerability vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file object oriented programming project client pom xml path to vulnerable library root repository com fasterxml jackson core jackson databind jackson databind jar root repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy spring boot starter web release jar root library spring boot starter json release jar x jackson databind jar vulnerable library vulnerability details fasterxml jackson databind x before mishandles the interaction between serialization gadgets and typing related to oadd org apache commons dbcp cpdsadapter driveradaptercpds publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind step up your open source security game with whitesource
| 0
|
225,488
| 17,862,081,870
|
IssuesEvent
|
2021-09-06 03:11:47
|
aodn/nrmn-application
|
https://api.github.com/repos/aodn/nrmn-application
|
closed
|
Mapping of measured Size class to stored size classes incorrect
|
issue ready to test
|
- M1 observable item size measurements are ignored, measurement of M1 observable item consistently set to the Fish size class
measurement 'Unsized'
- M2 observable item size measurements recorded with the 'UseInvertsizing' option set to 'YES' are recorded in Fish Size class AND M2 records are consistently set to measure_id =4 i.e. 7.5 cm whether the observation was sized or not and whatever the recorded size was.
|
1.0
|
Mapping of measured Size class to stored size classes incorrect - - M1 observable item size measurements are ignored, measurement of M1 observable item consistently set to the Fish size class
measurement 'Unsized'
- M2 observable item size measurements recorded with the 'UseInvertsizing' option set to 'YES' are recorded in Fish Size class AND M2 records are consistently set to measure_id =4 i.e. 7.5 cm whether the observation was sized or not and whatever the recorded size was.
|
non_priority
|
mapping of measured size class to stored size classes incorrect observable item size measurements are ignored measurement of observable item consistently set to the fish size class measurement unsized observable item size measurements recorded with the useinvertsizing option set to yes are recorded in fish size class and records are consistently set to measure id i e cm whether the observation was sized or not and whatever the recorded size was
| 0
|
230,700
| 25,482,750,882
|
IssuesEvent
|
2022-11-26 01:24:31
|
panasalap/linux-4.19.72_1
|
https://api.github.com/repos/panasalap/linux-4.19.72_1
|
reopened
|
CVE-2022-42896 (High) detected in linux-yoctov5.4.51
|
security vulnerability
|
## CVE-2022-42896 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linux-yoctov5.4.51</b></p></summary>
<p>
<p>Yocto Linux Embedded kernel</p>
<p>Library home page: <a href=https://git.yoctoproject.org/git/linux-yocto>https://git.yoctoproject.org/git/linux-yocto</a></p>
<p>Found in base branch: <b>master</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (1)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/net/bluetooth/l2cap_core.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Bluetooth: L2CAP: Fix accepting connection request for invalid SPSM
<p>Publish Date: 2022-10-13
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2022-42896>CVE-2022-42896</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2022-42896 (High) detected in linux-yoctov5.4.51 - ## CVE-2022-42896 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linux-yoctov5.4.51</b></p></summary>
<p>
<p>Yocto Linux Embedded kernel</p>
<p>Library home page: <a href=https://git.yoctoproject.org/git/linux-yocto>https://git.yoctoproject.org/git/linux-yocto</a></p>
<p>Found in base branch: <b>master</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (1)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/net/bluetooth/l2cap_core.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Bluetooth: L2CAP: Fix accepting connection request for invalid SPSM
<p>Publish Date: 2022-10-13
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2022-42896>CVE-2022-42896</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
non_priority
|
cve high detected in linux cve medium severity vulnerability vulnerable library linux yocto linux embedded kernel library home page a href found in base branch master vulnerable source files net bluetooth core c vulnerability details bluetooth fix accepting connection request for invalid spsm publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required none user interaction required scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href step up your open source security game with mend
| 0
|
38,187
| 2,841,918,534
|
IssuesEvent
|
2015-05-28 05:10:21
|
phetsims/tasks
|
https://api.github.com/repos/phetsims/tasks
|
opened
|
Test sims with games for issues with sound on iPad 2
|
High Priority QA Summer 2015 redeploy
|
@phet-steele this should be a quick task, please complete at your earliest convenience
This task is related to https://github.com/phetsims/vegas/issues/32
please test the following sims on iPad2 with iOS 8 (even though the orginal issues were reported with iOS7, if everything is fine with iOS8 it will not be worth investigating further) Just note if sound works. For any sims with an issue please note the sims in https://github.com/phetsims/vegas/issues/32
- [ ] Area builder
- [ ] Balancing act
- [ ] Balancing chemical equations
- [ ] Build an atom
- [ ] Fraction matcher
- [ ] Graphing lines
- [ ] Reactants products and leftovers
|
1.0
|
Test sims with games for issues with sound on iPad 2 - @phet-steele this should be a quick task, please complete at your earliest convenience
This task is related to https://github.com/phetsims/vegas/issues/32
please test the following sims on iPad2 with iOS 8 (even though the orginal issues were reported with iOS7, if everything is fine with iOS8 it will not be worth investigating further) Just note if sound works. For any sims with an issue please note the sims in https://github.com/phetsims/vegas/issues/32
- [ ] Area builder
- [ ] Balancing act
- [ ] Balancing chemical equations
- [ ] Build an atom
- [ ] Fraction matcher
- [ ] Graphing lines
- [ ] Reactants products and leftovers
|
priority
|
test sims with games for issues with sound on ipad phet steele this should be a quick task please complete at your earliest convenience this task is related to please test the following sims on with ios even though the orginal issues were reported with if everything is fine with it will not be worth investigating further just note if sound works for any sims with an issue please note the sims in area builder balancing act balancing chemical equations build an atom fraction matcher graphing lines reactants products and leftovers
| 1
|
745,011
| 25,966,237,590
|
IssuesEvent
|
2022-12-19 07:13:39
|
yugabyte/yugabyte-db
|
https://api.github.com/repos/yugabyte/yugabyte-db
|
closed
|
[YSQL] Batched Nested Loop join crashes on a join with multiple indexless relations
|
kind/bug area/ysql priority/medium status/awaiting-triage
|
Jira Link: [DB-4355](https://yugabyte.atlassian.net/browse/DB-4355)
### Description
It appears that the following sequence of queries are leading to a Postgres connection crash
```
CREATE TABLE s1(r1 int, r2 int, r3 int);
CREATE TABLE s2(r1 int, r2 int, r3 int);
CREATE TABLE s3(r1 int, r2 int);
CREATE INDEX ON s3 (r1 asc, r2 asc);
INSERT INTO s1 select i,i,i from generate_series(1,10) i;
INSERT INTO s2 select i,i,i from generate_series(1,10) i;
INSERT INTO s3 select i,i from generate_series(1,100) i;
SET enable_hashjoin = off;
SET enable_mergejoin = off;
SET enable_material = off;
SET yb_bnl_batch_size = 3;
/*+Leading((s2 (s1 s3)))*/explain analyze select s3.* from s1, s2, s3 where s3.r1 = s1.r1 and s3.r2 = s2.r2 and s1.r3 = s2.r3;
server closed the connection unexpectedly
This probably means the server terminated abnormally
before or while processing the request.
The connection to the server was lost. Attempting reset: Succeeded.
```
Upon further investigation, it appears that one bad occurrence in this execution is that we are forming a join tree as follows
Batched NL J1
-> Seq scan on s2
-> Batched NL J2
Join Filter: ((s2.r3 = s1.r3) AND (s1.r1 = s3.r1))
------> Seq scan on s1
------> Index only scan on s3 (Index Cond: ((r1 = ANY (ARRAY[s1.r1, $1, $2])) AND (r2 = ANY (ARRAY[s1.r2, $3, $4])))
Seeing how the sequential scan on s1 can't really accept a batch of tuples from s2, the outermost join on s2 should not be batched.
|
1.0
|
[YSQL] Batched Nested Loop join crashes on a join with multiple indexless relations - Jira Link: [DB-4355](https://yugabyte.atlassian.net/browse/DB-4355)
### Description
It appears that the following sequence of queries are leading to a Postgres connection crash
```
CREATE TABLE s1(r1 int, r2 int, r3 int);
CREATE TABLE s2(r1 int, r2 int, r3 int);
CREATE TABLE s3(r1 int, r2 int);
CREATE INDEX ON s3 (r1 asc, r2 asc);
INSERT INTO s1 select i,i,i from generate_series(1,10) i;
INSERT INTO s2 select i,i,i from generate_series(1,10) i;
INSERT INTO s3 select i,i from generate_series(1,100) i;
SET enable_hashjoin = off;
SET enable_mergejoin = off;
SET enable_material = off;
SET yb_bnl_batch_size = 3;
/*+Leading((s2 (s1 s3)))*/explain analyze select s3.* from s1, s2, s3 where s3.r1 = s1.r1 and s3.r2 = s2.r2 and s1.r3 = s2.r3;
server closed the connection unexpectedly
This probably means the server terminated abnormally
before or while processing the request.
The connection to the server was lost. Attempting reset: Succeeded.
```
Upon further investigation, it appears that one bad occurrence in this execution is that we are forming a join tree as follows
Batched NL J1
-> Seq scan on s2
-> Batched NL J2
Join Filter: ((s2.r3 = s1.r3) AND (s1.r1 = s3.r1))
------> Seq scan on s1
------> Index only scan on s3 (Index Cond: ((r1 = ANY (ARRAY[s1.r1, $1, $2])) AND (r2 = ANY (ARRAY[s1.r2, $3, $4])))
Seeing how the sequential scan on s1 can't really accept a batch of tuples from s2, the outermost join on s2 should not be batched.
|
priority
|
batched nested loop join crashes on a join with multiple indexless relations jira link description it appears that the following sequence of queries are leading to a postgres connection crash create table int int int create table int int int create table int int create index on asc asc insert into select i i i from generate series i insert into select i i i from generate series i insert into select i i from generate series i set enable hashjoin off set enable mergejoin off set enable material off set yb bnl batch size leading explain analyze select from where and and server closed the connection unexpectedly this probably means the server terminated abnormally before or while processing the request the connection to the server was lost attempting reset succeeded upon further investigation it appears that one bad occurrence in this execution is that we are forming a join tree as follows batched nl seq scan on batched nl join filter and seq scan on index only scan on index cond any array and any array seeing how the sequential scan on can t really accept a batch of tuples from the outermost join on should not be batched
| 1
|
515,123
| 14,951,083,530
|
IssuesEvent
|
2021-01-26 13:58:08
|
MapColonies/exporter-trigger
|
https://api.github.com/repos/MapColonies/exporter-trigger
|
closed
|
fix(kafka): add ssl support to configuration
|
enhancement priority: high severity: high
|
Need to make producer security protocol configurable.
|
1.0
|
fix(kafka): add ssl support to configuration - Need to make producer security protocol configurable.
|
priority
|
fix kafka add ssl support to configuration need to make producer security protocol configurable
| 1
|
651,211
| 21,469,639,960
|
IssuesEvent
|
2022-04-26 08:21:52
|
earth-chris/elapid
|
https://api.github.com/repos/earth-chris/elapid
|
closed
|
Convert transform keyword to **kwargs to support other sklearn model applications
|
enhancement low priority
|
The `elapid.geo.apply_model_to_rasters()` function currently accepts a `transform` keyword, which is passed to the `model.predict(x, transform=transform)` function when applied to raster data. This keyword is specific to the `MaxentModel()` object, and determines which type of model output to produce.
Since this keyword is specific to `MaxentModel()` objects, the `apply_model_to_rasters()` function can only be used with these models. It would be cool, however, to be able to use this function in conjunction with other `sklearn` model estimators. These models (like `RandomForestRegression()`) all have the same `model.fit()` and `model.predict()` structure, so we could use this function to apply more model types and compare outputs.
It would also be useful specifically for this package if we were to create new model forms (like niche envelope models) that don't use the transform keyword.
|
1.0
|
Convert transform keyword to **kwargs to support other sklearn model applications - The `elapid.geo.apply_model_to_rasters()` function currently accepts a `transform` keyword, which is passed to the `model.predict(x, transform=transform)` function when applied to raster data. This keyword is specific to the `MaxentModel()` object, and determines which type of model output to produce.
Since this keyword is specific to `MaxentModel()` objects, the `apply_model_to_rasters()` function can only be used with these models. It would be cool, however, to be able to use this function in conjunction with other `sklearn` model estimators. These models (like `RandomForestRegression()`) all have the same `model.fit()` and `model.predict()` structure, so we could use this function to apply more model types and compare outputs.
It would also be useful specifically for this package if we were to create new model forms (like niche envelope models) that don't use the transform keyword.
|
priority
|
convert transform keyword to kwargs to support other sklearn model applications the elapid geo apply model to rasters function currently accepts a transform keyword which is passed to the model predict x transform transform function when applied to raster data this keyword is specific to the maxentmodel object and determines which type of model output to produce since this keyword is specific to maxentmodel objects the apply model to rasters function can only be used with these models it would be cool however to be able to use this function in conjunction with other sklearn model estimators these models like randomforestregression all have the same model fit and model predict structure so we could use this function to apply more model types and compare outputs it would also be useful specifically for this package if we were to create new model forms like niche envelope models that don t use the transform keyword
| 1
|
271,310
| 29,418,957,300
|
IssuesEvent
|
2023-05-31 01:05:34
|
MidnightBSD/src
|
https://api.github.com/repos/MidnightBSD/src
|
closed
|
CVE-2016-10012 (High) detected in openssh-portableV_7_9_P1 - autoclosed
|
Mend: dependency security vulnerability
|
## CVE-2016-10012 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>openssh-portableV_7_9_P1</b></p></summary>
<p>
<p>Portable OpenSSH</p>
<p>Library home page: <a href=https://github.com/openssh/openssh-portable.git>https://github.com/openssh/openssh-portable.git</a></p>
<p>Found in base branch: <b>stable/2.1</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (2)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/crypto/openssh/monitor_mm.c</b>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/crypto/openssh/monitor_mm.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png?' width=19 height=20> Vulnerability Details</summary>
<p>
The shared memory manager (associated with pre-authentication compression) in sshd in OpenSSH before 7.4 does not ensure that a bounds check is enforced by all compilers, which might allows local users to gain privileges by leveraging access to a sandboxed privilege-separation process, related to the m_zback and m_zlib data structures.
<p>Publish Date: 2017-01-05
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2016-10012>CVE-2016-10012</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://gitlab.alpinelinux.org/alpine/aports/issues/6583">https://gitlab.alpinelinux.org/alpine/aports/issues/6583</a></p>
<p>Release Date: 2017-01-05</p>
<p>Fix Resolution: 7.4</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2016-10012 (High) detected in openssh-portableV_7_9_P1 - autoclosed - ## CVE-2016-10012 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>openssh-portableV_7_9_P1</b></p></summary>
<p>
<p>Portable OpenSSH</p>
<p>Library home page: <a href=https://github.com/openssh/openssh-portable.git>https://github.com/openssh/openssh-portable.git</a></p>
<p>Found in base branch: <b>stable/2.1</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (2)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/crypto/openssh/monitor_mm.c</b>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/crypto/openssh/monitor_mm.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png?' width=19 height=20> Vulnerability Details</summary>
<p>
The shared memory manager (associated with pre-authentication compression) in sshd in OpenSSH before 7.4 does not ensure that a bounds check is enforced by all compilers, which might allows local users to gain privileges by leveraging access to a sandboxed privilege-separation process, related to the m_zback and m_zlib data structures.
<p>Publish Date: 2017-01-05
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2016-10012>CVE-2016-10012</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://gitlab.alpinelinux.org/alpine/aports/issues/6583">https://gitlab.alpinelinux.org/alpine/aports/issues/6583</a></p>
<p>Release Date: 2017-01-05</p>
<p>Fix Resolution: 7.4</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
non_priority
|
cve high detected in openssh portablev autoclosed cve high severity vulnerability vulnerable library openssh portablev portable openssh library home page a href found in base branch stable vulnerable source files crypto openssh monitor mm c crypto openssh monitor mm c vulnerability details the shared memory manager associated with pre authentication compression in sshd in openssh before does not ensure that a bounds check is enforced by all compilers which might allows local users to gain privileges by leveraging access to a sandboxed privilege separation process related to the m zback and m zlib data structures publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required low user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with mend
| 0
|
4,906
| 2,610,160,507
|
IssuesEvent
|
2015-02-26 18:50:56
|
chrsmith/republic-at-war
|
https://api.github.com/repos/chrsmith/republic-at-war
|
closed
|
Map Issue
|
auto-migrated Priority-Medium Type-Defect
|
```
Fix spawn house on Trandosha..
```
-----
Original issue reported on code.google.com by `z3r0...@gmail.com` on 1 Feb 2011 at 7:04
|
1.0
|
Map Issue - ```
Fix spawn house on Trandosha..
```
-----
Original issue reported on code.google.com by `z3r0...@gmail.com` on 1 Feb 2011 at 7:04
|
non_priority
|
map issue fix spawn house on trandosha original issue reported on code google com by gmail com on feb at
| 0
|
112,965
| 11,784,053,100
|
IssuesEvent
|
2020-03-17 07:27:28
|
OpenEnergyPlatform/oeplatform
|
https://api.github.com/repos/OpenEnergyPlatform/oeplatform
|
opened
|
Dataview: The possibility for rules lacks documentation
|
SzenarienDB data view / modification documentation enhancement
|
The functionality below the data table is not self-explanatory and looks like a rather complex tool to use. It also currently does not become apparent what it is meant to do.
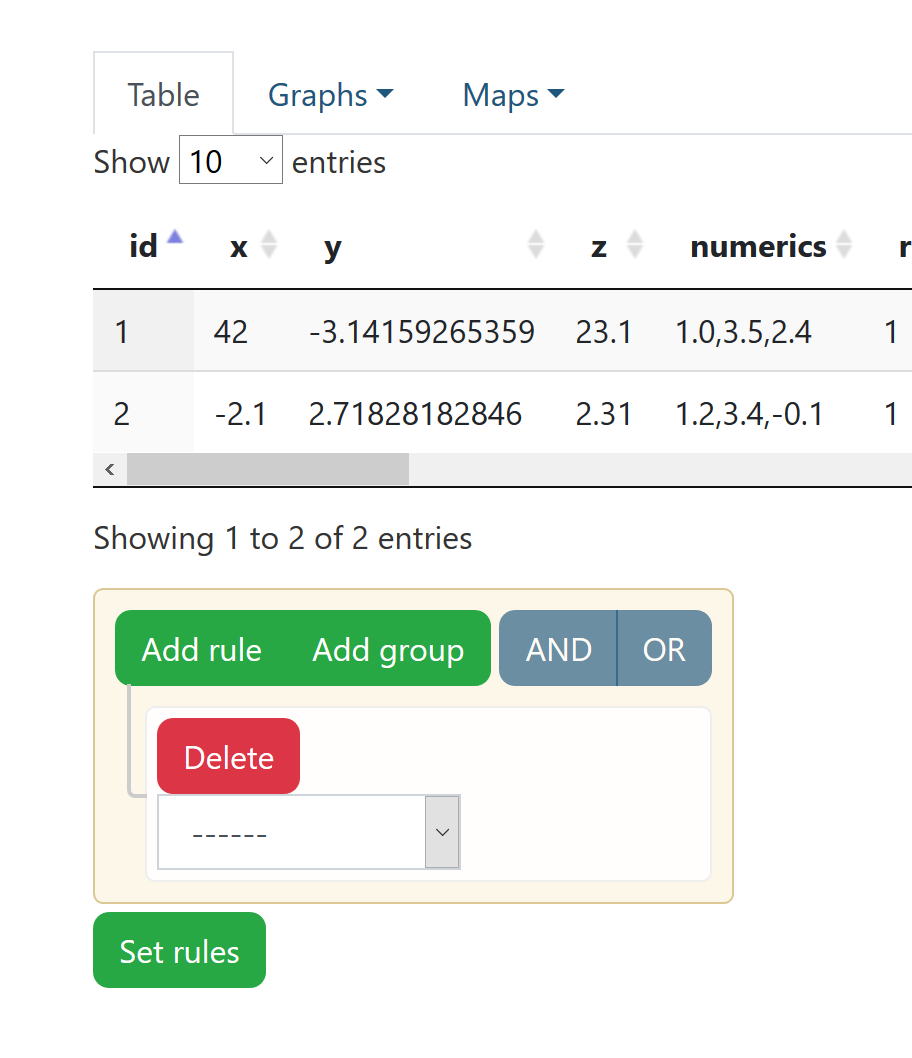
|
1.0
|
Dataview: The possibility for rules lacks documentation - The functionality below the data table is not self-explanatory and looks like a rather complex tool to use. It also currently does not become apparent what it is meant to do.

|
non_priority
|
dataview the possibility for rules lacks documentation the functionality below the data table is not self explanatory and looks like a rather complex tool to use it also currently does not become apparent what it is meant to do
| 0
|
482,741
| 13,912,478,132
|
IssuesEvent
|
2020-10-20 18:56:05
|
magento/magento2
|
https://api.github.com/repos/magento/magento2
|
closed
|
Related Products not working with Marketing Rules
|
Issue: Format is not valid PAP Priority: P1 Progress: done Project: GraphQL Reproduced on 2.4.x
|
Queries for Related Products like the one below only return values if the Related Products are added from the Product Settings. However, it is not accounting for Marketing Rules and it returning empty arrays. (Marketing / Related Products Rules) – This is how Related Products are set with Luma stock sample-data.
```java
query ProductQuery {
product: products(filter: \{ url_key: { eq: "chaz-kangeroo-hoodie" } }, pageSize: 1) {
items {
id
related_products {
id
name
url_key
}
}
}
}
```
Response:
```java
{
"data": {
"product": {
"items": <
{
"id": 70,
"related_products": []
}
>
}
}
}
```
Luma Theme:
!image-2020-06-02-16-10-01-234.png|width=1336,height=761!
|
1.0
|
Related Products not working with Marketing Rules - Queries for Related Products like the one below only return values if the Related Products are added from the Product Settings. However, it is not accounting for Marketing Rules and it returning empty arrays. (Marketing / Related Products Rules) – This is how Related Products are set with Luma stock sample-data.
```java
query ProductQuery {
product: products(filter: \{ url_key: { eq: "chaz-kangeroo-hoodie" } }, pageSize: 1) {
items {
id
related_products {
id
name
url_key
}
}
}
}
```
Response:
```java
{
"data": {
"product": {
"items": <
{
"id": 70,
"related_products": []
}
>
}
}
}
```
Luma Theme:
!image-2020-06-02-16-10-01-234.png|width=1336,height=761!
|
priority
|
related products not working with marketing rules queries for related products like the one below only return values if the related products are added from the product settings however it is not accounting for marketing rules and it returning empty arrays marketing related products rules – this is how related products are set with luma stock sample data java query productquery product products filter url key eq chaz kangeroo hoodie pagesize items id related products id name url key response java data product items id related products luma theme image png width height
| 1
|
20,053
| 4,488,034,476
|
IssuesEvent
|
2016-08-30 04:56:11
|
minetest/minetest
|
https://api.github.com/repos/minetest/minetest
|
closed
|
keymap_autorun is not documented in minetest.conf.example and settingtypes.txt.
|
@ Documentation
|
Also it is not changeable in key change menu.
|
1.0
|
keymap_autorun is not documented in minetest.conf.example and settingtypes.txt. - Also it is not changeable in key change menu.
|
non_priority
|
keymap autorun is not documented in minetest conf example and settingtypes txt also it is not changeable in key change menu
| 0
|
224,734
| 7,472,242,742
|
IssuesEvent
|
2018-04-03 12:02:18
|
geosolutions-it/MapStore2
|
https://api.github.com/repos/geosolutions-it/MapStore2
|
opened
|
Panels hide the feature info marker
|
Priority: Medium Project: C040 enhancement
|
### Description
We should move info marker on visible area when it's hidden by panels
### Other useful information (optional):
|
1.0
|
Panels hide the feature info marker - ### Description
We should move info marker on visible area when it's hidden by panels
### Other useful information (optional):
|
priority
|
panels hide the feature info marker description we should move info marker on visible area when it s hidden by panels other useful information optional
| 1
|
5,418
| 7,934,276,094
|
IssuesEvent
|
2018-07-08 17:15:15
|
Shroompow/DedShroom
|
https://api.github.com/repos/Shroompow/DedShroom
|
opened
|
Storage Manager
|
Launch-Requirement
|
Grants easy to use functions to interact with the database.
May load and unload files on certain occasions without changing the way the Manager is used.
User-Settings may unload when User is AFK or Offline for example.
Files can have `important`-status, indicating they shall always be loaded into memory.
Data from files loaded by the StorageManager should never be stored outside the class if possible.
This prevents the StorageManager from unloading files effectively as the garbage-collector won't kick in.
Instead Handles should be used.
Handles are object which contain data about which file they are linked to and a function to access this file which will load the file if necessary.
`getHandle(path_to_json_file)`
The Data of a handle can be accessed using:
`handle.access(callback)`
Example:
```js
handle.access((error,data)=>{
if(error){
//If for any reason the data could not be loaded.
//For example if the file has been deleted.
}
data.points++;
});
```
Helper Functions generate a Handle to their respective json-files.
If the json-file or folder-structure doesn't exist, it will be created with default values.
````js
getUserData(userId)
getGuildData(guildId)
```
Ideas:
Registry/Index for easily adding Storage-Types with default values without editing the class.
Helper functions would change to:
`get(type,argument)`
example:
`get(STORAGE_TYPE_USER,id)`
These Storage-Types would be specified similar to modules inside an index.
```js
{
"userdata": {path:"storage/users/*.json",init_data:{"points":0}}
}
```
This needs to be further thought through in the future.
|
1.0
|
Storage Manager - Grants easy to use functions to interact with the database.
May load and unload files on certain occasions without changing the way the Manager is used.
User-Settings may unload when User is AFK or Offline for example.
Files can have `important`-status, indicating they shall always be loaded into memory.
Data from files loaded by the StorageManager should never be stored outside the class if possible.
This prevents the StorageManager from unloading files effectively as the garbage-collector won't kick in.
Instead Handles should be used.
Handles are object which contain data about which file they are linked to and a function to access this file which will load the file if necessary.
`getHandle(path_to_json_file)`
The Data of a handle can be accessed using:
`handle.access(callback)`
Example:
```js
handle.access((error,data)=>{
if(error){
//If for any reason the data could not be loaded.
//For example if the file has been deleted.
}
data.points++;
});
```
Helper Functions generate a Handle to their respective json-files.
If the json-file or folder-structure doesn't exist, it will be created with default values.
````js
getUserData(userId)
getGuildData(guildId)
```
Ideas:
Registry/Index for easily adding Storage-Types with default values without editing the class.
Helper functions would change to:
`get(type,argument)`
example:
`get(STORAGE_TYPE_USER,id)`
These Storage-Types would be specified similar to modules inside an index.
```js
{
"userdata": {path:"storage/users/*.json",init_data:{"points":0}}
}
```
This needs to be further thought through in the future.
|
non_priority
|
storage manager grants easy to use functions to interact with the database may load and unload files on certain occasions without changing the way the manager is used user settings may unload when user is afk or offline for example files can have important status indicating they shall always be loaded into memory data from files loaded by the storagemanager should never be stored outside the class if possible this prevents the storagemanager from unloading files effectively as the garbage collector won t kick in instead handles should be used handles are object which contain data about which file they are linked to and a function to access this file which will load the file if necessary gethandle path to json file the data of a handle can be accessed using handle access callback example js handle access error data if error if for any reason the data could not be loaded for example if the file has been deleted data points helper functions generate a handle to their respective json files if the json file or folder structure doesn t exist it will be created with default values js getuserdata userid getguilddata guildid ideas registry index for easily adding storage types with default values without editing the class helper functions would change to get type argument example get storage type user id these storage types would be specified similar to modules inside an index js userdata path storage users json init data points this needs to be further thought through in the future
| 0
|
244,145
| 7,870,992,166
|
IssuesEvent
|
2018-06-25 05:49:06
|
cmacma7/bn
|
https://api.github.com/repos/cmacma7/bn
|
closed
|
[VIP價格] 在商品編輯頁,編輯VIP價格,會讓該品項名稱清空&顯示為sold out
|
First Priority bug 團購
|
[Scenario]
1. 編輯VIP價格商品
2. 編輯商品品項/設定VIP價格
[Result] 輸入任一個VIP價格,會讓品項名稱被清空 & 顯示為sold out

|
1.0
|
[VIP價格] 在商品編輯頁,編輯VIP價格,會讓該品項名稱清空&顯示為sold out - [Scenario]
1. 編輯VIP價格商品
2. 編輯商品品項/設定VIP價格
[Result] 輸入任一個VIP價格,會讓品項名稱被清空 & 顯示為sold out

|
priority
|
在商品編輯頁,編輯vip價格,會讓該品項名稱清空 顯示為sold out 編輯vip價格商品 編輯商品品項 設定vip價格 輸入任一個vip價格,會讓品項名稱被清空 顯示為sold out
| 1
|
72,536
| 19,305,899,873
|
IssuesEvent
|
2021-12-13 11:28:05
|
scylladb/scylla
|
https://api.github.com/repos/scylladb/scylla
|
closed
|
build: dist-deb target failing (in Fedora 34) after a recent update of debhelper
|
Build
|
With the most recent version of debhelper on Fedora, the `debuild` step fails with `error: maintainer script 'postinst' has bad permissions 1363`.
The problem is not present in debhelper 13.3.4, which is the version used in the current version of the frozen toolchain.
I have found another account of a similar problem here: https://www.mail-archive.com/debian-bugs-dist@lists.debian.org/msg1814310.html
This might be a debhelper issue rather than a Scylla issue, but I'm recording it here for reference.
|
1.0
|
build: dist-deb target failing (in Fedora 34) after a recent update of debhelper - With the most recent version of debhelper on Fedora, the `debuild` step fails with `error: maintainer script 'postinst' has bad permissions 1363`.
The problem is not present in debhelper 13.3.4, which is the version used in the current version of the frozen toolchain.
I have found another account of a similar problem here: https://www.mail-archive.com/debian-bugs-dist@lists.debian.org/msg1814310.html
This might be a debhelper issue rather than a Scylla issue, but I'm recording it here for reference.
|
non_priority
|
build dist deb target failing in fedora after a recent update of debhelper with the most recent version of debhelper on fedora the debuild step fails with error maintainer script postinst has bad permissions the problem is not present in debhelper which is the version used in the current version of the frozen toolchain i have found another account of a similar problem here this might be a debhelper issue rather than a scylla issue but i m recording it here for reference
| 0
|
107,774
| 9,223,090,398
|
IssuesEvent
|
2019-03-12 01:52:19
|
ThinkHub-io/coeus-issues
|
https://api.github.com/repos/ThinkHub-io/coeus-issues
|
closed
|
Patient ID's not validating correctly when tutor is grading
|
Testing bug
|
Michelle:
On the test site, staff can't grade the pending procedures because it kept saying ID not valid, even though the same ID worked for the student and was ok during the grading.
It's only when I pressed Save & Submit, the Warning Triangle appears next to Patient details, and I've lost all the grades clicked...
|
1.0
|
Patient ID's not validating correctly when tutor is grading - Michelle:
On the test site, staff can't grade the pending procedures because it kept saying ID not valid, even though the same ID worked for the student and was ok during the grading.
It's only when I pressed Save & Submit, the Warning Triangle appears next to Patient details, and I've lost all the grades clicked...
|
non_priority
|
patient id s not validating correctly when tutor is grading michelle on the test site staff can t grade the pending procedures because it kept saying id not valid even though the same id worked for the student and was ok during the grading it s only when i pressed save submit the warning triangle appears next to patient details and i ve lost all the grades clicked
| 0
|
376,769
| 26,216,187,173
|
IssuesEvent
|
2023-01-04 11:09:07
|
jekyll/jekyll
|
https://api.github.com/repos/jekyll/jekyll
|
closed
|
[Docs]: Jekyll on macOS - Step 2: "Install chruby and the latest Ruby with ruby-install" Fails Due to Outdated Ruby Version in Doc
|
has-pull-request documentation
|
<!-- Thanks for taking the time to open an issue and help us make Jekyll better! -->
## Motivation
<!-- Why should we update our docs? -->
I followed the [Jekyll on macOS](https://jekyllrb.com/docs/installation/macos/) guide to install and run Jekyll for the first time earlier today. I restarted Terminal per the guide at the end of step 2 in the guide and got an error message saying "chruby: unknown Ruby: ruby-3.1.2" as shown below:

## Suggestion
<!-- What should we do instead? -->
To fix it, "echo "chruby ruby-**3.1.2**" >> ~/.zshrc" should be "echo "chruby ruby-**3.1.3**" >> ~/.zshrc" in step 2 in the [Jekyll on macOS](https://jekyllrb.com/docs/installation/macos/) guide.
When I updated the line in .zshrc, I was able to proceed and install Jekyll successfully.

<!-- Thanks for taking the time to open an issue and help us make Jekyll better! -->
|
1.0
|
[Docs]: Jekyll on macOS - Step 2: "Install chruby and the latest Ruby with ruby-install" Fails Due to Outdated Ruby Version in Doc - <!-- Thanks for taking the time to open an issue and help us make Jekyll better! -->
## Motivation
<!-- Why should we update our docs? -->
I followed the [Jekyll on macOS](https://jekyllrb.com/docs/installation/macos/) guide to install and run Jekyll for the first time earlier today. I restarted Terminal per the guide at the end of step 2 in the guide and got an error message saying "chruby: unknown Ruby: ruby-3.1.2" as shown below:

## Suggestion
<!-- What should we do instead? -->
To fix it, "echo "chruby ruby-**3.1.2**" >> ~/.zshrc" should be "echo "chruby ruby-**3.1.3**" >> ~/.zshrc" in step 2 in the [Jekyll on macOS](https://jekyllrb.com/docs/installation/macos/) guide.
When I updated the line in .zshrc, I was able to proceed and install Jekyll successfully.

<!-- Thanks for taking the time to open an issue and help us make Jekyll better! -->
|
non_priority
|
jekyll on macos step install chruby and the latest ruby with ruby install fails due to outdated ruby version in doc motivation i followed the guide to install and run jekyll for the first time earlier today i restarted terminal per the guide at the end of step in the guide and got an error message saying chruby unknown ruby ruby as shown below suggestion to fix it echo chruby ruby zshrc should be echo chruby ruby zshrc in step in the guide when i updated the line in zshrc i was able to proceed and install jekyll successfully
| 0
|
247,480
| 20,981,893,607
|
IssuesEvent
|
2022-03-28 20:50:59
|
gakonst/foundry
|
https://api.github.com/repos/gakonst/foundry
|
closed
|
Resolution for duplicate test/contract names affecting forge test output
|
T-bug Cmd-forge-test C-forge P-high D-average
|
Demo repo: https://github.com/stevennevins/demo_behavior
Dapptools seems to handle if there are harness contracts with duplicate names and *.t.sol files with duplicate test case names, but forge will only display the result of the first case of these duplicates unless verbosity is increased. I've included a demo repo to show the behavior difference between dapptools and forge.
|
1.0
|
Resolution for duplicate test/contract names affecting forge test output - Demo repo: https://github.com/stevennevins/demo_behavior
Dapptools seems to handle if there are harness contracts with duplicate names and *.t.sol files with duplicate test case names, but forge will only display the result of the first case of these duplicates unless verbosity is increased. I've included a demo repo to show the behavior difference between dapptools and forge.
|
non_priority
|
resolution for duplicate test contract names affecting forge test output demo repo dapptools seems to handle if there are harness contracts with duplicate names and t sol files with duplicate test case names but forge will only display the result of the first case of these duplicates unless verbosity is increased i ve included a demo repo to show the behavior difference between dapptools and forge
| 0
|
164,678
| 26,006,339,113
|
IssuesEvent
|
2022-12-20 19:46:31
|
microsoft/vscode
|
https://api.github.com/repos/microsoft/vscode
|
reopened
|
Welcome page opens in Codespaces even when workbench.startupEditor is set to "readme" in Remote settings
|
bug *as-designed getting-started
|
<!-- ⚠️⚠️ Do Not Delete This! bug_report_template ⚠️⚠️ -->
<!-- Please read our Rules of Conduct: https://opensource.microsoft.com/codeofconduct/ -->
<!-- 🕮 Read our guide about submitting issues: https://github.com/microsoft/vscode/wiki/Submitting-Bugs-and-Suggestions -->
<!-- 🔎 Search existing issues to avoid creating duplicates. -->
<!-- 🧪 Test using the latest Insiders build to see if your issue has already been fixed: https://code.visualstudio.com/insiders/ -->
<!-- 💡 Instead of creating your report here, use 'Report Issue' from the 'Help' menu in VS Code to pre-fill useful information. -->
<!-- 🔧 Launch with `code --disable-extensions` to check. -->
Does this issue occur when all extensions are disabled?: Yes
<!-- 🪓 If you answered No above, use 'Help: Start Extension Bisect' from Command Palette to try to identify the cause. -->
<!-- 📣 Issues caused by an extension need to be reported directly to the extension publisher. The 'Help > Report Issue' dialog can assist with this. -->
The same issue as this issue occurs in the current version of codespaces.
#134073
- VS Code Version:1.69.0
x64
- OS Version: OSX 10.14.6
Steps to Reproduce:
1. Create a Codespace from a repo containing a .devcontainer.json with "workbench.startupEditor": "readme".
2. Welcome page still opens within a tab, per screenshot below.
<img width="1097" alt="スクリーンショット 2022-07-12 21 28 20" src="https://user-images.githubusercontent.com/6661165/178489669-23be95c6-d7db-4d04-8681-0d2c7d7b5e91.png">
|
1.0
|
Welcome page opens in Codespaces even when workbench.startupEditor is set to "readme" in Remote settings - <!-- ⚠️⚠️ Do Not Delete This! bug_report_template ⚠️⚠️ -->
<!-- Please read our Rules of Conduct: https://opensource.microsoft.com/codeofconduct/ -->
<!-- 🕮 Read our guide about submitting issues: https://github.com/microsoft/vscode/wiki/Submitting-Bugs-and-Suggestions -->
<!-- 🔎 Search existing issues to avoid creating duplicates. -->
<!-- 🧪 Test using the latest Insiders build to see if your issue has already been fixed: https://code.visualstudio.com/insiders/ -->
<!-- 💡 Instead of creating your report here, use 'Report Issue' from the 'Help' menu in VS Code to pre-fill useful information. -->
<!-- 🔧 Launch with `code --disable-extensions` to check. -->
Does this issue occur when all extensions are disabled?: Yes
<!-- 🪓 If you answered No above, use 'Help: Start Extension Bisect' from Command Palette to try to identify the cause. -->
<!-- 📣 Issues caused by an extension need to be reported directly to the extension publisher. The 'Help > Report Issue' dialog can assist with this. -->
The same issue as this issue occurs in the current version of codespaces.
#134073
- VS Code Version:1.69.0
x64
- OS Version: OSX 10.14.6
Steps to Reproduce:
1. Create a Codespace from a repo containing a .devcontainer.json with "workbench.startupEditor": "readme".
2. Welcome page still opens within a tab, per screenshot below.
<img width="1097" alt="スクリーンショット 2022-07-12 21 28 20" src="https://user-images.githubusercontent.com/6661165/178489669-23be95c6-d7db-4d04-8681-0d2c7d7b5e91.png">
|
non_priority
|
welcome page opens in codespaces even when workbench startupeditor is set to readme in remote settings does this issue occur when all extensions are disabled yes report issue dialog can assist with this the same issue as this issue occurs in the current version of codespaces vs code version os version osx steps to reproduce create a codespace from a repo containing a devcontainer json with workbench startupeditor readme welcome page still opens within a tab per screenshot below img width alt スクリーンショット src
| 0
|
297,162
| 9,161,301,946
|
IssuesEvent
|
2019-03-01 10:05:48
|
RavenProject/ravenwallet-ios
|
https://api.github.com/repos/RavenProject/ravenwallet-ios
|
closed
|
Qt - Wallet shows protocol raven:<address>&amount=22... etc
|
FIXED / DONE Low Priority enhancement
|
The iPhone scan should honor this protocol and fill in a send with the field info.
|
1.0
|
Qt - Wallet shows protocol raven:<address>&amount=22... etc - The iPhone scan should honor this protocol and fill in a send with the field info.
|
priority
|
qt wallet shows protocol raven amount etc the iphone scan should honor this protocol and fill in a send with the field info
| 1
|
61,187
| 14,619,094,070
|
IssuesEvent
|
2020-12-22 17:15:50
|
kenferrara/calcite
|
https://api.github.com/repos/kenferrara/calcite
|
opened
|
CVE-2016-2510 (High) detected in bsh-2.0b4.jar
|
security vulnerability
|
## CVE-2016-2510 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>bsh-2.0b4.jar</b></p></summary>
<p>BeanShell</p>
<p>Path to dependency file: calcite/server/build.gradle.kts</p>
<p>Path to vulnerable library: /home/wss-scanner/.gradle/caches/modules-2/files-2.1/org.beanshell/bsh/2.0b4/a05f0a0feefa8d8467ac80e16e7de071489f0d9c/bsh-2.0b4.jar</p>
<p>
Dependency Hierarchy:
- fmpp-0.9.16.jar (Root Library)
- :x: **bsh-2.0b4.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/kenferrara/calcite/commit/5e2bb91de24b843d35df04b29fe7158fad414ee0">5e2bb91de24b843d35df04b29fe7158fad414ee0</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
BeanShell (bsh) before 2.0b6, when included on the classpath by an application that uses Java serialization or XStream, allows remote attackers to execute arbitrary code via crafted serialized data, related to XThis.Handler.
<p>Publish Date: 2016-04-07
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2016-2510>CVE-2016-2510</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>8.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2016-2510">https://nvd.nist.gov/vuln/detail/CVE-2016-2510</a></p>
<p>Release Date: 2016-04-07</p>
<p>Fix Resolution: 2.0b6</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"Java","groupId":"org.beanshell","packageName":"bsh","packageVersion":"2.0b4","isTransitiveDependency":true,"dependencyTree":"net.sourceforge.fmpp:fmpp:0.9.16;org.beanshell:bsh:2.0b4","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.0b6"}],"vulnerabilityIdentifier":"CVE-2016-2510","vulnerabilityDetails":"BeanShell (bsh) before 2.0b6, when included on the classpath by an application that uses Java serialization or XStream, allows remote attackers to execute arbitrary code via crafted serialized data, related to XThis.Handler.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2016-2510","cvss3Severity":"high","cvss3Score":"8.1","cvss3Metrics":{"A":"High","AC":"High","PR":"None","S":"Unchanged","C":"High","UI":"None","AV":"Network","I":"High"},"extraData":{}}</REMEDIATE> -->
|
True
|
CVE-2016-2510 (High) detected in bsh-2.0b4.jar - ## CVE-2016-2510 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>bsh-2.0b4.jar</b></p></summary>
<p>BeanShell</p>
<p>Path to dependency file: calcite/server/build.gradle.kts</p>
<p>Path to vulnerable library: /home/wss-scanner/.gradle/caches/modules-2/files-2.1/org.beanshell/bsh/2.0b4/a05f0a0feefa8d8467ac80e16e7de071489f0d9c/bsh-2.0b4.jar</p>
<p>
Dependency Hierarchy:
- fmpp-0.9.16.jar (Root Library)
- :x: **bsh-2.0b4.jar** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/kenferrara/calcite/commit/5e2bb91de24b843d35df04b29fe7158fad414ee0">5e2bb91de24b843d35df04b29fe7158fad414ee0</a></p>
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
BeanShell (bsh) before 2.0b6, when included on the classpath by an application that uses Java serialization or XStream, allows remote attackers to execute arbitrary code via crafted serialized data, related to XThis.Handler.
<p>Publish Date: 2016-04-07
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2016-2510>CVE-2016-2510</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>8.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2016-2510">https://nvd.nist.gov/vuln/detail/CVE-2016-2510</a></p>
<p>Release Date: 2016-04-07</p>
<p>Fix Resolution: 2.0b6</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"Java","groupId":"org.beanshell","packageName":"bsh","packageVersion":"2.0b4","isTransitiveDependency":true,"dependencyTree":"net.sourceforge.fmpp:fmpp:0.9.16;org.beanshell:bsh:2.0b4","isMinimumFixVersionAvailable":true,"minimumFixVersion":"2.0b6"}],"vulnerabilityIdentifier":"CVE-2016-2510","vulnerabilityDetails":"BeanShell (bsh) before 2.0b6, when included on the classpath by an application that uses Java serialization or XStream, allows remote attackers to execute arbitrary code via crafted serialized data, related to XThis.Handler.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2016-2510","cvss3Severity":"high","cvss3Score":"8.1","cvss3Metrics":{"A":"High","AC":"High","PR":"None","S":"Unchanged","C":"High","UI":"None","AV":"Network","I":"High"},"extraData":{}}</REMEDIATE> -->
|
non_priority
|
cve high detected in bsh jar cve high severity vulnerability vulnerable library bsh jar beanshell path to dependency file calcite server build gradle kts path to vulnerable library home wss scanner gradle caches modules files org beanshell bsh bsh jar dependency hierarchy fmpp jar root library x bsh jar vulnerable library found in head commit a href found in base branch master vulnerability details beanshell bsh before when included on the classpath by an application that uses java serialization or xstream allows remote attackers to execute arbitrary code via crafted serialized data related to xthis handler publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution isopenpronvulnerability true ispackagebased true isdefaultbranch true packages vulnerabilityidentifier cve vulnerabilitydetails beanshell bsh before when included on the classpath by an application that uses java serialization or xstream allows remote attackers to execute arbitrary code via crafted serialized data related to xthis handler vulnerabilityurl
| 0
|
488,944
| 14,099,760,780
|
IssuesEvent
|
2020-11-06 02:16:22
|
reuseman/GoOutSafe
|
https://api.github.com/repos/reuseman/GoOutSafe
|
closed
|
As an operator I want to forbid marked customers from booking at my restaurant So that I avoid closing it
|
customer operator priority 2 user story
|
As an operator I want to forbid marked customers from booking at my restaurant So that I avoid closing it
|
1.0
|
As an operator I want to forbid marked customers from booking at my restaurant So that I avoid closing it - As an operator I want to forbid marked customers from booking at my restaurant So that I avoid closing it
|
priority
|
as an operator i want to forbid marked customers from booking at my restaurant so that i avoid closing it as an operator i want to forbid marked customers from booking at my restaurant so that i avoid closing it
| 1
|
72,155
| 23,962,442,657
|
IssuesEvent
|
2022-09-12 20:27:20
|
department-of-veterans-affairs/va.gov-cms
|
https://api.github.com/repos/department-of-veterans-affairs/va.gov-cms
|
opened
|
Archived Vet center content showing on preview server
|
Defect VA.gov frontend Content preview ⭐️ Facilities
|
## Describe the defect
The preview server is set up to show draft content so that editors can see what a page is supposed to look like before it is published. However, it should not be showing content that is archived.
This has surfaced as a defect in Vet centers where when a Vet Center archives a CAP, the cap still shows in the preview server and causes confusion for editors.
Here is a vet center cap that has been archived on staging
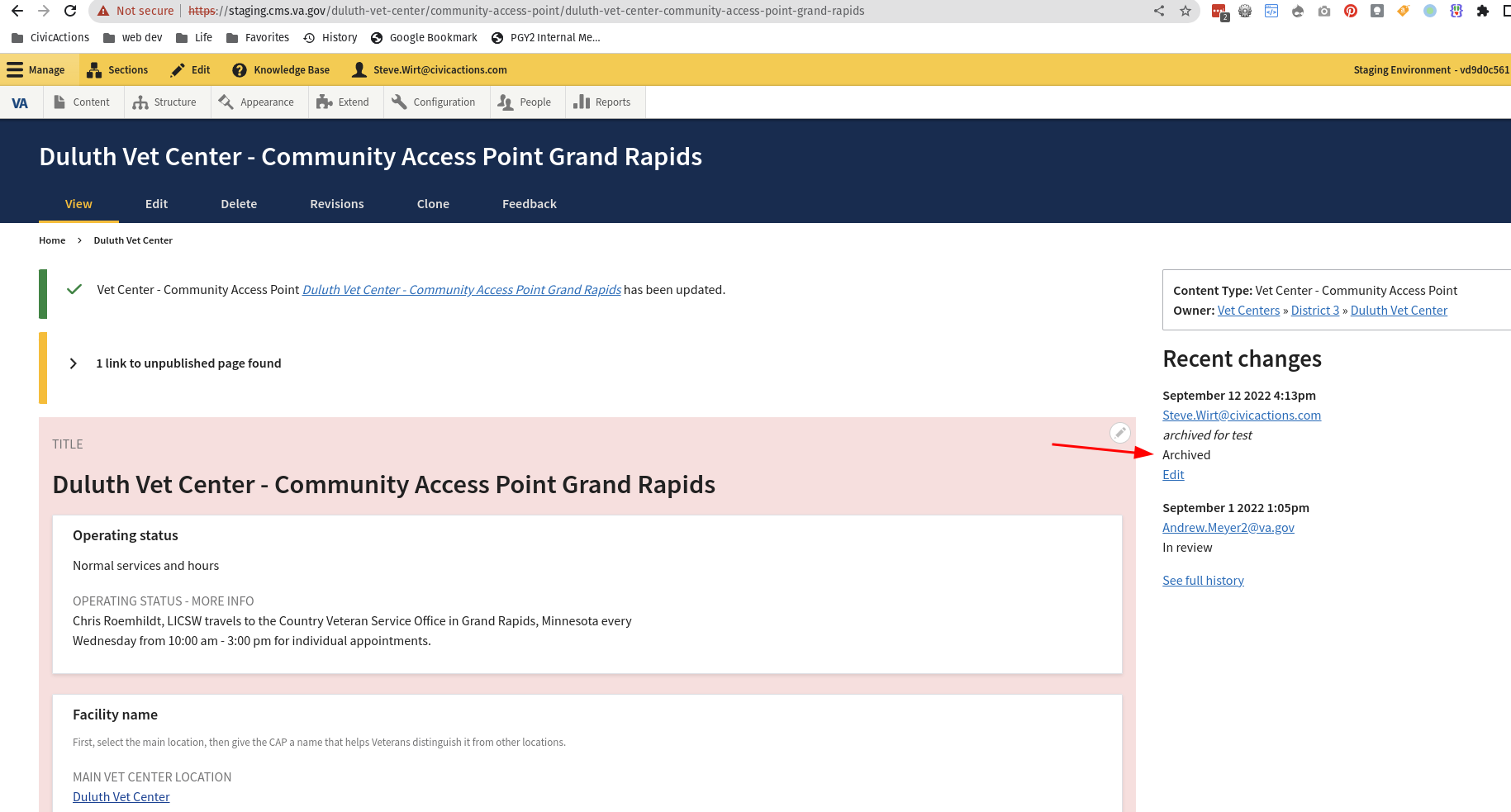
and here is the preview for the locations page still showing the archived facility.
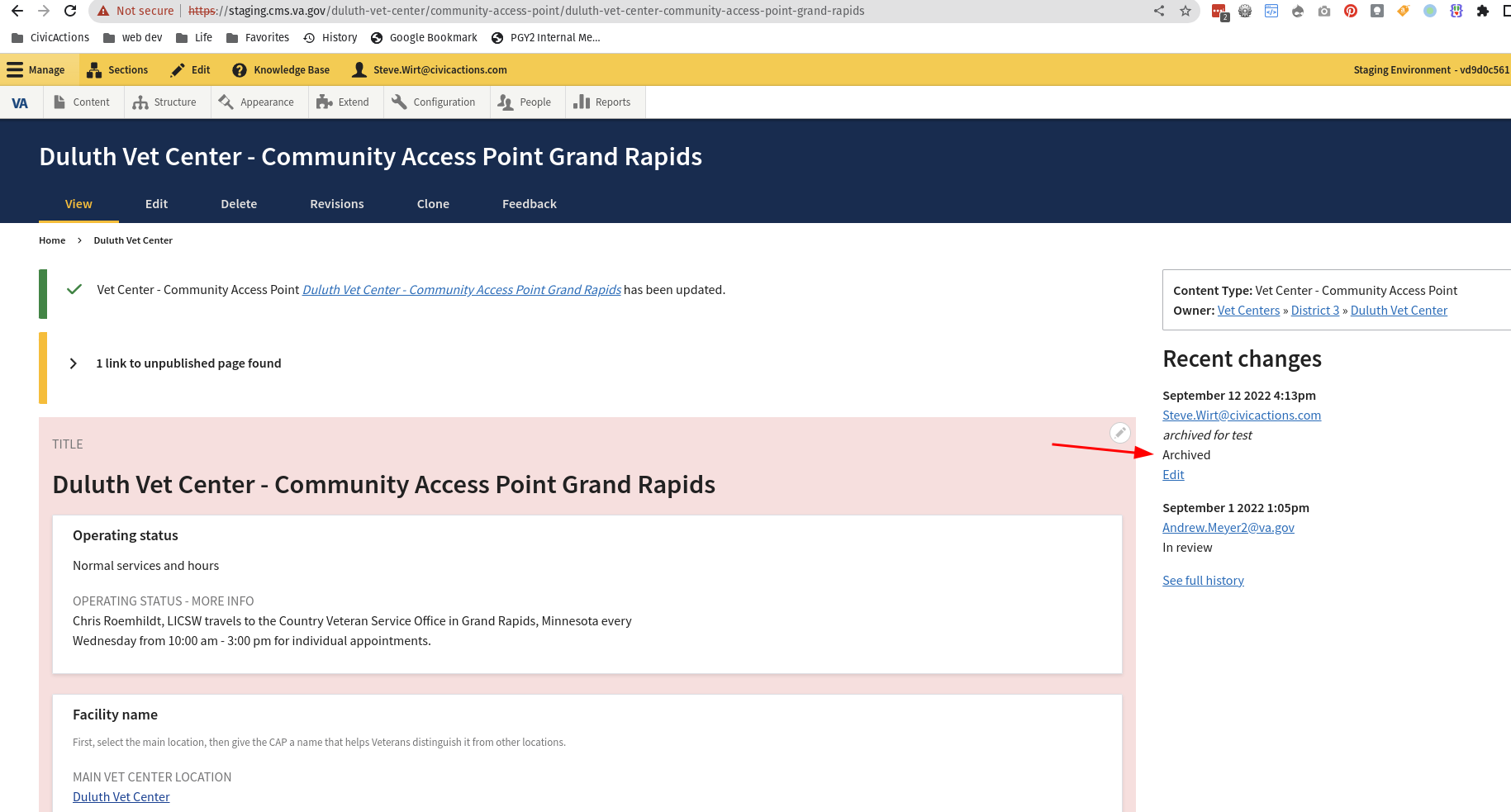
## To Reproduce
Steps to reproduce the behavior:
1. Go to This facility on staging and change its moderation state to "Archived" then save the node https://staging.cms.va.gov/duluth-vet-center/community-access-point/duluth-vet-center-community-access-point-grand-rapids
2. Go to the locations page https://staging.cms.va.gov/duluth-vet-center/locations and validate that the facility you just edited shows as archived.
3. Go to the preview for the locations page http://preview-staging.vfs.va.gov/preview?nodeId=28208 and noticed that the archived facillity still shows.
## AC / Expected behavior
- [ ] When a vetcenter is archived, it will not show in the web preview for the locations page.
- [ ] Draft content will still show in the preview server.
- [ ] It is possible that this is also happening on va.gov which means there error is in the FE and just trickling down to the preview server.
## Labels
(You can delete this section once it's complete)
- [x] Issue type (red) (defaults to "Defect")
- [ ] CMS subsystem (green)
- [ ] CMS practice area (blue)
- [x] CMS workstream (orange) (not needed for bug tickets)
- [ ] CMS-supported product (black)
### CMS Team
Please check the team(s) that will do this work.
- [ ] `Program`
- [ ] `Platform CMS Team`
- [ ] `Sitewide Crew`
- [ ] `⭐️ Sitewide CMS`
- [ ] `⭐️ Public Websites`
- [x] `⭐️ Facilities`
- [ ] `⭐️ User support`
|
1.0
|
Archived Vet center content showing on preview server - ## Describe the defect
The preview server is set up to show draft content so that editors can see what a page is supposed to look like before it is published. However, it should not be showing content that is archived.
This has surfaced as a defect in Vet centers where when a Vet Center archives a CAP, the cap still shows in the preview server and causes confusion for editors.
Here is a vet center cap that has been archived on staging

and here is the preview for the locations page still showing the archived facility.

## To Reproduce
Steps to reproduce the behavior:
1. Go to This facility on staging and change its moderation state to "Archived" then save the node https://staging.cms.va.gov/duluth-vet-center/community-access-point/duluth-vet-center-community-access-point-grand-rapids
2. Go to the locations page https://staging.cms.va.gov/duluth-vet-center/locations and validate that the facility you just edited shows as archived.
3. Go to the preview for the locations page http://preview-staging.vfs.va.gov/preview?nodeId=28208 and noticed that the archived facillity still shows.
## AC / Expected behavior
- [ ] When a vetcenter is archived, it will not show in the web preview for the locations page.
- [ ] Draft content will still show in the preview server.
- [ ] It is possible that this is also happening on va.gov which means there error is in the FE and just trickling down to the preview server.
## Labels
(You can delete this section once it's complete)
- [x] Issue type (red) (defaults to "Defect")
- [ ] CMS subsystem (green)
- [ ] CMS practice area (blue)
- [x] CMS workstream (orange) (not needed for bug tickets)
- [ ] CMS-supported product (black)
### CMS Team
Please check the team(s) that will do this work.
- [ ] `Program`
- [ ] `Platform CMS Team`
- [ ] `Sitewide Crew`
- [ ] `⭐️ Sitewide CMS`
- [ ] `⭐️ Public Websites`
- [x] `⭐️ Facilities`
- [ ] `⭐️ User support`
|
non_priority
|
archived vet center content showing on preview server describe the defect the preview server is set up to show draft content so that editors can see what a page is supposed to look like before it is published however it should not be showing content that is archived this has surfaced as a defect in vet centers where when a vet center archives a cap the cap still shows in the preview server and causes confusion for editors here is a vet center cap that has been archived on staging and here is the preview for the locations page still showing the archived facility to reproduce steps to reproduce the behavior go to this facility on staging and change its moderation state to archived then save the node go to the locations page and validate that the facility you just edited shows as archived go to the preview for the locations page and noticed that the archived facillity still shows ac expected behavior when a vetcenter is archived it will not show in the web preview for the locations page draft content will still show in the preview server it is possible that this is also happening on va gov which means there error is in the fe and just trickling down to the preview server labels you can delete this section once it s complete issue type red defaults to defect cms subsystem green cms practice area blue cms workstream orange not needed for bug tickets cms supported product black cms team please check the team s that will do this work program platform cms team sitewide crew ⭐️ sitewide cms ⭐️ public websites ⭐️ facilities ⭐️ user support
| 0
|
448
| 8,180,785,939
|
IssuesEvent
|
2018-08-28 20:35:38
|
planningcenter/developers
|
https://api.github.com/repos/planningcenter/developers
|
closed
|
Person endpoint cannot query for remote id equal to null
|
People question
|
**Affected Applications**
Which app(s) does this bug affect? API
**Describe the bug**
Need to be able to query for all people that do not have a remote id value. I've tried the following, but none of them return any people:
https://api.planningcenteronline.com/people/v2/people?where[remote_id]=null
https://api.planningcenteronline.com/people/v2/people?where[remote_id]=0
https://api.planningcenteronline.com/people/v2/people?where[remote_id]=
**Expected behavior**
Return every person who does not have a remote id
**Context (please complete the following information):**
- Endpoint: https://api.planningcenteronline.com/people/v2/people
- Language: C#
- Authentication: Personal Access Token
|
1.0
|
Person endpoint cannot query for remote id equal to null - **Affected Applications**
Which app(s) does this bug affect? API
**Describe the bug**
Need to be able to query for all people that do not have a remote id value. I've tried the following, but none of them return any people:
https://api.planningcenteronline.com/people/v2/people?where[remote_id]=null
https://api.planningcenteronline.com/people/v2/people?where[remote_id]=0
https://api.planningcenteronline.com/people/v2/people?where[remote_id]=
**Expected behavior**
Return every person who does not have a remote id
**Context (please complete the following information):**
- Endpoint: https://api.planningcenteronline.com/people/v2/people
- Language: C#
- Authentication: Personal Access Token
|
non_priority
|
person endpoint cannot query for remote id equal to null affected applications which app s does this bug affect api describe the bug need to be able to query for all people that do not have a remote id value i ve tried the following but none of them return any people null expected behavior return every person who does not have a remote id context please complete the following information endpoint language c authentication personal access token
| 0
|
720,631
| 24,799,803,133
|
IssuesEvent
|
2022-10-24 20:35:38
|
spacetelescope/jwql
|
https://api.github.com/repos/spacetelescope/jwql
|
closed
|
Implement unlooked filter
|
enhancement Web Application High Priority
|
We have a bit of infrastructure in place (in urls.py at least), to have a page that shows only new or "unlooked" data. We should finish implementing this, so that teams don't have to wade through data they have already examined in order to get to new files each day.
@BradleySappington suggested a filter to be added to each instrument's archive page, as well as each program's page, which would show only new data. This method has the advantage of then allowing for other filtered to be easily added (e.g. filters for the various types of anomalies.)
|
1.0
|
Implement unlooked filter - We have a bit of infrastructure in place (in urls.py at least), to have a page that shows only new or "unlooked" data. We should finish implementing this, so that teams don't have to wade through data they have already examined in order to get to new files each day.
@BradleySappington suggested a filter to be added to each instrument's archive page, as well as each program's page, which would show only new data. This method has the advantage of then allowing for other filtered to be easily added (e.g. filters for the various types of anomalies.)
|
priority
|
implement unlooked filter we have a bit of infrastructure in place in urls py at least to have a page that shows only new or unlooked data we should finish implementing this so that teams don t have to wade through data they have already examined in order to get to new files each day bradleysappington suggested a filter to be added to each instrument s archive page as well as each program s page which would show only new data this method has the advantage of then allowing for other filtered to be easily added e g filters for the various types of anomalies
| 1
|
761,564
| 26,686,203,830
|
IssuesEvent
|
2023-01-26 22:10:48
|
osulp/Scholars-Archive
|
https://api.github.com/repos/osulp/Scholars-Archive
|
closed
|
OAI, connect Set description to Admin Set abstract
|
Harvesting Priority: Low
|
Currently there's no OAI Set Description configured (just title). This isn't critical, but some harvesters may display the description somewhere in their interface.
This can pull from the Admin Set abstract/summary, though currently none of them have any values there.
|
1.0
|
OAI, connect Set description to Admin Set abstract - Currently there's no OAI Set Description configured (just title). This isn't critical, but some harvesters may display the description somewhere in their interface.
This can pull from the Admin Set abstract/summary, though currently none of them have any values there.
|
priority
|
oai connect set description to admin set abstract currently there s no oai set description configured just title this isn t critical but some harvesters may display the description somewhere in their interface this can pull from the admin set abstract summary though currently none of them have any values there
| 1
|
265,574
| 28,297,941,241
|
IssuesEvent
|
2023-04-10 01:18:21
|
nk7598/linux-4.19.72
|
https://api.github.com/repos/nk7598/linux-4.19.72
|
closed
|
CVE-2022-3303 (Medium) detected in linuxlinux-4.19.269 - autoclosed
|
Mend: dependency security vulnerability
|
## CVE-2022-3303 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linuxlinux-4.19.269</b></p></summary>
<p>
<p>The Linux Kernel</p>
<p>Library home page: <a href=https://mirrors.edge.kernel.org/pub/linux/kernel/v4.x/?wsslib=linux>https://mirrors.edge.kernel.org/pub/linux/kernel/v4.x/?wsslib=linux</a></p>
<p>Found in base branch: <b>master</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (2)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/sound/core/oss/pcm_oss.c</b>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/sound/core/oss/pcm_oss.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
A race condition flaw was found in the Linux kernel sound subsystem due to improper locking. It could lead to a NULL pointer dereference while handling the SNDCTL_DSP_SYNC ioctl. A privileged local user (root or member of the audio group) could use this flaw to crash the system, resulting in a denial of service condition
<p>Publish Date: 2022-09-27
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2022-3303>CVE-2022-3303</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>4.7</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: High
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.linuxkernelcves.com/cves/CVE-2022-3303">https://www.linuxkernelcves.com/cves/CVE-2022-3303</a></p>
<p>Release Date: 2022-09-27</p>
<p>Fix Resolution: v5.15.68,v5.19.9,v6.0-rc5</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2022-3303 (Medium) detected in linuxlinux-4.19.269 - autoclosed - ## CVE-2022-3303 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linuxlinux-4.19.269</b></p></summary>
<p>
<p>The Linux Kernel</p>
<p>Library home page: <a href=https://mirrors.edge.kernel.org/pub/linux/kernel/v4.x/?wsslib=linux>https://mirrors.edge.kernel.org/pub/linux/kernel/v4.x/?wsslib=linux</a></p>
<p>Found in base branch: <b>master</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (2)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/sound/core/oss/pcm_oss.c</b>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/sound/core/oss/pcm_oss.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
A race condition flaw was found in the Linux kernel sound subsystem due to improper locking. It could lead to a NULL pointer dereference while handling the SNDCTL_DSP_SYNC ioctl. A privileged local user (root or member of the audio group) could use this flaw to crash the system, resulting in a denial of service condition
<p>Publish Date: 2022-09-27
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2022-3303>CVE-2022-3303</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>4.7</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: High
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://www.linuxkernelcves.com/cves/CVE-2022-3303">https://www.linuxkernelcves.com/cves/CVE-2022-3303</a></p>
<p>Release Date: 2022-09-27</p>
<p>Fix Resolution: v5.15.68,v5.19.9,v6.0-rc5</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
non_priority
|
cve medium detected in linuxlinux autoclosed cve medium severity vulnerability vulnerable library linuxlinux the linux kernel library home page a href found in base branch master vulnerable source files sound core oss pcm oss c sound core oss pcm oss c vulnerability details a race condition flaw was found in the linux kernel sound subsystem due to improper locking it could lead to a null pointer dereference while handling the sndctl dsp sync ioctl a privileged local user root or member of the audio group could use this flaw to crash the system resulting in a denial of service condition publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity high privileges required low user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with mend
| 0
|
151,236
| 23,785,990,884
|
IssuesEvent
|
2022-09-02 10:06:58
|
spring-projects/spring-data-relational
|
https://api.github.com/repos/spring-projects/spring-data-relational
|
closed
|
DDL generation support
|
status: pending-design-work type: enhancement
|
Like Micronaut Data Jdbc/R2dbc, add JPA/Hibernate similar strategy to generate(or update) the database schemas automatically.
|
1.0
|
DDL generation support - Like Micronaut Data Jdbc/R2dbc, add JPA/Hibernate similar strategy to generate(or update) the database schemas automatically.
|
non_priority
|
ddl generation support like micronaut data jdbc add jpa hibernate similar strategy to generate or update the database schemas automatically
| 0
|
55,500
| 13,638,324,142
|
IssuesEvent
|
2020-09-25 09:12:36
|
TerryCavanagh/diceydungeonsbeta
|
https://api.github.com/repos/TerryCavanagh/diceydungeonsbeta
|
closed
|
Undo ignores changes to MaxHP from, eg, Kale Salad
|
v0.3: 4th June Build
|
Kale Salad:
https://streamable.com/n8br4
Modded health switch:
|
1.0
|
Undo ignores changes to MaxHP from, eg, Kale Salad - Kale Salad:
https://streamable.com/n8br4
Modded health switch:

|
non_priority
|
undo ignores changes to maxhp from eg kale salad kale salad modded health switch
| 0
|
775,001
| 27,215,081,097
|
IssuesEvent
|
2023-02-20 20:43:14
|
ascheid/itsg33-pbmm-issue-gen
|
https://api.github.com/repos/ascheid/itsg33-pbmm-issue-gen
|
closed
|
MP-6 MEDIA SANITIZATION
|
Priority: P2
|
MEDIA SANITIZATION | EQUIPMENT TESTING
The organization tests sanitization equipment and procedures [Assignment: organization-defined frequency] to verify that the intended sanitization is being achieved.
|
1.0
|
MP-6 MEDIA SANITIZATION - MEDIA SANITIZATION | EQUIPMENT TESTING
The organization tests sanitization equipment and procedures [Assignment: organization-defined frequency] to verify that the intended sanitization is being achieved.
|
priority
|
mp media sanitization media sanitization equipment testing the organization tests sanitization equipment and procedures to verify that the intended sanitization is being achieved
| 1
|
592,374
| 17,876,984,361
|
IssuesEvent
|
2021-09-07 06:04:41
|
grpc/grpc
|
https://api.github.com/repos/grpc/grpc
|
closed
|
Mechanism to limit build parallelism on gem installation.
|
kind/enhancement lang/ruby priority/P2 disposition/stale
|
<!--
PLEASE DO NOT POST A QUESTION HERE.
This form is for bug reports and feature requests ONLY!
For general questions and troubleshooting, please ask/look for answers at StackOverflow, with "grpc" tag: https://stackoverflow.com/questions/tagged/grpc
For questions that specifically need to be answered by gRPC team members, please ask/look for answers at grpc.io mailing list: https://groups.google.com/forum/#!forum/grpc-io
Issues specific to *grpc-java*, *grpc-go*, *grpc-node*, *grpc-dart*, *grpc-web* should be created in the repository they belong to (e.g. https://github.com/grpc/grpc-LANGUAGE/issues/new)
-->
### Is your feature request related to a problem? Please describe.
When I attempt to do a `bundle install` of my project (which depends on the `grpc` Ruby gem) on CircleCI, The `extconf.rb` detects that the machine it's running on has 36 cores (despite my resource class being limited to 4 vCPUs, no less) and attempts to build the native extension with a parallelism of 72. This exceeds the 8GB memory ceiling for the resource class.
### Describe the solution you'd like
A means by which I can tell the installation process to limit the build parallelism to something smaller. Perhaps an environment variable I could pass in? Whatever the mechanism, it would be ideal if it plays nice with Bundler of course.
### Describe alternatives you've considered
~~I may be able to live with a larger (and thus more expensive) resource class on my CI server, but that would make the `bundle install` step considerably more expensive.~~
Anything larger than the `large` resource class requires approval from a CSM at CircleCI, and we don't want to be on their radar for Enterprise Sales at this time. In the meantime I've forked this repo, and changed the relevant line of extconf.rb to cap things. Not an ideal solution, of course.
### Additional context
N/A
|
1.0
|
Mechanism to limit build parallelism on gem installation. - <!--
PLEASE DO NOT POST A QUESTION HERE.
This form is for bug reports and feature requests ONLY!
For general questions and troubleshooting, please ask/look for answers at StackOverflow, with "grpc" tag: https://stackoverflow.com/questions/tagged/grpc
For questions that specifically need to be answered by gRPC team members, please ask/look for answers at grpc.io mailing list: https://groups.google.com/forum/#!forum/grpc-io
Issues specific to *grpc-java*, *grpc-go*, *grpc-node*, *grpc-dart*, *grpc-web* should be created in the repository they belong to (e.g. https://github.com/grpc/grpc-LANGUAGE/issues/new)
-->
### Is your feature request related to a problem? Please describe.
When I attempt to do a `bundle install` of my project (which depends on the `grpc` Ruby gem) on CircleCI, The `extconf.rb` detects that the machine it's running on has 36 cores (despite my resource class being limited to 4 vCPUs, no less) and attempts to build the native extension with a parallelism of 72. This exceeds the 8GB memory ceiling for the resource class.
### Describe the solution you'd like
A means by which I can tell the installation process to limit the build parallelism to something smaller. Perhaps an environment variable I could pass in? Whatever the mechanism, it would be ideal if it plays nice with Bundler of course.
### Describe alternatives you've considered
~~I may be able to live with a larger (and thus more expensive) resource class on my CI server, but that would make the `bundle install` step considerably more expensive.~~
Anything larger than the `large` resource class requires approval from a CSM at CircleCI, and we don't want to be on their radar for Enterprise Sales at this time. In the meantime I've forked this repo, and changed the relevant line of extconf.rb to cap things. Not an ideal solution, of course.
### Additional context
N/A
|
priority
|
mechanism to limit build parallelism on gem installation please do not post a question here this form is for bug reports and feature requests only for general questions and troubleshooting please ask look for answers at stackoverflow with grpc tag for questions that specifically need to be answered by grpc team members please ask look for answers at grpc io mailing list issues specific to grpc java grpc go grpc node grpc dart grpc web should be created in the repository they belong to e g is your feature request related to a problem please describe when i attempt to do a bundle install of my project which depends on the grpc ruby gem on circleci the extconf rb detects that the machine it s running on has cores despite my resource class being limited to vcpus no less and attempts to build the native extension with a parallelism of this exceeds the memory ceiling for the resource class describe the solution you d like a means by which i can tell the installation process to limit the build parallelism to something smaller perhaps an environment variable i could pass in whatever the mechanism it would be ideal if it plays nice with bundler of course describe alternatives you ve considered i may be able to live with a larger and thus more expensive resource class on my ci server but that would make the bundle install step considerably more expensive anything larger than the large resource class requires approval from a csm at circleci and we don t want to be on their radar for enterprise sales at this time in the meantime i ve forked this repo and changed the relevant line of extconf rb to cap things not an ideal solution of course additional context n a
| 1
|
100,843
| 11,205,797,862
|
IssuesEvent
|
2020-01-05 16:40:57
|
BrancoLab/BrainRender
|
https://api.github.com/repos/BrancoLab/BrainRender
|
closed
|
Docs and Examples are outdated
|
documentation
|
Due to recent changes (e.g. 46c450059c0c909a9e422ba408cc50671a292c72), some of the docs and examples might be incorrect or not working. Need to go through them and check they work correctly.
|
1.0
|
Docs and Examples are outdated - Due to recent changes (e.g. 46c450059c0c909a9e422ba408cc50671a292c72), some of the docs and examples might be incorrect or not working. Need to go through them and check they work correctly.
|
non_priority
|
docs and examples are outdated due to recent changes e g some of the docs and examples might be incorrect or not working need to go through them and check they work correctly
| 0
|
164,502
| 20,364,516,506
|
IssuesEvent
|
2022-02-21 02:57:24
|
prafullkotecha/myIonicApp
|
https://api.github.com/repos/prafullkotecha/myIonicApp
|
opened
|
CVE-2022-0639 (Medium) detected in url-parse-1.4.7.tgz
|
security vulnerability
|
## CVE-2022-0639 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>url-parse-1.4.7.tgz</b></p></summary>
<p>Small footprint URL parser that works seamlessly across Node.js and browser environments</p>
<p>Library home page: <a href="https://registry.npmjs.org/url-parse/-/url-parse-1.4.7.tgz">https://registry.npmjs.org/url-parse/-/url-parse-1.4.7.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/url-parse/package.json</p>
<p>
Dependency Hierarchy:
- build-angular-0.1000.8.tgz (Root Library)
- webpack-dev-server-3.11.0.tgz
- sockjs-client-1.4.0.tgz
- :x: **url-parse-1.4.7.tgz** (Vulnerable Library)
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Authorization Bypass Through User-Controlled Key in NPM url-parse prior to 1.5.7.
<p>Publish Date: 2022-02-17
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2022-0639>CVE-2022-0639</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0639">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0639</a></p>
<p>Release Date: 2022-02-17</p>
<p>Fix Resolution: url-parse - 1.5.7</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2022-0639 (Medium) detected in url-parse-1.4.7.tgz - ## CVE-2022-0639 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>url-parse-1.4.7.tgz</b></p></summary>
<p>Small footprint URL parser that works seamlessly across Node.js and browser environments</p>
<p>Library home page: <a href="https://registry.npmjs.org/url-parse/-/url-parse-1.4.7.tgz">https://registry.npmjs.org/url-parse/-/url-parse-1.4.7.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/url-parse/package.json</p>
<p>
Dependency Hierarchy:
- build-angular-0.1000.8.tgz (Root Library)
- webpack-dev-server-3.11.0.tgz
- sockjs-client-1.4.0.tgz
- :x: **url-parse-1.4.7.tgz** (Vulnerable Library)
<p>Found in base branch: <b>main</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
Authorization Bypass Through User-Controlled Key in NPM url-parse prior to 1.5.7.
<p>Publish Date: 2022-02-17
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2022-0639>CVE-2022-0639</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0639">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0639</a></p>
<p>Release Date: 2022-02-17</p>
<p>Fix Resolution: url-parse - 1.5.7</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
non_priority
|
cve medium detected in url parse tgz cve medium severity vulnerability vulnerable library url parse tgz small footprint url parser that works seamlessly across node js and browser environments library home page a href path to dependency file package json path to vulnerable library node modules url parse package json dependency hierarchy build angular tgz root library webpack dev server tgz sockjs client tgz x url parse tgz vulnerable library found in base branch main vulnerability details authorization bypass through user controlled key in npm url parse prior to publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution url parse step up your open source security game with whitesource
| 0
|
48,681
| 2,999,445,842
|
IssuesEvent
|
2015-07-23 19:04:11
|
mesosphere/kubernetes-mesos
|
https://api.github.com/repos/mesosphere/kubernetes-mesos
|
closed
|
Apiserver proxy does not work in version 0.6 dcos packages
|
bug priority/P1
|
During smoke testing of the latest 0.6 dcos packages, we deployed the guestbook example with kube-dns support and tried to access the frontend service at end via:
http://<dcos-cluster>/service/kubernetes/api/v1/proxy/namespaces/default/services/frontend
This redirected back to
http://<dcos-cluster>/api/v1/proxy/namespaces/default/services/frontend/
Moreover, entering the full url with a / at the end did not work either:
http://<dcos-cluster>/service/kubernetes/api/v1/proxy/namespaces/default/services/frontend
Giving an 404 of openresty.
|
1.0
|
Apiserver proxy does not work in version 0.6 dcos packages - During smoke testing of the latest 0.6 dcos packages, we deployed the guestbook example with kube-dns support and tried to access the frontend service at end via:
http://<dcos-cluster>/service/kubernetes/api/v1/proxy/namespaces/default/services/frontend
This redirected back to
http://<dcos-cluster>/api/v1/proxy/namespaces/default/services/frontend/
Moreover, entering the full url with a / at the end did not work either:
http://<dcos-cluster>/service/kubernetes/api/v1/proxy/namespaces/default/services/frontend
Giving an 404 of openresty.
|
priority
|
apiserver proxy does not work in version dcos packages during smoke testing of the latest dcos packages we deployed the guestbook example with kube dns support and tried to access the frontend service at end via this redirected back to moreover entering the full url with a at the end did not work either giving an of openresty
| 1
|
82,974
| 10,317,045,907
|
IssuesEvent
|
2019-08-30 11:39:51
|
Rapporteket/smerte
|
https://api.github.com/repos/Rapporteket/smerte
|
opened
|
Moc-up of user controlled report subscriptions
|
documentation help wanted
|
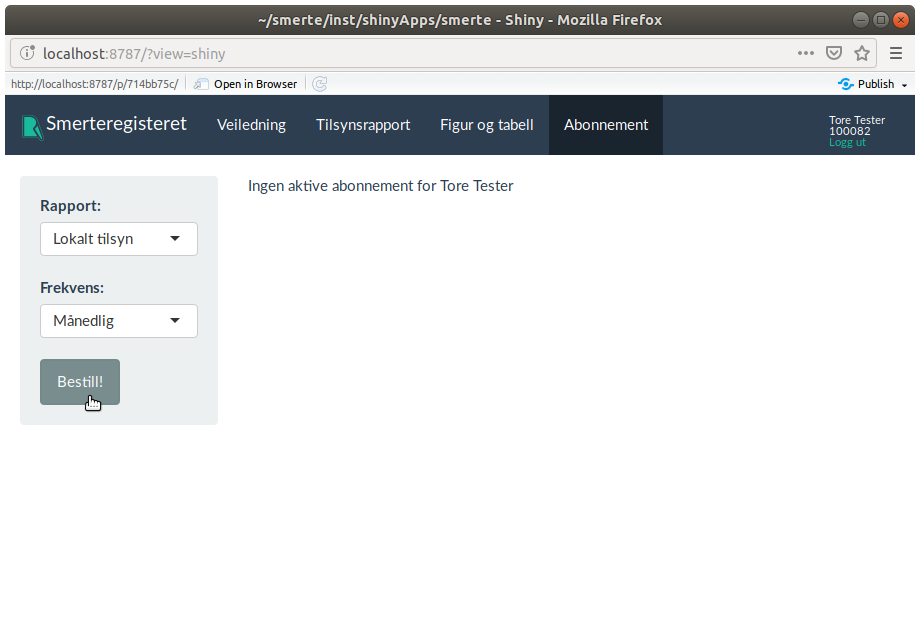
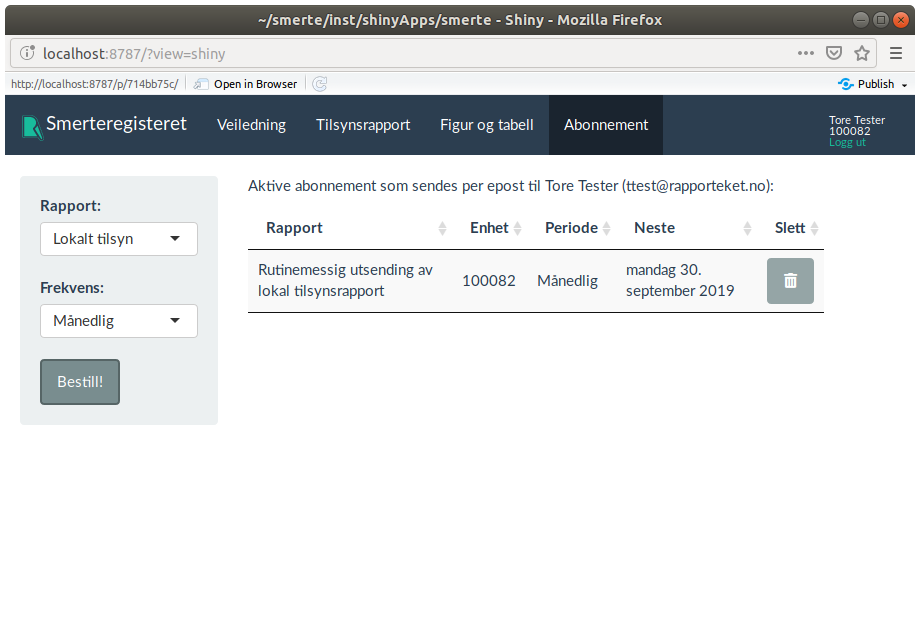
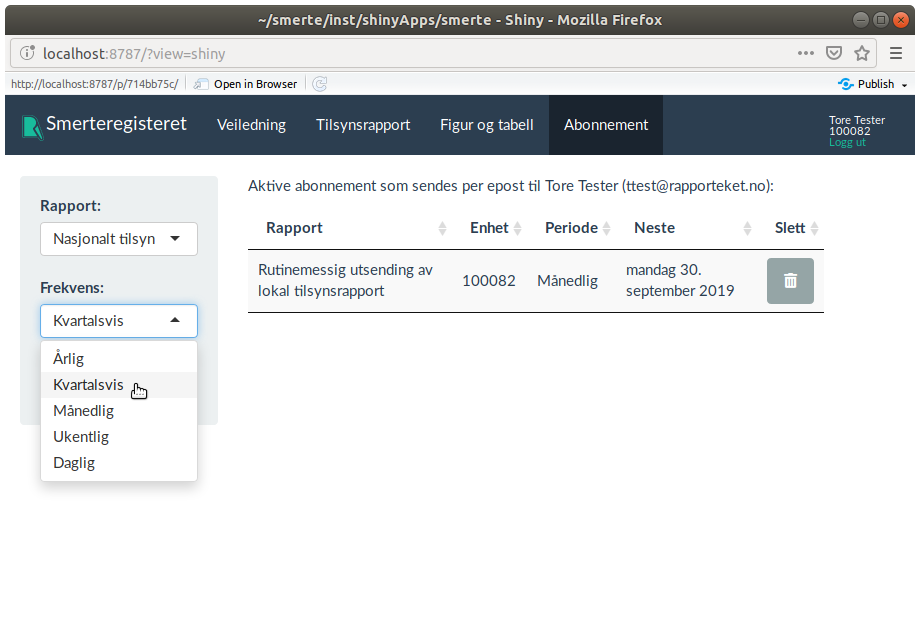
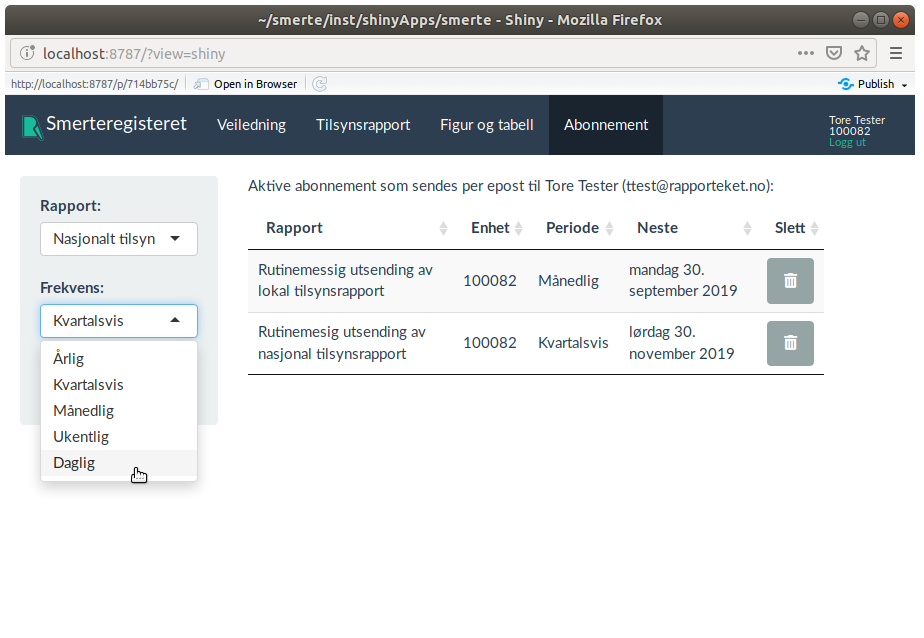
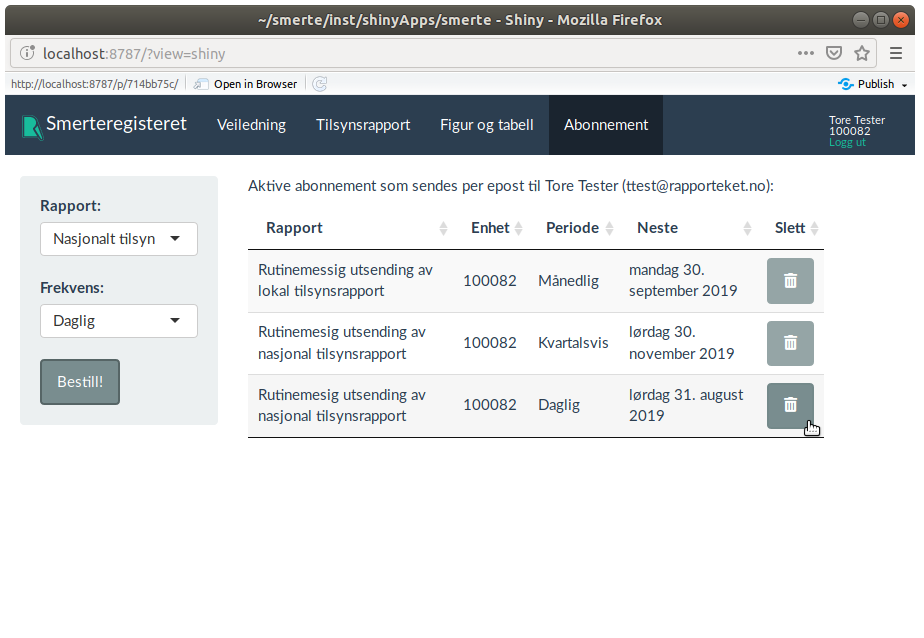
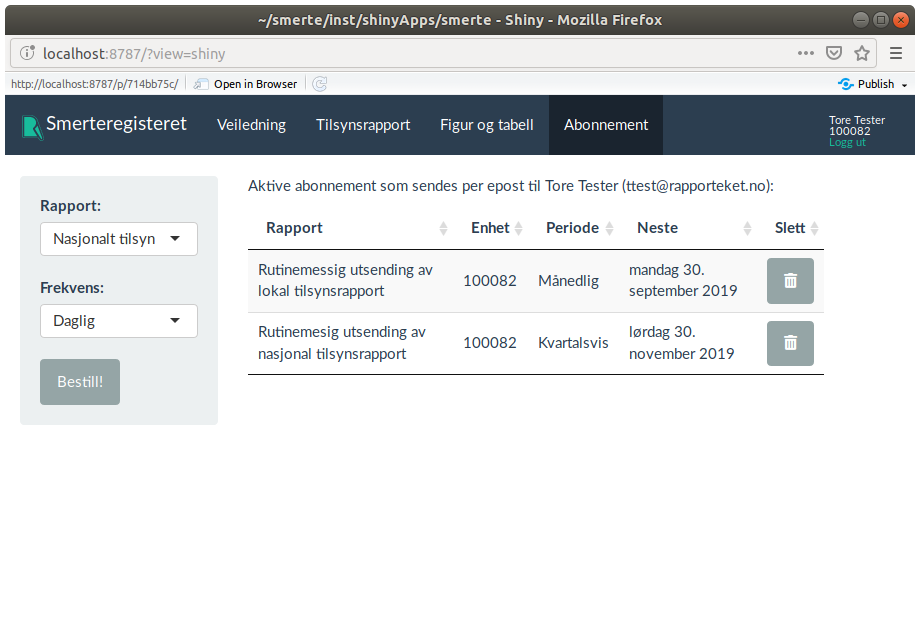
|
1.0
|
Moc-up of user controlled report subscriptions - 





|
non_priority
|
moc up of user controlled report subscriptions
| 0
|
440,885
| 30,762,025,016
|
IssuesEvent
|
2023-07-29 20:43:39
|
virtbad/menu-scraper-rs
|
https://api.github.com/repos/virtbad/menu-scraper-rs
|
closed
|
Publish a container to ghcr when creating a tag
|
documentation enhancement
|
# Goal
The menu-scraper should have a docker image which runs once a day and uploads all menus of a restaurant to an api. This image should be automatically built and published to ghcr everytime a new tag is created on the repository.
* [ ] Add workflow for automatic building & publishing to ghcr
* [ ] Add docs on how to host the scraper
|
1.0
|
Publish a container to ghcr when creating a tag - # Goal
The menu-scraper should have a docker image which runs once a day and uploads all menus of a restaurant to an api. This image should be automatically built and published to ghcr everytime a new tag is created on the repository.
* [ ] Add workflow for automatic building & publishing to ghcr
* [ ] Add docs on how to host the scraper
|
non_priority
|
publish a container to ghcr when creating a tag goal the menu scraper should have a docker image which runs once a day and uploads all menus of a restaurant to an api this image should be automatically built and published to ghcr everytime a new tag is created on the repository add workflow for automatic building publishing to ghcr add docs on how to host the scraper
| 0
|
192,532
| 22,215,966,584
|
IssuesEvent
|
2022-06-08 01:42:02
|
Bangtrongtuyet/phpmyAdmin
|
https://api.github.com/repos/Bangtrongtuyet/phpmyAdmin
|
opened
|
CVE-2021-43306 (Medium) detected in jquery-validation-1.19.0.tgz
|
security vulnerability
|
## CVE-2021-43306 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jquery-validation-1.19.0.tgz</b></p></summary>
<p>Client-side form validation made easy</p>
<p>Library home page: <a href="https://registry.npmjs.org/jquery-validation/-/jquery-validation-1.19.0.tgz">https://registry.npmjs.org/jquery-validation/-/jquery-validation-1.19.0.tgz</a></p>
<p>Path to dependency file: /phpmyAdmin/package.json</p>
<p>Path to vulnerable library: /node_modules/jquery-validation/package.json</p>
<p>
Dependency Hierarchy:
- :x: **jquery-validation-1.19.0.tgz** (Vulnerable Library)
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
An exponential ReDoS (Regular Expression Denial of Service) can be triggered in the jquery-validation npm package, when an attacker is able to supply arbitrary input to the url2 method
<p>Publish Date: 2022-06-02
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-43306>CVE-2021-43306</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.9</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://research.jfrog.com/vulnerabilities/jquery-validation-redos-xray-211348/">https://research.jfrog.com/vulnerabilities/jquery-validation-redos-xray-211348/</a></p>
<p>Release Date: 2022-06-02</p>
<p>Fix Resolution: 1.19.4-pre</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2021-43306 (Medium) detected in jquery-validation-1.19.0.tgz - ## CVE-2021-43306 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jquery-validation-1.19.0.tgz</b></p></summary>
<p>Client-side form validation made easy</p>
<p>Library home page: <a href="https://registry.npmjs.org/jquery-validation/-/jquery-validation-1.19.0.tgz">https://registry.npmjs.org/jquery-validation/-/jquery-validation-1.19.0.tgz</a></p>
<p>Path to dependency file: /phpmyAdmin/package.json</p>
<p>Path to vulnerable library: /node_modules/jquery-validation/package.json</p>
<p>
Dependency Hierarchy:
- :x: **jquery-validation-1.19.0.tgz** (Vulnerable Library)
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
An exponential ReDoS (Regular Expression Denial of Service) can be triggered in the jquery-validation npm package, when an attacker is able to supply arbitrary input to the url2 method
<p>Publish Date: 2022-06-02
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2021-43306>CVE-2021-43306</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.9</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: High
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://research.jfrog.com/vulnerabilities/jquery-validation-redos-xray-211348/">https://research.jfrog.com/vulnerabilities/jquery-validation-redos-xray-211348/</a></p>
<p>Release Date: 2022-06-02</p>
<p>Fix Resolution: 1.19.4-pre</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
non_priority
|
cve medium detected in jquery validation tgz cve medium severity vulnerability vulnerable library jquery validation tgz client side form validation made easy library home page a href path to dependency file phpmyadmin package json path to vulnerable library node modules jquery validation package json dependency hierarchy x jquery validation tgz vulnerable library vulnerability details an exponential redos regular expression denial of service can be triggered in the jquery validation npm package when an attacker is able to supply arbitrary input to the method publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity high privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution pre step up your open source security game with mend
| 0
|
191,406
| 22,215,770,873
|
IssuesEvent
|
2022-06-08 01:22:00
|
ShaikUsaf/linux-3.0.35
|
https://api.github.com/repos/ShaikUsaf/linux-3.0.35
|
opened
|
CVE-2015-8845 (Medium) detected in linux-stable-rtv3.8.6
|
security vulnerability
|
## CVE-2015-8845 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linux-stable-rtv3.8.6</b></p></summary>
<p>
<p>Julia Cartwright's fork of linux-stable-rt.git</p>
<p>Library home page: <a href=https://git.kernel.org/pub/scm/linux/kernel/git/julia/linux-stable-rt.git>https://git.kernel.org/pub/scm/linux/kernel/git/julia/linux-stable-rt.git</a></p>
<p>Found in base branch: <b>master</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (1)</summary>
<p></p>
<p>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
The tm_reclaim_thread function in arch/powerpc/kernel/process.c in the Linux kernel before 4.4.1 on powerpc platforms does not ensure that TM suspend mode exists before proceeding with a tm_reclaim call, which allows local users to cause a denial of service (TM Bad Thing exception and panic) via a crafted application.
<p>Publish Date: 2016-04-27
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2015-8845>CVE-2015-8845</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2015-8845">https://nvd.nist.gov/vuln/detail/CVE-2015-8845</a></p>
<p>Release Date: 2016-04-27</p>
<p>Fix Resolution: 4.4.1</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2015-8845 (Medium) detected in linux-stable-rtv3.8.6 - ## CVE-2015-8845 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linux-stable-rtv3.8.6</b></p></summary>
<p>
<p>Julia Cartwright's fork of linux-stable-rt.git</p>
<p>Library home page: <a href=https://git.kernel.org/pub/scm/linux/kernel/git/julia/linux-stable-rt.git>https://git.kernel.org/pub/scm/linux/kernel/git/julia/linux-stable-rt.git</a></p>
<p>Found in base branch: <b>master</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (1)</summary>
<p></p>
<p>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
The tm_reclaim_thread function in arch/powerpc/kernel/process.c in the Linux kernel before 4.4.1 on powerpc platforms does not ensure that TM suspend mode exists before proceeding with a tm_reclaim call, which allows local users to cause a denial of service (TM Bad Thing exception and panic) via a crafted application.
<p>Publish Date: 2016-04-27
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2015-8845>CVE-2015-8845</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>5.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Local
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2015-8845">https://nvd.nist.gov/vuln/detail/CVE-2015-8845</a></p>
<p>Release Date: 2016-04-27</p>
<p>Fix Resolution: 4.4.1</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
non_priority
|
cve medium detected in linux stable cve medium severity vulnerability vulnerable library linux stable julia cartwright s fork of linux stable rt git library home page a href found in base branch master vulnerable source files vulnerability details the tm reclaim thread function in arch powerpc kernel process c in the linux kernel before on powerpc platforms does not ensure that tm suspend mode exists before proceeding with a tm reclaim call which allows local users to cause a denial of service tm bad thing exception and panic via a crafted application publish date url a href cvss score details base score metrics exploitability metrics attack vector local attack complexity low privileges required low user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with mend
| 0
|
426,875
| 29,667,746,792
|
IssuesEvent
|
2023-06-11 02:11:27
|
aptos-labs/aptos-core
|
https://api.github.com/repos/aptos-labs/aptos-core
|
closed
|
[Docs] list all available configuration ports and their switches in the *-node.yaml
|
documentation Stale
|
# Aptos Documentation Issue
## Description
Please list all available configuration ports and their configuration values in the *-node.yaml file in addition to the listen ports
Examples:
inspection_service:
port: 9091
6180? 6182? 6186?
## Audience
Node runners using binaries
|
1.0
|
[Docs] list all available configuration ports and their switches in the *-node.yaml - # Aptos Documentation Issue
## Description
Please list all available configuration ports and their configuration values in the *-node.yaml file in addition to the listen ports
Examples:
inspection_service:
port: 9091
6180? 6182? 6186?
## Audience
Node runners using binaries
|
non_priority
|
list all available configuration ports and their switches in the node yaml aptos documentation issue description please list all available configuration ports and their configuration values in the node yaml file in addition to the listen ports examples inspection service port audience node runners using binaries
| 0
|
78,191
| 27,362,734,498
|
IssuesEvent
|
2023-02-27 16:54:45
|
SasView/sasview
|
https://api.github.com/repos/SasView/sasview
|
opened
|
`print` statements fail after preference restart
|
Defect
|
**Describe the bug**
`OSError(22)` is produced by print statements after an automatic restart is performed.
**To Reproduce**
Run `run.py` (I used PyCharm)
Change a preference that requires restart
Save, and run some code that has a print statement
**SasView version (please complete the following information):**
- Version: main
|
1.0
|
`print` statements fail after preference restart - **Describe the bug**
`OSError(22)` is produced by print statements after an automatic restart is performed.
**To Reproduce**
Run `run.py` (I used PyCharm)
Change a preference that requires restart
Save, and run some code that has a print statement
**SasView version (please complete the following information):**
- Version: main
|
non_priority
|
print statements fail after preference restart describe the bug oserror is produced by print statements after an automatic restart is performed to reproduce run run py i used pycharm change a preference that requires restart save and run some code that has a print statement sasview version please complete the following information version main
| 0
|
212,100
| 23,857,054,505
|
IssuesEvent
|
2022-09-07 01:29:24
|
phunware/copy-with
|
https://api.github.com/repos/phunware/copy-with
|
opened
|
WS-2021-0638 (High) detected in mocha-3.5.3.tgz
|
security vulnerability
|
## WS-2021-0638 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>mocha-3.5.3.tgz</b></p></summary>
<p>simple, flexible, fun test framework</p>
<p>Library home page: <a href="https://registry.npmjs.org/mocha/-/mocha-3.5.3.tgz">https://registry.npmjs.org/mocha/-/mocha-3.5.3.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/mocha/package.json</p>
<p>
Dependency Hierarchy:
- :x: **mocha-3.5.3.tgz** (Vulnerable Library)
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
There is regular Expression Denial of Service (ReDoS) vulnerability in mocha.
It allows cause a denial of service when stripping crafted invalid function definition from strs.
<p>Publish Date: 2021-09-18
<p>URL: <a href=https://github.com/mochajs/mocha/commit/61b4b9209c2c64b32c8d48b1761c3b9384d411ea>WS-2021-0638</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://huntr.dev/bounties/1d8a3d95-d199-4129-a6ad-8eafe5e77b9e/">https://huntr.dev/bounties/1d8a3d95-d199-4129-a6ad-8eafe5e77b9e/</a></p>
<p>Release Date: 2021-09-18</p>
<p>Fix Resolution: 6.0.0-0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
WS-2021-0638 (High) detected in mocha-3.5.3.tgz - ## WS-2021-0638 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>mocha-3.5.3.tgz</b></p></summary>
<p>simple, flexible, fun test framework</p>
<p>Library home page: <a href="https://registry.npmjs.org/mocha/-/mocha-3.5.3.tgz">https://registry.npmjs.org/mocha/-/mocha-3.5.3.tgz</a></p>
<p>Path to dependency file: /package.json</p>
<p>Path to vulnerable library: /node_modules/mocha/package.json</p>
<p>
Dependency Hierarchy:
- :x: **mocha-3.5.3.tgz** (Vulnerable Library)
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
There is regular Expression Denial of Service (ReDoS) vulnerability in mocha.
It allows cause a denial of service when stripping crafted invalid function definition from strs.
<p>Publish Date: 2021-09-18
<p>URL: <a href=https://github.com/mochajs/mocha/commit/61b4b9209c2c64b32c8d48b1761c3b9384d411ea>WS-2021-0638</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>7.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: None
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://huntr.dev/bounties/1d8a3d95-d199-4129-a6ad-8eafe5e77b9e/">https://huntr.dev/bounties/1d8a3d95-d199-4129-a6ad-8eafe5e77b9e/</a></p>
<p>Release Date: 2021-09-18</p>
<p>Fix Resolution: 6.0.0-0</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with Mend [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
non_priority
|
ws high detected in mocha tgz ws high severity vulnerability vulnerable library mocha tgz simple flexible fun test framework library home page a href path to dependency file package json path to vulnerable library node modules mocha package json dependency hierarchy x mocha tgz vulnerable library vulnerability details there is regular expression denial of service redos vulnerability in mocha it allows cause a denial of service when stripping crafted invalid function definition from strs publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact none integrity impact none availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with mend
| 0
|
381,295
| 11,275,904,267
|
IssuesEvent
|
2020-01-14 21:50:19
|
googleapis/java-language
|
https://api.github.com/repos/googleapis/java-language
|
closed
|
Synthesis failed for java-language
|
autosynth failure priority: p1 type: bug
|
Hello! Autosynth couldn't regenerate java-language. :broken_heart:
Here's the output from running `synth.py`:
```
Cloning into 'working_repo'...
Switched to branch 'autosynth'
Traceback (most recent call last):
File "/home/kbuilder/.pyenv/versions/3.6.1/lib/python3.6/runpy.py", line 193, in _run_module_as_main
"__main__", mod_spec)
File "/home/kbuilder/.pyenv/versions/3.6.1/lib/python3.6/runpy.py", line 85, in _run_code
exec(code, run_globals)
File "/tmpfs/src/git/autosynth/autosynth/synth.py", line 256, in <module>
main()
File "/tmpfs/src/git/autosynth/autosynth/synth.py", line 196, in main
last_synth_commit_hash = get_last_metadata_commit(args.metadata_path)
File "/tmpfs/src/git/autosynth/autosynth/synth.py", line 149, in get_last_metadata_commit
text=True,
File "/home/kbuilder/.pyenv/versions/3.6.1/lib/python3.6/subprocess.py", line 403, in run
with Popen(*popenargs, **kwargs) as process:
TypeError: __init__() got an unexpected keyword argument 'text'
```
Google internal developers can see the full log [here](https://sponge/482a7766-2134-4c8a-887d-f6441089f633).
|
1.0
|
Synthesis failed for java-language - Hello! Autosynth couldn't regenerate java-language. :broken_heart:
Here's the output from running `synth.py`:
```
Cloning into 'working_repo'...
Switched to branch 'autosynth'
Traceback (most recent call last):
File "/home/kbuilder/.pyenv/versions/3.6.1/lib/python3.6/runpy.py", line 193, in _run_module_as_main
"__main__", mod_spec)
File "/home/kbuilder/.pyenv/versions/3.6.1/lib/python3.6/runpy.py", line 85, in _run_code
exec(code, run_globals)
File "/tmpfs/src/git/autosynth/autosynth/synth.py", line 256, in <module>
main()
File "/tmpfs/src/git/autosynth/autosynth/synth.py", line 196, in main
last_synth_commit_hash = get_last_metadata_commit(args.metadata_path)
File "/tmpfs/src/git/autosynth/autosynth/synth.py", line 149, in get_last_metadata_commit
text=True,
File "/home/kbuilder/.pyenv/versions/3.6.1/lib/python3.6/subprocess.py", line 403, in run
with Popen(*popenargs, **kwargs) as process:
TypeError: __init__() got an unexpected keyword argument 'text'
```
Google internal developers can see the full log [here](https://sponge/482a7766-2134-4c8a-887d-f6441089f633).
|
priority
|
synthesis failed for java language hello autosynth couldn t regenerate java language broken heart here s the output from running synth py cloning into working repo switched to branch autosynth traceback most recent call last file home kbuilder pyenv versions lib runpy py line in run module as main main mod spec file home kbuilder pyenv versions lib runpy py line in run code exec code run globals file tmpfs src git autosynth autosynth synth py line in main file tmpfs src git autosynth autosynth synth py line in main last synth commit hash get last metadata commit args metadata path file tmpfs src git autosynth autosynth synth py line in get last metadata commit text true file home kbuilder pyenv versions lib subprocess py line in run with popen popenargs kwargs as process typeerror init got an unexpected keyword argument text google internal developers can see the full log
| 1
|
400,796
| 11,780,784,541
|
IssuesEvent
|
2020-03-16 20:50:55
|
Warcraft-GoA-Development-Team/Warcraft-Guardians-of-Azeroth
|
https://api.github.com/repos/Warcraft-GoA-Development-Team/Warcraft-Guardians-of-Azeroth
|
closed
|
No tech in Ulduar
|
:beetle: bug :beetle: :exclamation: priority high
|
**Your mod version is:**
8b07ae4
**What expansions do you have installed?**
Don't matter
**Are you using any submods/mods? If so, which?**
GoA
**Please explain your issue in as much detail as possible:**
Ulduar don't have techs
**Steps to reproduce the issue:**
Boot the game
**Upload an attachment below: .zip of your save, or screenshots:**
<details>
<summary>Click to expand</summary>

</details>
|
1.0
|
No tech in Ulduar - **Your mod version is:**
8b07ae4
**What expansions do you have installed?**
Don't matter
**Are you using any submods/mods? If so, which?**
GoA
**Please explain your issue in as much detail as possible:**
Ulduar don't have techs
**Steps to reproduce the issue:**
Boot the game
**Upload an attachment below: .zip of your save, or screenshots:**
<details>
<summary>Click to expand</summary>

</details>
|
priority
|
no tech in ulduar your mod version is what expansions do you have installed don t matter are you using any submods mods if so which goa please explain your issue in as much detail as possible ulduar don t have techs steps to reproduce the issue boot the game upload an attachment below zip of your save or screenshots click to expand
| 1
|
661,280
| 22,046,035,808
|
IssuesEvent
|
2022-05-30 01:53:09
|
TASVideos/tasvideos
|
https://api.github.com/repos/TASVideos/tasvideos
|
closed
|
Forum/MoodReport - link to usages of each mood
|
enhancement Forum System Priority: Bottom
|
for each user's mood avatar - provide a link that will go to a page displaying the topics they used the mood in
|
1.0
|
Forum/MoodReport - link to usages of each mood - for each user's mood avatar - provide a link that will go to a page displaying the topics they used the mood in
|
priority
|
forum moodreport link to usages of each mood for each user s mood avatar provide a link that will go to a page displaying the topics they used the mood in
| 1
|
580,960
| 17,270,715,991
|
IssuesEvent
|
2021-07-22 19:26:14
|
jcserv/ulinks
|
https://api.github.com/repos/jcserv/ulinks
|
opened
|
🛠️ Refactor: Page Size
|
medium priority
|
### Motivation 🏁
Handling page size for different display sizes is a bit tricky - the frontend is good in the sense that it'll neatly organize the entries into grids responsively, but the rows are uneven if your width has rows of 3 entries (since we return 8 currently)
### Describe your refactoring solution 🛠️
After talking it through with @CometWhoosh, there's two solutions:
1. determine dimension size and request a certain page size to backend (FE+BE soln)
2. display as many full rows as the screen size allows, and then hide remaining entries in the next page (FE soln)
CC @AipioxTechson for your thoughts on this too!
|
1.0
|
🛠️ Refactor: Page Size - ### Motivation 🏁
Handling page size for different display sizes is a bit tricky - the frontend is good in the sense that it'll neatly organize the entries into grids responsively, but the rows are uneven if your width has rows of 3 entries (since we return 8 currently)
### Describe your refactoring solution 🛠️
After talking it through with @CometWhoosh, there's two solutions:
1. determine dimension size and request a certain page size to backend (FE+BE soln)
2. display as many full rows as the screen size allows, and then hide remaining entries in the next page (FE soln)
CC @AipioxTechson for your thoughts on this too!
|
priority
|
🛠️ refactor page size motivation 🏁 handling page size for different display sizes is a bit tricky the frontend is good in the sense that it ll neatly organize the entries into grids responsively but the rows are uneven if your width has rows of entries since we return currently describe your refactoring solution 🛠️ after talking it through with cometwhoosh there s two solutions determine dimension size and request a certain page size to backend fe be soln display as many full rows as the screen size allows and then hide remaining entries in the next page fe soln cc aipioxtechson for your thoughts on this too
| 1
|
142,672
| 13,037,447,543
|
IssuesEvent
|
2020-07-28 13:50:38
|
superfly/flyctl
|
https://api.github.com/repos/superfly/flyctl
|
closed
|
Certs create/check should show configuration instructions
|
cli documentation enhancement
|
It's not obvious what to do after you create a certificate with flyctl, and we should explain to people how to:
1. Create a CNAME for DNS validation
2. Just change DNS for ALPN validation (not on wildcards though)
This is a little tricky, so we could show basics and link them to docs.
```
➜ ~ flyctl certs create wat.watwatwat.wat
Hostname =
Configured = false
Issued =
Certificate Authority =
DNS Provider =
DNS Validation Instructions =
DNS Validation Hostname =
DNS Validation Target =
Source =
Created At = 0001-01-01T00:00:00Z
Status =
```
|
1.0
|
Certs create/check should show configuration instructions - It's not obvious what to do after you create a certificate with flyctl, and we should explain to people how to:
1. Create a CNAME for DNS validation
2. Just change DNS for ALPN validation (not on wildcards though)
This is a little tricky, so we could show basics and link them to docs.
```
➜ ~ flyctl certs create wat.watwatwat.wat
Hostname =
Configured = false
Issued =
Certificate Authority =
DNS Provider =
DNS Validation Instructions =
DNS Validation Hostname =
DNS Validation Target =
Source =
Created At = 0001-01-01T00:00:00Z
Status =
```
|
non_priority
|
certs create check should show configuration instructions it s not obvious what to do after you create a certificate with flyctl and we should explain to people how to create a cname for dns validation just change dns for alpn validation not on wildcards though this is a little tricky so we could show basics and link them to docs ➜ flyctl certs create wat watwatwat wat hostname configured false issued certificate authority dns provider dns validation instructions dns validation hostname dns validation target source created at status
| 0
|
219,968
| 17,139,445,981
|
IssuesEvent
|
2021-07-13 07:58:58
|
SAPDocuments/Issues
|
https://api.github.com/repos/SAPDocuments/Issues
|
closed
|
Create an SAP BTP ABAP Environment Trial User
|
Low-Prio SCPTest-2106A SCPTest-fabap SCPTest-trial1 SCPTest-trial2
|
**Tutorials:** https://developers.sap.com/tutorials/abap-environment-trial-onboarding.html
--------------------------
**Issue:** We can provide both the options to connect to system to SAP BTP ABAP Environment.
**Steps to reproduce:**
At Step 1: Start boosters:
6. The booster is now executed successfully. Download the service key for later use. The service key is needed to setup the connection in ABAP Development Tools (ADT).
**Description:**
Since we are using **Select SAP BTP Cloud Foundry Environment and click Next >** in Step 3: 2nd point to connect the system to SAP BTP ABAP Environment, downloading the service key is not required.
Or else, before downloading there must be mentioned that "If you are connecting the system to SAP BTAP ABAP Environment in Step 3: 2nd point using Service Key option, then Download the service key. The service key is needed to setup the connection in ABAP Development Tools (ADT).
So we can provide both the options 1) To upload the service key which was downloaded earlier and connect the system using service key in Step 3.
2)Select SAP BTP Cloud Foundry Environment, here we use the user id and password and continue without any upload of service key. Hence, a download is not required for this option.
Labels:
Landscape Labels: trail1, trail2
Scenario Label: SCPTest-fabap
Priority: Low
Sprint Label: SCPTest-2106A
Thanks and Regards,
Farozan
|
4.0
|
Create an SAP BTP ABAP Environment Trial User - **Tutorials:** https://developers.sap.com/tutorials/abap-environment-trial-onboarding.html
--------------------------
**Issue:** We can provide both the options to connect to system to SAP BTP ABAP Environment.
**Steps to reproduce:**
At Step 1: Start boosters:
6. The booster is now executed successfully. Download the service key for later use. The service key is needed to setup the connection in ABAP Development Tools (ADT).
**Description:**
Since we are using **Select SAP BTP Cloud Foundry Environment and click Next >** in Step 3: 2nd point to connect the system to SAP BTP ABAP Environment, downloading the service key is not required.
Or else, before downloading there must be mentioned that "If you are connecting the system to SAP BTAP ABAP Environment in Step 3: 2nd point using Service Key option, then Download the service key. The service key is needed to setup the connection in ABAP Development Tools (ADT).
So we can provide both the options 1) To upload the service key which was downloaded earlier and connect the system using service key in Step 3.
2)Select SAP BTP Cloud Foundry Environment, here we use the user id and password and continue without any upload of service key. Hence, a download is not required for this option.
Labels:
Landscape Labels: trail1, trail2
Scenario Label: SCPTest-fabap
Priority: Low
Sprint Label: SCPTest-2106A
Thanks and Regards,
Farozan
|
non_priority
|
create an sap btp abap environment trial user tutorials issue we can provide both the options to connect to system to sap btp abap environment steps to reproduce at step start boosters the booster is now executed successfully download the service key for later use the service key is needed to setup the connection in abap development tools adt description since we are using select sap btp cloud foundry environment and click next in step point to connect the system to sap btp abap environment downloading the service key is not required or else before downloading there must be mentioned that if you are connecting the system to sap btap abap environment in step point using service key option then download the service key the service key is needed to setup the connection in abap development tools adt so we can provide both the options to upload the service key which was downloaded earlier and connect the system using service key in step select sap btp cloud foundry environment here we use the user id and password and continue without any upload of service key hence a download is not required for this option labels landscape labels scenario label scptest fabap priority low sprint label scptest thanks and regards farozan
| 0
|
257,348
| 27,563,763,594
|
IssuesEvent
|
2023-03-08 01:04:54
|
tamirverthim/arthas
|
https://api.github.com/repos/tamirverthim/arthas
|
opened
|
CVE-2019-14540 (High) detected in jackson-databind-2.7.9.4.jar
|
security vulnerability
|
## CVE-2019-14540 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jackson-databind-2.7.9.4.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /core/pom.xml</p>
<p>Path to vulnerable library: /root/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.7.9.4/jackson-databind-2.7.9.4.jar</p>
<p>
Dependency Hierarchy:
- termd-core-1.1.7.1.jar (Root Library)
- :x: **jackson-databind-2.7.9.4.jar** (Vulnerable Library)
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind before 2.9.10. It is related to com.zaxxer.hikari.HikariConfig.
<p>Publish Date: 2019-09-15
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14540>CVE-2019-14540</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>9.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14540">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14540</a></p>
<p>Release Date: 2019-09-15</p>
<p>Fix Resolution: com.fasterxml.jackson.core:jackson-databind:2.8.11.5,2.9.10,2.10.0.pr3,2.11.0.rc1</p>
</p>
</details>
<p></p>
|
True
|
CVE-2019-14540 (High) detected in jackson-databind-2.7.9.4.jar - ## CVE-2019-14540 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>jackson-databind-2.7.9.4.jar</b></p></summary>
<p>General data-binding functionality for Jackson: works on core streaming API</p>
<p>Library home page: <a href="http://github.com/FasterXML/jackson">http://github.com/FasterXML/jackson</a></p>
<p>Path to dependency file: /core/pom.xml</p>
<p>Path to vulnerable library: /root/.m2/repository/com/fasterxml/jackson/core/jackson-databind/2.7.9.4/jackson-databind-2.7.9.4.jar</p>
<p>
Dependency Hierarchy:
- termd-core-1.1.7.1.jar (Root Library)
- :x: **jackson-databind-2.7.9.4.jar** (Vulnerable Library)
<p>Found in base branch: <b>master</b></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
A Polymorphic Typing issue was discovered in FasterXML jackson-databind before 2.9.10. It is related to com.zaxxer.hikari.HikariConfig.
<p>Publish Date: 2019-09-15
<p>URL: <a href=https://www.mend.io/vulnerability-database/CVE-2019-14540>CVE-2019-14540</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>9.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14540">https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-14540</a></p>
<p>Release Date: 2019-09-15</p>
<p>Fix Resolution: com.fasterxml.jackson.core:jackson-databind:2.8.11.5,2.9.10,2.10.0.pr3,2.11.0.rc1</p>
</p>
</details>
<p></p>
|
non_priority
|
cve high detected in jackson databind jar cve high severity vulnerability vulnerable library jackson databind jar general data binding functionality for jackson works on core streaming api library home page a href path to dependency file core pom xml path to vulnerable library root repository com fasterxml jackson core jackson databind jackson databind jar dependency hierarchy termd core jar root library x jackson databind jar vulnerable library found in base branch master vulnerability details a polymorphic typing issue was discovered in fasterxml jackson databind before it is related to com zaxxer hikari hikariconfig publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution com fasterxml jackson core jackson databind
| 0
|
450,496
| 13,012,337,881
|
IssuesEvent
|
2020-07-25 04:53:59
|
buddyboss/buddyboss-platform
|
https://api.github.com/repos/buddyboss/buddyboss-platform
|
opened
|
Need photo tag when upload photo for album or photos to increase the search functionality in photos
|
feature: enhancement priority: medium
|
**Is your feature request related to a problem? Please describe.**
No, this is not a problem but customers want these features.
**Describe the solution you'd like**
When we upload a photo for album or photo then we need to add an option for giving photo Tag for each photo, that's why when user search photo in the search box than will be a good result user think.
https://prnt.sc/to8371
**Support ticket links**
https://secure.helpscout.net/conversation/1227129886/83577?folderId=3955985
|
1.0
|
Need photo tag when upload photo for album or photos to increase the search functionality in photos - **Is your feature request related to a problem? Please describe.**
No, this is not a problem but customers want these features.
**Describe the solution you'd like**
When we upload a photo for album or photo then we need to add an option for giving photo Tag for each photo, that's why when user search photo in the search box than will be a good result user think.
https://prnt.sc/to8371
**Support ticket links**
https://secure.helpscout.net/conversation/1227129886/83577?folderId=3955985
|
priority
|
need photo tag when upload photo for album or photos to increase the search functionality in photos is your feature request related to a problem please describe no this is not a problem but customers want these features describe the solution you d like when we upload a photo for album or photo then we need to add an option for giving photo tag for each photo that s why when user search photo in the search box than will be a good result user think support ticket links
| 1
|
58,415
| 24,444,355,427
|
IssuesEvent
|
2022-10-06 16:39:42
|
gradido/gradido
|
https://api.github.com/repos/gradido/gradido
|
closed
|
🔧 [Refactor] Merge components
|
good first issue service: wallet frontend refactor service: admin frontend
|
<!-- You can find the latest issue templates here https://github.com/ulfgebhardt/issue-templates -->
## 🔧 Refactor ticket
Merge components
IsModerator and IsNotModerator should be merged and one componente will be enough.
admin: https://github.com/gradido/gradido/tree/master/admin/src/components/ContributionMessages/slots
wallet frontend: https://github.com/gradido/gradido/tree/master/frontend/src/components/ContributionMessages/slots
this issues fixes #2169
|
2.0
|
🔧 [Refactor] Merge components - <!-- You can find the latest issue templates here https://github.com/ulfgebhardt/issue-templates -->
## 🔧 Refactor ticket
Merge components
IsModerator and IsNotModerator should be merged and one componente will be enough.
admin: https://github.com/gradido/gradido/tree/master/admin/src/components/ContributionMessages/slots
wallet frontend: https://github.com/gradido/gradido/tree/master/frontend/src/components/ContributionMessages/slots
this issues fixes #2169
|
non_priority
|
🔧 merge components 🔧 refactor ticket merge components ismoderator and isnotmoderator should be merged and one componente will be enough admin wallet frontend this issues fixes
| 0
|
618,440
| 19,457,289,968
|
IssuesEvent
|
2021-12-23 01:34:20
|
gitpod-io/website
|
https://api.github.com/repos/gitpod-io/website
|
closed
|
[pricing]: Create the question mark popovers for the Pricing Cards.
|
priority:high section: pricing
|
- [ ] Create the question mark popovers

|
1.0
|
[pricing]: Create the question mark popovers for the Pricing Cards. - - [ ] Create the question mark popovers

|
priority
|
create the question mark popovers for the pricing cards create the question mark popovers
| 1
|
282,989
| 21,316,007,324
|
IssuesEvent
|
2022-04-16 09:32:36
|
ivanaitzliddat/pe
|
https://api.github.com/repos/ivanaitzliddat/pe
|
opened
|
Change screenshot for deleting a contact
|
severity.VeryLow type.DocumentationBug
|
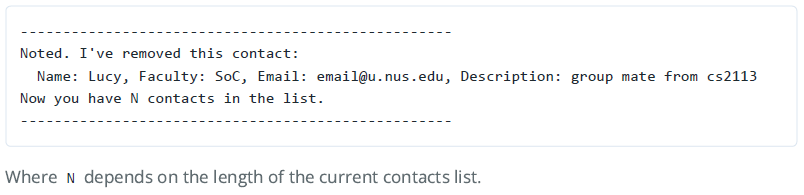
N will never be the output when a user uses it. Hence, providing a list of some sorts to justify the number shows in the expected outcome would be better.
<!--session: 1650095959978-2d35ac18-cc5d-4738-853a-84b4d2bcc82b-->
<!--Version: Web v3.4.2-->
|
1.0
|
Change screenshot for deleting a contact - 
N will never be the output when a user uses it. Hence, providing a list of some sorts to justify the number shows in the expected outcome would be better.
<!--session: 1650095959978-2d35ac18-cc5d-4738-853a-84b4d2bcc82b-->
<!--Version: Web v3.4.2-->
|
non_priority
|
change screenshot for deleting a contact n will never be the output when a user uses it hence providing a list of some sorts to justify the number shows in the expected outcome would be better
| 0
|
27,784
| 30,350,395,998
|
IssuesEvent
|
2023-07-11 18:29:24
|
mailpile/Mailpile
|
https://api.github.com/repos/mailpile/Mailpile
|
closed
|
Downloading PGP-encrypted content buglets
|
Bugs Back End Low Hanging Fruit Usability Mailpile-v1-is-Obsolete
|
Mailpile will currently transparently decrypt any attached PGP-encrypted content, which is nice.
However, this feature has two problems that need fixing:
* [ ] A way to download the encrypted data (w/o decrypting)
* [x] The decrypted data is served up with the wrong filename.
The latter issue is particularly vexing and needs to be fixed before 1.0.
Why it's bad: you download a file named `foo.zip.gpg`, which should actually be named `foo.zip`! Since it's named .gpg, the natural (or automatic) reaction is to open it using GnuPG which doesn't know what to do with the contents, which will cause even experienced users to be confused (e.g. assuming the data was corrupted somehow). Only a lucky few will think to try and directly unzip a file named `foo.zip.gpg`...
|
True
|
Downloading PGP-encrypted content buglets - Mailpile will currently transparently decrypt any attached PGP-encrypted content, which is nice.
However, this feature has two problems that need fixing:
* [ ] A way to download the encrypted data (w/o decrypting)
* [x] The decrypted data is served up with the wrong filename.
The latter issue is particularly vexing and needs to be fixed before 1.0.
Why it's bad: you download a file named `foo.zip.gpg`, which should actually be named `foo.zip`! Since it's named .gpg, the natural (or automatic) reaction is to open it using GnuPG which doesn't know what to do with the contents, which will cause even experienced users to be confused (e.g. assuming the data was corrupted somehow). Only a lucky few will think to try and directly unzip a file named `foo.zip.gpg`...
|
non_priority
|
downloading pgp encrypted content buglets mailpile will currently transparently decrypt any attached pgp encrypted content which is nice however this feature has two problems that need fixing a way to download the encrypted data w o decrypting the decrypted data is served up with the wrong filename the latter issue is particularly vexing and needs to be fixed before why it s bad you download a file named foo zip gpg which should actually be named foo zip since it s named gpg the natural or automatic reaction is to open it using gnupg which doesn t know what to do with the contents which will cause even experienced users to be confused e g assuming the data was corrupted somehow only a lucky few will think to try and directly unzip a file named foo zip gpg
| 0
|
418,588
| 12,200,171,187
|
IssuesEvent
|
2020-04-30 03:52:15
|
mandeep/sublime-text-conda
|
https://api.github.com/repos/mandeep/sublime-text-conda
|
closed
|
Use edit_settings command instead of open_file in Main.sublime-menu
|
Priority: High Status: Accepted Type: Maintenance
|
Setting definitions are currently defined with the following pattern in `Main.sublime-menu`:
```json
{
"caption": "Settings – Default",
"command": "open_file",
"args": { "file": "${packages}/Conda/Conda.sublime-settings", "platform": "Platform" }
}
```
This works without issue, but this method comes with the following caveats:
1. We have to open the Default/User options separately
2. Platform specific options must be defined for all supported platforms (each with their own `Default `and `User` component)
We can address both of these using the `edit_settings` command, which sublime uses by default for its own settings. The entirety of the `children` key can be replaced with a single command definition:
```json
{
"caption": "Settings",
"command": "edit_settings",
"args":
{
"base_file": "${packages}/Conda/Conda (${platform}).sublime-settings",
"default": "{\n\t$0\n}\n"
}
}
```
The `${platform}` environment variable takes care of our platform component. If user settings aren't defined, the `default` value creates a blank template that matches the POJO containing the default, platform specific settings.
The nice part about `edit_settings` is that both the default and user settings are opened side by side, which allows for easy editing and customization.
While consolidating `User` and `Default` options to a single `Settings` label changes the menu layout for the plugin, the new behavior matches that of editing Sublime's native options, so the end result should be a familiar experience.
I don't feel the current menu-options are a negative aspect of the plugin; this pattern is common among many popular packages, and I've used it in personal plugins as well. While sublime does a lot of things well, its documentation leaves something to be desired at times. I only recently came across `edit_settings` (you can find usage of it in `Default.sublime-commands`), and after putting into my own projects, overriding defaults is now much easier.
|
1.0
|
Use edit_settings command instead of open_file in Main.sublime-menu - Setting definitions are currently defined with the following pattern in `Main.sublime-menu`:
```json
{
"caption": "Settings – Default",
"command": "open_file",
"args": { "file": "${packages}/Conda/Conda.sublime-settings", "platform": "Platform" }
}
```
This works without issue, but this method comes with the following caveats:
1. We have to open the Default/User options separately
2. Platform specific options must be defined for all supported platforms (each with their own `Default `and `User` component)
We can address both of these using the `edit_settings` command, which sublime uses by default for its own settings. The entirety of the `children` key can be replaced with a single command definition:
```json
{
"caption": "Settings",
"command": "edit_settings",
"args":
{
"base_file": "${packages}/Conda/Conda (${platform}).sublime-settings",
"default": "{\n\t$0\n}\n"
}
}
```
The `${platform}` environment variable takes care of our platform component. If user settings aren't defined, the `default` value creates a blank template that matches the POJO containing the default, platform specific settings.
The nice part about `edit_settings` is that both the default and user settings are opened side by side, which allows for easy editing and customization.
While consolidating `User` and `Default` options to a single `Settings` label changes the menu layout for the plugin, the new behavior matches that of editing Sublime's native options, so the end result should be a familiar experience.
I don't feel the current menu-options are a negative aspect of the plugin; this pattern is common among many popular packages, and I've used it in personal plugins as well. While sublime does a lot of things well, its documentation leaves something to be desired at times. I only recently came across `edit_settings` (you can find usage of it in `Default.sublime-commands`), and after putting into my own projects, overriding defaults is now much easier.
|
priority
|
use edit settings command instead of open file in main sublime menu setting definitions are currently defined with the following pattern in main sublime menu json caption settings – default command open file args file packages conda conda sublime settings platform platform this works without issue but this method comes with the following caveats we have to open the default user options separately platform specific options must be defined for all supported platforms each with their own default and user component we can address both of these using the edit settings command which sublime uses by default for its own settings the entirety of the children key can be replaced with a single command definition json caption settings command edit settings args base file packages conda conda platform sublime settings default n t n n the platform environment variable takes care of our platform component if user settings aren t defined the default value creates a blank template that matches the pojo containing the default platform specific settings the nice part about edit settings is that both the default and user settings are opened side by side which allows for easy editing and customization while consolidating user and default options to a single settings label changes the menu layout for the plugin the new behavior matches that of editing sublime s native options so the end result should be a familiar experience i don t feel the current menu options are a negative aspect of the plugin this pattern is common among many popular packages and i ve used it in personal plugins as well while sublime does a lot of things well its documentation leaves something to be desired at times i only recently came across edit settings you can find usage of it in default sublime commands and after putting into my own projects overriding defaults is now much easier
| 1
|
55,063
| 13,958,370,970
|
IssuesEvent
|
2020-10-24 11:37:18
|
LayerXcom/anonify
|
https://api.github.com/repos/LayerXcom/anonify
|
closed
|
[anonify-eth-driver] All error handling at the time of event fetching is delayed after block height cache
|
Problem: bug Problem: security
|
* 特定の不正なトランザクションにより、ネットワーク全体が停止する可能性があるのでイベント取得時のあらゆるエラー処理はブロック高キャッシュ後に遅延処理する(つまり、エラーが発生するイベント同期は全てスキップする)
* 一方、特定のTEEインスタンスのみで発生するエラーの場合は状態の一貫性が崩れるので、スキップしたイベントを後から特定しそこからリトライ処理できるように識別可能なログを取得する
https://github.com/LayerXcom/anonify/blob/f829ed34d9cee41ee30f8e6395d6fcc29406bca7/modules/anonify-eth-driver/src/eth/event_watcher.rs#L43-L49
|
True
|
[anonify-eth-driver] All error handling at the time of event fetching is delayed after block height cache - * 特定の不正なトランザクションにより、ネットワーク全体が停止する可能性があるのでイベント取得時のあらゆるエラー処理はブロック高キャッシュ後に遅延処理する(つまり、エラーが発生するイベント同期は全てスキップする)
* 一方、特定のTEEインスタンスのみで発生するエラーの場合は状態の一貫性が崩れるので、スキップしたイベントを後から特定しそこからリトライ処理できるように識別可能なログを取得する
https://github.com/LayerXcom/anonify/blob/f829ed34d9cee41ee30f8e6395d6fcc29406bca7/modules/anonify-eth-driver/src/eth/event_watcher.rs#L43-L49
|
non_priority
|
all error handling at the time of event fetching is delayed after block height cache 特定の不正なトランザクションにより、ネットワーク全体が停止する可能性があるのでイベント取得時のあらゆるエラー処理はブロック高キャッシュ後に遅延処理する(つまり、エラーが発生するイベント同期は全てスキップする) 一方、特定のteeインスタンスのみで発生するエラーの場合は状態の一貫性が崩れるので、スキップしたイベントを後から特定しそこからリトライ処理できるように識別可能なログを取得する
| 0
|
91,191
| 3,839,391,983
|
IssuesEvent
|
2016-04-03 02:08:19
|
theBoardlist/website
|
https://api.github.com/repos/theBoardlist/website
|
closed
|
[emails] update rejection emails
|
B-Sprint High Priority
|
From Pending, if admin rejects user, send email as follows:
- if rejected endorser, send 1 - Sorry Email to rejected endorser
- if rejected candidate, send 1a - Sorry Email to rejected candidate
- if rejected searcher, send 1b - Sorry email to rejected searcher
These emails have been pushed to Mandrill.
|
1.0
|
[emails] update rejection emails - From Pending, if admin rejects user, send email as follows:
- if rejected endorser, send 1 - Sorry Email to rejected endorser
- if rejected candidate, send 1a - Sorry Email to rejected candidate
- if rejected searcher, send 1b - Sorry email to rejected searcher
These emails have been pushed to Mandrill.
|
priority
|
update rejection emails from pending if admin rejects user send email as follows if rejected endorser send sorry email to rejected endorser if rejected candidate send sorry email to rejected candidate if rejected searcher send sorry email to rejected searcher these emails have been pushed to mandrill
| 1
|
38,120
| 18,952,095,914
|
IssuesEvent
|
2021-11-18 16:07:34
|
benwbrum/fromthepage
|
https://api.github.com/repos/benwbrum/fromthepage
|
closed
|
Owner homepage performance with large numbers of document sets
|
performance
|
While there are no glaringly slow queries executed when displaying https://fromthepage.com/lva, the overall page performance is slow because we query to see whether the user is allowed to see each document set owned by the owner. If we instead got a list of all authorized document set IDs for the user in a single query and moved the display logic to check against that, we'd eliminate hundreds of queries.
This is the query that's running hundreds of times:
```
app/models/user.rb:115:in `collaborator?'
app/models/document_set.rb:38:in `show_to?'
app/models/user.rb:184:in `block in visible_collections_and_document_sets'
app/models/user.rb:184:in `select'
app/models/user.rb:184:in `visible_collections_and_document_sets'
app/controllers/user_controller.rb:70:in `profile'
app/controllers/application_controller.rb:29:in `switch_locale'
SELECT 1 AS one FROM `users` INNER JOIN `document_set_collaborators` ON `users`.`id` = `document_set_collaborators`.`user_id` WHERE `document_set_collaborators`.`document_set_id` = 453 AND `users`.`id` = 2 LIMIT 1;
```
|
True
|
Owner homepage performance with large numbers of document sets - While there are no glaringly slow queries executed when displaying https://fromthepage.com/lva, the overall page performance is slow because we query to see whether the user is allowed to see each document set owned by the owner. If we instead got a list of all authorized document set IDs for the user in a single query and moved the display logic to check against that, we'd eliminate hundreds of queries.
This is the query that's running hundreds of times:
```
app/models/user.rb:115:in `collaborator?'
app/models/document_set.rb:38:in `show_to?'
app/models/user.rb:184:in `block in visible_collections_and_document_sets'
app/models/user.rb:184:in `select'
app/models/user.rb:184:in `visible_collections_and_document_sets'
app/controllers/user_controller.rb:70:in `profile'
app/controllers/application_controller.rb:29:in `switch_locale'
SELECT 1 AS one FROM `users` INNER JOIN `document_set_collaborators` ON `users`.`id` = `document_set_collaborators`.`user_id` WHERE `document_set_collaborators`.`document_set_id` = 453 AND `users`.`id` = 2 LIMIT 1;
```
|
non_priority
|
owner homepage performance with large numbers of document sets while there are no glaringly slow queries executed when displaying the overall page performance is slow because we query to see whether the user is allowed to see each document set owned by the owner if we instead got a list of all authorized document set ids for the user in a single query and moved the display logic to check against that we d eliminate hundreds of queries this is the query that s running hundreds of times app models user rb in collaborator app models document set rb in show to app models user rb in block in visible collections and document sets app models user rb in select app models user rb in visible collections and document sets app controllers user controller rb in profile app controllers application controller rb in switch locale select as one from users inner join document set collaborators on users id document set collaborators user id where document set collaborators document set id and users id limit
| 0
|
237
| 2,518,244,240
|
IssuesEvent
|
2015-01-16 20:36:02
|
dart-lang/dartdoc-viewer
|
https://api.github.com/repos/dart-lang/dartdoc-viewer
|
closed
|
External links to anchors don't always scroll to the anchor
|
bug imported-from-google-code triaged
|
_From @kwalrath on August 30, 2014 00:10:40_
When I go to http://www.dartdocs.org/documentation/angular/0.14.0/index.html#angular/angular-tracing@id_traceDetectWTF (for example), traceDetectWTF is neither highlighted nor scrolled to. (This is in Chrome 38.) If I click traceDetectWTF in the TOC to the right, then the page correctly scrolls to and highlights that anchor, without the URL changing.
However, if I go to https://api.dartlang.org/apidocs/channels/stable/dartdoc-viewer/dart-core.DateTime#id_isBefore , it *does* go to the right place.
Perhaps dartdocs.org uses a different version of DartDocViewer? And/or maybe it's the difference in URL formats that matters? More details at https://github.com/dart-lang/www.dartlang.org/pull/362 .
_Original issue: http://code.google.com/p/dart/issues/detail?id=20752_
|
1.0
|
External links to anchors don't always scroll to the anchor - _From @kwalrath on August 30, 2014 00:10:40_
When I go to http://www.dartdocs.org/documentation/angular/0.14.0/index.html#angular/angular-tracing@id_traceDetectWTF (for example), traceDetectWTF is neither highlighted nor scrolled to. (This is in Chrome 38.) If I click traceDetectWTF in the TOC to the right, then the page correctly scrolls to and highlights that anchor, without the URL changing.
However, if I go to https://api.dartlang.org/apidocs/channels/stable/dartdoc-viewer/dart-core.DateTime#id_isBefore , it *does* go to the right place.
Perhaps dartdocs.org uses a different version of DartDocViewer? And/or maybe it's the difference in URL formats that matters? More details at https://github.com/dart-lang/www.dartlang.org/pull/362 .
_Original issue: http://code.google.com/p/dart/issues/detail?id=20752_
|
non_priority
|
external links to anchors don t always scroll to the anchor from kwalrath on august when i go to for example tracedetectwtf is neither highlighted nor scrolled to this is in chrome if i click tracedetectwtf in the toc to the right then the page correctly scrolls to and highlights that anchor without the url changing however if i go to it does go to the right place perhaps dartdocs org uses a different version of dartdocviewer and or maybe it s the difference in url formats that matters more details at original issue
| 0
|
191,873
| 22,215,859,185
|
IssuesEvent
|
2022-06-08 01:30:55
|
panasalap/linux-4.1.15
|
https://api.github.com/repos/panasalap/linux-4.1.15
|
reopened
|
CVE-2016-9555 (High) detected in linux179e72b561d3d331c850e1a5779688d7a7de5246
|
security vulnerability
|
## CVE-2016-9555 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linux179e72b561d3d331c850e1a5779688d7a7de5246</b></p></summary>
<p>
<p>Linux kernel stable tree mirror</p>
<p>Library home page: <a href=https://github.com/gregkh/linux.git>https://github.com/gregkh/linux.git</a></p>
<p>Found in HEAD commit: <a href="https://github.com/panasalap/linux-4.1.15/commit/aae4c2fa46027fd4c477372871df090c6b94f3f1">aae4c2fa46027fd4c477372871df090c6b94f3f1</a></p>
<p>Found in base branch: <b>master</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (2)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/net/sctp/sm_statefuns.c</b>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/net/sctp/sm_statefuns.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
The sctp_sf_ootb function in net/sctp/sm_statefuns.c in the Linux kernel before 4.8.8 lacks chunk-length checking for the first chunk, which allows remote attackers to cause a denial of service (out-of-bounds slab access) or possibly have unspecified other impact via crafted SCTP data.
<p>Publish Date: 2016-11-28
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2016-9555>CVE-2016-9555</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>9.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2016-9555">https://nvd.nist.gov/vuln/detail/CVE-2016-9555</a></p>
<p>Release Date: 2016-11-28</p>
<p>Fix Resolution: 4.8.8</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2016-9555 (High) detected in linux179e72b561d3d331c850e1a5779688d7a7de5246 - ## CVE-2016-9555 - High Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>linux179e72b561d3d331c850e1a5779688d7a7de5246</b></p></summary>
<p>
<p>Linux kernel stable tree mirror</p>
<p>Library home page: <a href=https://github.com/gregkh/linux.git>https://github.com/gregkh/linux.git</a></p>
<p>Found in HEAD commit: <a href="https://github.com/panasalap/linux-4.1.15/commit/aae4c2fa46027fd4c477372871df090c6b94f3f1">aae4c2fa46027fd4c477372871df090c6b94f3f1</a></p>
<p>Found in base branch: <b>master</b></p></p>
</details>
</p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Source Files (2)</summary>
<p></p>
<p>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/net/sctp/sm_statefuns.c</b>
<img src='https://s3.amazonaws.com/wss-public/bitbucketImages/xRedImage.png' width=19 height=20> <b>/net/sctp/sm_statefuns.c</b>
</p>
</details>
<p></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/high_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
The sctp_sf_ootb function in net/sctp/sm_statefuns.c in the Linux kernel before 4.8.8 lacks chunk-length checking for the first chunk, which allows remote attackers to cause a denial of service (out-of-bounds slab access) or possibly have unspecified other impact via crafted SCTP data.
<p>Publish Date: 2016-11-28
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2016-9555>CVE-2016-9555</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>9.8</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: High
- Integrity Impact: High
- Availability Impact: High
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2016-9555">https://nvd.nist.gov/vuln/detail/CVE-2016-9555</a></p>
<p>Release Date: 2016-11-28</p>
<p>Fix Resolution: 4.8.8</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
non_priority
|
cve high detected in cve high severity vulnerability vulnerable library linux kernel stable tree mirror library home page a href found in head commit a href found in base branch master vulnerable source files net sctp sm statefuns c net sctp sm statefuns c vulnerability details the sctp sf ootb function in net sctp sm statefuns c in the linux kernel before lacks chunk length checking for the first chunk which allows remote attackers to cause a denial of service out of bounds slab access or possibly have unspecified other impact via crafted sctp data publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction none scope unchanged impact metrics confidentiality impact high integrity impact high availability impact high for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource
| 0
|
12,741
| 9,780,321,762
|
IssuesEvent
|
2019-06-07 16:34:39
|
Azure/azure-cli
|
https://api.github.com/repos/Azure/azure-cli
|
closed
|
az cosmosdb create fails with 'too many 502 error responses'
|
Cosmos Question Service Attention
|
**Describe the bug**
When running az cosmosdb create, the command fails with 'too many 502 error responses' message.
**To Reproduce**
Run
```
az cosmosdb create --name cosmosdbtest2`
--resource-group cosmosdbtest1 `
--default-consistency-level Session `
--max-interval 5 `
--max-staleness-prefix 100
```
**Expected behavior**
The Cosmos DB instance is created without errors.
**Environment summary**
azure cli run Powershell window on Windows 10 Pro
az --version:
> acr (2.1.3)
> acs (2.3.0)
> advisor (0.6.0)
> ams (0.2.2)
> appservice (0.2.2)
> backup (1.2.0)
> batch (3.3.2)
> batchai (0.4.1)
> billing (0.2.0)
> cdn (0.1.0)
> cloud (2.1.0)
> cognitiveservices (0.2.0)
> command-modules-nspkg (2.0.2)
> configure (2.0.18)
> consumption (0.4.0)
> container (0.3.3)
> core (2.0.44)
> cosmosdb (0.2.0)
> dla (0.2.1)
> dls (0.1.0)
> dms (0.1.0)
> eventgrid (0.2.0)
> eventhubs (0.2.2)
> extension (0.2.1)
> feedback (2.1.4)
> find (0.2.12)
> interactive (0.3.28)
> iot (0.3.0)
> iotcentral (0.1.0)
> keyvault (2.2.2)
> lab (0.1.0)
> maps (0.3.1)
> monitor (0.2.2)
> network (2.2.3)
> nspkg (3.0.3)
> policyinsights (0.1.0)
> profile (2.1.1)
> rdbms (0.3.0)
> redis (0.3.0)
> relay (0.1.0)
> reservations (0.3.1)
> resource (2.1.2)
> role (2.1.3)
> search (0.1.1)
> servicebus (0.2.1)
> servicefabric (0.1.1)
> sql (2.1.2)
> storage (2.2.0)
> telemetry (1.0.0)
> vm (2.2.1)
**Additional context**
Full error message:
Error occurred in request., RetryError: HTTPSConnectionPool(host='management.azure.com', port=443): Max retries exceeded with url: /subscriptions/d090826d-21e1-44d7-9696-04e33887d08e/resourceGroups/cosmosdbtest1/providers/Microsoft.DocumentDB/databaseAccounts/cosmosdbtest2?api-version=2015-04-08 (Caused by ResponseError('too many 502 error responses',))
Traceback (most recent call last):
File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\requests\adapters.py", line 445, in send
timeout=timeout
File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\urllib3\connectionpool.py", line 731, in urlopen
body_pos=body_pos, **response_kw)
File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\urllib3\connectionpool.py", line 731, in urlopen
body_pos=body_pos, **response_kw)
File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\urllib3\connectionpool.py", line 731, in urlopen
body_pos=body_pos, **response_kw)
File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\urllib3\connectionpool.py", line 711, in urlopen
retries = retries.increment(method, url, response=response, _pool=self)
File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\urllib3\util\retry.py", line 398, in increment
raise MaxRetryError(_pool, url, error or ResponseError(cause))
urllib3.exceptions.MaxRetryError: HTTPSConnectionPool(host='management.azure.com', port=443): Max retries exceeded with url: /subscriptions/d090826d-21e1-44d7-9696-04e33887d08e/resourceGroups/cosmosdbtest1/providers/Microsoft.DocumentDB/databaseAccounts/cosmosdbtest2?api-version=2015-04-08 (Caused by ResponseError('too many 502 error responses',))
During handling of the above exception, another exception occurred:
> Traceback (most recent call last):
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\msrest\service_client.py", line 342, in send
> response = http_driver.send(request, **kwargs)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\msrest\service_client.py", line 187, in send
> **kwargs)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\requests\sessions.py", line 512, in request
> resp = self.send(prep, **send_kwargs)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\requests\sessions.py", line 622, in send
> r = adapter.send(request, **kwargs)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\requests\adapters.py", line 504, in send
> raise RetryError(e, request=request)
> requests.exceptions.RetryError: HTTPSConnectionPool(host='management.azure.com', port=443): Max retries exceeded with url: /subscriptions/d090826d-21e1-44d7-9696-04e33887d08e/resourceGroups/cosmosdbtest1/providers/Microsoft.DocumentDB/databaseAccounts/cosmosdbtest2?api-version=2015-04-08 (Caused by ResponseError('too many 502 error responses',))
>
> During handling of the above exception, another exception occurred:
>
> Traceback (most recent call last):
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\knack\cli.py", line 197, in invoke
> cmd_result = self.invocation.execute(args)
> File "C:\Users\troyd\AppData\Local\Temp\pip-install-_jje8pgf\azure-cli-core\azure\cli\core\commands\__init__.py", line 369, in execute
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\six.py", line 693, in reraise
> raise value
> File "C:\Users\troyd\AppData\Local\Temp\pip-install-_jje8pgf\azure-cli-core\azure\cli\core\commands\__init__.py", line 343, in execute
> File "C:\Users\troyd\AppData\Local\Temp\pip-install-_jje8pgf\azure-cli-core\azure\cli\core\commands\__init__.py", line 182, in __call__
> File "C:\Users\troyd\AppData\Local\Temp\pip-install-_jje8pgf\azure-cli-core\azure\cli\core\__init__.py", line 436, in default_command_handler
> File "C:\Users\troyd\AppData\Local\Temp\pip-install-_jje8pgf\azure-cli-cosmosdb\azure\cli\command_modules\cosmosdb\custom.py", line 85, in cli_cosmosdb_create
> File "C:\Users\troyd\AppData\Local\Temp\pip-install-_jje8pgf\azure-mgmt-cosmosdb\azure\mgmt\cosmosdb\operations\database_accounts_operations.py", line 291, in create_or_update
> File "C:\Users\troyd\AppData\Local\Temp\pip-install-_jje8pgf\azure-mgmt-cosmosdb\azure\mgmt\cosmosdb\operations\database_accounts_operations.py", line 242, in _create_or_update_initial
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\msrest\service_client.py", line 369, in send
> raise_with_traceback(ClientRequestError, msg, err)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\msrest\exceptions.py", line 54, in raise_with_traceback
> raise error.with_traceback(exc_traceback)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\msrest\service_client.py", line 342, in send
> response = http_driver.send(request, **kwargs)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\msrest\service_client.py", line 187, in send
> **kwargs)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\requests\sessions.py", line 512, in request
> resp = self.send(prep, **send_kwargs)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\requests\sessions.py", line 622, in send
> r = adapter.send(request, **kwargs)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\requests\adapters.py", line 504, in send
> raise RetryError(e, request=request)
> msrest.exceptions.ClientRequestError: Error occurred in request., RetryError: HTTPSConnectionPool(host='management.azure.com', port=443): Max retries exceeded with url: /subscriptions/d090826d-21e1-44d7-9696-04e33887d08e/resourceGroups/cosmosdbtest1/providers/Microsoft.DocumentDB/databaseAccounts/cosmosdbtest2?api-version=2015-04-08 (Caused by ResponseError('too many 502 error responses',))
|
1.0
|
az cosmosdb create fails with 'too many 502 error responses' - **Describe the bug**
When running az cosmosdb create, the command fails with 'too many 502 error responses' message.
**To Reproduce**
Run
```
az cosmosdb create --name cosmosdbtest2`
--resource-group cosmosdbtest1 `
--default-consistency-level Session `
--max-interval 5 `
--max-staleness-prefix 100
```
**Expected behavior**
The Cosmos DB instance is created without errors.
**Environment summary**
azure cli run Powershell window on Windows 10 Pro
az --version:
> acr (2.1.3)
> acs (2.3.0)
> advisor (0.6.0)
> ams (0.2.2)
> appservice (0.2.2)
> backup (1.2.0)
> batch (3.3.2)
> batchai (0.4.1)
> billing (0.2.0)
> cdn (0.1.0)
> cloud (2.1.0)
> cognitiveservices (0.2.0)
> command-modules-nspkg (2.0.2)
> configure (2.0.18)
> consumption (0.4.0)
> container (0.3.3)
> core (2.0.44)
> cosmosdb (0.2.0)
> dla (0.2.1)
> dls (0.1.0)
> dms (0.1.0)
> eventgrid (0.2.0)
> eventhubs (0.2.2)
> extension (0.2.1)
> feedback (2.1.4)
> find (0.2.12)
> interactive (0.3.28)
> iot (0.3.0)
> iotcentral (0.1.0)
> keyvault (2.2.2)
> lab (0.1.0)
> maps (0.3.1)
> monitor (0.2.2)
> network (2.2.3)
> nspkg (3.0.3)
> policyinsights (0.1.0)
> profile (2.1.1)
> rdbms (0.3.0)
> redis (0.3.0)
> relay (0.1.0)
> reservations (0.3.1)
> resource (2.1.2)
> role (2.1.3)
> search (0.1.1)
> servicebus (0.2.1)
> servicefabric (0.1.1)
> sql (2.1.2)
> storage (2.2.0)
> telemetry (1.0.0)
> vm (2.2.1)
**Additional context**
Full error message:
Error occurred in request., RetryError: HTTPSConnectionPool(host='management.azure.com', port=443): Max retries exceeded with url: /subscriptions/d090826d-21e1-44d7-9696-04e33887d08e/resourceGroups/cosmosdbtest1/providers/Microsoft.DocumentDB/databaseAccounts/cosmosdbtest2?api-version=2015-04-08 (Caused by ResponseError('too many 502 error responses',))
Traceback (most recent call last):
File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\requests\adapters.py", line 445, in send
timeout=timeout
File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\urllib3\connectionpool.py", line 731, in urlopen
body_pos=body_pos, **response_kw)
File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\urllib3\connectionpool.py", line 731, in urlopen
body_pos=body_pos, **response_kw)
File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\urllib3\connectionpool.py", line 731, in urlopen
body_pos=body_pos, **response_kw)
File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\urllib3\connectionpool.py", line 711, in urlopen
retries = retries.increment(method, url, response=response, _pool=self)
File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\urllib3\util\retry.py", line 398, in increment
raise MaxRetryError(_pool, url, error or ResponseError(cause))
urllib3.exceptions.MaxRetryError: HTTPSConnectionPool(host='management.azure.com', port=443): Max retries exceeded with url: /subscriptions/d090826d-21e1-44d7-9696-04e33887d08e/resourceGroups/cosmosdbtest1/providers/Microsoft.DocumentDB/databaseAccounts/cosmosdbtest2?api-version=2015-04-08 (Caused by ResponseError('too many 502 error responses',))
During handling of the above exception, another exception occurred:
> Traceback (most recent call last):
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\msrest\service_client.py", line 342, in send
> response = http_driver.send(request, **kwargs)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\msrest\service_client.py", line 187, in send
> **kwargs)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\requests\sessions.py", line 512, in request
> resp = self.send(prep, **send_kwargs)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\requests\sessions.py", line 622, in send
> r = adapter.send(request, **kwargs)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\requests\adapters.py", line 504, in send
> raise RetryError(e, request=request)
> requests.exceptions.RetryError: HTTPSConnectionPool(host='management.azure.com', port=443): Max retries exceeded with url: /subscriptions/d090826d-21e1-44d7-9696-04e33887d08e/resourceGroups/cosmosdbtest1/providers/Microsoft.DocumentDB/databaseAccounts/cosmosdbtest2?api-version=2015-04-08 (Caused by ResponseError('too many 502 error responses',))
>
> During handling of the above exception, another exception occurred:
>
> Traceback (most recent call last):
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\knack\cli.py", line 197, in invoke
> cmd_result = self.invocation.execute(args)
> File "C:\Users\troyd\AppData\Local\Temp\pip-install-_jje8pgf\azure-cli-core\azure\cli\core\commands\__init__.py", line 369, in execute
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\six.py", line 693, in reraise
> raise value
> File "C:\Users\troyd\AppData\Local\Temp\pip-install-_jje8pgf\azure-cli-core\azure\cli\core\commands\__init__.py", line 343, in execute
> File "C:\Users\troyd\AppData\Local\Temp\pip-install-_jje8pgf\azure-cli-core\azure\cli\core\commands\__init__.py", line 182, in __call__
> File "C:\Users\troyd\AppData\Local\Temp\pip-install-_jje8pgf\azure-cli-core\azure\cli\core\__init__.py", line 436, in default_command_handler
> File "C:\Users\troyd\AppData\Local\Temp\pip-install-_jje8pgf\azure-cli-cosmosdb\azure\cli\command_modules\cosmosdb\custom.py", line 85, in cli_cosmosdb_create
> File "C:\Users\troyd\AppData\Local\Temp\pip-install-_jje8pgf\azure-mgmt-cosmosdb\azure\mgmt\cosmosdb\operations\database_accounts_operations.py", line 291, in create_or_update
> File "C:\Users\troyd\AppData\Local\Temp\pip-install-_jje8pgf\azure-mgmt-cosmosdb\azure\mgmt\cosmosdb\operations\database_accounts_operations.py", line 242, in _create_or_update_initial
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\msrest\service_client.py", line 369, in send
> raise_with_traceback(ClientRequestError, msg, err)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\msrest\exceptions.py", line 54, in raise_with_traceback
> raise error.with_traceback(exc_traceback)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\msrest\service_client.py", line 342, in send
> response = http_driver.send(request, **kwargs)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\msrest\service_client.py", line 187, in send
> **kwargs)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\requests\sessions.py", line 512, in request
> resp = self.send(prep, **send_kwargs)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\requests\sessions.py", line 622, in send
> r = adapter.send(request, **kwargs)
> File "C:\Program Files (x86)\Microsoft SDKs\Azure\CLI2\Lib\site-packages\requests\adapters.py", line 504, in send
> raise RetryError(e, request=request)
> msrest.exceptions.ClientRequestError: Error occurred in request., RetryError: HTTPSConnectionPool(host='management.azure.com', port=443): Max retries exceeded with url: /subscriptions/d090826d-21e1-44d7-9696-04e33887d08e/resourceGroups/cosmosdbtest1/providers/Microsoft.DocumentDB/databaseAccounts/cosmosdbtest2?api-version=2015-04-08 (Caused by ResponseError('too many 502 error responses',))
|
non_priority
|
az cosmosdb create fails with too many error responses describe the bug when running az cosmosdb create the command fails with too many error responses message to reproduce run az cosmosdb create name resource group default consistency level session max interval max staleness prefix expected behavior the cosmos db instance is created without errors environment summary azure cli run powershell window on windows pro az version acr acs advisor ams appservice backup batch batchai billing cdn cloud cognitiveservices command modules nspkg configure consumption container core cosmosdb dla dls dms eventgrid eventhubs extension feedback find interactive iot iotcentral keyvault lab maps monitor network nspkg policyinsights profile rdbms redis relay reservations resource role search servicebus servicefabric sql storage telemetry vm additional context full error message error occurred in request retryerror httpsconnectionpool host management azure com port max retries exceeded with url subscriptions resourcegroups providers microsoft documentdb databaseaccounts api version caused by responseerror too many error responses traceback most recent call last file c program files microsoft sdks azure lib site packages requests adapters py line in send timeout timeout file c program files microsoft sdks azure lib site packages connectionpool py line in urlopen body pos body pos response kw file c program files microsoft sdks azure lib site packages connectionpool py line in urlopen body pos body pos response kw file c program files microsoft sdks azure lib site packages connectionpool py line in urlopen body pos body pos response kw file c program files microsoft sdks azure lib site packages connectionpool py line in urlopen retries retries increment method url response response pool self file c program files microsoft sdks azure lib site packages util retry py line in increment raise maxretryerror pool url error or responseerror cause exceptions maxretryerror httpsconnectionpool host management azure com port max retries exceeded with url subscriptions resourcegroups providers microsoft documentdb databaseaccounts api version caused by responseerror too many error responses during handling of the above exception another exception occurred traceback most recent call last file c program files microsoft sdks azure lib site packages msrest service client py line in send response http driver send request kwargs file c program files microsoft sdks azure lib site packages msrest service client py line in send kwargs file c program files microsoft sdks azure lib site packages requests sessions py line in request resp self send prep send kwargs file c program files microsoft sdks azure lib site packages requests sessions py line in send r adapter send request kwargs file c program files microsoft sdks azure lib site packages requests adapters py line in send raise retryerror e request request requests exceptions retryerror httpsconnectionpool host management azure com port max retries exceeded with url subscriptions resourcegroups providers microsoft documentdb databaseaccounts api version caused by responseerror too many error responses during handling of the above exception another exception occurred traceback most recent call last file c program files microsoft sdks azure lib site packages knack cli py line in invoke cmd result self invocation execute args file c users troyd appdata local temp pip install azure cli core azure cli core commands init py line in execute file c program files microsoft sdks azure lib site packages six py line in reraise raise value file c users troyd appdata local temp pip install azure cli core azure cli core commands init py line in execute file c users troyd appdata local temp pip install azure cli core azure cli core commands init py line in call file c users troyd appdata local temp pip install azure cli core azure cli core init py line in default command handler file c users troyd appdata local temp pip install azure cli cosmosdb azure cli command modules cosmosdb custom py line in cli cosmosdb create file c users troyd appdata local temp pip install azure mgmt cosmosdb azure mgmt cosmosdb operations database accounts operations py line in create or update file c users troyd appdata local temp pip install azure mgmt cosmosdb azure mgmt cosmosdb operations database accounts operations py line in create or update initial file c program files microsoft sdks azure lib site packages msrest service client py line in send raise with traceback clientrequesterror msg err file c program files microsoft sdks azure lib site packages msrest exceptions py line in raise with traceback raise error with traceback exc traceback file c program files microsoft sdks azure lib site packages msrest service client py line in send response http driver send request kwargs file c program files microsoft sdks azure lib site packages msrest service client py line in send kwargs file c program files microsoft sdks azure lib site packages requests sessions py line in request resp self send prep send kwargs file c program files microsoft sdks azure lib site packages requests sessions py line in send r adapter send request kwargs file c program files microsoft sdks azure lib site packages requests adapters py line in send raise retryerror e request request msrest exceptions clientrequesterror error occurred in request retryerror httpsconnectionpool host management azure com port max retries exceeded with url subscriptions resourcegroups providers microsoft documentdb databaseaccounts api version caused by responseerror too many error responses
| 0
|
356,127
| 10,589,090,791
|
IssuesEvent
|
2019-10-09 04:44:25
|
AY1920S1-CS2103T-W13-3/main
|
https://api.github.com/repos/AY1920S1-CS2103T-W13-3/main
|
opened
|
Editing cheatsheet feature
|
priority.High type.Task
|
Implementing 'editing' command so that users can customize the cheatsheet
|
1.0
|
Editing cheatsheet feature - Implementing 'editing' command so that users can customize the cheatsheet
|
priority
|
editing cheatsheet feature implementing editing command so that users can customize the cheatsheet
| 1
|
330,801
| 28,485,847,948
|
IssuesEvent
|
2023-04-18 07:49:13
|
unifyai/ivy
|
https://api.github.com/repos/unifyai/ivy
|
reopened
|
Fix jax_numpy_manipulation.test_jax_numpy_vsplit
|
JAX Frontend Sub Task Failing Test
|
| | |
|---|---|
|tensorflow|<a href="https://github.com/unifyai/ivy/actions/runs/4723000381/jobs/8378357215" rel="noopener noreferrer" target="_blank"><img src=https://img.shields.io/badge/-success-success></a>
|torch|<a href="https://github.com/unifyai/ivy/actions/runs/4723000381/jobs/8378357215" rel="noopener noreferrer" target="_blank"><img src=https://img.shields.io/badge/-failure-red></a>
|numpy|<a href="https://github.com/unifyai/ivy/actions/runs/4723000381/jobs/8378357215" rel="noopener noreferrer" target="_blank"><img src=https://img.shields.io/badge/-success-success></a>
|jax|<a href="https://github.com/unifyai/ivy/actions/runs/4723000381/jobs/8378357215" rel="noopener noreferrer" target="_blank"><img src=https://img.shields.io/badge/-success-success></a>
<details>
<summary>FAILED ivy_tests/test_ivy/test_frontends/test_jax/test_jax_numpy_manipulation.py::test_jax_numpy_vsplit[cpu-ivy.functional.backends.torch-False-False]</summary>
2023-04-17T16:23:53.9533505Z E TypeError: 'tuple' object does not support item assignment2023-04-17T16:23:53.9533880Z E Falsifying example: test_jax_numpy_vsplit(2023-04-17T16:23:53.9534329Z E dtype_value=(['uint8'], [array([[0]], dtype=uint8)]),2023-04-17T16:23:53.9534659Z E indices_or_sections=1,2023-04-17T16:23:53.9535107Z E fn_tree='ivy.functional.frontends.jax.numpy.vsplit',2023-04-17T16:23:53.9535522Z E test_flags=FrontendFunctionTestFlags(2023-04-17T16:23:53.9535857Z E num_positional_args=0,2023-04-17T16:23:53.9536130Z E with_out=False,2023-04-17T16:23:53.9536395Z E inplace=False,2023-04-17T16:23:53.9536666Z E as_variable=[False],2023-04-17T16:23:53.9536946Z E native_arrays=[False],2023-04-17T16:23:53.9537253Z E generate_frontend_arrays=False,2023-04-17T16:23:53.9537521Z E ),2023-04-17T16:23:53.9537802Z E on_device='cpu',2023-04-17T16:23:53.9538086Z E frontend='jax',2023-04-17T16:23:53.9538326Z E )2023-04-17T16:23:53.9538536Z E 2023-04-17T16:23:53.9539168Z E You can reproduce this example by temporarily adding @reproduce_failure('6.72.0', b'AAABAAABAAAAAAABAAAAAAA=') as a decorator on your test case
</details>
|
1.0
|
Fix jax_numpy_manipulation.test_jax_numpy_vsplit - | | |
|---|---|
|tensorflow|<a href="https://github.com/unifyai/ivy/actions/runs/4723000381/jobs/8378357215" rel="noopener noreferrer" target="_blank"><img src=https://img.shields.io/badge/-success-success></a>
|torch|<a href="https://github.com/unifyai/ivy/actions/runs/4723000381/jobs/8378357215" rel="noopener noreferrer" target="_blank"><img src=https://img.shields.io/badge/-failure-red></a>
|numpy|<a href="https://github.com/unifyai/ivy/actions/runs/4723000381/jobs/8378357215" rel="noopener noreferrer" target="_blank"><img src=https://img.shields.io/badge/-success-success></a>
|jax|<a href="https://github.com/unifyai/ivy/actions/runs/4723000381/jobs/8378357215" rel="noopener noreferrer" target="_blank"><img src=https://img.shields.io/badge/-success-success></a>
<details>
<summary>FAILED ivy_tests/test_ivy/test_frontends/test_jax/test_jax_numpy_manipulation.py::test_jax_numpy_vsplit[cpu-ivy.functional.backends.torch-False-False]</summary>
2023-04-17T16:23:53.9533505Z E TypeError: 'tuple' object does not support item assignment2023-04-17T16:23:53.9533880Z E Falsifying example: test_jax_numpy_vsplit(2023-04-17T16:23:53.9534329Z E dtype_value=(['uint8'], [array([[0]], dtype=uint8)]),2023-04-17T16:23:53.9534659Z E indices_or_sections=1,2023-04-17T16:23:53.9535107Z E fn_tree='ivy.functional.frontends.jax.numpy.vsplit',2023-04-17T16:23:53.9535522Z E test_flags=FrontendFunctionTestFlags(2023-04-17T16:23:53.9535857Z E num_positional_args=0,2023-04-17T16:23:53.9536130Z E with_out=False,2023-04-17T16:23:53.9536395Z E inplace=False,2023-04-17T16:23:53.9536666Z E as_variable=[False],2023-04-17T16:23:53.9536946Z E native_arrays=[False],2023-04-17T16:23:53.9537253Z E generate_frontend_arrays=False,2023-04-17T16:23:53.9537521Z E ),2023-04-17T16:23:53.9537802Z E on_device='cpu',2023-04-17T16:23:53.9538086Z E frontend='jax',2023-04-17T16:23:53.9538326Z E )2023-04-17T16:23:53.9538536Z E 2023-04-17T16:23:53.9539168Z E You can reproduce this example by temporarily adding @reproduce_failure('6.72.0', b'AAABAAABAAAAAAABAAAAAAA=') as a decorator on your test case
</details>
|
non_priority
|
fix jax numpy manipulation test jax numpy vsplit tensorflow img src torch img src numpy img src jax img src failed ivy tests test ivy test frontends test jax test jax numpy manipulation py test jax numpy vsplit e typeerror tuple object does not support item e falsifying example test jax numpy vsplit e dtype value dtype e indices or sections e fn tree ivy functional frontends jax numpy vsplit e test flags frontendfunctiontestflags e num positional args e with out false e inplace false e as variable e native arrays e generate frontend arrays false e e on device cpu e frontend jax e e e you can reproduce this example by temporarily adding reproduce failure b aaabaaabaaaaaaabaaaaaaa as a decorator on your test case
| 0
|
559,245
| 16,553,546,895
|
IssuesEvent
|
2021-05-28 11:23:39
|
ballerina-platform/ballerina-lang
|
https://api.github.com/repos/ballerina-platform/ballerina-lang
|
closed
|
Functions are not suggested in the expression context of listener declaration
|
Area/Completion Priority/Blocker SwanLakeDump Team/LanguageServer Type/Bug
|
**Description:**
`public listener module1:Listener myLst = <cursor>`
`public listener module1:Listener myLst = module1:<cursor>`
**Steps to reproduce:**
Get the completions at the given cursor positions and the functions are not suggested.
**Affected Versions:**
beta1-rc1 at least
|
1.0
|
Functions are not suggested in the expression context of listener declaration - **Description:**
`public listener module1:Listener myLst = <cursor>`
`public listener module1:Listener myLst = module1:<cursor>`
**Steps to reproduce:**
Get the completions at the given cursor positions and the functions are not suggested.
**Affected Versions:**
beta1-rc1 at least
|
priority
|
functions are not suggested in the expression context of listener declaration description public listener listener mylst public listener listener mylst steps to reproduce get the completions at the given cursor positions and the functions are not suggested affected versions at least
| 1
|
45,282
| 13,109,032,884
|
IssuesEvent
|
2020-08-04 17:55:39
|
phunware/node-amqp
|
https://api.github.com/repos/phunware/node-amqp
|
opened
|
CVE-2018-3721 (Medium) detected in lodash-1.3.1.tgz
|
security vulnerability
|
## CVE-2018-3721 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>lodash-1.3.1.tgz</b></p></summary>
<p>A utility library delivering consistency, customization, performance, and extras.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-1.3.1.tgz">https://registry.npmjs.org/lodash/-/lodash-1.3.1.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/node-amqp/package.json</p>
<p>Path to vulnerable library: /node-amqp/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- :x: **lodash-1.3.1.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/phunware/node-amqp/commit/500e2bb15969969277fdcb839c0f552fa836a4ab">500e2bb15969969277fdcb839c0f552fa836a4ab</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
lodash node module before 4.17.5 suffers from a Modification of Assumed-Immutable Data (MAID) vulnerability via defaultsDeep, merge, and mergeWith functions, which allows a malicious user to modify the prototype of "Object" via __proto__, causing the addition or modification of an existing property that will exist on all objects.
<p>Publish Date: 2018-06-07
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-3721>CVE-2018-3721</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: High
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2018-3721">https://nvd.nist.gov/vuln/detail/CVE-2018-3721</a></p>
<p>Release Date: 2018-06-07</p>
<p>Fix Resolution: 4.17.5</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
True
|
CVE-2018-3721 (Medium) detected in lodash-1.3.1.tgz - ## CVE-2018-3721 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>lodash-1.3.1.tgz</b></p></summary>
<p>A utility library delivering consistency, customization, performance, and extras.</p>
<p>Library home page: <a href="https://registry.npmjs.org/lodash/-/lodash-1.3.1.tgz">https://registry.npmjs.org/lodash/-/lodash-1.3.1.tgz</a></p>
<p>Path to dependency file: /tmp/ws-scm/node-amqp/package.json</p>
<p>Path to vulnerable library: /node-amqp/node_modules/lodash/package.json</p>
<p>
Dependency Hierarchy:
- :x: **lodash-1.3.1.tgz** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/phunware/node-amqp/commit/500e2bb15969969277fdcb839c0f552fa836a4ab">500e2bb15969969277fdcb839c0f552fa836a4ab</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
lodash node module before 4.17.5 suffers from a Modification of Assumed-Immutable Data (MAID) vulnerability via defaultsDeep, merge, and mergeWith functions, which allows a malicious user to modify the prototype of "Object" via __proto__, causing the addition or modification of an existing property that will exist on all objects.
<p>Publish Date: 2018-06-07
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-3721>CVE-2018-3721</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.5</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: Low
- User Interaction: None
- Scope: Unchanged
- Impact Metrics:
- Confidentiality Impact: None
- Integrity Impact: High
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://nvd.nist.gov/vuln/detail/CVE-2018-3721">https://nvd.nist.gov/vuln/detail/CVE-2018-3721</a></p>
<p>Release Date: 2018-06-07</p>
<p>Fix Resolution: 4.17.5</p>
</p>
</details>
<p></p>
***
Step up your Open Source Security Game with WhiteSource [here](https://www.whitesourcesoftware.com/full_solution_bolt_github)
|
non_priority
|
cve medium detected in lodash tgz cve medium severity vulnerability vulnerable library lodash tgz a utility library delivering consistency customization performance and extras library home page a href path to dependency file tmp ws scm node amqp package json path to vulnerable library node amqp node modules lodash package json dependency hierarchy x lodash tgz vulnerable library found in head commit a href vulnerability details lodash node module before suffers from a modification of assumed immutable data maid vulnerability via defaultsdeep merge and mergewith functions which allows a malicious user to modify the prototype of object via proto causing the addition or modification of an existing property that will exist on all objects publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required low user interaction none scope unchanged impact metrics confidentiality impact none integrity impact high availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution step up your open source security game with whitesource
| 0
|
1,588
| 3,796,432,718
|
IssuesEvent
|
2016-03-23 00:27:03
|
aws/aws-sdk-js
|
https://api.github.com/repos/aws/aws-sdk-js
|
closed
|
Support index field statistics
|
Service / API
|
Since 2015-03-05, we can retrieve statistics against index numeric field.
http://aws.amazon.com/releasenotes/Amazon-CloudSearch/5060064203846541
But the sdk doesn't support to get stats for a numeric field.
|
1.0
|
Support index field statistics - Since 2015-03-05, we can retrieve statistics against index numeric field.
http://aws.amazon.com/releasenotes/Amazon-CloudSearch/5060064203846541
But the sdk doesn't support to get stats for a numeric field.
|
non_priority
|
support index field statistics since we can retrieve statistics against index numeric field but the sdk doesn t support to get stats for a numeric field
| 0
|
660,795
| 22,031,364,117
|
IssuesEvent
|
2022-05-28 00:09:38
|
TheNexusCity/webaverse-app
|
https://api.github.com/repos/TheNexusCity/webaverse-app
|
closed
|
Drag & Drop Doesn't works for both vrms and glbs
|
high priority
|
Right now if we try to Drag and drop vrms, both drop to world /Equip to self crashes the build
Same happens while we try to drag and drop glbs.

https://user-images.githubusercontent.com/35926530/167917391-74365392-d5fb-437c-83a9-2370ad5c7d8c.mp4
Additional context for drag and drop function:
https://github.com/webaverse/docs/blob/e960fd7e46e910d0ec51f65e0b8bbbdf5e301f08/docs/engineering/app/react/components/drag-n-drop.md
|
1.0
|
Drag & Drop Doesn't works for both vrms and glbs - Right now if we try to Drag and drop vrms, both drop to world /Equip to self crashes the build
Same happens while we try to drag and drop glbs.

https://user-images.githubusercontent.com/35926530/167917391-74365392-d5fb-437c-83a9-2370ad5c7d8c.mp4
Additional context for drag and drop function:
https://github.com/webaverse/docs/blob/e960fd7e46e910d0ec51f65e0b8bbbdf5e301f08/docs/engineering/app/react/components/drag-n-drop.md
|
priority
|
drag drop doesn t works for both vrms and glbs right now if we try to drag and drop vrms both drop to world equip to self crashes the build same happens while we try to drag and drop glbs additional context for drag and drop function
| 1
|
67,696
| 28,013,837,971
|
IssuesEvent
|
2023-03-27 20:47:04
|
MicrosoftDocs/azure-docs
|
https://api.github.com/repos/MicrosoftDocs/azure-docs
|
closed
|
Constant 429 errors for F0 free tier custom classification
|
triaged cxp product-question forms-recognizer/subsvc Pri1 applied-ai-services/svc
|
[Enter feedback here]
Hello,
I am doing some testing within my own Azure portal using the F0 free tier for Form Recognizer.
In the custom classification model I've uploaded 5 invoices (2 page and 784kb size each invoice) and whenever I click on train 429 http response is popped up in my screen and model is not trained at all.
Why is this happening?
Thanks
---
#### Document Details
⚠ *Do not edit this section. It is required for learn.microsoft.com ➟ GitHub issue linking.*
* ID: c0b05595-41e1-3dd0-8c7c-22049208c4d9
* Version Independent ID: fd1def80-67b7-44d0-872a-170c1c9ab907
* Content: [Build and train a custom classifier - Azure Applied AI Services](https://learn.microsoft.com/en-us/azure/applied-ai-services/form-recognizer/how-to-guides/build-a-custom-classifier?view=form-recog-3.0.0)
* Content Source: [articles/applied-ai-services/form-recognizer/how-to-guides/build-a-custom-classifier.md](https://github.com/MicrosoftDocs/azure-docs/blob/main/articles/applied-ai-services/form-recognizer/how-to-guides/build-a-custom-classifier.md)
* Service: **applied-ai-services**
* Sub-service: **forms-recognizer**
* GitHub Login: @laujan
* Microsoft Alias: **lajanuar**
|
1.0
|
Constant 429 errors for F0 free tier custom classification -
[Enter feedback here]
Hello,
I am doing some testing within my own Azure portal using the F0 free tier for Form Recognizer.
In the custom classification model I've uploaded 5 invoices (2 page and 784kb size each invoice) and whenever I click on train 429 http response is popped up in my screen and model is not trained at all.
Why is this happening?
Thanks
---
#### Document Details
⚠ *Do not edit this section. It is required for learn.microsoft.com ➟ GitHub issue linking.*
* ID: c0b05595-41e1-3dd0-8c7c-22049208c4d9
* Version Independent ID: fd1def80-67b7-44d0-872a-170c1c9ab907
* Content: [Build and train a custom classifier - Azure Applied AI Services](https://learn.microsoft.com/en-us/azure/applied-ai-services/form-recognizer/how-to-guides/build-a-custom-classifier?view=form-recog-3.0.0)
* Content Source: [articles/applied-ai-services/form-recognizer/how-to-guides/build-a-custom-classifier.md](https://github.com/MicrosoftDocs/azure-docs/blob/main/articles/applied-ai-services/form-recognizer/how-to-guides/build-a-custom-classifier.md)
* Service: **applied-ai-services**
* Sub-service: **forms-recognizer**
* GitHub Login: @laujan
* Microsoft Alias: **lajanuar**
|
non_priority
|
constant errors for free tier custom classification hello i am doing some testing within my own azure portal using the free tier for form recognizer in the custom classification model i ve uploaded invoices page and size each invoice and whenever i click on train http response is popped up in my screen and model is not trained at all why is this happening thanks document details ⚠ do not edit this section it is required for learn microsoft com ➟ github issue linking id version independent id content content source service applied ai services sub service forms recognizer github login laujan microsoft alias lajanuar
| 0
|
283,004
| 8,712,847,344
|
IssuesEvent
|
2018-12-06 23:47:06
|
linkerd/linkerd2
|
https://api.github.com/repos/linkerd/linkerd2
|
closed
|
Generate Service Profile from openapi spec
|
area/cli area/controller priority/P1
|
The openapi specification allows for definition of service routes. This spec is perfect for generating service profiles. The CLI should be able to consume a definition and output the service profile.
Related: #1425 #1418
|
1.0
|
Generate Service Profile from openapi spec - The openapi specification allows for definition of service routes. This spec is perfect for generating service profiles. The CLI should be able to consume a definition and output the service profile.
Related: #1425 #1418
|
priority
|
generate service profile from openapi spec the openapi specification allows for definition of service routes this spec is perfect for generating service profiles the cli should be able to consume a definition and output the service profile related
| 1
|
51,648
| 12,759,708,827
|
IssuesEvent
|
2020-06-29 06:32:19
|
fission/fission
|
https://api.github.com/repos/fission/fission
|
closed
|
Package waiting for builder pod to be ready should be better
|
area-builder area-ux good first issue size/S
|
Right now the package watcher/builder waits for only 15 iterations for the builder pod to be ready. Some environments need a slightly higher time. This should be more of a retry backoff mechanism before failing
https://github.com/fission/fission/blob/f606c3705f81832008aba130de7a0f5845387583/pkg/buildermgr/pkgwatcher.go#L103-L105
|
1.0
|
Package waiting for builder pod to be ready should be better - Right now the package watcher/builder waits for only 15 iterations for the builder pod to be ready. Some environments need a slightly higher time. This should be more of a retry backoff mechanism before failing
https://github.com/fission/fission/blob/f606c3705f81832008aba130de7a0f5845387583/pkg/buildermgr/pkgwatcher.go#L103-L105
|
non_priority
|
package waiting for builder pod to be ready should be better right now the package watcher builder waits for only iterations for the builder pod to be ready some environments need a slightly higher time this should be more of a retry backoff mechanism before failing
| 0
|
579,146
| 17,173,750,666
|
IssuesEvent
|
2021-07-15 08:50:33
|
webcompat/web-bugs
|
https://api.github.com/repos/webcompat/web-bugs
|
reopened
|
m.youtube.com - site is not usable
|
browser-firefox-ios os-ios priority-critical status-needsinfo
|
<!-- @browser: Firefox iOS 34.2 -->
<!-- @ua_header: Mozilla/5.0 (iPhone; CPU iPhone OS 14_6 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) FxiOS/34.2 Mobile/15E148 Safari/605.1.15 -->
<!-- @reported_with: mobile-reporter -->
<!-- @extra_labels: browser-firefox-ios -->
**URL**: https://m.youtube.com/results?i got a letter my score 698 now its down ehy#searching
**Browser / Version**: Firefox iOS 34.2
**Operating System**: iOS 14.6
**Tested Another Browser**: Yes Other
**Problem type**: Site is not usable
**Description**: Unable to login
**Steps to Reproduce**:
its nothing new fix one thing to find 9 million more
<details>
<summary>Browser Configuration</summary>
<ul>
<li>None</li>
</ul>
</details>
_From [webcompat.com](https://webcompat.com/) with ❤️_
|
1.0
|
m.youtube.com - site is not usable - <!-- @browser: Firefox iOS 34.2 -->
<!-- @ua_header: Mozilla/5.0 (iPhone; CPU iPhone OS 14_6 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) FxiOS/34.2 Mobile/15E148 Safari/605.1.15 -->
<!-- @reported_with: mobile-reporter -->
<!-- @extra_labels: browser-firefox-ios -->
**URL**: https://m.youtube.com/results?i got a letter my score 698 now its down ehy#searching
**Browser / Version**: Firefox iOS 34.2
**Operating System**: iOS 14.6
**Tested Another Browser**: Yes Other
**Problem type**: Site is not usable
**Description**: Unable to login
**Steps to Reproduce**:
its nothing new fix one thing to find 9 million more
<details>
<summary>Browser Configuration</summary>
<ul>
<li>None</li>
</ul>
</details>
_From [webcompat.com](https://webcompat.com/) with ❤️_
|
priority
|
m youtube com site is not usable url got a letter my score now its down ehy searching browser version firefox ios operating system ios tested another browser yes other problem type site is not usable description unable to login steps to reproduce its nothing new fix one thing to find million more browser configuration none from with ❤️
| 1
|
284,080
| 24,579,586,397
|
IssuesEvent
|
2022-10-13 14:42:23
|
MPMG-DCC-UFMG/F01
|
https://api.github.com/repos/MPMG-DCC-UFMG/F01
|
closed
|
Teste de generalizacao para a tag Informações institucionais - Estrutura Organizacional - Memory - Buenópolis
|
generalization test development template - Memory (66) tag - Informações Institucionais subtag - Estrutura Organizacional
|
DoD: Realizar o teste de Generalização do validador da tag Informações institucionais - Estrutura Organizacional - Memory para o Município de Buenópolis.
|
1.0
|
Teste de generalizacao para a tag Informações institucionais - Estrutura Organizacional - Memory - Buenópolis - DoD: Realizar o teste de Generalização do validador da tag Informações institucionais - Estrutura Organizacional - Memory para o Município de Buenópolis.
|
non_priority
|
teste de generalizacao para a tag informações institucionais estrutura organizacional memory buenópolis dod realizar o teste de generalização do validador da tag informações institucionais estrutura organizacional memory para o município de buenópolis
| 0
|
32,380
| 12,112,820,888
|
IssuesEvent
|
2020-04-21 14:20:52
|
wrbejar/VulnerableJavaWebApplicationEUA
|
https://api.github.com/repos/wrbejar/VulnerableJavaWebApplicationEUA
|
opened
|
CVE-2018-14040 (Medium) detected in bootstrap-3.3.7.min.js
|
security vulnerability
|
## CVE-2018-14040 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>bootstrap-3.3.7.min.js</b></p></summary>
<p>The most popular front-end framework for developing responsive, mobile first projects on the web.</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/twitter-bootstrap/3.3.7/js/bootstrap.min.js">https://cdnjs.cloudflare.com/ajax/libs/twitter-bootstrap/3.3.7/js/bootstrap.min.js</a></p>
<p>Path to vulnerable library: /VulnerableJavaWebApplicationEUA/src/main/webapp/resources/js/bootstrap.min.js,/VulnerableJavaWebApplicationEUA/src/main/webapp/resources/js/bootstrap.min.js</p>
<p>
Dependency Hierarchy:
- :x: **bootstrap-3.3.7.min.js** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/wrbejar/VulnerableJavaWebApplicationEUA/commit/7bfbee08927b5431ce3ec79acd1a17e44f997efe">7bfbee08927b5431ce3ec79acd1a17e44f997efe</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
In Bootstrap before 4.1.2, XSS is possible in the collapse data-parent attribute.
<p>Publish Date: 2018-07-13
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-14040>CVE-2018-14040</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/twbs/bootstrap/pull/26630">https://github.com/twbs/bootstrap/pull/26630</a></p>
<p>Release Date: 2018-07-13</p>
<p>Fix Resolution: org.webjars.npm:bootstrap:4.1.2.org.webjars:bootstrap:4.1.2</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"JavaScript","packageName":"twitter-bootstrap","packageVersion":"3.3.7","isTransitiveDependency":false,"dependencyTree":"twitter-bootstrap:3.3.7","isMinimumFixVersionAvailable":true,"minimumFixVersion":"org.webjars.npm:bootstrap:4.1.2.org.webjars:bootstrap:4.1.2"}],"vulnerabilityIdentifier":"CVE-2018-14040","vulnerabilityDetails":"In Bootstrap before 4.1.2, XSS is possible in the collapse data-parent attribute.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-14040","cvss3Severity":"medium","cvss3Score":"6.1","cvss3Metrics":{"A":"None","AC":"Low","PR":"None","S":"Changed","C":"Low","UI":"Required","AV":"Network","I":"Low"},"extraData":{}}</REMEDIATE> -->
|
True
|
CVE-2018-14040 (Medium) detected in bootstrap-3.3.7.min.js - ## CVE-2018-14040 - Medium Severity Vulnerability
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/vulnerability_details.png' width=19 height=20> Vulnerable Library - <b>bootstrap-3.3.7.min.js</b></p></summary>
<p>The most popular front-end framework for developing responsive, mobile first projects on the web.</p>
<p>Library home page: <a href="https://cdnjs.cloudflare.com/ajax/libs/twitter-bootstrap/3.3.7/js/bootstrap.min.js">https://cdnjs.cloudflare.com/ajax/libs/twitter-bootstrap/3.3.7/js/bootstrap.min.js</a></p>
<p>Path to vulnerable library: /VulnerableJavaWebApplicationEUA/src/main/webapp/resources/js/bootstrap.min.js,/VulnerableJavaWebApplicationEUA/src/main/webapp/resources/js/bootstrap.min.js</p>
<p>
Dependency Hierarchy:
- :x: **bootstrap-3.3.7.min.js** (Vulnerable Library)
<p>Found in HEAD commit: <a href="https://github.com/wrbejar/VulnerableJavaWebApplicationEUA/commit/7bfbee08927b5431ce3ec79acd1a17e44f997efe">7bfbee08927b5431ce3ec79acd1a17e44f997efe</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/medium_vul.png' width=19 height=20> Vulnerability Details</summary>
<p>
In Bootstrap before 4.1.2, XSS is possible in the collapse data-parent attribute.
<p>Publish Date: 2018-07-13
<p>URL: <a href=https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-14040>CVE-2018-14040</a></p>
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/cvss3.png' width=19 height=20> CVSS 3 Score Details (<b>6.1</b>)</summary>
<p>
Base Score Metrics:
- Exploitability Metrics:
- Attack Vector: Network
- Attack Complexity: Low
- Privileges Required: None
- User Interaction: Required
- Scope: Changed
- Impact Metrics:
- Confidentiality Impact: Low
- Integrity Impact: Low
- Availability Impact: None
</p>
For more information on CVSS3 Scores, click <a href="https://www.first.org/cvss/calculator/3.0">here</a>.
</p>
</details>
<p></p>
<details><summary><img src='https://whitesource-resources.whitesourcesoftware.com/suggested_fix.png' width=19 height=20> Suggested Fix</summary>
<p>
<p>Type: Upgrade version</p>
<p>Origin: <a href="https://github.com/twbs/bootstrap/pull/26630">https://github.com/twbs/bootstrap/pull/26630</a></p>
<p>Release Date: 2018-07-13</p>
<p>Fix Resolution: org.webjars.npm:bootstrap:4.1.2.org.webjars:bootstrap:4.1.2</p>
</p>
</details>
<p></p>
<!-- <REMEDIATE>{"isOpenPROnVulnerability":true,"isPackageBased":true,"isDefaultBranch":true,"packages":[{"packageType":"JavaScript","packageName":"twitter-bootstrap","packageVersion":"3.3.7","isTransitiveDependency":false,"dependencyTree":"twitter-bootstrap:3.3.7","isMinimumFixVersionAvailable":true,"minimumFixVersion":"org.webjars.npm:bootstrap:4.1.2.org.webjars:bootstrap:4.1.2"}],"vulnerabilityIdentifier":"CVE-2018-14040","vulnerabilityDetails":"In Bootstrap before 4.1.2, XSS is possible in the collapse data-parent attribute.","vulnerabilityUrl":"https://vuln.whitesourcesoftware.com/vulnerability/CVE-2018-14040","cvss3Severity":"medium","cvss3Score":"6.1","cvss3Metrics":{"A":"None","AC":"Low","PR":"None","S":"Changed","C":"Low","UI":"Required","AV":"Network","I":"Low"},"extraData":{}}</REMEDIATE> -->
|
non_priority
|
cve medium detected in bootstrap min js cve medium severity vulnerability vulnerable library bootstrap min js the most popular front end framework for developing responsive mobile first projects on the web library home page a href path to vulnerable library vulnerablejavawebapplicationeua src main webapp resources js bootstrap min js vulnerablejavawebapplicationeua src main webapp resources js bootstrap min js dependency hierarchy x bootstrap min js vulnerable library found in head commit a href vulnerability details in bootstrap before xss is possible in the collapse data parent attribute publish date url a href cvss score details base score metrics exploitability metrics attack vector network attack complexity low privileges required none user interaction required scope changed impact metrics confidentiality impact low integrity impact low availability impact none for more information on scores click a href suggested fix type upgrade version origin a href release date fix resolution org webjars npm bootstrap org webjars bootstrap isopenpronvulnerability true ispackagebased true isdefaultbranch true packages vulnerabilityidentifier cve vulnerabilitydetails in bootstrap before xss is possible in the collapse data parent attribute vulnerabilityurl
| 0
|
165,603
| 14,006,832,496
|
IssuesEvent
|
2020-10-28 20:35:08
|
aristanetworks/ansible-avd
|
https://api.github.com/repos/aristanetworks/ansible-avd
|
closed
|
add a table of content at the begining of the dev documentation outputed by AVD
|
role: eos_cli_config_gen type: documentation type: enhancement
|
**Issue Type**
- Documentation template enhancement
**Describe the solution you'd like**
update the template [eos-device-documentation.j2](https://github.com/aristanetworks/ansible-avd/blob/devel/ansible_collections/arista/avd/roles/eos_cli_config_gen/templates/eos-device-documentation.j2) to include a table of content at the begining
**Role or Module Name**
eos_cli_config_gen
|
1.0
|
add a table of content at the begining of the dev documentation outputed by AVD - **Issue Type**
- Documentation template enhancement
**Describe the solution you'd like**
update the template [eos-device-documentation.j2](https://github.com/aristanetworks/ansible-avd/blob/devel/ansible_collections/arista/avd/roles/eos_cli_config_gen/templates/eos-device-documentation.j2) to include a table of content at the begining
**Role or Module Name**
eos_cli_config_gen
|
non_priority
|
add a table of content at the begining of the dev documentation outputed by avd issue type documentation template enhancement describe the solution you d like update the template to include a table of content at the begining role or module name eos cli config gen
| 0
|
765,241
| 26,838,836,667
|
IssuesEvent
|
2023-02-02 22:00:44
|
gamefreedomgit/Maelstrom
|
https://api.github.com/repos/gamefreedomgit/Maelstrom
|
closed
|
[Profession] Northern Cloth Scavenging
|
Professions Spell Priority: High Status: Confirmed
|
Training [Northern Cloth Scavenging](https://cata-twinhead.twinstar.cz/?spell=59390) through any of the questgivers that offers to train you this (as a quest hand in requiring 5g in Howling Fjord, Borean Tundra, Dalaran) does not teach player this skill. Northern Cloth Scavenging should also affect Embersilk.
https://wowpedia.fandom.com/wiki/Cloth_Scavenging?so=search
|
1.0
|
[Profession] Northern Cloth Scavenging - Training [Northern Cloth Scavenging](https://cata-twinhead.twinstar.cz/?spell=59390) through any of the questgivers that offers to train you this (as a quest hand in requiring 5g in Howling Fjord, Borean Tundra, Dalaran) does not teach player this skill. Northern Cloth Scavenging should also affect Embersilk.
https://wowpedia.fandom.com/wiki/Cloth_Scavenging?so=search
|
priority
|
northern cloth scavenging training through any of the questgivers that offers to train you this as a quest hand in requiring in howling fjord borean tundra dalaran does not teach player this skill northern cloth scavenging should also affect embersilk
| 1
|
23,274
| 11,864,421,800
|
IssuesEvent
|
2020-03-25 21:38:45
|
Azure/azure-sdk-for-python
|
https://api.github.com/repos/Azure/azure-sdk-for-python
|
closed
|
[ServiceBus] Unsupported type 0x40 for array
|
Client Service Bus customer-reported
|
When connecting to azure service bus topic, reading from it and at the same time renewing the message lock the following exception occurs:
```
Failed to complete mgmt operation.
Status code: 500
Message: b'Unsupported type 0x40 for array. TrackingId:6568100f-6493-4e0e-a8bd-7ca7ba948885_G0, SystemTracker:NoSystemTracker, Timestamp:2019-11-19T12:42:49'
Traceback (most recent call last):
File "/root/.local/share/virtualenvs/bin-BjCKre66/lib/python3.6/site-packages/azure/servicebus/aio/async_base_handler.py", line 90, in _mgmt_request_response
callback=callback)
File "/root/.local/share/virtualenvs/bin-BjCKre66/lib/python3.6/site-packages/uamqp/async_ops/client_async.py", line 337, in mgmt_request_async
**kwargs))
File "/root/.local/share/virtualenvs/bin-BjCKre66/lib/python3.6/site-packages/uamqp/async_ops/session_async.py", line 114, in mgmt_request_async
return parse_response(status, response, description)
File "/root/.local/share/virtualenvs/bin-BjCKre66/lib/python3.6/site-packages/azure/servicebus/common/mgmt_handlers.py", line 28, in lock_renew_op
status_code, description, message.get_data()))
azure.servicebus.common.errors.ServiceBusError: Management request returned status code: 500. Description: b'Unsupported type 0x40 for array. TrackingId:6568100f-6493-4e0e-a8bd-7ca7ba948885_G0, SystemTracker:NoSystemTracker, Timestamp:2019-11-19T12:42:49', Data: None
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
...
File "/root/.local/share/virtualenvs/bin-BjCKre66/lib/python3.6/site-packages/azure/servicebus/aio/async_message.py", line 62, in renew_lock
expiry = await self._receiver._renew_locks(self.lock_token) # pylint: disable=protected-access
File "/root/.local/share/virtualenvs/bin-BjCKre66/lib/python3.6/site-packages/azure/servicebus/aio/async_receive_handler.py", line 163, in _renew_locks
mgmt_handlers.lock_renew_op)
File "/root/.local/share/virtualenvs/bin-BjCKre66/lib/python3.6/site-packages/azure/servicebus/aio/async_base_handler.py", line 92, in _mgmt_request_response
raise ServiceBusError("Management request failed: {}".format(exp), exp)
azure.servicebus.common.errors.ServiceBusError: Management request failed: Management request returned status code: 500. Description: b'Unsupported type 0x40 for array. TrackingId:6568100f-6493-4e0e-a8bd-7ca7ba948885_G0, SystemTracker:NoSystemTracker, Timestamp:2019-11-19T12:42:49', Data: None
```
|
1.0
|
[ServiceBus] Unsupported type 0x40 for array - When connecting to azure service bus topic, reading from it and at the same time renewing the message lock the following exception occurs:
```
Failed to complete mgmt operation.
Status code: 500
Message: b'Unsupported type 0x40 for array. TrackingId:6568100f-6493-4e0e-a8bd-7ca7ba948885_G0, SystemTracker:NoSystemTracker, Timestamp:2019-11-19T12:42:49'
Traceback (most recent call last):
File "/root/.local/share/virtualenvs/bin-BjCKre66/lib/python3.6/site-packages/azure/servicebus/aio/async_base_handler.py", line 90, in _mgmt_request_response
callback=callback)
File "/root/.local/share/virtualenvs/bin-BjCKre66/lib/python3.6/site-packages/uamqp/async_ops/client_async.py", line 337, in mgmt_request_async
**kwargs))
File "/root/.local/share/virtualenvs/bin-BjCKre66/lib/python3.6/site-packages/uamqp/async_ops/session_async.py", line 114, in mgmt_request_async
return parse_response(status, response, description)
File "/root/.local/share/virtualenvs/bin-BjCKre66/lib/python3.6/site-packages/azure/servicebus/common/mgmt_handlers.py", line 28, in lock_renew_op
status_code, description, message.get_data()))
azure.servicebus.common.errors.ServiceBusError: Management request returned status code: 500. Description: b'Unsupported type 0x40 for array. TrackingId:6568100f-6493-4e0e-a8bd-7ca7ba948885_G0, SystemTracker:NoSystemTracker, Timestamp:2019-11-19T12:42:49', Data: None
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
...
File "/root/.local/share/virtualenvs/bin-BjCKre66/lib/python3.6/site-packages/azure/servicebus/aio/async_message.py", line 62, in renew_lock
expiry = await self._receiver._renew_locks(self.lock_token) # pylint: disable=protected-access
File "/root/.local/share/virtualenvs/bin-BjCKre66/lib/python3.6/site-packages/azure/servicebus/aio/async_receive_handler.py", line 163, in _renew_locks
mgmt_handlers.lock_renew_op)
File "/root/.local/share/virtualenvs/bin-BjCKre66/lib/python3.6/site-packages/azure/servicebus/aio/async_base_handler.py", line 92, in _mgmt_request_response
raise ServiceBusError("Management request failed: {}".format(exp), exp)
azure.servicebus.common.errors.ServiceBusError: Management request failed: Management request returned status code: 500. Description: b'Unsupported type 0x40 for array. TrackingId:6568100f-6493-4e0e-a8bd-7ca7ba948885_G0, SystemTracker:NoSystemTracker, Timestamp:2019-11-19T12:42:49', Data: None
```
|
non_priority
|
unsupported type for array when connecting to azure service bus topic reading from it and at the same time renewing the message lock the following exception occurs failed to complete mgmt operation status code message b unsupported type for array trackingid systemtracker nosystemtracker timestamp traceback most recent call last file root local share virtualenvs bin lib site packages azure servicebus aio async base handler py line in mgmt request response callback callback file root local share virtualenvs bin lib site packages uamqp async ops client async py line in mgmt request async kwargs file root local share virtualenvs bin lib site packages uamqp async ops session async py line in mgmt request async return parse response status response description file root local share virtualenvs bin lib site packages azure servicebus common mgmt handlers py line in lock renew op status code description message get data azure servicebus common errors servicebuserror management request returned status code description b unsupported type for array trackingid systemtracker nosystemtracker timestamp data none during handling of the above exception another exception occurred traceback most recent call last file root local share virtualenvs bin lib site packages azure servicebus aio async message py line in renew lock expiry await self receiver renew locks self lock token pylint disable protected access file root local share virtualenvs bin lib site packages azure servicebus aio async receive handler py line in renew locks mgmt handlers lock renew op file root local share virtualenvs bin lib site packages azure servicebus aio async base handler py line in mgmt request response raise servicebuserror management request failed format exp exp azure servicebus common errors servicebuserror management request failed management request returned status code description b unsupported type for array trackingid systemtracker nosystemtracker timestamp data none
| 0
|
700,881
| 24,076,744,633
|
IssuesEvent
|
2022-09-18 22:18:26
|
midas-network/midas-data
|
https://api.github.com/repos/midas-network/midas-data
|
closed
|
Demographics - new term?
|
low priority
|
The ontology contains "Age-stratified" as a subclass of "Population demographic census". This term is not yet in the data catalog entry form but if we add it, should we also add a term for:
- gender
- sex
- race
- ethnicity
|
1.0
|
Demographics - new term? - The ontology contains "Age-stratified" as a subclass of "Population demographic census". This term is not yet in the data catalog entry form but if we add it, should we also add a term for:
- gender
- sex
- race
- ethnicity
|
priority
|
demographics new term the ontology contains age stratified as a subclass of population demographic census this term is not yet in the data catalog entry form but if we add it should we also add a term for gender sex race ethnicity
| 1
|
620,324
| 19,559,264,104
|
IssuesEvent
|
2022-01-03 14:07:39
|
brave/brave-browser
|
https://api.github.com/repos/brave/brave-browser
|
closed
|
Change the description for the setting `Automatically sends crash reports to Brave`
|
needs-text-change priority/P3 QA/Yes release-notes/include OS/Android OS/Desktop
|
We are planning to`HangWatcher` feature which send crash dump when browser hangs.
Before enabling the feature the text should be changed to something like _Automatically sends crash reports and **hangs** to Brave_
Existing
<img width="698" alt="Screen Shot 2021-11-30 at 10 42 46 AM" src="https://user-images.githubusercontent.com/5951041/144108297-37db7f87-b047-4f52-a97a-99e8312f1ddd.png">
Security review: https://github.com/brave/security/issues/659
|
1.0
|
Change the description for the setting `Automatically sends crash reports to Brave` - We are planning to`HangWatcher` feature which send crash dump when browser hangs.
Before enabling the feature the text should be changed to something like _Automatically sends crash reports and **hangs** to Brave_
Existing
<img width="698" alt="Screen Shot 2021-11-30 at 10 42 46 AM" src="https://user-images.githubusercontent.com/5951041/144108297-37db7f87-b047-4f52-a97a-99e8312f1ddd.png">
Security review: https://github.com/brave/security/issues/659
|
priority
|
change the description for the setting automatically sends crash reports to brave we are planning to hangwatcher feature which send crash dump when browser hangs before enabling the feature the text should be changed to something like automatically sends crash reports and hangs to brave existing img width alt screen shot at am src security review
| 1
|
156,744
| 13,654,358,144
|
IssuesEvent
|
2020-09-27 17:01:42
|
JohnErnsthausen/roc
|
https://api.github.com/repos/JohnErnsthausen/roc
|
closed
|
Submit my Problem Statement
|
documentation
|
Hello @smiths, Please find my ProblemStatement document in the agreed upon directory.
|
1.0
|
Submit my Problem Statement - Hello @smiths, Please find my ProblemStatement document in the agreed upon directory.
|
non_priority
|
submit my problem statement hello smiths please find my problemstatement document in the agreed upon directory
| 0
|
695,567
| 23,864,253,130
|
IssuesEvent
|
2022-09-07 09:39:11
|
hengband/hengband
|
https://api.github.com/repos/hengband/hengband
|
opened
|
ObjectType::art_name をquarkインデックスから固定アーティファクト情報への参照 (optional)に変える
|
refactor Priority:LOW
|
昔の設計で、ObjectTypeに文字列まで保存させると容量の都合やらポインタの取り扱いやらで色々不都合があったのだと想定される
サッと取り出せるようにしたい
既に固定アーティファクト側の名前定義はそうなっている
銘以外は複雑なことをしなくても良くなる、はず
(過去バージョンとの兼ね合いがあるのでセーブファイルの読み込み時は注意)
|
1.0
|
ObjectType::art_name をquarkインデックスから固定アーティファクト情報への参照 (optional)に変える - 昔の設計で、ObjectTypeに文字列まで保存させると容量の都合やらポインタの取り扱いやらで色々不都合があったのだと想定される
サッと取り出せるようにしたい
既に固定アーティファクト側の名前定義はそうなっている
銘以外は複雑なことをしなくても良くなる、はず
(過去バージョンとの兼ね合いがあるのでセーブファイルの読み込み時は注意)
|
priority
|
objecttype art name をquarkインデックスから固定アーティファクト情報への参照 optional に変える 昔の設計で、objecttypeに文字列まで保存させると容量の都合やらポインタの取り扱いやらで色々不都合があったのだと想定される サッと取り出せるようにしたい 既に固定アーティファクト側の名前定義はそうなっている 銘以外は複雑なことをしなくても良くなる、はず 過去バージョンとの兼ね合いがあるのでセーブファイルの読み込み時は注意
| 1
|
710,712
| 24,430,158,571
|
IssuesEvent
|
2022-10-06 07:31:16
|
FinalProject-AIPARK/JenaPark-BE
|
https://api.github.com/repos/FinalProject-AIPARK/JenaPark-BE
|
opened
|
Video Entity, Service, Controller, Repository
|
Priority: Medium Type: Feature/Function Status: Proposal
|
## 설명
영상 관련 로직 구현
## 할 일
- [ ] Entity 완성
- [ ] Service 구현
- [ ] Controller 구현
- [ ] Repository 생성
## 기타
참조 및 링크를 첨부하시오.
|
1.0
|
Video Entity, Service, Controller, Repository - ## 설명
영상 관련 로직 구현
## 할 일
- [ ] Entity 완성
- [ ] Service 구현
- [ ] Controller 구현
- [ ] Repository 생성
## 기타
참조 및 링크를 첨부하시오.
|
priority
|
video entity service controller repository 설명 영상 관련 로직 구현 할 일 entity 완성 service 구현 controller 구현 repository 생성 기타 참조 및 링크를 첨부하시오
| 1
|
91,583
| 18,546,049,321
|
IssuesEvent
|
2021-10-21 22:23:36
|
ArctosDB/arctos
|
https://api.github.com/repos/ArctosDB/arctos
|
closed
|
Code Table Request - new part name
|
Priority-Critical (Arctos is broken) Function-CodeTables CodeTableCleanup
|
**Goal**
Discombobulate parts
**Context**
Need new "bare" part name
**Table**
https://arctos.database.museum/info/ctDocumentation.cfm?table=ctspecimen_part_name
**Value**
swab
**Definition**
An absorbent device. Should be accompanied by part attribute(s) specifying where and how the swab was used.
**Collection type**
Fish
Mamm
Bird
Herp
**Priority**
critical; will block part cleanup
|
2.0
|
Code Table Request - new part name - **Goal**
Discombobulate parts
**Context**
Need new "bare" part name
**Table**
https://arctos.database.museum/info/ctDocumentation.cfm?table=ctspecimen_part_name
**Value**
swab
**Definition**
An absorbent device. Should be accompanied by part attribute(s) specifying where and how the swab was used.
**Collection type**
Fish
Mamm
Bird
Herp
**Priority**
critical; will block part cleanup
|
non_priority
|
code table request new part name goal discombobulate parts context need new bare part name table value swab definition an absorbent device should be accompanied by part attribute s specifying where and how the swab was used collection type fish mamm bird herp priority critical will block part cleanup
| 0
|
66,082
| 12,709,034,294
|
IssuesEvent
|
2020-06-23 11:38:07
|
microsoft/AL
|
https://api.github.com/repos/microsoft/AL
|
opened
|
Warn when triggers are declared with no code
|
static-code-analysis
|
**Title**
I suggest a code analysis rule when a trigger has been declared and contains no code between begin/end.
**Description**
Developers might create empty triggers by using VSCode templates.
The worst come from the txt2al tool: in C/AL+years of development and developers might have created empty triggers just by letting a local variable declared and not removing it.
**Reason for the rule**
Like warning AA0137 it would let us keep the code clean and prevent triggers to be called without reason.
**Bad code sample**
Example of what bad code the rule should catch:
```
trigger OnAfterGetRecord()
var
Status: Text;
i: Integer;
j: Integer;
begin
end;
```
**Good code sample**
Example of what code should look like:
``` The trigger should be removed ```
**Good and bad practices for fixing the rule**
A code action could be provided to remove the trigger.
**Remarks**
A similar rule could apply on empty procedures.
|
1.0
|
Warn when triggers are declared with no code - **Title**
I suggest a code analysis rule when a trigger has been declared and contains no code between begin/end.
**Description**
Developers might create empty triggers by using VSCode templates.
The worst come from the txt2al tool: in C/AL+years of development and developers might have created empty triggers just by letting a local variable declared and not removing it.
**Reason for the rule**
Like warning AA0137 it would let us keep the code clean and prevent triggers to be called without reason.
**Bad code sample**
Example of what bad code the rule should catch:
```
trigger OnAfterGetRecord()
var
Status: Text;
i: Integer;
j: Integer;
begin
end;
```
**Good code sample**
Example of what code should look like:
``` The trigger should be removed ```
**Good and bad practices for fixing the rule**
A code action could be provided to remove the trigger.
**Remarks**
A similar rule could apply on empty procedures.
|
non_priority
|
warn when triggers are declared with no code title i suggest a code analysis rule when a trigger has been declared and contains no code between begin end description developers might create empty triggers by using vscode templates the worst come from the tool in c al years of development and developers might have created empty triggers just by letting a local variable declared and not removing it reason for the rule like warning it would let us keep the code clean and prevent triggers to be called without reason bad code sample example of what bad code the rule should catch trigger onaftergetrecord var status text i integer j integer begin end good code sample example of what code should look like the trigger should be removed good and bad practices for fixing the rule a code action could be provided to remove the trigger remarks a similar rule could apply on empty procedures
| 0
|
51,427
| 7,699,135,203
|
IssuesEvent
|
2018-05-19 08:28:16
|
benoitc/gunicorn
|
https://api.github.com/repos/benoitc/gunicorn
|
opened
|
Use literalinclude in docs/source/deploy.rst
|
Documentation Help Wanted
|
Currently, we are duplicating some examples in our deployment documentation. We could use `literalinclude` for the following configuration files:
* Runit: https://github.com/benoitc/gunicorn/blob/master/examples/gunicorn_rc
* Supervisor: https://github.com/benoitc/gunicorn/blob/master/examples/supervisor.conf
We should also move Upstart (and probably there are others) example into `examples/` and include it via `literalinclude`.
|
1.0
|
Use literalinclude in docs/source/deploy.rst - Currently, we are duplicating some examples in our deployment documentation. We could use `literalinclude` for the following configuration files:
* Runit: https://github.com/benoitc/gunicorn/blob/master/examples/gunicorn_rc
* Supervisor: https://github.com/benoitc/gunicorn/blob/master/examples/supervisor.conf
We should also move Upstart (and probably there are others) example into `examples/` and include it via `literalinclude`.
|
non_priority
|
use literalinclude in docs source deploy rst currently we are duplicating some examples in our deployment documentation we could use literalinclude for the following configuration files runit supervisor we should also move upstart and probably there are others example into examples and include it via literalinclude
| 0
|
549,508
| 16,094,246,408
|
IssuesEvent
|
2021-04-26 20:39:10
|
Warcraft-GoA-Development-Team/Warcraft-Guardians-of-Azeroth
|
https://api.github.com/repos/Warcraft-GoA-Development-Team/Warcraft-Guardians-of-Azeroth
|
opened
|
Shadow Council missions need more variety
|
:grey_exclamation: priority low :question: suggestion :question:
|
<!--
DO NOT REMOVE PRE-EXISTING LINES
IF YOU WANT TO SUGGEST A FEW THINGS, OPEN A NEW ISSUE PER EVERY SUGGESTION
----------------------------------------------------------------------------------------------------------
-->
This is a part of a much larger post I put out earlier. However at the request of a dev, I went out and split it into a set of smaller suggestions.
So I just finished a nearly 40 year playthrough of the Burning Blade clan in Desolace. My goal was to establish something akin to the Old Horde, visibly consorting with demons and ruling with an iron fist, and while I did have a blast exploring the various events and options that you folk have made for this unique playthrough, there were some problems that eventually forced me to stop the run as a whole.
A separate but still relevant point is the Shadow Council missions, first of all its almost impossible to find a virgin or a priest in the court I was commanding, I had to marry my vassals and wait for them to have a kid before killing them... yeah it was fucked up. It could use a bit more variety, like recruiting an important member to the Shadow Council or converting a faithful to fel worship and such. I also thought that it could've been really cool if controlled counties can have their unique version of purge population like mass sacrifice to the fel, which could perhaps spawn other unique events.
|
1.0
|
Shadow Council missions need more variety - <!--
DO NOT REMOVE PRE-EXISTING LINES
IF YOU WANT TO SUGGEST A FEW THINGS, OPEN A NEW ISSUE PER EVERY SUGGESTION
----------------------------------------------------------------------------------------------------------
-->
This is a part of a much larger post I put out earlier. However at the request of a dev, I went out and split it into a set of smaller suggestions.
So I just finished a nearly 40 year playthrough of the Burning Blade clan in Desolace. My goal was to establish something akin to the Old Horde, visibly consorting with demons and ruling with an iron fist, and while I did have a blast exploring the various events and options that you folk have made for this unique playthrough, there were some problems that eventually forced me to stop the run as a whole.
A separate but still relevant point is the Shadow Council missions, first of all its almost impossible to find a virgin or a priest in the court I was commanding, I had to marry my vassals and wait for them to have a kid before killing them... yeah it was fucked up. It could use a bit more variety, like recruiting an important member to the Shadow Council or converting a faithful to fel worship and such. I also thought that it could've been really cool if controlled counties can have their unique version of purge population like mass sacrifice to the fel, which could perhaps spawn other unique events.
|
priority
|
shadow council missions need more variety do not remove pre existing lines if you want to suggest a few things open a new issue per every suggestion this is a part of a much larger post i put out earlier however at the request of a dev i went out and split it into a set of smaller suggestions so i just finished a nearly year playthrough of the burning blade clan in desolace my goal was to establish something akin to the old horde visibly consorting with demons and ruling with an iron fist and while i did have a blast exploring the various events and options that you folk have made for this unique playthrough there were some problems that eventually forced me to stop the run as a whole a separate but still relevant point is the shadow council missions first of all its almost impossible to find a virgin or a priest in the court i was commanding i had to marry my vassals and wait for them to have a kid before killing them yeah it was fucked up it could use a bit more variety like recruiting an important member to the shadow council or converting a faithful to fel worship and such i also thought that it could ve been really cool if controlled counties can have their unique version of purge population like mass sacrifice to the fel which could perhaps spawn other unique events
| 1
|
265,442
| 8,354,374,340
|
IssuesEvent
|
2018-10-02 13:09:24
|
mozilla/addons-server
|
https://api.github.com/repos/mozilla/addons-server
|
opened
|
Validate submitted source code
|
component: devhub priority: p2
|
https://github.com/mozilla/addons-server/blob/d71d63cc1e350ddebe495cda6ea4247edcb35414/src/olympia/versions/models.py#L42-L44 allows different file formats for uploading source code.
We rely on them being valid for doing code-search (and review of course), but we don't do any kind of validation (other than checking the file extension). The result is, that there are some files either being corrupt/incomplete or have the wrong file extension (presumably to make the upload pass), but are in fact a different compression algorithm.
Therefore, we need to add some validation to uploaded source code files:
* Check the file signature (magic number), instead of just the file extension and
* Verify the archive is valid.
Looking into [pyunpack](https://github.com/ponty/pyunpack) might be worthwhile.
Justification for P2: The daily code-extraction script that provides the data for code-search relies valid files and correct format. We recently mitigated some issues regarding formats, but we cannot anticipate or support every potential compression algorithm.
|
1.0
|
Validate submitted source code - https://github.com/mozilla/addons-server/blob/d71d63cc1e350ddebe495cda6ea4247edcb35414/src/olympia/versions/models.py#L42-L44 allows different file formats for uploading source code.
We rely on them being valid for doing code-search (and review of course), but we don't do any kind of validation (other than checking the file extension). The result is, that there are some files either being corrupt/incomplete or have the wrong file extension (presumably to make the upload pass), but are in fact a different compression algorithm.
Therefore, we need to add some validation to uploaded source code files:
* Check the file signature (magic number), instead of just the file extension and
* Verify the archive is valid.
Looking into [pyunpack](https://github.com/ponty/pyunpack) might be worthwhile.
Justification for P2: The daily code-extraction script that provides the data for code-search relies valid files and correct format. We recently mitigated some issues regarding formats, but we cannot anticipate or support every potential compression algorithm.
|
priority
|
validate submitted source code allows different file formats for uploading source code we rely on them being valid for doing code search and review of course but we don t do any kind of validation other than checking the file extension the result is that there are some files either being corrupt incomplete or have the wrong file extension presumably to make the upload pass but are in fact a different compression algorithm therefore we need to add some validation to uploaded source code files check the file signature magic number instead of just the file extension and verify the archive is valid looking into might be worthwhile justification for the daily code extraction script that provides the data for code search relies valid files and correct format we recently mitigated some issues regarding formats but we cannot anticipate or support every potential compression algorithm
| 1
|
559,581
| 16,565,731,773
|
IssuesEvent
|
2021-05-29 11:14:29
|
sopra-fs21-group-11/sopra-server
|
https://api.github.com/repos/sopra-fs21-group-11/sopra-server
|
closed
|
S9: As a user I want to be able to chat with other players in the game which are logged in
|
medium priority user story
|
- [ ] only a unique username is possible
|
1.0
|
S9: As a user I want to be able to chat with other players in the game which are logged in - - [ ] only a unique username is possible
|
priority
|
as a user i want to be able to chat with other players in the game which are logged in only a unique username is possible
| 1
|
478,608
| 13,782,311,241
|
IssuesEvent
|
2020-10-08 17:27:09
|
AY2021S1-CS2103T-F13-3/tp
|
https://api.github.com/repos/AY2021S1-CS2103T-F13-3/tp
|
closed
|
As a registration admin, I can add a new patient record using a minimal amount of detail, so that I can register important details first and add in more details at a later stage.
|
priority.Medium type.Story
|
Compulsory fields: `IC`, `Name`, `Phone`, `DOB`
Optional fields: `Height`, `Weight`, `Blood Type`, `Address`, `Email`
Contains #45 #48 #49
|
1.0
|
As a registration admin, I can add a new patient record using a minimal amount of detail, so that I can register important details first and add in more details at a later stage. - Compulsory fields: `IC`, `Name`, `Phone`, `DOB`
Optional fields: `Height`, `Weight`, `Blood Type`, `Address`, `Email`
Contains #45 #48 #49
|
priority
|
as a registration admin i can add a new patient record using a minimal amount of detail so that i can register important details first and add in more details at a later stage compulsory fields ic name phone dob optional fields height weight blood type address email contains
| 1
|
45,851
| 5,967,393,040
|
IssuesEvent
|
2017-05-30 15:51:43
|
typearea/dembelo
|
https://api.github.com/repos/typearea/dembelo
|
closed
|
Finanzierungsseite: Seite designen
|
Design ready
|
Siehe #230: Der Leser soll merken, wieso die Geschichte an dem jeweiligen Textknoten endet, und er soll erfahren, was er tun soll, damit die Geschichte weitergeht. Der Leser soll zu Patreon geleitet werden, wo er textknotenunabhängig für eine Fortsetzung spenden kann.
In diesem Ticket soll die Finanzierungsseite designt werden.
|
1.0
|
Finanzierungsseite: Seite designen - Siehe #230: Der Leser soll merken, wieso die Geschichte an dem jeweiligen Textknoten endet, und er soll erfahren, was er tun soll, damit die Geschichte weitergeht. Der Leser soll zu Patreon geleitet werden, wo er textknotenunabhängig für eine Fortsetzung spenden kann.
In diesem Ticket soll die Finanzierungsseite designt werden.
|
non_priority
|
finanzierungsseite seite designen siehe der leser soll merken wieso die geschichte an dem jeweiligen textknoten endet und er soll erfahren was er tun soll damit die geschichte weitergeht der leser soll zu patreon geleitet werden wo er textknotenunabhängig für eine fortsetzung spenden kann in diesem ticket soll die finanzierungsseite designt werden
| 0
|
39,476
| 5,234,258,031
|
IssuesEvent
|
2017-01-30 15:14:31
|
cockroachdb/cockroach
|
https://api.github.com/repos/cockroachdb/cockroach
|
closed
|
github.com/cockroachdb/cockroach/pkg/storage: TestStoreRangeSplitAtIllegalKeys failed under stress
|
Robot test-failure
|
SHA: https://github.com/cockroachdb/cockroach/commits/4c53128707d07d268833ff5ccb5acee9d8720544
Parameters:
```
COCKROACH_PROPOSER_EVALUATED_KV=false
TAGS=
GOFLAGS=-race
```
Stress build found a failed test: https://teamcity.cockroachdb.com/viewLog.html?buildId=133052&tab=buildLog
```
I170130 09:52:56.740095 33202 gossip/gossip.go:293 [n1] NodeDescriptor set to node_id:1 address:<network_field:"" address_field:"" > attrs:<> locality:<>
I170130 09:52:56.747691 33202 storage/store.go:1255 [n1,s1]: failed initial metrics computation: [n1,s1]: system config not yet available
I170130 09:52:56.757282 33232 storage/split_queue.go:99 [split,s1,r1/1:/M{in-ax},@c4216de000] splitting at keys [/Table/11/0 /Table/12/0 /Table/13/0 /Table/14/0]
I170130 09:52:56.761121 33232 storage/replica_command.go:2354 [split,s1,r1/1:/M{in-ax},@c4216de000] initiating a split of this range at key /Table/11 [r2]
E170130 09:52:56.777337 33232 storage/queue.go:599 [split,s1,r1/1:/{Min-Table/11},@c4216de000] unable to split [n1,s1,r1/1:/{Min-Table/11}] at key "/Table/12/0": key range /Table/12/0-/Table/12/0 outside of bounds of range /Min-/Max
I170130 09:52:56.786641 33232 storage/split_queue.go:99 [split,s1,r1/1:/{Min-Table/11},@c4216de000] splitting at keys [/Table/0/0]
I170130 09:52:56.786874 33232 storage/replica_command.go:2354 [split,s1,r1/1:/{Min-Table/11},@c4216de000] initiating a split of this range at key /Table/0 [r3]
E170130 09:52:56.805231 33233 storage/queue.go:610 [replicate,s1,r1/1:/{Min-Table/0},@c4216de000] purgatory: 0 of 0 stores with all attributes matching []; likely not enough nodes in cluster
I170130 09:52:56.805780 33232 storage/split_queue.go:99 [split,s1,r2/1:/{Table/11-Max},@c420f2e000] splitting at keys [/Table/12/0 /Table/13/0 /Table/14/0]
I170130 09:52:56.805976 33232 storage/replica_command.go:2354 [split,s1,r2/1:/{Table/11-Max},@c420f2e000] initiating a split of this range at key /Table/12 [r4]
E170130 09:52:56.807588 33233 storage/queue.go:610 [replicate,s1,r3/1:/Table/{0-11},@c420f2e300] purgatory: 0 of 0 stores with all attributes matching []; likely not enough nodes in cluster
W170130 09:52:56.810589 33232 storage/stores.go:218 range not contained in one range: [/Meta2/Table/12,/Table/12/NULL), but have [/Min,/Table/0)
I170130 09:52:56.813616 33202 util/stop/stopper.go:472 quiescing; tasks left:
1 storage/queue.go:507
1 kv/txn_coord_sender.go:920
I170130 09:52:56.814085 33202 util/stop/stopper.go:472 quiescing; tasks left:
1 storage/queue.go:507
W170130 09:52:56.814230 33232 storage/replica.go:2148 [split,s1,r1/1:/{Min-Table/0},@c4216de000] shutdown cancellation after 0.0s of attempting command [txn: bbecd1fd], Noop, Put [/Meta2/Max,/Min), Put [/Meta2/Table/12,/Min)
E170130 09:52:56.814909 33232 internal/client/txn.go:356 [split,s1,r2/1:/{Table/11-Max},@c420f2e000] failure aborting transaction: writing transaction timed out or ran on multiple coordinators; abort caused by: node unavailable; try another peer
E170130 09:52:56.815229 33232 storage/queue.go:599 [split,s1,r2/1:/{Table/11-Max},@c420f2e000] unable to split [n1,s1,r2/1:/{Table/11-Max}] at key "/Table/12/0": storage/replica_command.go:2433: split at key /Table/12 failed: node unavailable; try another peer
client_split_test.go:88: /Table/10: unexpected split error key range /Table/10-/Table/10 outside of bounds of range /Min-/Table/0
```
|
1.0
|
github.com/cockroachdb/cockroach/pkg/storage: TestStoreRangeSplitAtIllegalKeys failed under stress - SHA: https://github.com/cockroachdb/cockroach/commits/4c53128707d07d268833ff5ccb5acee9d8720544
Parameters:
```
COCKROACH_PROPOSER_EVALUATED_KV=false
TAGS=
GOFLAGS=-race
```
Stress build found a failed test: https://teamcity.cockroachdb.com/viewLog.html?buildId=133052&tab=buildLog
```
I170130 09:52:56.740095 33202 gossip/gossip.go:293 [n1] NodeDescriptor set to node_id:1 address:<network_field:"" address_field:"" > attrs:<> locality:<>
I170130 09:52:56.747691 33202 storage/store.go:1255 [n1,s1]: failed initial metrics computation: [n1,s1]: system config not yet available
I170130 09:52:56.757282 33232 storage/split_queue.go:99 [split,s1,r1/1:/M{in-ax},@c4216de000] splitting at keys [/Table/11/0 /Table/12/0 /Table/13/0 /Table/14/0]
I170130 09:52:56.761121 33232 storage/replica_command.go:2354 [split,s1,r1/1:/M{in-ax},@c4216de000] initiating a split of this range at key /Table/11 [r2]
E170130 09:52:56.777337 33232 storage/queue.go:599 [split,s1,r1/1:/{Min-Table/11},@c4216de000] unable to split [n1,s1,r1/1:/{Min-Table/11}] at key "/Table/12/0": key range /Table/12/0-/Table/12/0 outside of bounds of range /Min-/Max
I170130 09:52:56.786641 33232 storage/split_queue.go:99 [split,s1,r1/1:/{Min-Table/11},@c4216de000] splitting at keys [/Table/0/0]
I170130 09:52:56.786874 33232 storage/replica_command.go:2354 [split,s1,r1/1:/{Min-Table/11},@c4216de000] initiating a split of this range at key /Table/0 [r3]
E170130 09:52:56.805231 33233 storage/queue.go:610 [replicate,s1,r1/1:/{Min-Table/0},@c4216de000] purgatory: 0 of 0 stores with all attributes matching []; likely not enough nodes in cluster
I170130 09:52:56.805780 33232 storage/split_queue.go:99 [split,s1,r2/1:/{Table/11-Max},@c420f2e000] splitting at keys [/Table/12/0 /Table/13/0 /Table/14/0]
I170130 09:52:56.805976 33232 storage/replica_command.go:2354 [split,s1,r2/1:/{Table/11-Max},@c420f2e000] initiating a split of this range at key /Table/12 [r4]
E170130 09:52:56.807588 33233 storage/queue.go:610 [replicate,s1,r3/1:/Table/{0-11},@c420f2e300] purgatory: 0 of 0 stores with all attributes matching []; likely not enough nodes in cluster
W170130 09:52:56.810589 33232 storage/stores.go:218 range not contained in one range: [/Meta2/Table/12,/Table/12/NULL), but have [/Min,/Table/0)
I170130 09:52:56.813616 33202 util/stop/stopper.go:472 quiescing; tasks left:
1 storage/queue.go:507
1 kv/txn_coord_sender.go:920
I170130 09:52:56.814085 33202 util/stop/stopper.go:472 quiescing; tasks left:
1 storage/queue.go:507
W170130 09:52:56.814230 33232 storage/replica.go:2148 [split,s1,r1/1:/{Min-Table/0},@c4216de000] shutdown cancellation after 0.0s of attempting command [txn: bbecd1fd], Noop, Put [/Meta2/Max,/Min), Put [/Meta2/Table/12,/Min)
E170130 09:52:56.814909 33232 internal/client/txn.go:356 [split,s1,r2/1:/{Table/11-Max},@c420f2e000] failure aborting transaction: writing transaction timed out or ran on multiple coordinators; abort caused by: node unavailable; try another peer
E170130 09:52:56.815229 33232 storage/queue.go:599 [split,s1,r2/1:/{Table/11-Max},@c420f2e000] unable to split [n1,s1,r2/1:/{Table/11-Max}] at key "/Table/12/0": storage/replica_command.go:2433: split at key /Table/12 failed: node unavailable; try another peer
client_split_test.go:88: /Table/10: unexpected split error key range /Table/10-/Table/10 outside of bounds of range /Min-/Table/0
```
|
non_priority
|
github com cockroachdb cockroach pkg storage teststorerangesplitatillegalkeys failed under stress sha parameters cockroach proposer evaluated kv false tags goflags race stress build found a failed test gossip gossip go nodedescriptor set to node id address attrs locality storage store go failed initial metrics computation system config not yet available storage split queue go splitting at keys storage replica command go initiating a split of this range at key table storage queue go unable to split at key table key range table table outside of bounds of range min max storage split queue go splitting at keys storage replica command go initiating a split of this range at key table storage queue go purgatory of stores with all attributes matching likely not enough nodes in cluster storage split queue go splitting at keys storage replica command go initiating a split of this range at key table storage queue go purgatory of stores with all attributes matching likely not enough nodes in cluster storage stores go range not contained in one range table table null but have min table util stop stopper go quiescing tasks left storage queue go kv txn coord sender go util stop stopper go quiescing tasks left storage queue go storage replica go shutdown cancellation after of attempting command noop put max min put table min internal client txn go failure aborting transaction writing transaction timed out or ran on multiple coordinators abort caused by node unavailable try another peer storage queue go unable to split at key table storage replica command go split at key table failed node unavailable try another peer client split test go table unexpected split error key range table table outside of bounds of range min table
| 0
|
5,484
| 2,576,735,455
|
IssuesEvent
|
2015-02-12 12:32:11
|
eclipsesource/tabris-js
|
https://api.github.com/repos/eclipsesource/tabris-js
|
closed
|
Load tabris.js as a module
|
priority: medium
|
Currently tabris.js is located by the "tabris" entry in a projects package.json, which is not part of any standard. We should load tabris.js as a node-module instead. To do so we need the following.
- tabris.js must be provided in a way that can be installed via npm. While the obvioius solution is to contribute it to npm itself, but it can also be an URL pointing to a git repo or tgz archive.
- The module script needs to be separated from tabris.js and built into the clients themselves.
- The native funtions require by the module system need to be made available before tabris.js is loaded. Either the nativeBridge is installed sooner, or these specific funtions are attached to the Module system itself.
- The startup must be changed to first load the Module script, then call require("tabris"). Everything else should be done by the module system.
|
1.0
|
Load tabris.js as a module - Currently tabris.js is located by the "tabris" entry in a projects package.json, which is not part of any standard. We should load tabris.js as a node-module instead. To do so we need the following.
- tabris.js must be provided in a way that can be installed via npm. While the obvioius solution is to contribute it to npm itself, but it can also be an URL pointing to a git repo or tgz archive.
- The module script needs to be separated from tabris.js and built into the clients themselves.
- The native funtions require by the module system need to be made available before tabris.js is loaded. Either the nativeBridge is installed sooner, or these specific funtions are attached to the Module system itself.
- The startup must be changed to first load the Module script, then call require("tabris"). Everything else should be done by the module system.
|
priority
|
load tabris js as a module currently tabris js is located by the tabris entry in a projects package json which is not part of any standard we should load tabris js as a node module instead to do so we need the following tabris js must be provided in a way that can be installed via npm while the obvioius solution is to contribute it to npm itself but it can also be an url pointing to a git repo or tgz archive the module script needs to be separated from tabris js and built into the clients themselves the native funtions require by the module system need to be made available before tabris js is loaded either the nativebridge is installed sooner or these specific funtions are attached to the module system itself the startup must be changed to first load the module script then call require tabris everything else should be done by the module system
| 1
|
113,128
| 4,543,583,965
|
IssuesEvent
|
2016-09-10 06:46:00
|
dwyl/hq
|
https://api.github.com/repos/dwyl/hq
|
closed
|
Write a github reference for non-technical people
|
enhancement help wanted priority-2 va-task
|
**We use Github to manage our projects.** It's our [version control system](https://git-scm.com/book/en/v2/Getting-Started-About-Version-Control), our task list ([product backlog](https://www.atlassian.com/agile/backlogs/), where our [automated reviews take place](https://github.com/dwyl/repo-badges) and where our progress can be fully tracked.
However, whereas developers are often familiar with Github, clients are not. We need to have a document that clients can refer back to after a short training session (or as _the_ training session) on the most important things they need to know to work with issues and track progress on GitHub.
|
1.0
|
Write a github reference for non-technical people - **We use Github to manage our projects.** It's our [version control system](https://git-scm.com/book/en/v2/Getting-Started-About-Version-Control), our task list ([product backlog](https://www.atlassian.com/agile/backlogs/), where our [automated reviews take place](https://github.com/dwyl/repo-badges) and where our progress can be fully tracked.
However, whereas developers are often familiar with Github, clients are not. We need to have a document that clients can refer back to after a short training session (or as _the_ training session) on the most important things they need to know to work with issues and track progress on GitHub.
|
priority
|
write a github reference for non technical people we use github to manage our projects it s our our task list where our and where our progress can be fully tracked however whereas developers are often familiar with github clients are not we need to have a document that clients can refer back to after a short training session or as the training session on the most important things they need to know to work with issues and track progress on github
| 1
|
38,964
| 8,560,220,501
|
IssuesEvent
|
2018-11-09 00:10:05
|
WordPress/twentynineteen
|
https://api.github.com/repos/WordPress/twentynineteen
|
closed
|
PHP syntax errors on PHP < 5.5 made it to master due to Travis not failing builds
|
code quality has patch needs testing
|
As of writing this, `footer.php` contains this:
```php
<?php if ( ! empty( get_bloginfo( 'name' ) ) ) : ?>
```
which results in `Fatal error: Can't use function return value in write context in ./footer.php on line 21` on PHP < 5.5 due to no arbitrary expression support for `empty()` (the same issue is present in `site-branding.php` as well).
While the travis checks did output the parse error, the build did not fail since `find` does not technically fail and thus its exit code is 0.
I'll submit a PR to fix this in a couple of minutes.
|
1.0
|
PHP syntax errors on PHP < 5.5 made it to master due to Travis not failing builds - As of writing this, `footer.php` contains this:
```php
<?php if ( ! empty( get_bloginfo( 'name' ) ) ) : ?>
```
which results in `Fatal error: Can't use function return value in write context in ./footer.php on line 21` on PHP < 5.5 due to no arbitrary expression support for `empty()` (the same issue is present in `site-branding.php` as well).
While the travis checks did output the parse error, the build did not fail since `find` does not technically fail and thus its exit code is 0.
I'll submit a PR to fix this in a couple of minutes.
|
non_priority
|
php syntax errors on php made it to master due to travis not failing builds as of writing this footer php contains this php which results in fatal error can t use function return value in write context in footer php on line on php due to no arbitrary expression support for empty the same issue is present in site branding php as well while the travis checks did output the parse error the build did not fail since find does not technically fail and thus its exit code is i ll submit a pr to fix this in a couple of minutes
| 0
|
670,595
| 22,695,477,299
|
IssuesEvent
|
2022-07-05 05:17:18
|
space-wizards/RobustToolbox
|
https://api.github.com/repos/space-wizards/RobustToolbox
|
opened
|
findgridsintersecting Box2Rotated needs to be tighter
|
Issue: Feature Request Priority: 2-Important Difficulty: 2-Medium
|
RN it just converts it to an AABB and checks which is much more approximate which sometimes affects evac shuttle docking in ss14.
|
1.0
|
findgridsintersecting Box2Rotated needs to be tighter - RN it just converts it to an AABB and checks which is much more approximate which sometimes affects evac shuttle docking in ss14.
|
priority
|
findgridsintersecting needs to be tighter rn it just converts it to an aabb and checks which is much more approximate which sometimes affects evac shuttle docking in
| 1
|
14,461
| 24,915,231,267
|
IssuesEvent
|
2022-10-30 10:17:04
|
cskefu/cskefu
|
https://api.github.com/repos/cskefu/cskefu
|
closed
|
Setup 春松客服贡献者协议:DCO or CLA
|
requirement
|
Use contributor-assistant, https://github.com/contributor-assistant/github-action.
Decide which form to use: DCO or CLA.
|
1.0
|
Setup 春松客服贡献者协议:DCO or CLA -
Use contributor-assistant, https://github.com/contributor-assistant/github-action.
Decide which form to use: DCO or CLA.
|
non_priority
|
setup 春松客服贡献者协议:dco or cla use contributor assistant decide which form to use dco or cla
| 0
|
180,332
| 13,930,091,034
|
IssuesEvent
|
2020-10-22 01:28:53
|
OpenMined/PySyft
|
https://api.github.com/repos/OpenMined/PySyft
|
closed
|
Add torch.Tensor.__itruediv__ to allowlist and test suite
|
Priority: 2 - High :cold_sweat: Severity: 3 - Medium :unamused: Status: Available :wave: Type: New Feature :heavy_plus_sign: Type: Testing :test_tube:
|
# Description
This issue is a part of Syft 0.3.0 Epic 2: https://github.com/OpenMined/PySyft/issues/3696
In this issue, you will be adding support for remote execution of the torch.Tensor.__itruediv__
method or property. This might be a really small project (literally a one-liner) or
it might require adding significant functionality to PySyft OR to the testing suite
in order to make sure the feature is both functional and tested.
## Step 0: Run tests and ./scripts/pre_commit.sh
Before you get started with this project, let's make sure you have everything building and testing
correctly. Clone the codebase and run:
```pip uninstall syft```
followed by
```pip install -e .```
Then run the pre-commit file (which will also run the tests)
```./scripts/pre_commit.sh```
If all of these tests pass, continue on. If not, make sure you have all the
dependencies in requirements.txt installed, etc.
## Step 1: Uncomment your method in the allowlist.py file
Inside [allowlist.py](https://github.com/OpenMined/PySyft/blob/syft_0.3.0/src/syft/lib/torch/allowlist.py) you will find a huge dictionary of methods. Find your method and uncomment the line its on. At the time
of writing this Issue (WARNING: THIS MAY HAVE CHANGED) the dictionary maps from the
string name of the method (in your case 'torch.Tensor.__itruediv__') to the string representation
of the type the method returns.
## Step 2: Run Unit Tests
Run the following:
```python setup.py test```
And wait to see if some of the tests fail. Why might the tests fail now? I'm so glad you asked!
https://github.com/OpenMined/PySyft/blob/syft_0.3.0/tests/syft/lib/torch/tensor/tensor_remote_method_api_suite_test.py
In this file you'll find the torch method test suite. It AUTOMATICALLY loads all methods
from the allowlist.py file you modified in the previous step. It attempts to test them.
# Step 3: If you get a Failing Test
If you get a failing test, this could be for one of a few reasons:
### Reason 1 - The testing suite passed in non-compatible arguments
The testing suite is pretty dumb. It literally just has a permutation of possible
arguments to pass into every method on torch tensors. So, if one of those permutations
doesn't work for your method (aka... perhaps it tries to call your method without
any arguments but torch.Tensor.__itruediv__ actually requires some) then the test will
fail if the error hasn't been seen before.
If this happens - don't worry! Just look inside the only test in that file and look
for the huge lists of error types to ignore. Add your error to the list and keep
going!!!
*WARNING:* make sure that the testing suite actually tests your method via remote
execution once you've gotten all the tests passing. Aka - if the testing suite
doesn't have ANY matching argument permutations for your method, then you're
literally creating a bunch of unit tests that do absolutely nothing. If this is the
case, then ADD MORE ARGUMENT TYPES TO THE TESTING SUITE so that your argument
gets run via remote execution. DO NOT CLOSE THIS ISSUE until you can verify that
torch.Tensor.__itruediv__ is actually executed remotely inside of a unit tests (and not
skipped). Aka - at least one of the test_all_allowlisted_tensor_methods_work_remotely_on_all_types
unit tests with your method should run ALL THE WAY TO THE END (instead of skipping
the last part.)
*Note:* adding another argument type might require some serialization work if
we don't support arguments of that type yet. If so, this is your job to add it
to the protobuf files in order to close this issue!
### Reason 2 - torch.Tensor.__itruediv__ returns a non-supported type
If this happens, you've got a little bit of work in front of you. We don't have
pointer objects to very many remote object types. So, if your method returns anything
other than a single tensor, you probably need to add support for the type it returns
(Such as a bool, None, int, or other types).
*IMPORTANT:* do NOT return the value itself to the end user!!! Return a pointer object
to that type!
*NOTE:* at the time of writing - there are several core pieces of Syft not yet working
to allow you to return any type other than a torch tensor. If you're not comfortable
investigating what those might be - skip this issue and try again later once
someone else has solved these issues.
### Reason 3 - There's something else broken
Chase those stack traces! Talk to friends in Slack. Look at how other methods are supported.
This is a challenging project in a fast moving codebase!
And don't forget - if this project seems to complex - there are plenty of others that
might be easier.
|
2.0
|
Add torch.Tensor.__itruediv__ to allowlist and test suite -
# Description
This issue is a part of Syft 0.3.0 Epic 2: https://github.com/OpenMined/PySyft/issues/3696
In this issue, you will be adding support for remote execution of the torch.Tensor.__itruediv__
method or property. This might be a really small project (literally a one-liner) or
it might require adding significant functionality to PySyft OR to the testing suite
in order to make sure the feature is both functional and tested.
## Step 0: Run tests and ./scripts/pre_commit.sh
Before you get started with this project, let's make sure you have everything building and testing
correctly. Clone the codebase and run:
```pip uninstall syft```
followed by
```pip install -e .```
Then run the pre-commit file (which will also run the tests)
```./scripts/pre_commit.sh```
If all of these tests pass, continue on. If not, make sure you have all the
dependencies in requirements.txt installed, etc.
## Step 1: Uncomment your method in the allowlist.py file
Inside [allowlist.py](https://github.com/OpenMined/PySyft/blob/syft_0.3.0/src/syft/lib/torch/allowlist.py) you will find a huge dictionary of methods. Find your method and uncomment the line its on. At the time
of writing this Issue (WARNING: THIS MAY HAVE CHANGED) the dictionary maps from the
string name of the method (in your case 'torch.Tensor.__itruediv__') to the string representation
of the type the method returns.
## Step 2: Run Unit Tests
Run the following:
```python setup.py test```
And wait to see if some of the tests fail. Why might the tests fail now? I'm so glad you asked!
https://github.com/OpenMined/PySyft/blob/syft_0.3.0/tests/syft/lib/torch/tensor/tensor_remote_method_api_suite_test.py
In this file you'll find the torch method test suite. It AUTOMATICALLY loads all methods
from the allowlist.py file you modified in the previous step. It attempts to test them.
# Step 3: If you get a Failing Test
If you get a failing test, this could be for one of a few reasons:
### Reason 1 - The testing suite passed in non-compatible arguments
The testing suite is pretty dumb. It literally just has a permutation of possible
arguments to pass into every method on torch tensors. So, if one of those permutations
doesn't work for your method (aka... perhaps it tries to call your method without
any arguments but torch.Tensor.__itruediv__ actually requires some) then the test will
fail if the error hasn't been seen before.
If this happens - don't worry! Just look inside the only test in that file and look
for the huge lists of error types to ignore. Add your error to the list and keep
going!!!
*WARNING:* make sure that the testing suite actually tests your method via remote
execution once you've gotten all the tests passing. Aka - if the testing suite
doesn't have ANY matching argument permutations for your method, then you're
literally creating a bunch of unit tests that do absolutely nothing. If this is the
case, then ADD MORE ARGUMENT TYPES TO THE TESTING SUITE so that your argument
gets run via remote execution. DO NOT CLOSE THIS ISSUE until you can verify that
torch.Tensor.__itruediv__ is actually executed remotely inside of a unit tests (and not
skipped). Aka - at least one of the test_all_allowlisted_tensor_methods_work_remotely_on_all_types
unit tests with your method should run ALL THE WAY TO THE END (instead of skipping
the last part.)
*Note:* adding another argument type might require some serialization work if
we don't support arguments of that type yet. If so, this is your job to add it
to the protobuf files in order to close this issue!
### Reason 2 - torch.Tensor.__itruediv__ returns a non-supported type
If this happens, you've got a little bit of work in front of you. We don't have
pointer objects to very many remote object types. So, if your method returns anything
other than a single tensor, you probably need to add support for the type it returns
(Such as a bool, None, int, or other types).
*IMPORTANT:* do NOT return the value itself to the end user!!! Return a pointer object
to that type!
*NOTE:* at the time of writing - there are several core pieces of Syft not yet working
to allow you to return any type other than a torch tensor. If you're not comfortable
investigating what those might be - skip this issue and try again later once
someone else has solved these issues.
### Reason 3 - There's something else broken
Chase those stack traces! Talk to friends in Slack. Look at how other methods are supported.
This is a challenging project in a fast moving codebase!
And don't forget - if this project seems to complex - there are plenty of others that
might be easier.
|
non_priority
|
add torch tensor itruediv to allowlist and test suite description this issue is a part of syft epic in this issue you will be adding support for remote execution of the torch tensor itruediv method or property this might be a really small project literally a one liner or it might require adding significant functionality to pysyft or to the testing suite in order to make sure the feature is both functional and tested step run tests and scripts pre commit sh before you get started with this project let s make sure you have everything building and testing correctly clone the codebase and run pip uninstall syft followed by pip install e then run the pre commit file which will also run the tests scripts pre commit sh if all of these tests pass continue on if not make sure you have all the dependencies in requirements txt installed etc step uncomment your method in the allowlist py file inside you will find a huge dictionary of methods find your method and uncomment the line its on at the time of writing this issue warning this may have changed the dictionary maps from the string name of the method in your case torch tensor itruediv to the string representation of the type the method returns step run unit tests run the following python setup py test and wait to see if some of the tests fail why might the tests fail now i m so glad you asked in this file you ll find the torch method test suite it automatically loads all methods from the allowlist py file you modified in the previous step it attempts to test them step if you get a failing test if you get a failing test this could be for one of a few reasons reason the testing suite passed in non compatible arguments the testing suite is pretty dumb it literally just has a permutation of possible arguments to pass into every method on torch tensors so if one of those permutations doesn t work for your method aka perhaps it tries to call your method without any arguments but torch tensor itruediv actually requires some then the test will fail if the error hasn t been seen before if this happens don t worry just look inside the only test in that file and look for the huge lists of error types to ignore add your error to the list and keep going warning make sure that the testing suite actually tests your method via remote execution once you ve gotten all the tests passing aka if the testing suite doesn t have any matching argument permutations for your method then you re literally creating a bunch of unit tests that do absolutely nothing if this is the case then add more argument types to the testing suite so that your argument gets run via remote execution do not close this issue until you can verify that torch tensor itruediv is actually executed remotely inside of a unit tests and not skipped aka at least one of the test all allowlisted tensor methods work remotely on all types unit tests with your method should run all the way to the end instead of skipping the last part note adding another argument type might require some serialization work if we don t support arguments of that type yet if so this is your job to add it to the protobuf files in order to close this issue reason torch tensor itruediv returns a non supported type if this happens you ve got a little bit of work in front of you we don t have pointer objects to very many remote object types so if your method returns anything other than a single tensor you probably need to add support for the type it returns such as a bool none int or other types important do not return the value itself to the end user return a pointer object to that type note at the time of writing there are several core pieces of syft not yet working to allow you to return any type other than a torch tensor if you re not comfortable investigating what those might be skip this issue and try again later once someone else has solved these issues reason there s something else broken chase those stack traces talk to friends in slack look at how other methods are supported this is a challenging project in a fast moving codebase and don t forget if this project seems to complex there are plenty of others that might be easier
| 0
|
9,918
| 3,078,606,949
|
IssuesEvent
|
2015-08-21 11:28:37
|
devprovers/QA-Teamwork-Provers
|
https://api.github.com/repos/devprovers/QA-Teamwork-Provers
|
closed
|
Add Contact
|
To Be Tested Use Case
|
Use Case №12: Add Contact
Primary Actor: User
Pre Condition: User logged in
Main scenario:
1. User initiates the “Add Contact” functionality from CRM/Contacts (left pane, refer user screens in Appendix )
2. User specifies first and last names of the contact
3. User specifies email
4. User specifies phone
5. User specifies Company (if necessary)
6. User specifies contact type
7. User specifies responsible person
8. A contact is created
Alternate scenario:
8.1. Add Contact cancelation
8.1.1. “Add Contact” functionality is canceled
8.2. Contact with the same information exists
8.2.1. System asks the user for different information
8.2.1. Contact is created
8.2.2. System asks the user for merging with existing contact
8.2.1. Contact is merged
8.2.3. System cancels the “Add Contact” functionality
|
1.0
|
Add Contact - Use Case №12: Add Contact
Primary Actor: User
Pre Condition: User logged in
Main scenario:
1. User initiates the “Add Contact” functionality from CRM/Contacts (left pane, refer user screens in Appendix )
2. User specifies first and last names of the contact
3. User specifies email
4. User specifies phone
5. User specifies Company (if necessary)
6. User specifies contact type
7. User specifies responsible person
8. A contact is created
Alternate scenario:
8.1. Add Contact cancelation
8.1.1. “Add Contact” functionality is canceled
8.2. Contact with the same information exists
8.2.1. System asks the user for different information
8.2.1. Contact is created
8.2.2. System asks the user for merging with existing contact
8.2.1. Contact is merged
8.2.3. System cancels the “Add Contact” functionality
|
non_priority
|
add contact use case № add contact primary actor user pre condition user logged in main scenario user initiates the “add contact” functionality from crm contacts left pane refer user screens in appendix user specifies first and last names of the contact user specifies email user specifies phone user specifies company if necessary user specifies contact type user specifies responsible person a contact is created alternate scenario add contact cancelation “add contact” functionality is canceled contact with the same information exists system asks the user for different information contact is created system asks the user for merging with existing contact contact is merged system cancels the “add contact” functionality
| 0
|
40,871
| 10,198,251,195
|
IssuesEvent
|
2019-08-13 04:21:12
|
jccastillo0007/eFacturaT
|
https://api.github.com/repos/jccastillo0007/eFacturaT
|
closed
|
Condominios - CxC, agregar la búsqueda que se tiene en catálogos e Ingresos
|
defect
|
Para el menú de Ingresar Cobro y Cartera por Casa.
En los otros menús, no se ocupa esa búsqueda
|
1.0
|
Condominios - CxC, agregar la búsqueda que se tiene en catálogos e Ingresos - Para el menú de Ingresar Cobro y Cartera por Casa.
En los otros menús, no se ocupa esa búsqueda
|
non_priority
|
condominios cxc agregar la búsqueda que se tiene en catálogos e ingresos para el menú de ingresar cobro y cartera por casa en los otros menús no se ocupa esa búsqueda
| 0
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.